Human and Mobile Robot Tracking in Environments with Different Scales
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Hmong Culture: Kinship, Marriage & Family Systems
THE HMONG CULTURE: KINSHIP, MARRIAGE & FAMILY SYSTEMS By Teng Moua A Research Paper Submitted in Partial Fulfillment of the Requirements for the Master of Science Degree With a Major in Marriage and Family Therapy Approved: 2 Semester Credits _________________________ Thesis Advisor The Graduate College University of Wisconsin-Stout May 2003 i The Graduate College University of Wisconsin-Stout Menomonie, Wisconsin 54751 ABSTRACT Moua__________________________Teng_____________________(NONE)________ (Writer) (Last Name) (First) (Initial) The Hmong Culture: Kinship, Marriage & Family Systems_____________________ (Title) Marriage & Family Therapy Dr. Charles Barnard May, 2003___51____ (Graduate Major) (Research Advisor) (Month/Year) (No. of Pages) American Psychological Association (APA) Publication Manual_________________ (Name of Style Manual Used In This Study) The purpose of this study is to describe the traditional Hmong kinship, marriage and family systems in the format of narrative from the writer’s experiences, a thorough review of the existing literature written about the Hmong culture in these three (3) categories, and two structural interviews of two Hmong families in the United States. This study only gives a general overview of the traditional Hmong kinship, marriage and family systems as they exist for the Hmong people in the United States currently. Therefore, it will not cover all the details and variations regarding the traditional Hmong kinship, marriage and family which still guide Hmong people around the world. Also, it will not cover the ii whole life course transitions such as childhood, adolescence, adulthood, late adulthood or the aging process or life core issues. This study is divided into two major parts: a review of literature and two interviews of the two selected Hmong families (one traditional & one contemporary) in the Minneapolis-St. -

A Re-Evaluation of Pelliot Tibétain 1257: an Early Tibet- An-Chinese Glossary from Dunhuang1
A Re-evaluation of Pelliot tibétain 1257: An Early Tibet- an-Chinese Glossary from Dunhuang1 James B. Apple and Shinobu A. Apple Introduction elliot tibétain 1257 (hereafter, PT1257) is an early manuscript preserved from the ancient city-state of Dunhuang kept P among the materials of the Paul Pelliot collection conserved at the Bibliothéque Nationale de France in Paris, France. Digital images of the manuscript are found at the web site of Gallica Digital Library (http://gallica.bnf.fr) and the International Dunhuang Project (http:// idp.bl.uk/; hereafter, IDP). French scholars Marcelle Lalou (1939) and R.A. Stein (1983 [English translation 2010]) have previously dis- cussed in an abbreviated manner the content and characteristics of this manuscript. A more extensive discussion of PT1257 is found among Japanese Buddhologists and specialists in Dunhuang studies. Akira Fujieda (1966), Zuihō Yamaguchi (1975), and Noriaki Haka- maya (1984) have provided initial insights into the structure and con- tent of PT1257 while the work of Ryūtoku Kimura (1985) and Kōsho Akamatsu (1988) have furnished more detailed points of analysis that have contributed to our current understanding of this manu- script. Other scholarship related to PT1257 has suggested that the manuscript was from a Chinese monastery and that it was utilized to help Chinese scholars translate Tibetan. This paper re-evaluates this presumption based upon a close analysis of the material components of the manuscript, the scribal writing, its list of Buddhist scriptures, and its vocabulary. Our assessment argues that PT1257 was a copy of a document initiated and circulated by Tibetans, presumably among Chinese monasteries in Dunhuang, to learn the Chinese equivalents to Tibetan translation terminology that was already in use among Tibet- ans. -

Evaluating Performance Benefits of Head Tracking in Modern Video
Evaluating Performance Benefits of Head Tracking in Modern Video Games Arun Kulshreshth Joseph J. LaViola Jr. Department of EECS Department of EECS University of Central Florida University of Central Florida 4000 Central Florida Blvd 4000 Central Florida Blvd Orlando, FL 32816, USA Orlando, FL 32816, USA [email protected] [email protected] ABSTRACT PlayStation Move, TrackIR 5) that support 3D spatial in- teraction have been implemented and made available to con- We present a study that investigates user performance ben- sumers. Head tracking is one example of an interaction tech- efits of using head tracking in modern video games. We nique, commonly used in the virtual and augmented reality explored four di↵erent carefully chosen commercial games communities [2, 7, 9], that has potential to be a useful ap- with tasks which can potentially benefit from head tracking. proach for controlling certain gaming tasks. Recent work on For each game, quantitative and qualitative measures were head tracking and video games has shown some potential taken to determine if users performed better and learned for this type of gaming interface. For example, Sko et al. faster in the experimental group (with head tracking) than [10] proposed a taxonomy of head gestures for first person in the control group (without head tracking). A game ex- shooter (FPS) games and showed that some of their tech- pertise pre-questionnaire was used to classify participants niques (peering, zooming, iron-sighting and spinning) are into casual and expert categories to analyze a possible im- useful in games. In addition, previous studies [13, 14] have pact on performance di↵erences. -

Gateless Gate Has Become Common in English, Some Have Criticized This Translation As Unfaithful to the Original
Wú Mén Guān The Barrier That Has No Gate Original Collection in Chinese by Chán Master Wúmén Huìkāi (1183-1260) Questions and Additional Comments by Sŏn Master Sǔngan Compiled and Edited by Paul Dōch’ŏng Lynch, JDPSN Page ii Frontspiece “Wú Mén Guān” Facsimile of the Original Cover Page iii Page iv Wú Mén Guān The Barrier That Has No Gate Chán Master Wúmén Huìkāi (1183-1260) Questions and Additional Comments by Sŏn Master Sǔngan Compiled and Edited by Paul Dōch’ŏng Lynch, JDPSN Sixth Edition Before Thought Publications Huntington Beach, CA 2010 Page v BEFORE THOUGHT PUBLICATIONS HUNTINGTON BEACH, CA 92648 ALL RIGHTS RESERVED. COPYRIGHT © 2010 ENGLISH VERSION BY PAUL LYNCH, JDPSN NO PART OF THIS BOOK MAY BE REPRODUCED OR TRANSMITTED IN ANY FORM OR BY ANY MEANS, GRAPHIC, ELECTRONIC, OR MECHANICAL, INCLUDING PHOTOCOPYING, RECORDING, TAPING OR BY ANY INFORMATION STORAGE OR RETRIEVAL SYSTEM, WITHOUT THE PERMISSION IN WRITING FROM THE PUBLISHER. PRINTED IN THE UNITED STATES OF AMERICA BY LULU INCORPORATION, MORRISVILLE, NC, USA COVER PRINTED ON LAMINATED 100# ULTRA GLOSS COVER STOCK, DIGITAL COLOR SILK - C2S, 90 BRIGHT BOOK CONTENT PRINTED ON 24/60# CREAM TEXT, 90 GSM PAPER, USING 12 PT. GARAMOND FONT Page vi Dedication What are we in this cosmos? This ineffable question has haunted us since Buddha sat under the Bodhi Tree. I would like to gracefully thank the author, Chán Master Wúmén, for his grace and kindness by leaving us these wonderful teachings. I would also like to thank Chán Master Dàhuì for his ineptness in destroying all copies of this book; thankfully, Master Dàhuì missed a few so that now we can explore the teachings of his teacher. -

An Efficient Framework for Implementing Persistent Data Structures on Asymmetric NVM Architecture
AsymNVM: An Efficient Framework for Implementing Persistent Data Structures on Asymmetric NVM Architecture Teng Ma Mingxing Zhang Kang Chen∗ [email protected] [email protected] [email protected] Tsinghua University Tsinghua University & Sangfor Tsinghua University Beijing, China Shenzhen, China Beijing, China Zhuo Song Yongwei Wu Xuehai Qian [email protected] [email protected] [email protected] Alibaba Tsinghua University University of Southern California Beijing, China Beijing, China Los Angles, CA Abstract We build AsymNVM framework based on AsymNVM ar- The byte-addressable non-volatile memory (NVM) is a promis- chitecture that implements: 1) high performance persistent ing technology since it simultaneously provides DRAM-like data structure update; 2) NVM data management; 3) con- performance, disk-like capacity, and persistency. The cur- currency control; and 4) crash-consistency and replication. rent NVM deployment with byte-addressability is symmetric, The key idea to remove persistency bottleneck is the use of where NVM devices are directly attached to servers. Due to operation log that reduces stall time due to RDMA writes and the higher density, NVM provides much larger capacity and enables efficient batching and caching in front-end nodes. should be shared among servers. Unfortunately, in the sym- To evaluate performance, we construct eight widely used metric setting, the availability of NVM devices is affected by data structures and two transaction applications based on the specific machine it is attached to. High availability canbe AsymNVM framework. In a 10-node cluster equipped with achieved by replicating data to NVM on a remote machine. real NVM devices, results show that AsymNVM achieves However, it requires full replication of data structure in local similar or better performance compared to the best possible memory — limiting the size of the working set. -
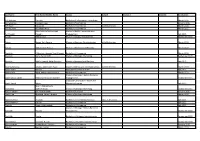
Last Name First Name/Middle Name Course Award Course 2 Award 2 Graduation
Last Name First Name/Middle Name Course Award Course 2 Award 2 Graduation A/L Krishnan Thiinash Bachelor of Information Technology March 2015 A/L Selvaraju Theeban Raju Bachelor of Commerce January 2015 A/P Balan Durgarani Bachelor of Commerce with Distinction March 2015 A/P Rajaram Koushalya Priya Bachelor of Commerce March 2015 Hiba Mohsin Mohammed Master of Health Leadership and Aal-Yaseen Hussein Management July 2015 Aamer Muhammad Master of Quality Management September 2015 Abbas Hanaa Safy Seyam Master of Business Administration with Distinction March 2015 Abbasi Muhammad Hamza Master of International Business March 2015 Abdallah AlMustafa Hussein Saad Elsayed Bachelor of Commerce March 2015 Abdallah Asma Samir Lutfi Master of Strategic Marketing September 2015 Abdallah Moh'd Jawdat Abdel Rahman Master of International Business July 2015 AbdelAaty Mosa Amany Abdelkader Saad Master of Media and Communications with Distinction March 2015 Abdel-Karim Mervat Graduate Diploma in TESOL July 2015 Abdelmalik Mark Maher Abdelmesseh Bachelor of Commerce March 2015 Master of Strategic Human Resource Abdelrahman Abdo Mohammed Talat Abdelziz Management September 2015 Graduate Certificate in Health and Abdel-Sayed Mario Physical Education July 2015 Sherif Ahmed Fathy AbdRabou Abdelmohsen Master of Strategic Marketing September 2015 Abdul Hakeem Siti Fatimah Binte Bachelor of Science January 2015 Abdul Haq Shaddad Yousef Ibrahim Master of Strategic Marketing March 2015 Abdul Rahman Al Jabier Bachelor of Engineering Honours Class II, Division 1 -

A Dictionary of Kristang (Malacca Creole Portuguese) with an English-Kristang Finderlist
A dictionary of Kristang (Malacca Creole Portuguese) with an English-Kristang finderlist PacificLinguistics REFERENCE COpy Not to be removed Baxter, A.N. and De Silva, P. A dictionary of Kristang (Malacca Creole Portuguese) English. PL-564, xxii + 151 pages. Pacific Linguistics, The Australian National University, 2005. DOI:10.15144/PL-564.cover ©2005 Pacific Linguistics and/or the author(s). Online edition licensed 2015 CC BY-SA 4.0, with permission of PL. A sealang.net/CRCL initiative. Pacific Linguistics 564 Pacific Linguistics is a publisher specialising in grammars and linguistic descriptions, dictionaries and other materials on languages of the Pacific, Taiwan, the Philippines, Indonesia, East Timor, southeast and south Asia, and Australia. Pacific Linguistics, established in 1963 through an initial grant from the Hunter Douglas Fund, is associated with the Research School of Pacific and Asian Studies at The Australian National University. The authors and editors of Pacific Linguistics publications are drawn from a wide range of institutions around the world. Publications are refereed by scholars with relevant expertise, who are usually not members of the editorial board. FOUNDING EDITOR: Stephen A. Wurm EDITORIAL BOARD: John Bowden, Malcolm Ross and Darrell Tryon (Managing Editors), I Wayan Arka, Bethwyn Evans, David Nash, Andrew Pawley, Paul Sidwell, Jane Simpson EDITORIAL ADVISORY BOARD: Karen Adams, Arizona State University Lillian Huang, National Taiwan Normal Peter Austin, School of Oriental and African University Studies -

Course Syllabus
DMA 325 EFP Videography (TTh 9:30am-12:00pm) Dr. George Vinovich, Professor & Chair, Digital Media Arts Office Hours: TTh 12-3pm in LCH A215 (310) 243-3945 [email protected] Mario Congreve, Lecturer, Digital Media Arts Office Hours: TTh 12-1pm in LIB B108 (310) 243-2053 Cell (310) 704-7635 [email protected] COURSE OBJECTIVE : Technical and theoretical aspects of shooting professional video on location using electronic field production techniques and equipment. Technical emphasis on proper staging, lighting, framing, shot composition, miking, and camera movement. Producer/director emphasis on oral “project pitch” presentation, pre-interviewing, script writing, location scouting, production filming, and post production editing. Each student co-producer team is required to pitch, write, film and edit a 5-10 minute Documentary Production according to the Documentary Project requirements. MATERIALS: (2) SDHC cards for camera original source footage Sony SDXC 64GB and final edited sequence (1) Stereo Headphones with 1/8” Mini Plug and 20ft Extension (For monitoring boom audio) (1) Solid State Drive (no rotational drives) 500mbps USB 3 (For backup and finishing room) (*) Food and beverages for talent and crew on location shoots, rehearsals, and casting sessions. COURSE CONTENT 1. Camera Systems - setup and operation of cinema camcorder system; use of various prime lenses for master shot, OS, and CU; use of neutral density filters for achieving shallow depth of field; use of scene files and other related camera menu variables to achieve various effects. 2. System Peripherals - setup and operation of system peripherals such as fluid head tripod, gimbal, dolly, crane, slider, battery packs, and chargers. -

Motion Tracking in Field Sports Using GPS And
Motion tracking in field sports using GPS and IMU M. Roobeek Master of Science Thesis Delft Center for Systems and Control Motion tracking in field sports using GPS and IMU Master of Science Thesis For the degree of Master of Science in Systems & Control at Delft University of Technology M. Roobeek February 16, 2017 Faculty of Mechanical, Maritime and Materials Engineering (3mE) · Delft University of Technology The work in this thesis was conducted on behalf of, and carried out in cooperation with JOHAN Sports. Their cooperation is hereby gratefully acknowledged. Copyright c Delft Center for Systems and Control (DCSC) All rights reserved. Abstract Injuries are a sportsman’s worst nightmare: They withhold players from playing, they weaken teams and they force clubs to buy a bench-full of substitutes. On top of that, injuries can cause an awful lot of pain. Regulating match and training intensity can drastically decrease the risk of getting injured. Furthermore, it can optimally prepare players for matchday. To enable player load regulation, accurate measurements of player positions, velocities and especially accelerations are required. To measure these quantities, JOHAN Sports develops a sports player motion tracking system. The device that is used for motion tracking contains a 9-DoF MEMS Inertial Measurement Unit (IMU) and a GPS receiver. These low-cost MEMS sensors are combined via sensor fusion. The challenge in this filtering problem lies in the limited and low-quality sensor measurements combined with the high-dynamic player motion consisting of rapid orientation changes and sensed impacts in every step. Being able to overcome these challenges paves the way for injury prevention, saving sports clubs, teams and players a lot of misery. -

Augmented and Virtual Reality in Operations
Augmented and Virtual Reality in Operations A guide for investment Introduction Augmented Reality and Virtual Reality (AR/VR) are not new, but recent advances in computational power, storage, graphics processing, and high-resolution displays have helped overcome some of the constraints that have stood in the way of the widespread use of these immersive technologies. Global spending on AR/VR is now expected to reach $17.8 billion in 2018, an increase of nearly 95% over the $9.1 billion estimate for 2017.1 Given this impetus, we wanted to understand more about the current state of play with AR/VR in the enterprise. We surveyed executives at 700+ companies, including 600 companies who are either experimenting with or implementing AR/VR; spoke with AR/VR-focused leadership at global companies, start-ups, and vendors; and analyzed over 35 use cases, with a particular focus on: • The use of AR/VR for internal industrial company operations, including, but not limited to, design, engineering, and field services • The automotive, utility, and discrete manufacturing sectors. This research focuses on organizations that have initiated their AR/VR journey, whether by experimentation or implementation, and aims to answer a number of questions: • How is AR/VR being used today? • Where should organizations invest – what are the use cases that generate the most value? • How can companies either begin or evolve their initiatives? Outside of this report, terms you will commonly find when reading about AR/VR are mixed reality, hybrid reality, or merged reality in which both the physical and the virtual or digital realities coexist or even merge. -

Efficient Camera Selection for Maximized Target Coverage In
. EFFICIENT CAMERA SELECTION FOR MAXIMIZED TARGET COVERAGE IN UNDERWATER ACOUSTIC SENSOR NETWORKS by Abdullah Albuali B.S., King Faisal University, 2009 A Thesis Submitted in Partial Fulfillment of the Requirements for the Master of Science Degree Department of Computer Science in the Graduate School Southern Illinois University Carbondale December 2014 THESIS APPROVAL EFFICIENT CAMERA SELECTION FOR MAXIMIZED TARGET COVERAGE IN UNDERWATER ACOUSTIC SENSOR NETWORKS By Abdullah Albuali A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science in the field of Computer Science Approved by: Kemal Akkaya, Chair Henry Hexmoor Michael Wainer Graduate School Southern Illinois University Carbondale October 31st, 2014 AN ABSTRACT OF THE THESIS OF ABDULLAH ALBUALI, for the Master of Science degree in Computer Science, presented on 31 October 2014, at Southern Illinois University Carbondale. TITLE: EFFICIENT CAMERA SELECTION FOR MAXIMIZED TARGET COVERAGE IN UNDERWATER ACOUSTIC SENSOR NETWORKS MAJOR PROFESSOR: Dr. Kemal Akkaya In Underwater Acoustic Sensor Networks (UWASNs), cameras have recently been deployed for enhanced monitoring. However, their use has faced several obstacles. Since video capturing and processing consume significant amounts of camera battery power, they are kept in sleep mode and activated only when ultrasonic sensors detect a target. The present study proposes a camera relocation structure in UWASNs to maximize the coverage of detected targets with the least possible vertical camera movement. This approach determines the coverage of each acoustic sensor in advance by getting the most applicable cameras in terms of orientation and frustum of camera in 3-D that are covered by such sensors. Whenever a target is exposed, this information is then used and shared with other sensors that detected the same target. -

The Incidental Learning of L2 Chinese Vocabulary Through Reading
Reading in a Foreign Language October 2020, Volume 32, No. 2 ISSN 1539-0578 pp. 169–193 The Incidental Learning of L2 Chinese Vocabulary through Reading Jing Zhou Pomona College United States Richard R. Day University of Hawai’i at Mānoa United States Abstract The study investigated the effect of marginal glossing and frequency of occurrence on the incidental learning of six aspects of vocabulary knowledge through reading in the second language (L2) Chinese. Participants were 30 intermediate L2 Chinese learners in an American public university. The MACOVA tests indicated that the treatment group who read with marginal glossing significantly outperformed (F = 6.686, p < 0.01) the control group who did not read with marginal glossing on six aspects of vocabulary knowledge after reading two stories. Significant differences were found on receptive word form, productive word form, receptive word meaning, and productive word grammatical function. The two-way ANOVA test suggested that the treatment group performed consistently better on learning words repeated three times and one time, and there was no interaction between the groups and the frequency of occurrence the words. The findings indicated that reading interesting and comprehensible Chinese stories can be beneficial for the learning of Chinese words. Keywords: L2 reading, marginal glossing, frequency of occurrence, incidental learning, receptive knowledge, productive knowledge, word form, word meaning, word grammatical function Vocabulary is one of the most important aspects of second or foreign language (L2) learning. However, the number of words needed to be learned to become proficient in the L2 is too large to learn through direct learning alone.