Steam Browser Protocol Insecurity (Whenlocalbugsgoremote)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

12 Browser Alternativi Dalle Alte Prestazioni
12 browser alternativi dalle alte prestazioni Scritto da Mercoledì 17 Marzo 2010 23:59 E' molto probabile che per leggere queste righe stiate utilizzando un browser come Firefox, oppure Internet Explorer, o Google Chrome. Questa considerazione nasce dalla constatazione che questi tre browser assieme coprono circa il 90% del mercato. Il fatto che questi 3 programmi abbiano una così vasta popolarità non comporta che si tratti delle soluzioni migliori, vista l'abbondanza di alternative presenti. {loadposition user7} Ecco, a titolo di esempio, una serie di ben 12 browser disponibili gratuitamente, che potrebbero in realtà corrispondere alle vostre esigenze in maniera migliore rispetto ai nomi più conosciuti. Maxthon Si tratta del progetto nato come MyIE2. Nel corso degli anni è diventato un potente browser a schede adatto per tutti gli utenti. Oltre alle funzionalità di navigazione di base, Maxthon Browser fornisce un ricco set di funzionalità per migliorarei vostri percorsi di navigazione 1 / 10 12 browser alternativi dalle alte prestazioni Scritto da Mercoledì 17 Marzo 2010 23:59 Sistema Operativo: Windows Arora Arora è un leggero browser web. È dotato di rendering veloce, potente motore JavaScript e supporta plug-in Netscape. Sistema Operativo: Windows, Mac OS X, Linux Amaya 2 / 10 12 browser alternativi dalle alte prestazioni Scritto da Mercoledì 17 Marzo 2010 23:59 SistemaAmayaperfettamente non Operativo: è solo integrata un Windows, browser con l'editing, Macweb, OS ma tanto X,è ancheUnix da renderloplatforms un editor un web. prezioso La modalità strumento di visualizzazionecollaborativo. è Flock 3 / 10 12 browser alternativi dalle alte prestazioni Scritto da Mercoledì 17 Marzo 2010 23:59 Flock è un browser con un focus sui social media. -

The Development and Validation of the Game User Experience Satisfaction Scale (Guess)
THE DEVELOPMENT AND VALIDATION OF THE GAME USER EXPERIENCE SATISFACTION SCALE (GUESS) A Dissertation by Mikki Hoang Phan Master of Arts, Wichita State University, 2012 Bachelor of Arts, Wichita State University, 2008 Submitted to the Department of Psychology and the faculty of the Graduate School of Wichita State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy May 2015 © Copyright 2015 by Mikki Phan All Rights Reserved THE DEVELOPMENT AND VALIDATION OF THE GAME USER EXPERIENCE SATISFACTION SCALE (GUESS) The following faculty members have examined the final copy of this dissertation for form and content, and recommend that it be accepted in partial fulfillment of the requirements for the degree of Doctor of Philosophy with a major in Psychology. _____________________________________ Barbara S. Chaparro, Committee Chair _____________________________________ Joseph Keebler, Committee Member _____________________________________ Jibo He, Committee Member _____________________________________ Darwin Dorr, Committee Member _____________________________________ Jodie Hertzog, Committee Member Accepted for the College of Liberal Arts and Sciences _____________________________________ Ronald Matson, Dean Accepted for the Graduate School _____________________________________ Abu S. Masud, Interim Dean iii DEDICATION To my parents for their love and support, and all that they have sacrificed so that my siblings and I can have a better future iv Video games open worlds. — Jon-Paul Dyson v ACKNOWLEDGEMENTS Althea Gibson once said, “No matter what accomplishments you make, somebody helped you.” Thus, completing this long and winding Ph.D. journey would not have been possible without a village of support and help. While words could not adequately sum up how thankful I am, I would like to start off by thanking my dissertation chair and advisor, Dr. -

Using Replicated Execution for a More Secure and Reliable Web Browser
Using Replicated Execution for a More Secure and Reliable Web Browser Hui Xue Nathan Dautenhahn Samuel T. King University of Illinois at Urbana Champaign huixue2, dautenh1, kingst @uiuc.edu { } Abstract Unfortunately, hackers actively exploit these vulnerabil- ities as indicated in reports from the University of Wash- Modern web browsers are complex. They provide a ington [46], Microsoft [61], and Google [49, 48]. high-performance and rich computational environment Both industry and academia have improved the se- for web-based applications, but they are prone to nu- curity and reliability of web browsers. Current com- merous types of security vulnerabilities that attackers modity browsers make large strides towards improving actively exploit. However, because major browser plat- the security and reliability of plugins by using sandbox- forms differ in their implementations they rarely exhibit ing techniques to isolate plugins from the rest of the the same vulnerabilities. browser [62, 33]. However, these browsers still scatter In this paper we present Cocktail, a system that uses security logic throughout millions of lines of code, leav- three different off-the-shelf web browsers in parallel to ing these systems susceptible to browser-based attacks. provide replicated execution for withstanding browser- Current research efforts, like Tahoma [32], the OP web based attacks and improving browser reliability. Cock- browser [36], the Gazelle web browser [59], and the Illi- tail mirrors inputs to each replica and votes on browser nois Browser Operating System [58] all propose build- states and outputs to detect potential attacks, while con- ing new web browsers to improve security. Although tinuing to run. -

Maelstrom Web Browser Free Download
maelstrom web browser free download 11 Interesting Web Browsers (That Aren’t Chrome) Whether it’s to peruse GitHub, send the odd tweetstorm or catch-up on the latest Netflix hit — Chrome’s the one . But when was the last time you actually considered any alternative? It’s close to three decades since the first browser arrived; chances are it’s been several years since you even looked beyond Chrome. There’s never been more choice and variety in what you use to build sites and surf the web (the 90s are back, right?) . So, here’s a run-down of 11 browsers that may be worth a look, for a variety of reasons . Brave: Stopping the trackers. Brave is an open-source browser, co-founded by Brendan Eich of Mozilla and JavaScript fame. It’s hoping it can ‘save the web’ . Available for a variety of desktop and mobile operating systems, Brave touts itself as a ‘faster and safer’ web browser. It achieves this, somewhat controversially, by automatically blocking ads and trackers. “Brave is the only approach to the Web that puts users first in ownership and control of their browsing data by blocking trackers by default, with no exceptions.” — Brendan Eich. Brave’s goal is to provide an alternative to the current system publishers employ of providing free content to users supported by advertising revenue. Developers are encouraged to contribute to the project on GitHub, and publishers are invited to become a partner in order to work towards an alternative way to earn from their content. Ghost: Multi-session browsing. -

Steam System Services
Steam System Services Steam System Services Working in partnership to deliver a cleaner more efficient future Steam System Services Steam System Services 100 years of steam expertise across industry We have been dealing with industrial markets and their total steam requirements for over 100 years, gaining considerable expert knowledge of steam engineering and steam systems. It has been evident in recent years that our customers’ requirements have changed due to the significant increase in fuel costs and environmental issues. In addition, many of our customers have been forced to make cost-cutting exercises resulting in the reduction of maintenance teams and loss of steam engineering experience. This is where our Steam System Services have evolved to support you, by helping you to maintain performance and reduce costs, by working alongside your maintenance teams to improve and sustain your plants efficiency. Our services are tailored and integrated to suit your resources, plant requirements and budget. Qualified and experienced engineers will work with you to implement the improvements to your system and then help you to maintain the resulting performance gains which usually give very rapid returns on your investment. Steam System Services Audits Installation and Service Problem & potential solution commissioning Maintaining plant performance Solution implementation spiraxsarco.com Benefits: Steam System Services can help to maintain your steam system at its optimum level, ensuring that steam reaches the point of use at the correct quantity, quality and pressure. Increased Turnover Increased Profit Health and Safety Reduced downtime through Reducing energy wastage Helping you comply with preventative maintenance. and emissions. regulations / legislation. Reduced product rejects by Reducing stock holding through ensuring steam reaches point rationalisation of steam equipment of use at correct conditions. -

Day of Defeat : Official Strategy Guide Kindle
DAY OF DEFEAT : OFFICIAL STRATEGY GUIDE PDF, EPUB, EBOOK Prima Development | 160 pages | 01 Jun 2003 | Prima Publishing,U.S. | 9780761543503 | English | Rocklin, United States Day of Defeat : Official Strategy Guide PDF Book Paladin Anima Powers. Playing online is fundamentally different from playing offline, as greater amounts of interactivity and chaos often push you to new limits as a general and a soldier. When playing a sniper, find a spot and start sniping; trying to be mobile may be more fun, but sticking to a good perch that overlooks a high-traffic area is far more helpful if you're into mobile sniping, try the Rifleman class. Don't know how effective this is for small games, but there is a marked difference in large games. While there is always a raging debate over whether the recoils are too hard or too soft, dealing with recoil is the same across the board. A large clip allowed for agile attacks on fortified positions. Follow the sound of the ringing phone through the little office and down the corridor. Thanks to anybody who still believes in acting civil online! You can get there easily by going to the flag 3 sewers, then taking a left down to the area under the church. The graphics aren't the best, but this game was tons of fun back in the day! There's a door on the right side that leads directly in. Finally, if you're in need of a defensive location, enter the left path out of your spawn. Errors and other gremlins squashed. -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session. -

How to Get Steam Keys for Humble Bundle Games?
[ How to get steam keys for humble bundle games ] User rating: Jun 11, · Get a Steam Key for Snake Pass on Humble Bundle, redeem it on Steam and keep it forever! You can claim the game from June 11th at CET to June 14th at CET. Follow us on Twitter, Facebook or Steam to get a reminder when the next freebie launches! ABOUT THE GAME. ★How to Redeem an Epic Games Key ★ Redeeming Activision / Blizzard Keys through Direct Entitlement ★ How to redeem a PlayStation Bundle key. ★ Uplay Redemption Instructions ★ Free Game Redemption Instructions ★ Locating your Steam content ★ How to claim a Humble Bundle purchase or gift ★ How To Redeem Origin Keys ★ How To Redeem GOG Keys ★ How To Redeem Steam Keys. Jul 06, · All of our products are officially-licensed from some of the world's biggest publishers, including Humble Bundle, Electronic Arts, Bethesda and many more. We began our story in the 90s, making affordable software and games available to all on PC CD-ROM. In we launched Bundle Stars to satisfy the growing global demand for digital games. Jul 16, · If you are looking specifically for keys, you won't get them. HB sends an email with a link. In that link are the games. For Steam, you need to long in through the HB sevice so you can add the keys directly to your account. (Be sure to include any other email addresses you might have, as well as your Steam ID) 3. Getting your free game key. Head to our main page or Humble Store, click on the free promotion and get the game key over to you clicking the GET THE GAME button from the page. -

Update 22 November 2017 Best Game Yang Baru Masuk
Downloaded from: justpaste.it/premiumlink UPDATE 22 NOVEMBER 2017 BEST GAME YANG BARU MASUK DAFTAR LIST NieR Automata - (10DVD) Full CPY Releases REKOMENDASI SPESIFIKASI PC PALING RENDAH BISA MAIN GAME BERAT/BESAR TAHUN 2017 SET LOW / MID FPS 30 KURANG LEBIH VERSI INTEL DAN NVIDIA TERENDAH: PROCIE: INTEL I3 RAM: 6GB VGA: NVIDIA GTX 660 WINDOWS 7 VERSI AMD TERENDAH: PROCIE: AMD A6-7400K RAM: 6GB VGA: AMD R7 360 WINDOWS 7 REKOMENDASI SPESIFIKASI PC PALING STABIL FPS 40-+ SET HIGH / ULTRA: PROCIE INTEL I7 6700 / AMD RYZEN 7 1700 RAM 16GB DUAL CHANNEL / QUAD CHANNEL DDR3 / UP VGA NVIDIA GTX 1060 6GB / AMD RX 570 HARDDISK SEAGATE / WD, SATA 6GB/S 5400RPM / UP SSD OPERATING SYSTEM SANDISK / SAMSUNG MOTHERBOARD MSI / ASUS / GIGABYTE / ASROCK PSU 500W CORSAIR / ENERMAX WINDOWS 10 CEK SPESIFIKASI PC UNTUK GAME YANG ANDA INGIN MAINKAN http://www.game-debate.com/ ------------------------------------------------------------------------------------------------------------------------------ -------- LANGKAH COPY & INSTAL PALING LANCAR KLIK DI SINI Order game lain kirim email ke [email protected] dan akan kami berikan link menuju halaman pembelian game tersebut di Tokopedia / Kaskus ------------------------------------------------------------------------------------------------------------------------------ -------- Download List Untuk di simpan Offline LINK DOWNLOAD TIDAK BISA DI BUKA ATAU ERROR, COBA LINK DOWNLOAD LAIN SEMUA SITUS DI BAWAH INI SUDAH DI VERIFIKASI DAN SUDAH SAYA COBA DOWNLOAD SENDIRI, ADALAH TEMPAT DOWNLOAD PALING MUDAH OPENLOAD.CO CLICKNUPLOAD.ORG FILECLOUD.IO SENDIT.CLOUD SENDSPACE.COM UPLOD.CC UPPIT.COM ZIPPYSHARE.COM DOWNACE.COM FILEBEBO.COM SOLIDFILES.COM TUSFILES.NET ------------------------------------------------------------------------------------------------------------------------------ -------- List Online: TEKAN CTR L+F UNTUK MENCARI JUDUL GAME EVOLUSI GRAFIK GAME DAN GAMEPLAY MENINGKAT MULAI TAHUN 2013 UNTUK MENCARI GAME TAHUN 2013 KE ATAS TEKAN CTRL+F KETIK 12 NOVEMBER 2013 1. -

PROCEDURAL CONTENT GENERATION for GAME DESIGNERS a Dissertation
UNIVERSITY OF CALIFORNIA SANTA CRUZ EXPRESSIVE DESIGN TOOLS: PROCEDURAL CONTENT GENERATION FOR GAME DESIGNERS A dissertation submitted in partial satisfaction of the requirements for the degree of DOCTOR OF PHILOSOPHY in COMPUTER SCIENCE by Gillian Margaret Smith June 2012 The Dissertation of Gillian Margaret Smith is approved: ________________________________ Professor Jim Whitehead, Chair ________________________________ Associate Professor Michael Mateas ________________________________ Associate Professor Noah Wardrip-Fruin ________________________________ Professor R. Michael Young ________________________________ Tyrus Miller Vice Provost and Dean of Graduate Studies Copyright © by Gillian Margaret Smith 2012 TABLE OF CONTENTS List of Figures .................................................................................................................. ix List of Tables ................................................................................................................ xvii Abstract ...................................................................................................................... xviii Acknowledgments ......................................................................................................... xx Chapter 1: Introduction ....................................................................................................1 1 Procedural Content Generation ................................................................................. 6 1.1 Game Design................................................................................................... -
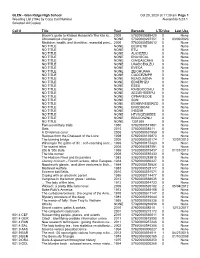
Glen Ridge High School 1 Page Oct 20, 2020 at 11:39 Am Weeding List
GLEN - Glen Ridge High School Oct 20, 2020 at 11:39 am 1Page Weeding List (164) by Copy Call Number Alexandria 6.23.1 Selected:All Copies Call # Title Year Barcode LTD Use Last Use Bloom's guide to Khaled Hosseini's The kite ru... 2009 57820000588429 0 None Chromebook charger NONE 57820000297351 3 03/09/2020 Medicine, health, and bioethics : essential prim... 2006 57820000538013 0 None NO TITLE NONE EEUFET8I 0 None NO TITLE NONE ETU 0 None NO TITLE NONE AUCIEZEU 0 None NO TITLE NONE ENA1GCAL 0 None NO TITLE NONE OIAIQA8CNH5 0 None NO TITLE NONE UAADCEGLZU 0 None NO TITLE NONE EVECA 0 None NO TITLE NONE ZEIOHUAAA 0 None NO TITLE NONE CUOCEZMPE 0 None NO TITLE NONE KEAOUADNA 0 None NO TITLE NONE ED8ERHZU 0 None NO TITLE NONE ESEU 0 None NO TITLE NONE RAIQGCCOAU 0 None NO TITLE NONE AEZJEHSSSPU 0 None NO TITLE NONE CPNARECOE 0 None NO TITLE NONE SON 0 None NO TITLE NONE EEHBVNEUERZO 0 None NO TITLE NONE ENODBOAII 0 None NO TITLE NONE IHBDIIH 0 None NO TITLE NONE HTVUQZUKEEE 0 None NO TITLE NONE BBACCNZNU 0 None NO TITLE NONE 1301309 0 None Famous military trials 1980 57820000517881 0 None Geis 2016 5782000058211 0 None A Christmas carol 2008 57820000587959 0 None Recipes from the Chateaux of the Loire 1998 57820000169873 0 None The burning bridge 2005 57820000520174 7 12/07/2015 Winning in the game of life : self-coaching secr... 1999 57820000157423 0 None The scarlet letter 2006 57820000587991 0 None 20s & '30s style 1989 57820000079437 2 01/31/2013 The kite runner 2008 57820000585433 0 None The Hudson River and its painters 1983 57820000283815 0 None Literary criticism - French writers, other Europea...1984 57820000080427 0 None Napoleon's glands : and other ventures in bioh.. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29.