Archetype-Based Modeling of Persona for Comprehensive Personality Computing from Personal Big Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sacred Psychoanalysis” – an Interpretation Of
“SACRED PSYCHOANALYSIS” – AN INTERPRETATION OF THE EMERGENCE AND ENGAGEMENT OF RELIGION AND SPIRITUALITY IN CONTEMPORARY PSYCHOANALYSIS by JAMES ALISTAIR ROSS A thesis submitted to The University of Birmingham for the degree of DOCTOR OF PHILOSOPHY School of Philosophy, Theology and Religion College of Arts and Law The University of Birmingham July 2010 University of Birmingham Research Archive e-theses repository This unpublished thesis/dissertation is copyright of the author and/or third parties. The intellectual property rights of the author or third parties in respect of this work are as defined by The Copyright Designs and Patents Act 1988 or as modified by any successor legislation. Any use made of information contained in this thesis/dissertation must be in accordance with that legislation and must be properly acknowledged. Further distribution or reproduction in any format is prohibited without the permission of the copyright holder. ABSTRACT From the 1970s the emergence of religion and spirituality in psychoanalysis is a unique development, given its traditional pathologizing stance. This research examines how and why ‘sacred psychoanalysis’ came about and whether this represents a new analytic movement with definable features or a diffuse phenomena within psychoanalysis that parallels developments elsewhere. After identifying the research context, a discussion of definitions and qualitative reflexive methodology follows. An account of religious and spiritual engagement in psychoanalysis in the UK and the USA provides a narrative of key people and texts, with a focus on the theoretical foundations established by Winnicott and Bion. This leads to a detailed examination of the literary narratives of religious and spiritual engagement understood from: Christian; Natural; Maternal; Jewish; Buddhist; Hindu; Muslim; Mystical; and Intersubjective perspectives, synthesized into an interpretative framework of sacred psychoanalysis. -
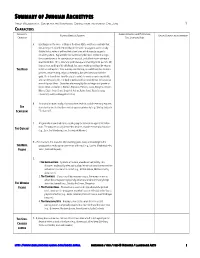
AP Jungian Archetypes GO
SUMMARY OF JUNGIAN ARCHETYPES PHILLIP WEDGEWORTH, CENTER FOR THE HUMANITIES; DERIVED FROM THE WORK OF CARL JUNG 1 CHARACTERS ARCHETYPAL GENERAL EXAMPLES FROM POP CULTURE, ESSENTIAL DETAILS & EXAMPLES SPECIFIC EXAMPLES FROM LITERATURE CHARACTER FILM, LITERATURE, NEWS A. Lord Raglan in The Hero: A Study in Tradition, Myth, and Drama contends that this archetype is so well defined that the life of the protagonist can be clearly divided into a series of well-marked adventures, which strongly suggest a ritualistic pattern. Raglan finds that traditionally the hero's mother is a virgin, the circumstances of his conception are unusual, and at birth some attempt is made to kill him. He is, however, spirited away and reared by foster parents. We know almost nothing of his childhood, but upon reaching manhood he returns THE HERO to his future kingdom. After a victory over the king or a wild beast, he marries a princess, becomes king, reigns uneventfully, but later loses favor with the gods. He is then driven from the city after which he meets a mysterious death, often at the top of a hill. His body is not buried; but nevertheless, he has one or more holy sepulchers. Characters who exemplify this archetype to a greater or lesser extent are Oedipus, Theseus, Romulus, Perseus, Jason, Dionysos, Joseph, Moses, Elijah, Jesus Christ, Siegfried, Arthur, Robin Hood, Watu Gunung (Javanese), and Llew Llawgyffes (Celtic). B. An animal or more usually a human whose death in a public ceremony expiates THE some taint or sin that has been visited upon a community (e.g., Shirley Jackson's SCAPEGOAT "The Lottery"). -

Mixed Metaphors and Narrative Shifts: Archetypes
Mixed Metaphors and Narrative Shifts Archetypes Raya A. Jones Cardiff University Abstract. Jungian archetype theory exemplifies tensions between ways of questioning in psychology. Jung anchors his thesis in the contrasting discourses of biology and metaphysics, though his narrative presents a ‘whole’ transcending both. The present focus is on its problematic touch- down in the discourse of science. The essay considers, in turn, tensions specific to Jung’s writing, tensions between Jungian theory development and the logic of scientific discovery, and tensions inherent in post-Jungian revisions of archetype theory, culminating in the relationship between saying and seeing problematized by Wittgenstein. Throughout, the essay engages with Jung’s theorizing as itself a creative process, the products of which (the specific propositions debated by his followers and critics) may be viewed as crossroads requiring readers of Jung to make decisions as to which way to turn. In closing, the possibility of integrating Jung’s thought with a dialogical approach is indicated. Key Words: archetypes, Jung, language games, science vs art I am inclined to think that scientific discovery is impossible without faith in ideas which are of a purely speculative kind, and sometimes even quite hazy; a faith which is completely unwarranted from the point of view of science . (Popper, 1934/1958, p. 38) C.G. Jung (1954/1960a) believed that the theory of archetypes explains scientific theories, among other things: ‘All the most powerful ideas in history go back to archetypes . the central concepts of science, philo- sophy, and ethics are no exception to this rule’ (para. 342). Judged against scientific criteria, archetype theory has barely progressed from a speculative hazy idea, such as those to which Popper refers. -

Moving Myths: a Heuristic Inquiry Into the Role of Jungian Concepts in The
Columbia College Chicago Digital Commons @ Columbia College Chicago Creative Arts Therapies Theses Thesis & Capstone Collection 12-13-2017 Moving Myths: A Heuristic Inquiry Into the Role of Jungian Concepts in the Theoretical Framework of a Dance/Movement Therapy Student Maura Reagan Columbia College Chicago Follow this and additional works at: https://digitalcommons.colum.edu/theses_dmt Part of the Dance Movement Therapy Commons This work is licensed under a Creative Commons Attribution-Noncommercial-No Derivative Works 4.0 License. Recommended Citation Reagan, Maura, "Moving Myths: A Heuristic Inquiry Into the Role of Jungian Concepts in the Theoretical Framework of a Dance/ Movement Therapy Student" (2017). Creative Arts Therapies Theses. 95. https://digitalcommons.colum.edu/theses_dmt/95 This Thesis is brought to you for free and open access by the Thesis & Capstone Collection at Digital Commons @ Columbia College Chicago. It has been accepted for inclusion in Creative Arts Therapies Theses by an authorized administrator of Digital Commons @ Columbia College Chicago. For more information, please contact [email protected]. MOVING MYTHS: A HEURISTIC INQUIRY INTO THE ROLE OF JUNGIAN CONCEPTS IN THE THEORHETICAL FRAMEWORK OF A DANCE/MOVEMENT THERAPY STUDENT Maura Reagan Thesis submitted to the faculty of Columbia College Chicago in partial fulfillment of the requirements for Master of Arts in Dance/Movement Therapy & Counseling Department of Creative Arts Therapies December 2017 Committee: Susan Imus, MA, BC-DMT, LCPC, GL-CMA Chair, Dance/Movement Therapy and Counseling Laura Downey, MA, BC-DMT, LPC, GL-CMA Research Coordinator Susan Imus, MA, BC-DMT, LCPC, GL-CMA Thesis Advisor Aisha Bell, MA, BC-DMT, LCPC Reader Abstract The purpose of this heuristic study was to develop a personal dance/movement therapy approach and interventions that utilize the Jungian concepts of myth and archetypes. -

Jungian Archetypes
Evan L, Vania C, Chevin J, Ellen P, Brian W, Grace Z Jungian Archetypes Carl Jung founded the key concept of archetypes contained within the ego, the personal unconscious and the collective unconscious, the ideas and memories shared in all humans. Jung explored the influences of the psyche parts of the mind, concerning the concept of recurring patterns, plotlines or figures. This idea is often portrayed as symbols or myths and occurs throughout the novel Three Day Road and the movie Whale Rider. In this analysis, the archetypes of the Anima and Animus, the Shadow, and the Sage are examined. There are three main classes of archetypes; archetypal characters, or personality archetypes, archetypal situations, and archetypal symbols. Personality archetypes relate to common patterns in the roles of characters, such as Elijah in the role of the Trickster archetype. Archetypal situations represent universal plotlines such as the Journey, the Quest, and the Death and Rebirth, while archetypal symbols usually include polarities such as Light and Dark or Spring and Winter, often signalling or representing good or evil. The archetype of the Shadow is established with suppressed desires, inclination, and flaws in the unconscious mind as humans strive to adapt to societal norms. The Shadow veils the dark parts of the intellect which are often disregarded by personal morals. Joseph Boyden’s novel Three Day Road showcases the Shadow through the character development of Xavier and Elijah, more specifically Elijah as Xavier’s Shadow. The friendship between Elijah and Xavier moulds their characters into one persona as they grow up together being raised by Niska. -

Jung's Archetypes of Persona and Shadow in Wilde's the Picture Of
TELL Journal, Volume 3, Number 1, April 2015 ISSN : 2338-8927 JUNG’S ARCHETYPES OF PERSONA AND SHADOW IN WILDE’S THE PICTURE OF DORIAN GRAY AND STEVENSON’S DR. JEKYLL AND MR. HYDE Dyah Kurniawati [email protected] Universitas PGRI RonggolaweTuban Abstract As a mirror of real life, literature contains things happening in the life of human beings and their surroundings. A careful study of literary works represents a way to add experience about life and also to gain knowledge about human life with all of their problems. The two novels being discusses in this article are Oscar Wilde‟s The Picture of Dorian Grayand Robert Louis Stevenson‟s Dr. Jekyll and Mr.Hyde.This article will be analyzed by using Carl Gustav Jung‟s archetypes theory in order to make a comparative study through both of those novels. Thus, this study concerns to Jung‟s archetypes of persona and shadow. The method of the research is descriptive text analysis. At the same time, the article writer also used comparative study. It was due to the aims of this study, which was to compare two literary works of the same country.The results of this study show the different achievements of persona and shadow through the representation of the characters of Dorian Gray in The Picture of Dorian Gray and Dr. Henry Jekyll in Dr. Jekyll and Mr. Hyde. The similarity of the two novels lies on the theme namely ways on fulfilling one‟s desire toward physical condition, while the differences are lie in the ways to achieve the goals of the main characters. -

Archetype/ Symbol in the Psychology of CG Jung Free Ebook
COMPLEX/ ARCHETYPE/ SYMBOL IN THE PSYCHOLOGY OF C.G. JUNG DOWNLOAD FREE BOOK Jolande Jacobi, Ralph Manheim | 256 pages | 21 Apr 1971 | Princeton University Press | 9780691017747 | English | New Jersey, United States Jungian archetypes The existence Complex/ Archetype/ Symbol in the Psychology of C.G. Jung the instincts Complex/ Archetype/ Symbol in the Psychology of C.G. Jung no more be proved than the existence of the archetypes, so long as they do not manifest themselves concretely. Wow, I really liked this - the first half was very informative, and quite helpful in understanding the concepts she is expounding on, but appropriately simple, and the second half - which is really a seperate work - is the interpretation of one particularly meaningful dream - in a beautifully composed and deeply touching way - a very good read. As well, Complex/ Archetype/ Symbol in the Psychology of C.G. Jung first two people function as each other's anima and animustheir romantic love serving to make each other psychologically complete. The mother, we know, frequently knows right away, consciously or psychically, that she is now pregnant. One person found this helpful. That is why it lies ready to hand in the unconscious of every man. In the Jungian perspective, therefore, the essence of the complex includes its autonomous psychic existence separate from consciousness and a feeling charge which exerts influence on consciousness. On the contrary, it continues vigorously during the first years of life into adolescence and probably beyond. Jacobi, The Psychology of C. Ken Wilber developed a theory called Spectrum of Consciousness, which expanded the Jungian archetypes. -

Worshipping the Dark the Manifestations of Carl
WORSHIPPING THE DARK THE MANIFESTATIONS OF CARL GUSTAV JUNG'S ARCHETYPE OF THE SHADOW IN CONTEMPORARY WICCA Nicholas Marc Dion Faculty of Religious Studies McGill University, Montreal October 2006 A thesis submitted to Mc Gill University in partial fulfillment of the requirements of the degree of Master of Arts © Nicholas Dion, 2006 Library and Bibliothèque et 1+1 Archives Canada Archives Canada Published Heritage Direction du Branch Patrimoine de l'édition 395 Wellington Street 395, rue Wellington Ottawa ON K1A ON4 Ottawa ON K1A ON4 Canada Canada Your file Votre référence ISBN: 978-0-494-28552-7 Our file Notre référence ISBN: 978-0-494-28552-7 NOTICE: AVIS: The author has granted a non L'auteur a accordé une licence non exclusive exclusive license allowing Library permettant à la Bibliothèque et Archives and Archives Canada to reproduce, Canada de reproduire, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par télécommunication ou par l'Internet, prêter, telecommunication or on the Internet, distribuer et vendre des thèses partout dans loan, distribute and sell th es es le monde, à des fins commerciales ou autres, worldwide, for commercial or non sur support microforme, papier, électronique commercial purposes, in microform, et/ou autres formats. paper, electronic and/or any other formats. The author retains copyright L'auteur conserve la propriété du droit d'auteur ownership and moral rights in et des droits moraux qui protège cette thèse. this thesis. Neither the thesis Ni la thèse ni des extraits substantiels de nor substantial extracts from it celle-ci ne doivent être imprimés ou autrement may be printed or otherwise reproduits sans son autorisation. -

Jungian Typologies and Conscious Preferences in Career and Intimate Relationship Development
JUNGIAN TYPOLOGIES AND CONSCIOUS PREFERENCES IN CAREER AND INTIMATE RELATIONSHIP DEVELOPMENT BY RAYMOND ,tERRY 1 JR. Bachelor of Arts Central State University Edmond, Oklahoma 1971 Master of Arts University of Oklahoma Norman, Oklahoma 1974 Submitted to the Faculty of the Graduate College of the Oklahoma State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY July, 1989 JUNGIAN TYPOLOGIES AND CONSCIOUS PREFERENCES IN CAREER AND INTIMATE RELATIONSHIP DEVELOPMENT Thesis Approved: /-- .. Thesis Adv ser - / I ii 1352148 COPYRIGHT by Raymond Perry, Jr. July, 1989 PREFACE A study of the role of unconscious personality variables in career and relationship development was completed. The unconscious variables selected for this study are based on the theories of C. G. Jung. Psychological types, and masculine and feminine archetypes identified in this study were generalized from Jung's original theories. A decision was made to develop questionnaires that would enable the researcher to assess masculine and feminine archetypal preferences. These assessment questionnaires were developed as part of a pilot study. The final study is based on a sample of 74 males and 91 females who were enrolled at three colleges and universities in a Southwestern state. All participants in this study completed the following psychological instruments; Myers-Briggs Type Indicator, Self-Directed Search, Masculine or Feminine Archetype Questionnaire, and a Projected-Masculine or Projected-Feminine Archetype Questionnaire. Statistical and descriptive procedures were used to analyze nine hypotheses. Difficulties and limitations inherent in a study of conscious correlates of unconscious personality variables are evident in the results. The iii findings in this study may have limited practical application at this time. -

“Gypsy” Fate: Carriers of Our Collective Shadow
Journal of Jungian Scholarly Studies Vol. 4, No. 1, 2008 “Gypsy” Fate: Carriers of our collective shadow Alexandra Fidyk, Ph.D. National-Louis University, Chicago If only it were all so simple! If only there were evil people somewhere insidiously committing evil deeds, and it were necessary only to separate them from the rest of us and destroy them. But the line dividing good and evil cuts through the heart of every human being. And who is willing to destroy a piece of his own heart? (Alexander Solzhenitsyn, The Gulag Archipelago) Story of the Stranger “Strangers, gods and monsters,” writes Richard Kearney (2003) “represent experiences of extremity which bring us to the edge. They subvert our established categories and challenge us to think again” (p. 3). Through this interpretation of “stranger” and “scapegoat,” I consider the European Roma1 as a group that challenges our way of thinking. The Roma as named are those who “threaten the known with the unknown” and so are “exiled to hell or heaven; or simply ostracized from the human community into a land of aliens” (Kearney, 2003, p. 3). Through a Romani narrative, woven of fact and fiction2, I consider how a group, which has been deeply identified with the role of the scapegoat, suffers negative inflation, exile and splitting. By fact and fiction I point to the inseparability of living and recounting stories, of Romani biography and cultural myth, and of stories told among the Roma and those told to non-Roma when creating any narrative. This identification of scapegoat by both themselves and others speaks to us of our split between the conscious and unconscious, familiar and unfamiliar, same and other. -

Self Individuation Process in the Main Character of Black Swan Movie
SELF INDIVIDUATION PROCESS IN THE MAIN CHARACTER OF BLACK SWAN MOVIE YohanaFebry Chris Suprapto Faculty of Humanity, Diponegoro University ABSTRACT Black Swan movie directed by Darren Aronofsky is a movie which includes many psychological aspects in it. This movie tells us about a journey to find the true self of the main character named Nina Sayers. The writer uses library research in collecting the data. The objectives of this thesis are to describe both intrinsic aspects which include narrative (theme, character, setting and conflict) and cinematic elements (mise-en-scene, camera distance, and sound) and to explain extrinsic aspects. To analyze the extrinsic aspects of the movie, the writer usespsychological approach. The writer analyses how Nina finds her true self related to Carl Jung theory about self individuation process. There are four kinds of archetypes in order to acknowledge the self individuation process. They are “persona”, “shadow”, “anima and animus”, and “Self”. Eventually, the writer finds that Nina does not experience those four archetypes. The result of this thesis is the “shadow” and “persona” are two archetypes which dominate Nina. It can be stated that the main character does not succeed in the process of self individuation proposed by Carl Gustav Jung. Keyword: life, journey, the true self, analytical psychology, self-individuation, archetype INTRODUCTION Literature has become an important part of human beings for ages. It develops that literature not only become part of human’s being life but also lifestyle for the consumer. As time goes by, technology also improves dramatically that literature can be enjoyed through film. The film functions as a media to depict the imagination, ideas, thoughts, feelings, or information toward the viewer. -

Public Relations Review Performance and Persona
Public Relations Review 41 (2015) 675–680 Contents lists available at ScienceDirect Public Relations Review Performance and Persona: Goffman and Jung’s approaches to professional identity applied to public relations ∗ Johanna Fawkes Charles Sturt University, School of Communication and Creative Industries, Panorama Avenue, Bathurst, NSW 2795, Australia a r t i c l e i n f o a b s t r a c t Article history: Public relations work involves shaping, reflecting and communicating identity for organi- Received 30 September 2013 sations and individuals, and is in turn shaped by the professional identity both of the field Received in revised form 3 February 2014 and individual public relations practitioners. This paper explores these issues from the dual Accepted 10 February 2014 perspectives of sociologist Erving Goffman’s (1922–1982) reflections on the performance Available online 22 March 2014 of work and Carl Jung’s (1875–1961) concept of Persona, the socially acceptable face of the individual or group. The former explores these issues through observation of exter- Keywords: nal behaviours, the latter by engaging with the psyche. Goffman and Jung, despite their Professional identity conflicting worldviews, offer a complementary understanding of the operation, internal Public relations Goffman and external, of professional identity. Jung The paper, which is conceptual and interpretive, with the objective of building theory, Performance summarises contemporary approaches to professional identity in public relations and other Persona fields, before introducing Goffman, who is often mentioned in this context, and Jung, who is not. Together these two scholars offer insights into the interior and exterior aspects of iden- tity, which is here applied to public relations, raising questions both about the production of identity as a commodity for others and the production of self-image of public relations prac- titioners.