35:2 Berkeley Technology Law Journal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Last Chapter of the Vietnam War: Normalization, Nongovernmental Actors and the Politics of Human Rights, 1975-1995
University of New Hampshire University of New Hampshire Scholars' Repository Doctoral Dissertations Student Scholarship Spring 2017 The Last Chapter of the Vietnam War: Normalization, Nongovernmental Actors and the Politics of Human Rights, 1975-1995 Amanda C. Demmer University of New Hampshire, Durham Follow this and additional works at: https://scholars.unh.edu/dissertation Recommended Citation Demmer, Amanda C., "The Last Chapter of the Vietnam War: Normalization, Nongovernmental Actors and the Politics of Human Rights, 1975-1995" (2017). Doctoral Dissertations. 153. https://scholars.unh.edu/dissertation/153 This Dissertation is brought to you for free and open access by the Student Scholarship at University of New Hampshire Scholars' Repository. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of University of New Hampshire Scholars' Repository. For more information, please contact [email protected]. THE LAST CHAPTER OF THE VIETNAM WAR: NORMALIZATION, NONGOVERNMENTAL ACTORS AND THE POLITICS OF HUMAN RIGHTS, 1975-1995 BY AMANDA C. DEMMER B.A., State University of New York at Fredonia, 2010 M.A., University of New Hampshire, 2012 DISSERTATION Submitted to the University of New Hampshire in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy in History May, 2017 ALL RIGHTS RESERVED © 2017 Amanda C. Demmer ii This dissertation has been examined and approved in partial fulfillment of the requirements for the degree of Ph.D. in History by: Dissertation Director, Kurkpatrick Dorsey, Professor of History and History Graduate Program Director Lucy E. Salyer, Associate Professor of History Jessica M. Lepler, Associate Professor of History Lien-Hang T. -

Download PDF File
from the 33rd Annual Camden Conference The Media Revolution: Changing the World Nicco Mele , Nic Newman , Joshua Tucker , Jeff Jarvis , Courtney Radsch , Maria Ressa , Lydia Cacho Ribeiro , Jason Rezaian, Yeganeh Rezaian, Kathleen Hall Jamieson, David Brancaccio 2020 BOARD OF DIRECTORS Matthew Storin, President Karin Look, Vice President Don Abbott, Treasurer Wayne Hobson, Secretary John Doughty Peter Fitzgerald James Hengerer Peter Imber Elaine Keyes Eric Lebson Emily Lusher Merlin Miller Jane Nyce Sandra Ruch Charlotte Singleton Ward Wickwire About the Camden Conference ow in its 33rd year, this midwinter event in Midcoast Maine is routinely cited ADVISORY COUNCIL as an outstanding example of civic engagement, as it brings in experts from Richard Anderson Naround the world to discuss and debate issues of international import. This David Babski past February, speaker Kathleen Hall Jamieson of the University of Pennsylvania Ann Beaudry hailed the Camden Conference as “democratic engagement in action.” John Bird The three-day event plays out before a capacity audience in the beautiful Camden Bruce Cole Opera House and is live-streamed to locations in Portland, Belfast, and Rockland, as John Davidson well as Hanover, N.H. Each of the Maine locations includes a contingent of students Thomas M. Deford from high schools and colleges throughout the state, who study the topic as part of Leslie Fillnow their curriculum in the months prior. Additional social and substantive activities are Will Galloway planned for those students in the various locations over the course of the weekend. Charlie Graham The Camden Conference is primarily a volunteer organization with just two paid Kathleen Hirsch staff members. -

George Mousourakis*, Comprarative Law, Legal Transplants and Legal Change
George Mousourakis*, Comprarative Law, Legal Transplants and Legal Change Abstract: The changes in the legal universe that have been taking place in the last few decades have increased the potential value of different kinds of comparative law information and thereby urged new objectives for the comparative law community. The comparative method, which was earlier applied in the traditional framework of domestic law, is now being adapted to the new needs created by the ongoing globalization process, becoming broader and more comprehensive with respect to both its scope and goals. Associated with this development is a growing interest in the question of transferability or transplantability of legal norms and institutions across different cultures, especially in so far as current legal integration and harmonization processes require reasonably transferable models. This paper critically examines the issue of transferability of laws with particular attention to the theory of legal transplants propounded by Professor Alan Watson, one of the most influential contemporary comparatists and legal historians. It is submitted that the element of relativity imposed by the special relationship of the law to its socio-cultural environment must be taken into consideration when the comparative method is applied. However, the view held by some scholars that legal transplants are impossible betrays an exaggeration of cultural diversity as it contradicts the teachings of history and is at odds with recent trends towards legal integration in certain world regions. Keywords: Comparative law, reception of laws, legal harmonization, families of law, legal transplants, legal chang Introductory At a time when our world society is increasingly mobile and legal life is internationalized, the role of comparative law is gaining importance. -

Julius-Kühn-Archiv Everyone Interested
ICP-PR Honey Bee Protection Group 1980 - 2017 The ICP-PR Bee Protection Group held its rst meeting in Wageningen in 1980 and over the subsequent 38 years it has become the established expert forum for discussing the risks of pesticides to bees and developing solutions how to assess and manage this risk. In recent years, the Bee Protection Group has enlarged its scope of interest from honey bees to many other pollinating insects, such as wild bees including bumble bees. 462 The group organizes international scienti c symposia, usually once in every three years. These are open to Julius-Kühn-Archiv everyone interested. The group tries to involve as many countries as possible, by organizing symposia each time in another European country. It operates with working groups studying speci c problems and propo- Pieter A. Oomen, Jens Pistorius (Editors) sing solutions that are subsequently discussed in plenary symposia. A wide range of international experts active in this eld drawn from regulatory authorities, industry, universities and research institutes participate in the discussions. Hazards of pesticides to bees In the past decade the symposium has largely extended beyond Europe, and is established as the internatio- nal expert forum with participants from several continents. 13th International Symposium of the ICP-PR Bee Protection Group 18. - 20. October 2017, València (Spain) - Proceedings - International Symposium of the ICP-PR Bee Group Protection of the ICP-PR Symposium International th Hazards of pesticides to bees of pesticides - 13 to Hazards 462 2018 Julius Kühn-Institut Bundesforschungsinstitut für Kulturp anzen Julius Kühn-Institut, Bundesforschungsinstitut für Kulturpflanzen (JKI) Veröffentlichungen des JKI Das Julius Kühn-Institut ist eine Bundesoberbehörde und ein Bundesforschungsinstitut. -

Taking Better Account: Contemporary Slavery, Gendered Narratives, and the Feminization of Struggle
Samuel Martı´nez Taking Better Account: Contemporary Slavery, Gendered Narratives, and the Feminization of Struggle Women are taking leading roles in redefining social concepts and global policy issues in areas such as development, democracy, human rights, world security, and the environment. This means not just looking at what have been called ‘‘women’s issues’’—a ghetto, or separate sphere that remains on the margins of society—but rather moving women from the margins to the center by questioning the most fundamental concepts of our social order so that they take better account of women’s lives.1 Not just ‘‘victims’’ but perpetrators and responders, too, are characters whose stories and personal details convey the gendered character of human rights reporting. Accepting this fact and considering that male responders and perpetrators feature in human rights narratives more often than female, it also follows that male as well as female gender constructs are encoded in human rights narratives. These prin- ciples—that gender is a salient dimension of the construction of all three figures in Makau Mutua’s triumvirate of ‘‘saint, savage and victim,’’ and that preconceptions about masculinity as well as femininity give texture and emotional depth to human rights representations—are the starting point for my reading of the gender of human rights narratives.2 A feminist reading, following Charlotte Bunch’s words in the epigraph, means not just looking at ‘‘women’s issues’’ but questioning fundamental aspects of the social order. Are there aspects of the global social order that, when taken for granted within human rights discourse, work in tandem with assumed aspects of small-scale social orders to relegate women and derogated minorities to silence and passivity? I present evidence that such exclusionary effects are real but operate subtly—blanket critique of human rights is not what I seek and it is not my point to style human rights the handmaiden of a new imperialism. -
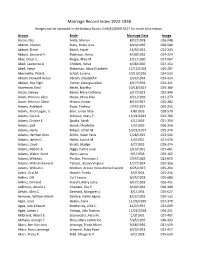
Marriage Record Index 1922-1938 Images Can Be Accessed in the Indiana Room
Marriage Record Index 1922-1938 Images can be accessed in the Indiana Room. Call (812)949-3527 for more information. Groom Bride Marriage Date Image Aaron, Elza Antle, Marion 8/12/1928 026-048 Abbott, Charles Ruby, Hallie June 8/19/1935 030-580 Abbott, Elmer Beach, Hazel 12/9/1922 022-243 Abbott, Leonard H. Robinson, Berta 4/30/1926 024-324 Abel, Oscar C. Ringle, Alice M. 1/11/1930 027-067 Abell, Lawrence A. Childers, Velva 4/28/1930 027-154 Abell, Steve Blakeman, Mary Elizabeth 12/12/1928 026-207 Abernathy, Pete B. Scholl, Lorena 10/15/1926 024-533 Abram, Howard Henry Abram, Elizabeth F. 3/24/1934 029-414 Absher, Roy Elgin Turner, Georgia Lillian 4/17/1926 024-311 Ackerman, Emil Becht, Martha 10/18/1927 025-380 Acton, Dewey Baker, Mary Cathrine 3/17/1923 022-340 Adam, Herman Glen Harpe, Mary Allia 4/11/1936 031-273 Adam, Herman Glenn Hinton, Esther 8/13/1927 025-282 Adams, Adelbert Pope, Thelma 7/14/1927 025-255 Adams, Ancil Logan, Jr. Eiler, Lillian Mae 4/8/1933 028-570 Adams, Cecil A. Johnson, Mary E. 12/21/1923 022-706 Adams, Crozier E. Sparks, Sarah 4/1/1936 031-250 Adams, Earl Snook, Charlotte 1/5/1935 030-250 Adams, Harry Meyer, Lillian M. 10/21/1927 025-376 Adams, Herman Glen Smith, Hazel Irene 2/28/1925 023-502 Adams, James O. Hallet, Louise M. 4/3/1931 027-476 Adams, Lloyd Kirsch, Madge 6/7/1932 028-274 Adams, Robert A. -

ZIMBABWE COUNTRY of ORIGIN INFORMATION (COI) REPORT COI Service
ZIMBABWE COUNTRY OF ORIGIN INFORMATION (COI) REPORT COI Service 25 March 2011 ZIMBABWE 25 MARCH 2011 Contents Preface Latest News EVENTS IN ZIMBABWE FROM 22 FEBRUARY 2011 TO 24 MARCH 2011 Useful news sources for further information REPORTS ON ZIMBABWE PUBLISHED OR ACCESSED BETWEEN 22 FEBRUARY 2011 AND 24 MARCH 2011 Paragraphs Background Information 1. GEOGRAPHY ............................................................................................................ 1.01 Public holidays ..................................................................................................... 1.06 Map ........................................................................................................................ 1.07 2. ECONOMY ................................................................................................................ 2.01 Remittances .......................................................................................................... 2.06 Sanctions .............................................................................................................. 2.08 3. HISTORY (19TH CENTURY TO 2008)............................................................................. 3.01 Matabeleland massacres 1983 - 87 ..................................................................... 3.03 Political events: late 1980s - 2007...................................................................... 3.06 Events in 2008 - 2010 ........................................................................................... 3.23 -

Amnesty International, Human Rights & U.S. Policy
AMNESTY INTERNATIONAL, HUMAN RIGHTS & U.S. POLICY Maria Baldwin A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY December 2006 Committee: Gary R. Hess, Advisor Franklin W. Goza Graduate Faculty Representative Robert Buffington Douglas Forsyth ii ABSTRACT Gary R. Hess, Advisor This dissertation assesses Amnesty International’s ability to influence U.S. foreign policy through an examination of its human rights campaigns in three different nations—Guatemala, the United States and the People’s Republic of China. While these nations are quite different from one another, according to Amnesty International they share an important characteristic; each nation has violated their citizens’ human rights. Sometimes the human rights violations, which provoked Amnesty International’s involvement occurred on a large scale; such as the “disappearances” connected with Guatemala’s long civil war or the imprisonment of political dissidents in the PRC. Other times the human rights violations that spurred Amnesty International’s involvement occurred on a smaller-scale but still undermined the Universal Declaration of Human Rights; such as the United States use of capital punishment. During the Guatemalan and Chinese campaigns Amnesty International attempted to influence the United States relations with these countries by pressuring U.S. policymakers to construct foreign policies that reflected a grave concern for institutionalized human rights abuse and demanded its end. Similarly during its campaign against the United States use of the death penalty Amnesty International attempted to make it a foreign policy liability for the United States. How effective Amnesty International has been in achieving these goals is the subject of this dissertation. -

Summer Newsletter 2012
Summer 2012 Let’s Network! Hero’s daughter visits Oxford House Members who have visited the ZA office will Like Zimbabwe know that just along the passage is the Oxford Association on House chapel, a beautiful wood-panelled room Facebook and Join that in past times was regularly used for prayer and worship and today is also used for commu- in our debates nity events and activities. On the wall of the chapel are several plaques to past wardens of Oxford House, founded in 1884 as a Church of England university settlement. One of these is dedicated to Guy Clutton-Brock and his wife Molly, who took over Oxford House in 1940 and ran it through years of World War II. Their doors were open to all as a refuge from the bombing of London and the stress of the conflict. Friday 18 May saw the launch of ZA’s new cultural platform Sally Clutton-Brock, now Sally Roschnik, was Zimbabwe Unwound: A project creat ing non partisan and Guy and Molly’s only child, born and brought up empowering platforms for Zimbabwean Refugees and the wider in Oxford House before the family moved to community. Zimbabwe, then Rhodesia, and founded the non- Truly fantastic music from Mashasha and Sam, plus some racial co-operative, Cold Comfort Farm. They striking poems from Kennedy Madhorimbo, and Vivian Mara- lived in Zimbabwe until Guy was stripped of his vanyika taking us down memory lane with a DJ set of Zimbab- citizenship and deported by Ian Smith. After his wean Classical music made for a really memorable evening. -

Law Enforcement Agency Directory
Michigan Law Enforcement Agencies 08/16/2021 ADRIAN POLICE DEPARTMENT ALBION DPS ALLEGAN POLICE DEPARTMENT CHIEF VINCENT P EMRICK CHIEF SCOTT KIPP CHIEF JAY GIBSON 155 E. MAUMEE STREET 112 W CASS ST 170 MONROE ST ADRIAN MI 49221 ALBION MI 49224 ALLEGAN MI 49010 TX: 517-264-4846 TX: 517-629-3933 TX: 269-673-2115 FAX: 517-264-1927 FAX: 517-629-7828 FAX: 269-673-5170 ADRIAN TOWNSHIP POLICE ALCONA COUNTY SHERIFFS OFFICE ALLEN PARK POLICE DEPARTMENT SHERIFF SCOTT A. STEPHENSON DEPARTMENT CHIEF GARY HANSELMAN 214 WEST MAIN CHIEF CHRISTOPHER S EGAN 2907 TIPTON HWY HARRISVILLE MI 48740 15915 SOUTHFIELD RD ADRIAN MI 49221 TX: 989-724-6271 ALLEN PARK MI 48101 TX: 517-264-1000 FAX: 989-724-6181 TX: 313-386-7800 FAX: 517-265-6300 FAX: 313-386-4158 ALGER COUNTY SHERIFFS OFFICE ADRIAN-BLISSFIELD RAILROAD SHERIFF TODD BROCK ALLEN PARK POLICE POLICE 101 EAST VARNUM STE B DEPARTMENT CHIEF MARK W. DOBRONSKI MUNISING MI 49862 CHIEF CHRISTOPHER S EGAN 38235 N. EXECUTIVE DR. TX: 906-387-4444 15915 SOUTHFIELD RD WESTLAND MI 48185 FAX: 906-387-1728 ALLEN PARK MI 48101 TX: 734-641-2300 TX: 313-386-7800 FAX: 734-641-2323 ALLEGAN COUNTY SHERIFFS FAX: OFFICE AKRON POLICE DEPARTMENT SHERIFF FRANK BAKER ALMA DEPARTMENT OF PUBLIC CHIEF MATTHEW SIMERSON 640 RIVER ST. SAFETY 4380 BEACH STREET ALLEGAN MI 49010 CHIEF KENDRA OVERLA P.O. BOX 295 TX: 269-673-0500 525 EAST SUPERIOR AKRON MI 48701 FAX: 269-673-0406 ALMA MI 48801 TX: 989-691-5354 TX: 989-463-8317 FAX: 989-691-5423 FAX: 989-463-6233 Michigan Law Enforcement Agencies 08/16/2021 ALMONT POLICE DEPARTMENT AMTRAK RAILROAD POLICE ARGENTINE TOWNSHIP POLICE CHIEF ANDREW MARTIN DEPUTY CHIEF JOSEPH DEPARTMENT 817 NORTH MAIN PATTERSON CHIEF DANIEL K ALLEN ALMONT MI 48003 600 DEY ST. -

2012 Annual Report
The year kicked off with a long-awaited Indiana specialty license plate and concluded with a With the groundbreaking ceremony of the International Orangutan record-breaking Christmas celebration. In between, animal conservation was at the forefront in Center came a game-changing moment – this time for orangutans here many ways and included the opening of the outstanding exotic bird exhibit Flights of Fancy, and in the wild. The Center is a unique facility specifically designed to noteworthy births of an elephant and dolphin, and arrivals of a rescued sea lion and baby meet the physical, social, and intellectual needs of these endangered INDIANAPOLIS ZOO walrus. The traditional crowd-pleasing seasonal celebrations also filled the year. And don’t great apes. Its centerpiece, a 150-foot beacon that will be illuminated Annual Report 2012 forget White River Gardens, where orchids flourished in a salute to the natural world. by lights the orangutans turn on, represents the hope that the species not only will survive but also thrive in a world-class environment. Changing the game FOR an ge endangered The Indianapolis Prize Gala showcased our passion for preservation, as this fourth biennial award lauded a distinguished polar bear researcher. The honor was so prestigious it was called the Nobel Prize for the animal conservation world. neration Your generous support is why we celebrate another successful, transformative year. Look inside as we remember some of the highlights and anticipate the challenges ahead. Was 2012 the best year ever for your Indianapolis Zoo? It certainly felt like it. Making a difference for natural world natural for Making adifference THE Dear Friends: We often hear experts speak of the “transformative” power of various entities or ideas. -

Annual Report 2005
2416/D/Rev.1 International Atomic Energy Agency Coordinated Research Activities Annual Report and Statistics for 2007 July 2008 Research Contracts Administration Section Department of Nuclear Sciences and Applications International Atomic Energy Agency http://cra.iaea.org/ TABLE OF CONTENTS EXECUTIVE SUMMARY..................................................................................................................... ii 1. INTRODUCTION .........................................................................................................................1 2. COORDINATED RESEARCH ACTIVITIES IN SUPPORT OF IAEA PROGRAMMES AND SUBPROGRAMMES ..........................................................................................................2 3. COORDINATED RESEARCH ACTIVITIES IN 2007................................................................3 3.1. Member State Participation ..........................................................................................11 3.2. Extra Budgetary Funding..............................................................................................12 3.3. Coordinated Research Projects Completed in 2007 .....................................................12 4. CRP EVALUATION REPORTS FOR COMPLETED CRPS ....................................................13 ANNEX I Total Number of Proposals Received and Awards Made in 2007 ANNEX II Distribution of Total 2007 Contract Awards by Country and Programme ANNEX III Research Coordination Meetings Held in 2007 by Subprogramme ANNEX IV Countries