Chapter 6 Medium Access Control Protocols and Local Area Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Logical Link Control and Channel Scheduling for Multichannel Underwater Sensor Networks
ICST Transactions on Mobile Communications and Applications Research Article Logical Link Control and Channel Scheduling for Multichannel Underwater Sensor Networks Jun Li ∗, Mylene` Toulgoat, Yifeng Zhou, and Louise Lamont Communications Research Centre Canada, 3701 Carling Avenue, Ottawa, ON. K2H 8S2 Canada Abstract With recent developments in terrestrial wireless networks and advances in acoustic communications, multichannel technologies have been proposed to be used in underwater networks to increase data transmission rate over bandwidth-limited underwater channels. Due to high bit error rates in underwater networks, an efficient error control technique is critical in the logical link control (LLC) sublayer to establish reliable data communications over intrinsically unreliable underwater channels. In this paper, we propose a novel protocol stack architecture featuring cross-layer design of LLC sublayer and more efficient packet- to-channel scheduling for multichannel underwater sensor networks. In the proposed stack architecture, a selective-repeat automatic repeat request (SR-ARQ) based error control protocol is combined with a dynamic channel scheduling policy at the LLC sublayer. The dynamic channel scheduling policy uses the channel state information provided via cross-layer design. It is demonstrated that the proposed protocol stack architecture leads to more efficient transmission of multiple packets over parallel channels. Simulation studies are conducted to evaluate the packet delay performance of the proposed cross-layer protocol stack architecture with two different scheduling policies: the proposed dynamic channel scheduling and a static channel scheduling. Simulation results show that the dynamic channel scheduling used in the cross-layer protocol stack outperforms the static channel scheduling. It is observed that, when the dynamic channel scheduling is used, the number of parallel channels has only an insignificant impact on the average packet delay. -

MAC Protocols for IEEE 802.11Ax: Avoiding Collisions on Dense Networks Rafael A
MAC Protocols for IEEE 802.11ax: Avoiding Collisions on Dense Networks Rafael A. da Silva1 and Michele Nogueira1;2 1Department of Informatics, Federal University of Parana,´ Curitiba, PR, Brazil 2Electrical and Computer Engineering, Carnegie Mellon University, Pittsburgh, PA, USA E-mails: [email protected] and [email protected] Wireless networks have become the main form of Internet access. Statistics show that the global mobile Internet penetration should exceed 70% until 2019. Wi-Fi is an important player in this change. Founded on IEEE 802.11, this technology has a crucial impact in how we share broadband access both in domestic and corporate networks. However, recent works have indicated performance issues in Wi-Fi networks, mainly when they have been deployed without planning and under high user density. Hence, different collision avoidance techniques and Medium Access Control protocols have been designed in order to improve Wi-Fi performance. Analyzing the collision problem, this work strengthens the claims found in the literature about the low Wi-Fi performance under dense scenarios. Then, in particular, this article overviews the MAC protocols used in the IEEE 802.11 standard and discusses solutions to mitigate collisions. Finally, it contributes presenting future trends arXiv:1611.06609v1 [cs.NI] 20 Nov 2016 in MAC protocols. This assists in foreseeing expected improvements for the next generation of Wi-Fi devices. I. INTRODUCTION Statistics show that wireless networks have become the main form of Internet access with an expected global mobile Internet penetration exceeding 70% until 2019 [1]. Wi-Fi Notice: This work has been submitted to the IEEE for possible publication. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Migrating Backoff to the Frequency Domain
No Time to Countdown: Migrating Backoff to the Frequency Domain Souvik Sen Romit Roy Choudhury Srihari Nelakuditi Duke University Duke University University of South Carolina Durham, NC, USA Durham, NC, USA Columbia, SC, USA [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION Conventional WiFi networks perform channel contention in Access control strategies are designed to arbitrate how mul- time domain. This is known to be wasteful because the chan- tiple entities access a shared resource. Several distributed nel is forced to remain idle while all contending nodes are protocols embrace randomization to achieve arbitration. In backing off for multiple time slots. This paper proposes to WiFi networks, for example, each participating node picks a break away from convention and recreate the backing off op- random number from a specified range and begins counting eration in the frequency domain. Our basic idea leverages the down. The node that finishes first, say N1, wins channel con- observation that OFDM subcarriers can be treated as integer tention and begins transmission. The other nodes freeze their numbers. Thus, instead of picking a random backoff duration countdown temporarily, and revive it only after N1’s trans- in time, a contending node can signal on a randomly cho- mission is complete. Since every node counts down at the sen subcarrier. By employing a second antenna to listen to same pace, this scheme produces an implicit ordering among all the subcarriers, each node can determine whether its cho- nodes. Put differently, the node that picks the smallest ran- sen integer (or subcarrier) is the smallest among all others. -

Collision Detection
Computer Networking Michaelmas/Lent Term M/W/F 11:00-12:00 LT1 in Gates Building Slide Set 3 Evangelia Kalyvianaki [email protected] 2017-2018 1 Topic 3: The Data Link Layer Our goals: • understand principles behind data link layer services: (these are methods & mechanisms in your networking toolbox) – error detection, correction – sharing a broadcast channel: multiple access – link layer addressing – reliable data transfer, flow control • instantiation and implementation of various link layer technologies – Wired Ethernet (aka 802.3) – Wireless Ethernet (aka 802.11 WiFi) • Algorithms – Binary Exponential Backoff – Spanning Tree 2 Link Layer: Introduction Some terminology: • hosts and routers are nodes • communication channels that connect adjacent nodes along communication path are links – wired links – wireless links – LANs • layer-2 packet is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 3 Link Layer (Channel) Services • framing, physical addressing: – encapsulate datagram into frame, adding header, trailer – channel access if shared medium – “MAC” addresses used in frame headers to identify source, dest • different from IP address! • reliable delivery between adjacent nodes – we see some of this again in the Transport Topic – seldom used on low bit-error link (fiber, some twisted pair) – wireless links: high error rates 4 Link Layer (Channel) Services - 2 • flow control: – pacing between adjacent sending and receiving nodes • error control: – error -

GS970M Datasheet
Switches | Product Information CentreCOM® GS970M Series Managed Gigabit Ethernet Switches The Allied Telesis CentreCOM GS970M Series of Layer 3 Gigabit switches offer an impressive set of features in a compact design, making them ideal for applications at the network edge. STP root guard ۼۼ Overview Management (UniDirectional Link Detection (UDLD ۼۼ Allied Telesis Autonomous Management ۼۼ Allied Telesis CentreCOM GS970M Series switches provide an excellent Framework™ (AMF) enables powerful centralized management and zerotouch device installation and Security Features access solution for today’s networks, recovery Access Control Lists (ACLs) based on Layer 2, 3 ۼۼ supporting Gigabit to the desktop for Console management port on the front panel for and 4 headers ۼۼ maximum performance. The Power ease of access Configurable auth-fail and guest VLANs ۼۼ Eco-friendly mode allows ports and LEDs to be ۼۼ over Ethernet Plus (PoE+) models Authentication, Authorization, and Accounting ۼۼ provide an ideal solution for connecting disabled to save power (AAA) Industry-standard CLI with context-sensitive help ۼ and remotely powering wireless access ۼ ۼ Bootloader can be password protected for device ۼ ,points, IP video surveillance cameras Powerful CLI scripting engine security ۼۼ ۼ and IP phones. The GS970M models BPDU protection ۼۼ -Comprehensive SNMP MIB support for standards ۼ feature 8, 16 or 24 Gigabit ports, based device management ۼ DHCP snooping, IP source guard and Dynamic ARP ۼ and 2 or 4 SFP uplinks, for secure (Built-in text editor Inspection -

Communications Programming Concepts
AIX Version 7.1 Communications Programming Concepts IBM Note Before using this information and the product it supports, read the information in “Notices” on page 323 . This edition applies to AIX Version 7.1 and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2010, 2014. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this document............................................................................................vii How to use this document..........................................................................................................................vii Highlighting.................................................................................................................................................vii Case-sensitivity in AIX................................................................................................................................vii ISO 9000.....................................................................................................................................................vii Communication Programming Concepts................................................................. 1 Data Link Control..........................................................................................................................................1 Generic Data Link Control Environment Overview............................................................................... -

Ts 138 321 V15.3.0 (2018-09)
ETSI TS 138 321 V15.3.0 (2018-09) TECHNICAL SPECIFICATION 5G; NR; Medium Access Control (MAC) protocol specification (3GPP TS 38.321 version 15.3.0 Release 15) 3GPP TS 38.321 version 15.3.0 Release 15 1 ETSI TS 138 321 V15.3.0 (2018-09) Reference RTS/TSGR-0238321vf30 Keywords 5G ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -

Tutorial on Network Communications and Security
Lecture Notes Introduction to Digital Networks and Security Raj Bridgelall, PhD © Raj Bridgelall, PhD (North Dakota State University, College of Business) Page 1/23 Table of Contents PART I – NETWORKING CONCEPTS.....................................................................................4 1 INTRODUCTION..................................................................................................................4 2 DATA COMMUNICATIONS ..............................................................................................4 2.1 THE OSI MODEL ...............................................................................................................4 2.2 NETWORKING DEVICES .....................................................................................................5 2.3 TCP/IP ..............................................................................................................................6 3 MOBILE IP ............................................................................................................................7 3.1 FIREWALLS........................................................................................................................9 3.2 DHCP AND DNS ..............................................................................................................9 3.3 IPV6 ................................................................................................................................10 PART II – CRYPTOGRAPHY AND NETWORK SECURITY .............................................12 -

How Computers Share Data
06 6086 ch03 4/6/04 2:51 PM Page 41 HOUR 3 Getting Data from Here to There: How Computers Share Data In this hour, we will first discuss four common logi- cal topologies, starting with the most common and ending with the most esoteric: . Ethernet . Token Ring . FDDI . ATM In the preceding hour, you read a brief definition of packet-switching and an expla- nation of why packet switching is so important to data networking. In this hour, you learn more about how networks pass data between computers. This process will be discussed from two separate vantage points: logical topologies, such as ethernet, token ring, and ATM; and network protocols, which we have not yet discussed. Why is packet switching so important? Recall that it enables multiple computers to send multiple messages down a single piece of wire, a technical choice that is both efficient and an elegant solution. Packet switching is intrinsic to computer network- ing—without packet switching, no network. In the first hour, you learned about the physical layouts of networks, such as star, bus, and ring technologies, which create the highways over which data travels. In the next hour, you learn about these topologies in more depth. But before we get to them, you have to know the rules of the road that determine how data travels over a network. In this hour, then, we’ll review logical topologies. 06 6086 ch03 4/6/04 2:51 PM Page 42 42 Hour 3 Logical Topologies Before discussing topologies again, let’s revisit the definition of a topology. -

Listen Before You Talk but on the Frequency Domain
1 Listen Before You Talk But On The Frequency Domain Souvik Sen Romit Roy Choudhury Srihari Nelakuditi Duke University Duke University University of South Carolina Abstract Access control strategies are designed to arbitrate how multiple entities access a shared resource. Several dis- tributed protocols embrace randomization to achieve arbitration. In WiFi networks, for example, each participating node picks a random number from a specified range and begins counting down. The device that reaches zero first wins the contention and initiates transmission. This core idea – called backoff – is known to be inherently wasteful because the channel must remain idle while all contending nodes are simultaneously counting down. This wastage has almost been accepted as a price for decentralization. In this paper, we ask whether the entire backoff operation can be migrated to the frequency domain, thereby eliminating a long-standing source of channel inefficiency. Our core idea draws on OFDM subcarriers in modern WiFi radios, treating each subcarrier as an integer number. By transmitting a signal on a random subcarrier frequency, and using a second antenna to listen for all active frequencies, each node may be able to detect its rank among all contenders. Since signaling on subcarriers is almost instantaneous, the wastage from backoff can become negligible. We design such an unconventional backoff scheme called Back2F, implement it on a software- radio testbed, and demonstrate its feasibility with real-world experiments. A natural next step would be to revisit today’s protocols, and ask what other operations may be similarly migrated to the frequency domain. I. PROBLEM &MOTIVATION Accessing a shared resource in a decentralized manner has been studied for several decades. -
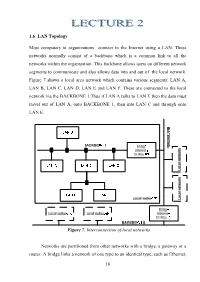
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges.