A Traffic Analysis of a Busy Counter-Strike Server
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Day of Defeat : Official Strategy Guide Kindle
DAY OF DEFEAT : OFFICIAL STRATEGY GUIDE PDF, EPUB, EBOOK Prima Development | 160 pages | 01 Jun 2003 | Prima Publishing,U.S. | 9780761543503 | English | Rocklin, United States Day of Defeat : Official Strategy Guide PDF Book Paladin Anima Powers. Playing online is fundamentally different from playing offline, as greater amounts of interactivity and chaos often push you to new limits as a general and a soldier. When playing a sniper, find a spot and start sniping; trying to be mobile may be more fun, but sticking to a good perch that overlooks a high-traffic area is far more helpful if you're into mobile sniping, try the Rifleman class. Don't know how effective this is for small games, but there is a marked difference in large games. While there is always a raging debate over whether the recoils are too hard or too soft, dealing with recoil is the same across the board. A large clip allowed for agile attacks on fortified positions. Follow the sound of the ringing phone through the little office and down the corridor. Thanks to anybody who still believes in acting civil online! You can get there easily by going to the flag 3 sewers, then taking a left down to the area under the church. The graphics aren't the best, but this game was tons of fun back in the day! There's a door on the right side that leads directly in. Finally, if you're in need of a defensive location, enter the left path out of your spawn. Errors and other gremlins squashed. -

EA and Valve Unveil the Black Box and the Orange Box
EA and Valve Unveil The Black Box and The Orange Box Innovative Action Titles Ship in Fall 2007 and Include Portal(TM), Team Fortress(R) 2 and Half-Life(R) 2: Episode Two in One Box REDWOOD CITY, Calif.--(BUSINESS WIRE)--Feb. 7, 2007--Electronic Arts (NASDAQ:ERTS), the world's leading interactive entertainment company, and Valve®, the award-winning studio behind the blockbuster franchises Half-Life® and Counter- Strike®, today announced the naming and product configurations The Black Box and The Orange Box, two of the most anticipated action game offerings shipping worldwide in Fall 2007. The Black Box will ship for the PC, and includes Half-Life 2: Episode Two, Portal and Team Fortress 2. The Orange Box will ship for the PC, PLAYSTATION®3 computer entertainment system, and Xbox 360™ videogame and entertainment system, and includes all the content of The Black Box, plus the original Half-Life 2 and Half-Life 2: Episode One. Innovative games included in The Black Box and The Orange Box include: -- Half-Life 2: Episode Two -- the second installment in Valve's episodic trilogy advances the award-winning story, leading the player to new locations outside of City 17. -- Portal -- a pioneering type of single player action game that rewrites the rules for how players approach and manipulate their environment - much like how Half-Life 2's Gravity Gun reinvented the way gamers interact with objects in the game. -- Team Fortress 2 -- an all-new version of the legendary title that spawned team based multiplayer action games. The game's daring new art style features the most advanced graphics of any Source-based game released to date. -

Valve's Day of Defeat™ for the PC Invades Retail Shelves Nationwide
Valve's Day Of Defeat™ for the PC Invades Retail Shelves Nationwide Santa Monica, CA - May 8, 2003 - Activision, Inc. (Nasdaq: ATVI) and Valve are taking World War II fans online to the battlefield with the retail release of Day of Defeat™. The title, a multiplayer WWII first-person action game powered by Valve's Half-Life® technology, provides intense team-based gameplay that pits gamers in Axis vs. Allies squad-based combat in Western Europe at the height of the war in 1944. Day of Defeat is available at retail outlets nationwide for a suggested retail price of $29.99 and carries a "T" (Teen - Blood, Violence - content suitable for persons ages 13 and older) rating by the ESRB. "With true to life WWII weapons and multiplayer at its best, Day of Defeat captures the intensity and emotion of fighting alongside other soldiers in the battlefields of Western Europe," said Larry Goldberg, executive vice president, Activision Worldwide Studios. "Whether you're playing as Allied or Axis forces, Day of Defeat takes the fast-paced action and heart- stopping gameplay that its fans have come to crave to a higher level with updated graphics and new maps and classes." Day of Defeat features fifteen multiplayer maps and an incredible collection of historic weaponry that provide for an intense brand of team-based warfare. The game also includes all new character models, new animations, increased textures and particle effects system. "Day of Defeat has broken through to become one of the most popular online action games in the world, second only to Counter-Strike," said Gabe Newell, co-founder and managing director of Valve. -

Shading in Valve's Source Engine
Shading in Valve’s Source Engine SIGGRAPH 2006 Jason Mitchell Valve Introduction ¾ World Lighting • Radiosity Normal Mapping • Specular Lighting ¾ Model lighting • Irradiance Volume • Half-Lambert • Phong terms ¾ High Dynamic Range Rendering • Tone mapping • Autoexposure ¾ Color Correction Timeline ¾ Half-Life 2 and Counter-Strike: Source (November 2004) • Baseline shading model we’ll present today ¾ Lost Coast (October 2005) • High Dynamic Range Rendering ¾ Day of Defeat: Source (September 2005) • Color Correction and HDR ¾ Half-Life 2: Episode One (June 2006) • Phong shading Episodic Content Î Incremental Technology ¾ The extensions to the baseline Half-Life 2 technology have been shipped in subsequent products in the year and a half since HL2 shipped. • More efficient way to develop technology • Delivers value to customers and licensees ¾ Shorten the delay between hardware availability and game support Marketplace Context See full survey at http://www.steampowered.com/status/survey.html World Lighting with Radiosity ¾ Realism ¾ More forgiving than direct lighting only • Avoids harsh lighting situations • Less micro-management of light sources for content production • Can’t tune lights shot-by-shot like movies. Don’t know what the shots are, and don’t want to take the production time to do this Direct lighting only Radiosity lighting Normal Mapping ¾ Reusable high-frequency detail ¾ Higher detail than we can currently get from triangles ¾ Works well with both diffuse and specular lighting models ¾ Can now be made to integrate with radiosity -

Sturmbot 1.9 Install for Day of Defeat Steam - Version 2
Sturmbot 1.9 install for Day of Defeat Steam - Version 2 If you just got day of defeat and want a single payer mode, use the installer. Just be sure you installed day of defeat steam 1.3, run the game once, opened a map and closed it down. Then add this custom file set. I place the credits and contents last (down below) as you have already read about this package. Two ways to install, installer or manual zip, scroll down for your preference. This will not get you VAC banned or alter your online game experience. It sure will change your day of defeat single play experience. WARNING ITEMS The installer will overwrite your userconfig.cfg file. The userconfig.cfg files is not a normal game file... if you don't know of it... you have not got one so use the installer! Basically the new file will add some scripts, binds and commands to give you custom crosshairs and a new in- game menu. I recommend all new players use the installer, you just need to get the right folder to install the files into and the installer takes care of the rest. If you had Sturmbot before there are new waypoints, you need to delete your old files in the dod\sturmbot\learn and dod\sturmbot\temp folders. If you have older waypoint versions you will find the bots have written what they learn when you play, while great old waypoint temp files can really mess up any new waypoints. New users - Do the below for the installer Experienced users for a manual zip install do the technique after the installer technique. -

Press Release
PRESS RELEASE For Immediate Release: MNSi Telecom Announces New Peering Agreements with Major Gaming Companies WINDSOR, ON (June 13, 2018) - MNSi Telecom has just announced new peering agreements with Valve Software , Blizzard Entertainment , Riot Games and Twitch.tv . These arrangements should reduce latency and improve performance for Fibre customers using those services. Gamers can be a pretty demanding group. In an environment where even a fraction of a second of lag could be the difference between online life and death, players crave better, stronger and more reliable connections. Connections need to be fast and dependable to avoid any noticeable stutter. Online play involves sending and receiving data packets in real time – that’s bits and bits of information that will communicate dynamically changing events within a game as they happen - affecting user play across the country or around the world. One of the best ways to help ensure smooth play is peering. That’s when two or more companies work together to optimize the flow of data traffic between them to facilitate smoother connections. If your internet provider has a peering agreement with an online gaming company, then you’ve got a leg-up as a gamer in your quest for a dependable connection and a better online gaming experience. MNSi’s new peering agreements with Valve Software , Blizzard Entertainment , Riot Games and Twitch.tv will offer users more efficient downloads, better video streaming and much lower latency when playing games over the MNSi Fibre network. Gamers also pay attention to the speed of their connection for more than just playing the game – it’s about sharing wins, posting highlights and streaming events. -
Day of Defeat Source Free Download Pc Game Full Version Torrent
Day Of Defeat Source Free Download Pc Game Full Version Torrent 1 / 4 Day Of Defeat Source Free Download Pc Game Full Version Torrent 2 / 4 3 / 4 Version: Latest Torrent / Magnet; Maps for Day of Defeat: Source. Version: Final Torrent / Magnet. Garry's Mod (No-Steam). Version: Latest. It seemed a little odd to release Day of Defeat in 2003 (the original DoD dates ... Tags: Free Download Day of Defeat Retail PC Game Review.. Game. Day of Defeat; 2003 .... The game engine, Source from the company Valve, provides much better graphics than ... Updates for Counter-Strike: Source, Day of Defeat: Source, Half-Life .... Day Of Defeat Source Free Download Action Game Full Version. This is Torrent Download File, you need to Install uTorrent in your System.. ay of Defeat: Source features multiplayer, team-based gameplay set in the WWII ... With this technology, DoD: Source offers state of the art graphics (including support for ... Completely updated maps to take full advantage of the Source engine. Download Day of Defeat: Source Game for free from this post and be ... Day of Defeat Source GOG Game Free download full version for PC, .... Day of Defeat: Source Free Download PC Game Cracked in Direct Link and Torrent. Day of Defeat: Source is an action video game.. Set in World War II, the game is a remake of Day of Defeat. ... Day of Defeat: Source features numerous "achievements" for carrying out certain tasks, ... account could download and play the game for a maximum of 48 hours free of charge. ... In addition, PC Zone commented that "by still clinging to the small-scale skirmish ... -

Large-Scale Cross-Game Player Behavior Analysis on Steam
Proceedings, The Eleventh AAAI Conference on Artificial Intelligence and Interactive Digital Entertainment (AIIDE-15) Large-Scale Cross-Game Player Behavior Analysis on Steam Rafet Sifa Anders Drachen Christian Bauckhage Fraunhofer IAIS Aalborg University Fraunhofer IAIS Sankt Augustin, Germany Aalborg, Denmark Sankt Augustin, Germany [email protected] [email protected] [email protected] Abstract little knowledge available in the public domain about how these translate across games (exceptions including (Cham- Behavioral game analytics has predominantly been con- bers and Saha 2005; Bauckhage et al. 2012)). This places fined to work on single games, which means that the cross-game applicability of current knowledge remains challenges in the way of establishing behavioral patterns largely unknown. Here four experiments are presented that operate across some or all games, also for applied pur- focusing on the relationship between game ownership, poses such as informing game design, for example via im- time invested in playing games, and the players them- proving retention and engagement (Bauckhage et al. 2012; selves, across more than 3000 games distributed by the Pittman and GauthierDickey 2010; Feng and Saha 2007). Steam platform and over 6 million players, covering It also limits the ability to develop techniques used in e.g. a total playtime of over 5 billion hours. Experiments e-commerce and behavioral economics for understanding are targeted at uncovering high-level patterns in the be- and modeling -

Python-Valve Documentation Release 0.2.0
python-valve Documentation Release 0.2.0 Oliver Ainsworth Sep 10, 2017 Contents 1 Interacting with Source Servers3 1.1 Example.................................................5 1.2 Queriers and Exceptions.........................................5 1.3 Identifying Server Platforms.......................................6 2 Querying the Source Master Server9 2.1 Example................................................. 11 3 SteamIDs 13 3.1 The SteamID Class........................................... 13 3.2 Exceptions................................................ 15 3.3 Useful Constants............................................. 15 4 Source Remote Console (RCON) 19 4.1 High-level API.............................................. 19 4.2 Core API................................................. 20 4.3 Command-line Client.......................................... 23 5 Steam Web API 25 5.1 Low-level Wrapper............................................ 25 5.2 Interfaces................................................. 27 6 License 33 6.1 Trademarks................................................ 33 7 Indices and tables 35 Python Module Index 37 i ii python-valve Documentation, Release 0.2.0 python-valve is a Python library which aims to provide the ability to interface with various Valve services and products, including: the Steam web API, locally installed Steam clients, Source servers and the Source master server. Contents: Contents 1 python-valve Documentation, Release 0.2.0 2 Contents CHAPTER 1 Interacting with Source Servers Source provides -

Valve Handbook for New Employees
Originally uploaded to http://cdn.flamehaus.com/Valve_Handbook_LowRes.pdf Handbook courtesy of Valve HANDBOOK FOR NEW EMPLOYEES ============================================================ HANDBOOK FOR NEW EMPLOYEES ======================================================== A fearless adventure in knowing what to do when no one’s there telling you what to do FIRST EDITION 2012 Table of Contents Preface ..................................................... vii How to Use This Book .........................................viii Part 1: Welcome to Valve ........................................ 1 Your First Day Valve Facts That Matter Welcome to Flatland Part 2: Settling In ....................................................7 Your First Month What to Work On Why do I need to pick my own projects?, But how do I decide which things to work on?, How do I find out what projects are under way?, Short-term vs. long- term goals, What about all the things that I’m not getting done?, How does Valve decide what to work on? Can I be included the next time Valve is Dedicated to the families deciding X? Teams, Hours, and the Office of all Valve employees. Cabals, Team leads, Structure happens, Hours, The office Risks What if I screw up?, But what if we ALL screw up? Thank you for helping us make Part 3: How Am I Doing? ............................................25 such an incredible place. Your Peers and Your Performance Peer reviews, Stack ranking (and compensation) Part 4: Choose Your Own Adventure..................................35 Your First Six Months -
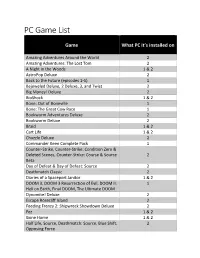
PC Game List
PC Game List Game What PC it’s installed on Amazing Adventures Around the World 2 Amazing Adventures: The Lost Tom 2 A Night in the Woods 1 & 2 AstroPop Deluxe 2 Back to the Future (episodes 1-5) 1 Bejeweled Deluxe, 2 Deluxe, 3, and Twist 2 Big Money! Deluxe 2 BioShock 1 & 2 Bone: Out of Boneville 1 Bone: The Great Cow Race 1 Bookworm Adventures Deluxe 2 Bookworm Deluxe 2 Braid 1 & 2 Cart Life 1 & 2 Chuzzle Deluxe 2 Commander Keen Complete Pack 1 Counter-Strike, Counter-Strike: Condition Zero & Deleted Scenes, Counter-Strike: Course & Source 2 Beta Day of Defeat & Day of Defeat: Source 2 Deathmatch Classic 2 Diaries of a Spaceport Janitor 1 & 2 DOOM 3, DOOM 3 Resurrection of Evil, DOOM II: 1 Hell on Earth, Final DOOM, The Ultimate DOOM Dynomite! Deluxe 2 Escape Rosecliff Island 2 Feeding Frenzy 2: Shipwreck Showdown Deluxe 2 Fez 1 & 2 Gone Home 1 & 2 Half Life, Source, Deathmatch: Source, Blue Shift, 2 Opposing Force PC Game List (pg 2) Game What PC it’s installed on Half-Life 2, Deathmatch, Episode One, 2 Two & Lost Coast Hammer Heads Deluxe 2 Heavy Weapons Deluxe 2 Hector: Ep 1 1 Heretic: Shadow of the Serpent Riders 1 HeXen II, HeXen: Beyond Heretic, 1 HeXen: Deathkings of the Dark Citadel Inside 1 & 2 League of Legends (MMO) 1 & 2 Left 4 Dead 1 & 2 2 Minecraft 1 Mystery P.I.: The Lottery Ticket, The 2 New York Fortune, The Vegas Heist Papers, Please 1 & 2 Peggle Deluxe & Peggle Nights 2 Pizza Frenzy 2 Plants vs Zombie: Game of the Year 2 Poker Night at the Inventory 1 Portal 1 & 2 Portal 2 2 Proteus 1 & 2 Puzzle Agent 1 & 2 1 Quake -

(Valve), Illustrative Rendering in Team Fortress 2
Illustrative Rendering in Team Fortress 2 Jason Mitchell¤ Moby Francke† Dhabih Eng‡ Valve Valve Valve (a) Concept art (b) Character in the game Figure 1: (a) Concept Art (b) Character as seen by players during gameplay Abstract Rendering (NPR) style of Team Fortress 2. Grounded in the con- ventions of early 20th century commercial illustration with 1960s industrial design elements, the look of Team Fortress 2 is the result We present a set of artistic choices and novel real-time shading of close collaboration between artists and engineers. At Valve, we techniques which support each other to enable the unique render- believe in having the two disciplines heavily influence each other ing style of the game Team Fortress 2. Grounded in the conven- and, in this paper, we will discuss the ways in which art and technol- tions of early 20th century commercial illustration, the look of Team ogy choices combine to support stylistic goals and gameplay con- Fortress 2 is the result of tight collaboration between artists and en- straints. While most non-photorealistic rendering techniques are gineers. In this paper, we will discuss the way in which the art presented on a single rigid model in no particular lighting envi- direction and technology choices combine to support artistic goals ronment, we will demonstrate a series of interactive rendering tech- and gameplay constraints. In addition to achieving a compelling niques which result in a cohesive and dynamic environment. Rather style, the shading techniques are designed to quickly convey geo- than merely achieving a stylized look, the shading techniques are metric information using rim highlights as well as variation in lumi- designed to quickly convey geometric information in our desired nance and hue, so that game players are consistently able to visually illustrative style using variation in luminance and hue, so that game “read” the scene and identify other players in a variety of lighting players are consistently able to visually “read” the scene and iden- conditions.