Topological Analysis of Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Part 2: Packet Transmission
Mesh networks LAN technologies and network topology • Early local networks used dedicated links between each pair of computers LANs and shared media • Some useful properties Locality of reference – hardware and frame details can be tailored for Star, bus and ring topologies each link Medium access control protocols – easy to enforce security and privacy Disadvantages of meshes Links between rooms/buildings • Poor scalability • Many links would follow the same physical path Shared Communication Channels Locality of reference • Shared LANs invented in the 1960s • LANs now connect more computers than any other form of network • Rely on computers sharing a single medium • The reason LANs are so popular is due to • Computers coordinate their access the principle of locality of reference • Low cost – physical locality of reference - computers more • But not suitable for wide area - likely to communicate with those nearby communication delays inhibit coordination – temporal locality of reference - computer is more likely to communicate with the same computers repeatedly 1 LAN topologies • LANs may be categorised according to topology ring bus star Pros and cons Example bus network: Ethernet • Star is more robust but hub may be a • Single coaxial cable - the ether - to which bottleneck computers connect • Ring enables easy coordination but is • IEEE standard specifies details sensitive to a cable being cut – data rates • Bus requires less wiring but is also sensitive – maximum length and minimum separation to a cable being cut – frame formats -

The Design of PROFIBUS-DP HUB Based on FPGA
International Conference on Computer Science and Service System (CSSS 2014) The Design of PROFIBUS-DP HUB based on FPGA Jiao Ping Zhou Tong Lab. of Networked Control Systems Lab. of Networked Control Systems Shenyang Institute of Automation (SIA), Chinese Shenyang Institute of Automation (SIA), Chinese Academy of Sciences China, Shenyang Academy of Sciences China, Shenyang [email protected] [email protected] Abstract—This paper analyzes the PROFIBUS-DP and specified the standard EIA RS-485, and the traffic rate is physical layer signals states, DP time series and other from 9.6kbps to 12Mbps [2, 3, 6]. characteristics. In the past, PROFIBUS-DP HUB common IEC 1158-2 specified the station number of problems of poor universal apply, shape communication is PROFIBUS-DP is 126 (station address from 0 to 125 contain more time-consuming, required message analysis, Drop frame master and slave station) [4]. In the one segment of etc, this paper propose a new design of PROFIBUS-DP HUB PROFIBUS-DP, the maximum station is 32. DP HUB or DP which based on FPGA. The design contain a detector which Repeater device requires the use, if want to connect more used to monitor the physical layer signal state of the DP bus, stations or change the network topology. As figure shown, use of FPGA synthesis logic signal, could control the direction DP HUB or DP Repeater divided the DP network into many of data flow in the physical layer, and Unrelated with the subnet segments [7]. Each interface of DP HUB is a upper layer protocol, without message analysis, compliance the protocol which used the standard RS-485, and Repeater, which can independently drive a PROFIBUS baudrate-adaptive. -

Field Networking Solutions
Field Networking Solutions Courtesy of Steven Engineering, Inc. ! 230 Ryan Way, South San Francisco, CA 94080-6370 ! Main Office: (650) 588-9200 ! Outside Local Area: (800) 258-9200 ! www.stevenengineering.com TYPES OF FIELDBUS NETWORKS* Field Networking 101 Features and Benefits of Fieldbus Networks The combination of intelligent field devices, digital bus networks, and various open communications protocols Fieldbus networks provide an array of features and benefits that make them an excellent choice is producing extraordinary results at process plants in nearly all process control environments. around the world. Compared to conventional technology, fieldbus networks deliver the following benefits: Just as our ability to retrieve, share, and analyze data Reduced field wiring costs has increased tremendously by use of the Internet and - Two wires from the control room to many devices PC network technology in our homes and at our desk- Reduced commissioning costs tops, so has our ability to control and manage our - Less time and personnel needed to perform process plants improved. Digital connectivity in process I/O wiring checkouts - No time spent calibrating intermediate signals manufacturing plants provides an infrastructure for the (such as 4-20mA signals) - Digital values are delivered directly from field flow of real-time data from the process level, making it devices, increasing accuracy available throughout our enterprise networks. This data Reduced engineering/operating costs is being used at all levels of the enterprise to provide - Much smaller space required for panels, I/O racks, and connectivity boxes increased process monitoring and control, inventory and - Fewer I/O cards and termination panels for materials planning, advanced diagnostics, maintenance control system equipment - Lower power consumption by control system planning, and asset management. -

Efficiently Triggering, Debugging and Decoding Low-Speed Serial Buses
Efficiently Triggering, Debugging and Decoding Low-Speed Serial Buses Hello, my name is Jerry Mark, I am a Product Marketing Engineer at Tektronix. The following presentation discusses aspects of embedded design techniques for “Efficiently Triggering, Debugging, and Decoding Low-Speed Serial Buses”. 1 Agenda Introduction – Parallel Interconnects – Transition from Parallel to Serial Buses – High-Speed versus Low-Speed Serial Data Buses Low-Speed Serial Data Buses – Challenges – Technology Reviews – Measurement Solutions Summary 2 In this presentation we will begin by taking a glance at the transition from parallel-to-serial data and the challenges this presents to engineers. Then we will briefly review some of the most widely used low-speed serial buses in industry today and some of their key characteristics. We will turn our attention to the key measurements on these buses. Subsequently, we will present by example how the low-speed serial solution from Tektronix addresses these challenges. 2 Parallel Interconnects Traditional way to connect digital devices used parallel buses Advantages – Simple point-to-point connections – All signals are transmitted in parallel, simultaneously – Easy to capture state of bus (if you have enough channels!) – Decoding the bus is relatively easy Disadvantages – Occupies a lot of circuit board space – All high-speed connections must be the same length – Many connections limit reliability – Connectors may be very large 3 Parallel buses present all of the bits in parallel, as shown in the logic analyzer display. A parallel connection between two ICs can be as simple as point-to-point circuit board traces for each of the data lines. If you can physically probe these lines, it is easy to display the bus state on a logic analyzer or mixed signal oscilloscope. -

Comparison of Network Topologies for Optical Fiber Communication
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 10, December- 2012 Comparison Of Network Topologies For Optical Fiber Communication Mr. Bhupesh Bhatia Ms. Ashima Bhatnagar Bhatia Department of Electronics and Communication, Department of Computer Science, Guru Prem Sukh Memorial College of Engineering, Tecnia Institute of Advanced Studies, Delhi Delhi Ms. Rashmi Ishrawat Department of Computer Science, Tecnia Institute of Advanced Studies, Delhi Abstract advent of the Information age. Optical In this paper, the various network topologies technologies can cost effectively meet have been compared. The signal is analyzed as it corporate bandwidth needs today and passes through each node in each of the network tomorrow. Internet connections offering topology. There is no appreciable signal degradation in the ring network. Also there is bandwidth on demand, to fiber on the increase in Quality factor i.e. signal keeps on LAN. Fiber to the home can provide true improving as it passes through the successiveIJERT IJERTbroadband connectivity for nodes. For the bus topology, the quality of signal telecommuters as well as converged goes on decreasing with increase in the number multimedia offerings for consumers [2]. of nodes and the power penalty goes on increasing. For the star topology, it is observed These different communication networks that received power values of each node at a can be configured in a number of same distance from the hub are same and the topologies. These include a bus, with or performance is same. For the tree topology, it is without a backbone, a star network, a observed that the performance is almost identical ring network, which can be redundant to the performance of ring topology, as signal quality is improved as it passes through the and/ or self-healing, or some successive nodes of the hierarchy. -
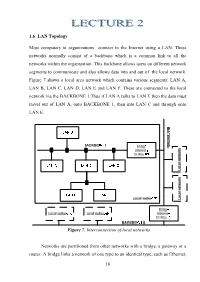
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges. -

Real-Time Communication Protocols: an Overview∗
Real-time communication protocols: an overview∗ Ferdy Hanssen and Pierre G. Jansen October 2003 Abstract This paper describes several existing data link layer protocols that provide real-time capabilities on wired networks, focusing on token-ring and Carrier Sense Multiple Access based networks. Existing modifications to provide better real-time capabilities and performance are also described. Finally the pros and cons regarding the At-Home Anywhere project are discussed. 1 Introduction In the past twenty-five years several different, wired networks have been designed and built. But not all of them are dependable, i.e. suitable for accomodating real-time traffic, or traffic with Quality of Service (QoS) requirements. Some were designed with QoS in mind, some had QoS added as an after-thought, and some do not support QoS requirements at all. The most popular wired network architecture used to date, IEEE 802.3 [46], pop- ularly called Ethernet1, does not provide any support for real-time traffic. There are no provisions to reserve bandwidth for a certain connection. Nodes access the network using the CSMA/CD (Carrier Sense Multiple Access with Collision Detect) technique [70]. The CSMA/CD algorithm does not define a collision resolvance protocol of its own. Ethernet uses the BEB (Binary Exponential Back-Off) algo- rithm. This algorithm resolves collisions in a non-deterministic manner, while the first requirement for a network to be called real-time is determinism. The most popular real-time network architecture, Asynchronous Transfer Mode (ATM), is used mostly for internetwork links these days. ATM provides high band- widths and QoS guarantees, but has proven to be too expensive for use as a lo- cal area network. -

COSC460 Report: Medium Access Control Protocols for WDM Optical Networks
COSC460 Report: Medium access control protocols for WDM optical networks November 6, 2001 Robert Mollard Associate Prof. K. Pawlikowski1 1Supervisor Abstract Wavelength-division multiplexing (WDM) has emerged as the most popular technology for utilising the huge bandwidth of optical fibre. This paper surveys medium access control protocols for the star, bus and ring WDM network topologies. The performance of two recently developed protocols, Pipelining Cyclic Scheduling Algorithm (PCSA) and Reservation/ACK/Transmission Protocol (RATP), is evaluated by stochastic simulation. It was found that RATP’s performance (measured by throughput and de- lay) degrades sharply with the increase in network size, making it impractical for use in metropolitan- or wide-area networks. PCSA does not suffer from this restriction, and can realise a throughput of 1. It also delivers short average packet delays, especially under light to moderate system loads. Keywords: Optical networks, wavelength division multiplexing, medium access control. Contents 1 Introduction 4 1.1Reportstructure........................... 5 2 Exploiting optical bandwidth 6 2.1 Time-division and Code-division multiplexing . 6 2.2 Wavelength-division multiplexing . 7 2.2.1 WDMnetworkclassification................. 7 3 Medium access control protocols 9 4 Previous Work 11 4.1 Indulska and Richards . 11 4.2Montgomery.............................. 11 4.3Li,MaodeandHamdi........................ 11 5 Star Topology 12 5.1Demonstrators............................ 13 5.2MACprotocols............................ 13 5.2.1 AlohaandSlottedAloha.................. 15 5.2.2 I-SA.............................. 15 5.2.3 I-SA*............................. 15 5.2.4 I-TDMA............................ 16 5.2.5 I-TDMA*........................... 16 5.2.6 TDMA-C........................... 16 5.2.7 DT-WDMA.......................... 16 5.2.8 Conflict-free DT-WDMA . -

Chapter 6 Medium Access Control Protocols and Local Area Networks
Chapter 6 Medium Access Control Protocols and Local Area Networks Part I: Medium Access Control Part II: Local Area Networks Chapter Overview l Broadcast Networks l Medium Access Control l All information sent to all l To coordinate access to users shared medium l No routing l Data link layer since direct l Shared media transfer of frames l Radio l Local Area Networks l Cellular telephony l High-speed, low-cost l Wireless LANs communications between co-located computers l Copper & Optical l Typically based on l Ethernet LANs broadcast networks l Cable Modem Access l Simple & cheap l Limited number of users Chapter 6 Medium Access Control Protocols and Local Area Networks Part I: Medium Access Control Multiple Access Communications Random Access Scheduling Channelization Delay Performance Chapter 6 Medium Access Control Protocols and Local Area Networks Part II: Local Area Networks Overview of LANs Ethernet Token Ring and FDDI 802.11 Wireless LAN LAN Bridges Chapter 6 Medium Access Control Protocols and Local Area Networks Multiple Access Communications Multiple Access Communications l Shared media basis for broadcast networks l Inexpensive: radio over air; copper or coaxial cable l M users communicate by broadcasting into medium l Key issue: How to share the medium? 3 2 4 1 Shared multiple access medium M 5 … Approaches to Media Sharing Medium sharing techniques Static Dynamic medium channelization access control l Partition medium Scheduling Random access l Dedicated allocation to users l Polling: take turns l Loose l Satellite l Request -

Comparison of Network Topology Types in Communication Systems and Computer Networks 1404703
Alexandria University Institute of Graduate Studies and Research Department of Information Technology M.Sc. program in Information Technology 2020 Assignment (1) of Comparison of network topology types in Communication Systems and Computer Networks 1404703 Supervisor Prof. Shawkat K. Guirguis Name: Israa Faisal Jassam ID: 1404-3-160 1 1. Introduction 1.1 Network topologies: It is the schematic description of a network arrangement, connecting various nodes (sender and receiver) through lines of connection. There are two types of network topologies: physical and logical. Physical topology confirms the physical layout of the connected devices and nodes, while the logical topology focuses on the pattern of data transfer between network nodes. 1.1.1 Physical topology: refers to the interconnected structure of a local area network (LAN). The method employed to connect the physical devices on the network with the cables, and the type of cabling used, all constitute the physical topology. Physical topology is further divided into two sections, Point-to-point connections and Multipoint connections. point-to-point connection: a communication link is established between two devices with one wire. A simple example of point-to-point connection is talking over telephone between two persons where anyone else is not allowed to use the phone on either side (Fig.1). Fig.1: multipoint connection: is a connection established between more than two devices. In multipoint connection, a single link is shared by multiple devices. So, it can be said that the channel capacity is shared temporarily by every device connecting to the link. If devices are using the link turn by turn, then it is said to be time shared line configuration. -

Media Access Control (MAC) (With Some IEEE 802 Standards)
Department of Computer and IT Engineering University of Kurdistan Computer Networks I Media Access Control (MAC) (with some IEEE 802 standards) By: Dr. Alireza Abdollahpouri Media Access Control Multiple access links There is ‘ collision ’ if more than one node sends at the same time only one node can send successfully at a time 2 Media Access Control • When a "collision" occurs, the signals will get distorted and the frame will be lost the link bandwidth is wasted during collision • Question: How to coordinate the access of multiple sending and receiving nodes to the shared link ? • Solution: We need a protocol to determine how nodes share channel Medium Access control (MAC) protocol • The main task of a MAC protocol is to minimize collisions in order to utilize the bandwidth by: - Determining when a node can use the link (medium) - What a node should do when the link is busy - What the node should do when it is involved in collision 3 Ideal Multiple Access Protocol 1. When one node wants to transmit, it can send at rate R bps, where R is the channel rate. 2. When M nodes want to transmit, each can send at average rate R/M (fair) 3. fully decentralized: - No special node to coordinate transmissions - No synchronization of clocks, slots 4. Simple Does not exist!! 4 Three Ways to Share the Media Channel partitioning MAC protocols: • Share channel efficiently and fairly at high load • Inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! “Taking turns” protocols • Eliminates empty slots without -

Hardware Architectures
Hardware Architectures Parallel Programming 2020-11-10 Jun.-Prof. Dr. Michael Kuhn [email protected] Parallel Computing and I/O Institute for Intelligent Cooperating Systems Faculty of Computer Science Otto von Guericke University Magdeburg https://parcio.ovgu.de Outline Review Hardware Architectures Review Introduction Classification Memory Access Models Network Summary Michael Kuhn Hardware Architectures 1/43 Performance Analysis and Optimization Review • Why should performance measurements be repeated? 1. Warm up the hardware 2. Eliminate random errors 3. Eliminate systematic errors 4. Increase measurement time Michael Kuhn Hardware Architectures 2/43 Performance Analysis and Optimization Review • What does memory-bound stand for? 1. Performance is limited by processor throughput 2. Application does not have enough main memory 3. Data cannot be moved in main memory 4. Performance is limited by memory throughput Michael Kuhn Hardware Architectures 2/43 Performance Analysis and Optimization Review • Why are caches important? 1. Decrease latency of memory accesses 2. Increase size of main memory 3. Reduce power consumption of memory accesses 4. Increase throughput of main memory Michael Kuhn Hardware Architectures 2/43 Performance Analysis and Optimization Review • Which is the best performance metric? 1. Runtime 2. Utilization 3. FLOPS 4. FLOPS per watt Michael Kuhn Hardware Architectures 2/43 Outline Introduction Hardware Architectures Review Introduction Classification Memory Access Models Network Summary Michael Kuhn Hardware Architectures