Managed Code Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

C++/CLI Tutorial
CC++++//CCLLII TTuuttoorriiaall Author: Adam Sawicki, [email protected], www.asawicki.info Version 1.0, December 2011 Table of Contents Table of Contents .............................................................................................................................................................. 1 Introduction ...................................................................................................................................................................... 2 What is C++/CLI? ............................................................................................................................................................... 2 Why Use C++/CLI? ......................................................................................................................................................... 2 What C++/CLI is Not? .................................................................................................................................................... 2 Hello World Example ........................................................................................................................................................ 3 Project Properties ............................................................................................................................................................. 3 Namespaces ..................................................................................................................................................................... -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . .. -

Introduction to Managed Code
McGrath.book Page 89 Thursday, December 7, 2006 10:04 AM 3 Introduction to Managed Code Technology is dominated by two types of people: those who understand what they do not manage, and those who manage what they do not understand. —PUTT’S LAW Topics Covered in This Chapter What Is Managed Code? Introduction to Object-Oriented Programming Exploring the .NET Framework VSTO and Managed Code Summary Review Questions What Is Managed Code? Code that runs within the .NET Framework is considered managed code. This includes applications written in languages such as Visual C# and Visual Basic 2005. Code that is not managed by the .NET Frame- work is typically referred to as unmanaged code. This includes applica- tions written in programming languages such as C++, Visual Basic 6.0, and VBA. All Office solutions created using VSTO are written in managed code. VSTO supports both Visual Basic 2005 and Visual C#; however, we refer only to Visual Basic 2005 in text and in code examples in this book 89 McGrath.book Page 90 Thursday, December 7, 2006 10:04 AM 90 Chapter 3 Introduction to Managed Code because we believe it is easier to transition from VBA to Visual Basic 2005. Keep in mind that there is much to learn about the .NET Frame- work and managed code; this chapter only scratches the surface. Following are some benefits of using managed code: • Improved security. Often, security permissions are enabled or disabled by end users or determined by the identity of the user who is attempting to run code. However, code managed by the .NET Framework uses the security model code access security (CAS), which is based on the code’s identity and location. -

Visual Basic .NET and the .NET Platform: an Advanced Guide
Visual Basic .NET and the .NET Platform: An Advanced Guide ANDREWTROELSEN APress Media, LLC Visual Basic .NET and the .NET Platform: An Advanced Guide Copyright ©2002 by Andrew'Ii'oelsen Originally published by Apress in 2002 All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN 978-1-893115-26-2 ISBN 978-1-4302-0849-5 (eBook) DOI 10.1007/978-1-4302-0849-5 Trademarked names may appear in this book. Rather than use a trademark sym bol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Editorial Directors: Dan Appleman, Gary Cornell, Jason Gilmore, Karen Watterson Technical Reviewers: Pamela Fanstill, Rob Macdonald, Dan Appleman, William Oellermann Managing Editor: Grace Wong Copy Editors: Anne Friedman, Nicole LeClerc Production Editors: Janet Vail with Kari Brooks and Anne Friedman Composition and Art Services: Impressions Book and Journal Services, Inc. Indexer: Carol Burbo Cover Designer: Tom Debolski Marketing Manager: Stephanie Rodriguez Distributed to the book trade in the United States by Springer-Verlag New York, lnc.,175 Fifth Avenue, New York, NY, 10010 and outside the United States by Springer-Verlag GmbH & Co. KG, Tiergartenstr. 17, 69112 Heidelberg, Germany In the United States, phone 1-800-SPRINGER, email orders@springer-ny. -

INTRODUCTION to .NET FRAMEWORK NET Framework .NET Framework Is a Complete Environment That Allows Developers to Develop, Run, An
INTRODUCTION TO .NET FRAMEWORK NET Framework .NET Framework is a complete environment that allows developers to develop, run, and deploy the following applications: Console applications Windows Forms applications Windows Presentation Foundation (WPF) applications Web applications (ASP.NET applications) Web services Windows services Service-oriented applications using Windows Communication Foundation (WCF) Workflow-enabled applications using Windows Workflow Foundation (WF) .NET Framework also enables a developer to create sharable components to be used in distributed computing architecture. NET Framework supports the object-oriented programming model for multiple languages, such as Visual Basic, Visual C#, and Visual C++. NET Framework supports multiple programming languages in a manner that allows language interoperability. This implies that each language can use the code written in some other language. The main components of .NET Framework? The following are the key components of .NET Framework: .NET Framework Class Library Common Language Runtime Dynamic Language Runtimes (DLR) Application Domains Runtime Host Common Type System Metadata and Self-Describing Components Cross-Language Interoperability .NET Framework Security Profiling Side-by-Side Execution Microsoft Intermediate Language (MSIL) The .NET Framework is shipped with compilers of all .NET programming languages to develop programs. Each .NET compiler produces an intermediate code after compiling the source code. 1 The intermediate code is common for all languages and is understandable only to .NET environment. This intermediate code is known as MSIL. IL Intermediate Language is also known as MSIL (Microsoft Intermediate Language) or CIL (Common Intermediate Language). All .NET source code is compiled to IL. IL is then converted to machine code at the point where the software is installed, or at run-time by a Just-In-Time (JIT) compiler. -

ASP.NET SQL Server
CYAN YELLOW MAGENTA BLACK PANTONE 123 C BOOKS FOR PROFESSIONALS BY PROFESSIONALS® THE EXPERT’S VOICE® IN SQL SERVER Companion eBook Available Pro ASP.NET for SQL Server: High Performance Data Access for Web Developers Pro Dear Reader, ASP.NET ASP.NET As web developers, we work with ASP.NET and SQL Server by using a rich toolkit of databound controls and database functionality that promises great Pro performance and productivity gains after we know how to use it properly. Unfortunately, that toolkit is cluttered with a wide spectrum of features—some ideal for the one-man shop building a tiny application, and others aimed at large developer teams producing websites used by thousands of people. This book carves out a path for the senior developer who needs to produce a professional website that will perform well under high load. I focus on what a senior developer should know and use daily while also for explaining which features to avoid and why. There are several, little-known features ASP.NET in ASP.NET and SQL Server that work very well together without requiring much effort. These features get detailed coverage. Each chapter includes a full sample project, to help you learn by digging into some good code. These projects are for designed to keep you engaged while using them to understand the chapter topics in greater detail. What you will learn from this book are techniques that allow you to leverage SQL Server the many performance and productivity improvements that have been provided ASP.NET and SQL Server. These improvements will help you produce better SQL Server websites with the desired results right from the start. -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Special Characters Numbers
Index ■Special Characters AddServiceEndpoint( ) member, ServiceHost type, #define, preprocessor directive, 317–319 1032 #elif, preprocessor directive, 317–318 ADO.NET #else, preprocessor directive, 317–318 additional namespaces, 763–764 #endif, preprocessor directive, 317–318 vs. ADO classic, 759–760 #endregion, preprocessor directive, 317 application configuration files, 769–770 #if, preprocessor directive, 317–318 asynchronous data access, 792–793 #region, preprocessor directive, 317 autogenerated data components, 824–825 #undef, preprocessor directive, 317–319 autogenerating SQL commands, 816–817 % modulo operator, C#, 1097 autoincrementing, 797 & operator, pointer types, 312–313 binding DataTables to user interfaces, 804, 806 * operator, pointer types, 312–313 Command object, 781–782 ?? operator, 133 connected layer, 778 += operator, 610 connected vs. disconnected layer, 760 <%@Page%> directive attribute, ASP.NET, 846 connecting to database, Visual Studio 2005, 776 <%Import%> directive, ASP.NET, 846–847 connection objects, 779–780 => token, 1098 ConnectionStringBuilder object, 780–781 ? suffix, nullable types, 131 connectionStrings element, application configuration, 774–775 ■Numbers data access libraries, 1130 data adapter objects, 811–812 3D graphics graphical service, WPF, 1012 data providers, 760, 762 3D rendered animation, 970 data wizards, 822–825 100% code approach, 1048 DataColumn objects, 796, 798 ■ DataRelation objects, 817–820 A DataRow objects, 798–799, 801 A# programming language, 8 DataRow.RowState property, 799–800 Abort( -
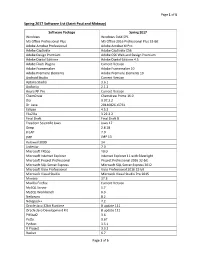
Spring 2017 Software List (Saint Paul and Midway)
Page 1 of 5 Spring 2017 Software List (Saint Paul and Midway) Software Package Spring 2017 Windows Windows 7x64 SP1 MS Office Professional Plus MS Office 2016 Professional Plus 32-Bit Adobe Acrobat Professional Adobe Acrobat XI Pro Adobe Captivate Adobe Captivate CS6 Adobe Design Premium Adobe CS6 Web and Design Premium Adobe Digital Editions Adobe Digital Editions 4.5 Adobe Flash Plugins Current Version Adobe Framemaker Adobe Framemaker 10 Adobe Premiere Elements Adobe Premiere Elements 10 Android Studio Current Version Aptana Studio 3.6.1 Audacity 2.1.2 Axure RP Pro Current Version ChemDraw Chemdraw Prime 16.0 Dia 0.97.2.2 Dr. Java 20140826-r5761 Eclipse 4.5.2 FileZilla 3.22.2.2 Final Draft Final Draft 8 Freedom Scientific Jaws Jaws 17 Gimp 2.8.18 JFLAP 7.0 JMP JMP 13 Kurzweil 3000 14 Lodestar 7.0 Microsoft FXCop 10.0 Microsoft Internet Explorer Internet Explorer 11 with Silverlight Microsoft Project Professional Project Professional 2016 32-bit Microsoft SQL Server Express Microsoft SQL Server Express 2012 Microsoft Visio Professional Visio Professional 2016 32-bit Microsoft Visual Studio Microsoft Visual Studio Pro 2015 Minitab 17.3 Mozilla Firefox Current Version MySQL Server 5.7 MySQL Workbench 6.3 Netbeans 8.2 Notepad++ 7.2 Oracle Java 32bit Runtime 8 update 111 Oracle Java Development Kit 8 update 111 PHStat2 3.6 Putty 0.67 Python 3.5.1 R Project 3.3.2 Racket 6.7 Page 1 of 5 Page 2 of 5 Software Package Spring 2017 Raptor Current Version SAP Client SAP Client 7.4.9 SAP Lumira 1.31.1 SAP Crystal Reports Current Version SPSS SPSS -

NET Hacking & In-Memory Malware
.NET Hacking & In-Memory Malware Shawn Edwards Shawn Edwards Cyber Adversarial Engineer The MITRE Corporation Hacker Maker Learner Take stuff apart. Change it. Put Motivated by an incessant Devoted to a continuous effort it back together. desire to create and craft. of learning and sharing knowledge. Red teamer. Adversary Numerous personal and emulator. professional projects. B.S. in Computer Science. Adversary Emulation @ MITRE • Red teaming, but specific threat actors • Use open-source knowledge of their TTPs to emulate their behavior and operations • Ensures techniques are accurate to real world • ATT&CK (Adversarial Tactics Techniques and Common Knowledge) • Public wiki of real-world adversary TTPs, software, and groups • CALDERA • Modular Automated Adversary Emulation framework Adversary Emulation @ MITRE • ATT&CK • Adversarial Tactics Techniques and Common Knowledge • Public wiki of real-world adversary TTPs, software, and groups • Lets blue team and red team speak in the same language • CALDERA • Modular Automated Adversary Emulation framework • Adversary Mode: • AI-driven “red team in a box” • Atomic Mode: • Define Adversaries, give them abilities, run operations. Customize everything at will. In-Memory Malware • Is not new • Process Injection has been around for a long time • Typically thought of as advanced tradecraft; not really • Surged in popularity recently • Made easier by open-source or commercial red team tools • For this talk, only discuss Windows malware • When relevant, will include the ATT&CK Technique ID In-Memory -

Embedding Mono Code in Unmanaged Applications on GNU/Linux
Embedding Mono code in unmanaged applications on GNU/Linux LTH School of Engineering at Campus Helsingborg Department of Computer Science Bachelor thesis: Martin Arvidsson Viktor Hermansson c Copyright Martin Arvidsson, Viktor Hermansson LTH School of Engineering Lund University Box 882 SE-251 08 Helsingborg Sweden LTH Ingenj¨orsh¨ogskolan vid Campus Helsingborg Lunds universitet Box 882 251 08 Helsingborg Printed in Sweden Media-Tryck Biblioteksdirektionen Lunds universitet Lund 2011 Abstract In today's society more and more work is carried out with the help of dif- ferent computer systems. To benefit from the data, integration between the systems is needed. Saab has developed a solution to the problem, by the name WISE. With a modular design costs can be minimized, because a new integration does not necessarily require new software, but can be achieved with configuration of an existing module. (a so-called driver). By supporting languages on a higher level than C++, development of new drivers can be speeded up to further decrease the costs. As a first step C# support was implemented with the help of C++/CLI. Such a solution is constrained to the Windows platform. To be able to meet the customers need for Linux compatibility this project was initiated, to create a wrapper driver with the help of Mono. In the report it is shown that it is fully possible to create a working embedding of C# with the Mono runtime. The documentation of the limited embedding-API is however inadequate, this resulted in us having to investigate the functionality by creating small test cases and read the source code to see how function calls behaved. -

20 Le Regular Expression Seconda Parte
������������������������������������������������������������� ��������������������������������������� ������������������������������������������������������������ ����������������������������� ���������������������������������� ��������������������������������������������������� ������������������������������������������������������������������������������������������������������������������������������������� 400X302 Computer programming.ind1 1 20-03-2007 10:29:34 ������������������������������������������������������������� ��������������������������������������� ������������������������������������������������������������ ����������������������������� ���������������������������������� ��������������������������������������������������� ������������������������������������������������������������������������������������������������������������������������������������� 400X302 Computer programming.ind1 1 20-03-2007 10:29:34 I N V E T R I N A V B J 7 5 Doing Objects Object-Oriented Programming Access Data in Visual Basic 2005 Languages: Interpretation Analysis Cookbook di D. Kurata di Craig - I. D. di K.Bluttman - W.S. Freeze Addison Wesley Springer O’ Reilly 552 pp - 46,95 Euro 256 pp - 36,70 Euro 366 pp - 47,20 Euro ISBN 9780321320490 ISBN 9781846287732 ISBN 9780596101220 Scrivi a [email protected] specificando nell’oggetto della e-mail: IN VETRINA VBJ n. 75 oppure inviaci il coupon al numero di fax 0587/732232 Potrai acquistare i libri qui riportati con uno SCONTO ECCEZIONALE del 10% anche se acquisti solo un libro oppure del 20%