Understanding Local Area Networking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Expand and Enhance Your Home Network with Gigabit Powerline
Expand and Enhance Your Home Network with Gigabit Powerline • The HomePlug AV2 standard creates The ZyXEL PLA5405 1200 Mbps Powerline Gigabit Ethernet Adapter is based on the latest powerline networks with data HomePlug AV2 standard and features data transfer rates of up to 1200 Mbps*. The Powerline transfer rates of up to 1200 Mbps* adapter plugs into an existing power outlet and instantly enables high-speed network access • Enjoy high-speed networking through a home’s electrical lines. The device offers a perfect solution for streaming HD movies, and complete coverage through playing online games and enjoying other network-intensive applications—all without the hassle of Line-Natural/Line-Ground MIMO** installing cables throughout the residence. Featuring the latest HomePlug AV2 MIMO** technology, technology the PLA5405 utilizes multiple lines from your home’s existing electrical wiring, whereas non-MIMO • No extra wires or configuration based HomePlug AV technology uses a single line. This enables the PLA5405 adapter to perform at required up to twice the speed of existing 600 Mbps* Powerline products. • Perfect for connecting smart TVs and playing online games Benefits • QoS enhances media streaming Enjoy high-speed networking and increased coverage through MIMO quality capabilities** • Single push-and-secure button for With advanced HomePlug AV2 technology, the ZyXEL PLA5405 provides users with steady, high-speed easy security setup data transfer rates of up to 1200 Mbps* and is backward compatible with HomePlug AV and IEEE • Compliant with IEEE 1901 and 1901-based products. The new HomePlug AV2 Multiple Input Multiple Output (MIMO) feature increases HomePlug AV technology throughput and coverage. -

Life Cycle of Municipal Wi-Fi
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Tseng, Chien-Kai; Huang, Kuang-Chiu Conference Paper Life Cycle of Municipal Wi-Fi 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017 Provided in Cooperation with: International Telecommunications Society (ITS) Suggested Citation: Tseng, Chien-Kai; Huang, Kuang-Chiu (2017) : Life Cycle of Municipal Wi- Fi, 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017, International Telecommunications Society (ITS), Calgary This Version is available at: http://hdl.handle.net/10419/168493 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. -

Lab Report: 2.1.3 Connect to an Ethernet Network
Lab Report: 2.1.3 Connect to an Ethernet Network Performance Your Score: 0 of 2 (0%) Elapsed Time: 9 seconds Task Summary Actions you were required to perform: In In Office 1, connect the twisted pair cable between the workstation and the wall plate In In Office 1, confirm that the workstation has a connection to the local network and the Internet Explanation To complete this lab, use twisted pair cable with RJ45 connectors to connect to a wired Ethernet network. RJ45 connectors have eight wires (as seen below) and are larger than RJ11 connectors. Complete the following steps: 1. Under Office 1, select Hardware to go to the workstation. 2. Above the computer, select Back to switch to the back view of the computer. 3. On the Shelf, expand the Cables category. 4. Select the RJ45 cable. 5. In the Selected Component window, drag and drop the connector to the Ethernet port on the computer. 6. In the Selected Component window, drag the other connector to the Ethernet port on the wall outlet. 7. Select Click to view Windows 10 on the monitor to confirm that the workstation has a connection to the local network and the internet. 8. In the notification area, right-click the Network icon and select Open Network and Sharing Center. The diagram should indicate an active connection to the network and the internet. Lab Report: 2.2.3 Connect a Cable Modem Performance Your Score: 0 of 4 (0%) Elapsed Time: 6 seconds Task Summary Actions you were required to perform: In Connect the cable modem to the Internet using the RG-6 cable In Connect the computer to the cable modem using the Ethernet cable In Plug in the cable modem In Confirm that the computer is properly connected to the Internet Explanation In this lab, your task is to complete the following: Connect the components to make the internet connection. -

Approved Modem List
Approved Modem List Internet Only Cable Modems* SMC Networks D3CM1604 This broadband modem supports downstream speeds up to 640Mbps and 120Mbps on the upstream. The extreme speed allows faster streaming HD videos, file downloads and high-speed gaming. The D3CM1604 is the ideal solution for your house or small home business. hitron CDA3-35 The CDA3-35 is the perfect choice for cable operators who want to offer high-speed broadband access to their customer base economically. It delivers speeds of up to 1.2Gbps (32×8) with thirty-two bonded downstream channels over its DOCSIS interface. Arris CM3200 The CM3200 is well-suited to the home user – offering the speeds to stream multimedia content to multiple devices and the responsiveness to keep you “in the game” for online gaming. However, the CM3200 is also a serious commercial solution, ready to meet the challenging demands of small business. Cable Modems with WIFI* Arris SURFboard® Modem & Wi-F® Router SBG6580 High-speed Internet and Wireless N at your fingertips. The SURFboard SBG6580 Wi-Fi Cable Modem is 3 products in one device: DOCSIS 3.0 Cable Modem, Dual-Band 802.11n Wi-Fi Access Point and 4-port Gigabit Ethernet Router. Arris DG2470 Wireless Gateway The Touchstone DG2470 is a DOCSIS3.0 home data gateway supporting 24 x 8 channel bonding for up to 960Mbps of broadband data. It combines a 4-port gigabit router, MoCA 2.0 over coax, and a dual band 802.11ac wireless access point. Arris TG2472 Wireless Gateway The Touchstone TG2472 is a DOCSIS3.0 home telephony gateway supporting 24 x 8 channel bonding for up to 960Mbps of broadband data. -

Best Practices for Keeping Your Home Network Secure1
BEST PRACTICES FOR KEEPING YOUR HOME 1 NETWORK SECURE Don't be a victim; cyber criminals may leverage your home network to gain access to personal, private, and confidential information. Help protect yourself and your family by observing some basic guidelines and implementing the following mitigations on your home network. COMPUTING AND ENTERTAINMENT DEVICE RECOMMENDATIONS Electronic computing devices including computers, laptops, printers, mobile phones, tablets, security cameras, home appliances, cars and other “Internet of Things” devices must all be secured in order to prevent attack. Most home entertainment and utility devices, such as home monitoring systems, baby monitors, Internet of Things (IoT), Smart Devices, Blu-ray™2 players, streaming video players, and video game consoles are capable of accessing the Internet, recording audio, and/or capturing video. Implemented security measures can ensure these devices don’t become the weak link in your home protection. 1. Upgrade to a Modern Operating System and Keep it Up-To-Date The most recent version of any operating system (OS) inevitably contains security features not found in previous versions. Many of these security features are enabled by default and help prevent common attack vectors. Increase the difficulty for an adversary to gain privileged access by utilizing the latest available and supported OS for desktops, laptops, and other devices. Enable automatic update functionality inside the OS. If automatic updates are not possible, download and install patches and updates from a trusted vendor minimally on a monthly basis. 2. Exercise Secure User Habits To minimize ransomware threat, backup data on external drives and portable media. Disconnect external storage when not in use. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

The Future of Personal Area Networks in a Ubiquitous Computing World
Copyright is owned by the Author of the thesis. Permission is given for a copy to be downloaded by an individual for the purpose of research and private study only. The thesis may not be reproduced elsewhere without the permission of the Author. The Future of Personal Area Networks in a Ubiquitous Computing World A thesis presented in partial fulfillment of the requirements for the degree of Master of Information Sciences in Information Systems at Massey University, Auckland New Zealand Fei Zhao 2008 ABSTRACT In the future world of ubiquitous computing, wireless devices will be everywhere. Personal area networks (PANs), networks that facilitate communications between devices within a short range, will be used to send and receive data and commands that fulfill an individual’s needs. This research determines the future prospects of PANs by examining success criteria, application areas and barriers/challenges. An initial set of issues in each of these three areas is identified from the literature. The Delphi Method is used to determine what experts believe what are the most important success criteria, application areas and barriers/challenges. Critical success factors that will determine the future of personal area networks include reliability of connections, interoperability, and usability. Key application areas include monitoring, healthcare, and smart things. Important barriers and challenges facing the deployment of PAN are security, interference and coexistence, and regulation and standards. i ACKNOWLEDGEMENTS Firstly, I would like to take this opportunity to express my sincere gratitude to my supervisor – Associate Professor Dennis Viehland, for all his support and guidance during this research. Without his advice and knowledge, I would not have completed this research. -

Computer Networking 101 (HH – Rev1)
Computer Networking 101 (HH – rev1) Henrietta Hankin Library 215 Windgate Drive Chester Springs, PA 19425 Phone: (610) 321-1700 [email protected] www.ccls.org/hankin https://www.facebook.com/HankinBranchLibrary Computer Networking 101 Page 1 Computer Networking 101 (HH – rev1) Workshop Topics: Fundamentals Network Protocols Home Network Components Diagnostics Outline of Workshop: 1. Fundamentals a. What is a computer network? b. Local Area Networks (LANs) c. Wide Area Networks (WANs) d. Virtual Private Network (VPN – AKA Tunneling) e. The Internet f. Peer-to-Peer Networks g. Server-based Networks h. Wireless Local Area Networks (WLANs) 2. Network Protocols a. TCP/IP b. Ethernet c. Ethernet Standards (802.3, 10BaseT, 100BaseT) d. Wireless Protocols (802.11xxx) 3. Home Network Components - Hardware a. PC/Laptop with Network interface Card (NIC) b. Cable Modem c. Router, Switch, Hub d. LAN Cabling e. Network Printer 4. Home Network Components – Software a. Peer-to-peer b. Domain Name Server (DNS) c. Dynamic Host Configuration Protocol (DHCP) d. Firewall 5. Network Diagnostics a. ipconfig command b. ping command c. Command to identify all active network components d. Wireshark Page 2 Computer Networking 101 (HH – rev1) Fundamentals What is a computer network? A computer network consists of a collection of computers, printers and other devices that are connected together so that they can talk to each other. Local Area Networks (LANs), Wide Area Networks (WANs) and Virtual Private Networks (VPNs) are all examples of computer networks. Local Area Networks (LANs) LANs connect computers and other devices that are located physically close to each other. A computer network in a house or office is an example of a LAN. -

Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN
DOI : https://dx.doi.org/10.26808/rs.re.v4i1.02 International Journal of Research in Engineering & Science ISSN:(P) 2572-4274 (O) 2572-4304 Available online on http://rspublication.com/IJRES/IJRE.html volume 4 Issue 1 Jan.-Feb 2020 Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN S.N. Arinze, G.N. Onoh and D.O. Abonyi Abstract Wireless Fidelity utilizes radio waves. Radio waves have limited bandwidth, fully exploited, and low speed. Light fidelity is a visible light communication used as a medium to carry high-speed data. It can complement the wireless fidelity in accessing the internet, thereby reducing congestion. In this work, a hybrid of light fidelity and wireless fidelity was carried out in an indoor environment. The geometry of the light fidelity access point and wireless fidelity access point was analyzed in the MatLab environment to know the highest power received by the user. Some ranges of received power considered for good reception wereassigned for each of the wireless access points in the MatLab program. Visual Basic, an object-oriented computer programming language, reads the signal coming from the communication port of light fidelity and wireless fidelity. It mimics the analyzed MatLab program of a hybrid network of light fidelity and wireless fidelity and connects to any of the wireless access points based on the set conditions of the satisfied received power. With these, the light fidelity can complement the limited available radio frequency. Index Terms—Light Fidelity, MatLab, Visual Basic, Wireless Fidelity. I. INTRODUCTION Wireless Fidelity network allows more than one device to communicate and share information within defined regions like office, home, and campus. -
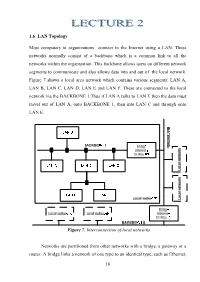
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges. -

Home Network System FAQ 20170202
FAQ Home Network System As of February 2, 2017 FAQ for quick setup and easier use - Index STEP 1 Open the package and confirm the accessories Accessories Page 2-5 Basic Concept Page 7-11 & Operation STEP 2 Set up main unit (Hub) System Initial Setup Page 12-14 STEP 3 Install the Home Network app. Application Page 15-18 STEP 4 Make sure your mobile device is connected to Application Page 15-18 your Wi-Fi® network. STEP 5 Cordless Handset Page 19-28 Set up accessories HUB Page 29-33 Indoor Camera Page 34-41 Outdoor Camera Page 42-49 Motion Sensor Page 50-53 Window / Door Sensor Page 54-56 Water Leak Sensor Page 57 Class Break Sensor Page 58 Indoor Siren Page 59 Access Keypad Page 60 Keychain Remote Page 61 Backup Battery Page 62 Smart Plug Page 63-64 Full HD Camera Page 65-67 1 Accessories - What are the accessories for? HUB (KX-HNB600) Indoor Camera (KX-HNC200/210) • Full color camera with night vision and built-in microphone • Joins all system devices together for live monitoring and recording • Connects to your landline for making and receiving calls • Built-in motion sensor (visual detection), sound sensor, • Supports SD card connection for recording camera video and temperature sensor can be used to trigger other and audio. actions (camera recording, turning on a light, etc.) • Built-in microphone and speaker for two-way communication Outdoor Camera (KX-HNC600) Window / Door Sensor (KX-HNS101) • Full color camera with night vision and built-in microphone for live monitoring and recording • Detects when the corresponding window or door is • Built-in motion sensor (visual detection), sound opened.