Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browsers and Their Use in Smart Devices
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Alina Kogai 179247IACB Browsers and their use in smart devices Bachelor’s thesis Supervisor: Vladimir Viies Associate Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Alina Kogai 179247IACB Brauserid ja nende kasutamine nutiseadmetes Bakalaureusetöö Juhendaja: Vladimir Viies Dotsent Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Alina Kogai 30.11.2020 3 BAKALAUREUSETÖÖ ÜLESANDEPÜSTITUS Kuupäev: 23.09.2020 Üliõpilase ees- ja perekonnanimi: Alina Kogai Üliõpilaskood: 179247IACB Lõputöö teema: Brauserid ja nende kasutamine nutiseadmetes Juhendaja: Vladimir Viies Kaasjuhendaja: Lahendatavad küsimused ning lähtetingimused: Populaarsemate brauserite analüüs. Analüüs arvestada: mälu kasutus, kiirus turvalisus ja privaatsus, brauserite lisad. Valja toodate brauseri valiku kriteeriumid ja soovitused. Lõpetaja allkiri (digitaalselt allkirjastatud) 4 Abstract The aim of this bachelor's thesis is to give recommendations on which web browser is best suited for different user groups on different platforms. The thesis presents a methodology for evaluating browsers which are available on all platforms based on certain criteria. Tests on PC, mobile and tablet were performed for methodology demonstration. To evaluate the importance of the criteria a survey was conducted. The results are used to make recommendations to Internet user groups on the selection of the most suitable browser for different platforms. This thesis is written in English and is 43 pages long, including 5 chapters, 20 figures and 18 tables. 5 Annotatsioon Brauserid ja nende kasutamine nutiseadmetes Selle bakalaureuse töö eesmärk on anda nõuandeid selle kohta, milline veebibrauser erinevatel platvormitel sobib erinevate kasutajagruppide jaoks kõige parem. -

A Testing Strategy for Html5 Parsers
A TESTING STRATEGY FOR HTML5 PARSERS A DISSERTATION SUBMITTED TO THE UNIVERSITY OF MANCHESTER FOR THE DEGREE OF MASTER OF SCIENCE IN THE FACULTY OF ENGINEERING AND PHYSICAL SCIENCES 2015 By Jose´ Armando Zamudio Barrera School of Computer Science Contents Abstract 9 Declaration 10 Copyright 11 Acknowledgements 12 Dedication 13 Glossary 14 1 Introduction 15 1.1 Aim . 16 1.2 Objectives . 16 1.3 Scope . 17 1.4 Team organization . 17 1.5 Dissertation outline . 17 1.6 Terminology . 18 2 Background and theory 19 2.1 Introduction to HTML5 . 19 2.1.1 HTML Historical background . 19 2.1.2 HTML versus the draconian error handling . 20 2.2 HTML5 Parsing Algorithm . 21 2.3 Testing methods . 23 2.3.1 Functional testing . 23 2.3.2 Oracle testing . 25 2.4 Summary . 26 2 3 HTML5 parser implementation 27 3.1 Design . 27 3.1.1 Overview . 27 3.1.2 State design pattern . 29 3.1.3 Tokenizer . 31 3.1.4 Tree constructor . 32 3.1.5 Error handling . 34 3.2 Building . 34 3.3 Testing . 35 3.3.1 Tokenizer . 35 3.3.2 Tree builder . 36 3.4 Summary . 37 4 Test Framework 38 4.1 Design . 38 4.1.1 Architecture . 38 4.1.2 Adapters . 39 4.1.3 Comparator and plurality agreement . 41 4.2 Building . 42 4.2.1 Parser adapters implementations . 43 4.2.2 Preparing the input . 43 4.2.3 Comparator . 44 4.3 Other framework features . 45 4.3.1 Web Interface . 45 4.3.2 Tracer . -

Opera Software the Best Browsing Experience on Any Device
Opera Software The best browsing experience on any device The best Internet experience on any device Web Standards for the Future – Bruce Lawson, Opera.com • Web Evangelist, Opera • Tech lead, Law Society & Solicitors Regulation Authority (2004-8) • Author 2 books on Web Standards, edited 2 • Committee member for British Standards Institution (BSI) for the new standard for accessible websites • Member of Web Standards Project: Accessibility Task Force • Member of W3C Mobile Best Practices Working Group Web Standards for the Future – Bruce Lawson, Opera.com B.A., Honours English Literature and Language with Drama Theresa is blind But she can use the Web if made with standards The big picture WWW The big picture Western Western Web A web (pre)history • 1989 TBL proposes a project • 1992 <img> in Mosaic beta. Now 99.57% (MAMA) • 1994 W3C started at MIT • 1996 The Browser Wars • 1999 WAP, Web Content Accessibility Guidelines (WCAG) • 2000 Flash Modern web history • 2000-ish .com Crash - Time to grow up... • 2002 Opera Mobile with Small Screen Rendering • 2005 WHAT-WG founded, W3C Mobile Web Initiative starts • 2007 W3C adopts WHAT-WG spec as basis for HTML 5 • January 22, 2008 First public working draft of HTML 5 Standards at Opera • 25 employees work on standards • Mostly at W3C - a big player • Working on many standards • Bringing new work to W3C • Implementing Standards properly (us and you!) (Web Standards Curriculum www.opera.com/wsc) Why standards? The Web works everywhere - The Web is the platform • Good standards help developers: validate; separate content and presentation - means specialisation and maintainability. -

Opera Mini Opera Mobile Shipments Pre-Installed in 4Q08: 7.3 Million
Opera Software Fourth quarter 2008 A note from our lawyers 2 This presentation contains and is, i.a., based on forward-looking statements. These statements involve known and unknown risks, uncertainties and other factors which may cause our actual results, performance or achievements to be materially different from any future results, performances or achievements expressed or implied by the forward-looking statements . Forward-looking statements may in some cases be identified by terminology such as “may”, “will”, “could”, “should”, “expect”, “plan”, “intend”, “anticipate”, “believe”, “estimate”, “predict”, “pp,gpgyotential” or “continue”, the negative of such terms or other comparable terminology. These statements are only predictions. Actual events or results may differ materially, and a number of factors may cause our actual results to differ materially from any such statement. Although we believe that the expectations and assumptions reflected in the statements are reasonable, we cannot guarantee future results, levels of activity, performance or achievement. Opera Software ASA makes no representation or warranty (express or implied) as to the correctness or completeness of the presentation, and neither Opera Software ASA nor any of its direc tors or emp loyees assumes any lia bility resu lting from use. Excep t as requ ire d by law, we undertake no obligation to update publicly any forward-looking statements for any reason after the date of this presentation to conform these statements to actual results or to changes in our expectations. You are advised, however, to consult any further public disclosures made by us, su ch as filings made w ith the OSE or press releases . -
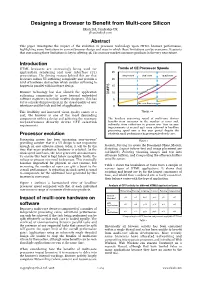
Designing a Browser to Benefit from Multi-Core Silicon
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

Designing Beneath the Surface of the Web Sarah Horton Dartmouth College 6224 Baker/Berry Hanover, NH 03755 USA 603 646-1087 [email protected]
Designing Beneath the Surface of the Web Sarah Horton Dartmouth College 6224 Baker/Berry Hanover, NH 03755 USA 603 646-1087 [email protected] ABSTRACT clarity influence how well software can read and interpret the At its most basic, the web allows for two modes of access: visual source code. Nonvisual web access can be improved by applying and non-visual. For the most part, our design attention is focused the following guidelines for source code design. on making decisions that affect the visual, or surface, layer — Shneiderman defines universal usability as an approach to design colors and type, screen dimensions, fixed or flexible layouts. that is focused on “enabling all citizens to succeed in using However, much of the power of the technology lies beneath the information and communication technologies to support their surface, in the underlying code of the page. There, in the unseen tasks” [18]. A focus on page code design improves the universal depths of the page code, we make decisions that influence how usability of web pages by addressing access challenges in a well, or poorly, our pages are read and interpreted by software. In variety of contexts. For instance, the small viewport on mobile this paper, we shift our attention beneath the surface of the web devices presents many of the same challenges as nonvisual access. and focus on design decisions that affect nonvisual access to web This paper concludes with a discussion of how these guidelines pages. can be applied to improve web access for mobile users. Categories and Subject Descriptors 2. -

FOCUS: Shedding Light on the High Search Response Time in the Wild
FOCUS: Shedding Light on the High Search Response Time in the Wild Dapeng Liu†, Youjian Zhao†, Kaixin Sui†, Lei Zou†, Dan Pei†⇤ , Qingqian Tao‡, Xiyang Chen‡, Dai Tan‡ †Tsinghua University †Tsinghua National Laboratory for Information Science and Technology (TNList) ‡Baidu Abstract—Response time plays a key role in Web services, as it 1) What are the HSRT conditions (the combinations of significantly impacts user engagement, and consequently the Web attributes and specific values in search logs which have providers’ revenue. Using a large search engine as a case study, a higher concentration of HSRT)? we propose a machine learning based analysis framework, called FOCUS, as the first step to automatically debug high search 2) Which HSRT condition types are prevalent across days? response time (HSRT) in search logs. The output of FOCUS offers 3) How does each attribute affect SRT in those prevalent a promising starting point for operators’ further investigation. HSRT condition types? FOCUS has been deployed in one of the largest search engines for 2.5 months and analyzed about one billion search logs. The answers to the above questions can offer a promising Compared with a previous approach, FOCUS generates 90% starting point to narrow down the HSRT debugging space to less items for investigation and achieves both higher recall and a few suspect attributes and specific values, based on which higher precision. The results of FOCUS enable us to make several further effective investigation can be done through taking interesting observations. For example, we find that popular advantage of additional data sources (beyond search logs) and queries are more image-intensive (e.g., TV series and shopping), but they have relatively low SRT because they are cached domain knowledge. -

Cloud Computing Bible
Barrie Sosinsky Cloud Computing Bible Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2011 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-90356-8 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, 201-748-6011, fax 201-748-6008, or online at http://www.wiley.com/go/permissions. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. The advice and strategies contained herein may not be suitable for every situation. This work is sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other professional services. -
QNX Web Browser
PRODUCT BRIEF QNX Web Browser The QNX Web Browser, based on the Blink rendering engine, is a state-of-the-art browser designed to address performance, reliability, memory footprint, and security requirements of embedded systems. With a heritage of best-in-class browser technology from BlackBerry, the QNX Web Browser enables a wide range of uses from pure document viewers and video players, to feature-rich application environments in systems such as infotainment head units and in-flight entertainment units. The browser employs a modular, component based architecture that leverages QNX Neutrino® Realtime Operating System’s advanced memory protection, security mechanisms, and concurrency to provide reliable, robust, and responsive performance. Overview Benefits Web applications have been widely used on PCs and mobile • Highly secure browser designed with most advanced QNX devices. These applications are now surfacing in embedded SDP 7.0 security mechanisms systems due to the large developer base to draw from, as well as • Up to 35% lower memory footprint when compared to a general ease of development, deployment, and portability of web Linux-based implementation technologies. Consequently, web browsers are becoming a central • Fully-integrated with other QNX technologies including: component of modern-day embedded systems. o Video playback capabilities of QNX Multimedia Suite To provide an optimal web experience in an embedded system, o Location manager service for geolocation the browser must enable high performance and stability within the o QNX CAR Platform for Infotainment confines of limited system memory. Also of vital importance is adaptability. That is, to ensure a continued optimal browsing • Customization for fine grain control of features, behavior and experience, web browsers must keep pace with upstream appearance development. -

A Multi-Year Quest for the Best Web Test ACT I History of Debugging Protocols 2012 St
A multi-year quest for the best web test ACT I History of Debugging Protocols 2012 St. Petersburg 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Web Inspector Protocol 2012: Web Inspector Protocol Web Inspector protocol 2013: Chrome Forked WebKit! 2013: Chrome DevTools Protocol 2015: Chrome DevTools Protocol - 273 methods - 98 events - Used by IDEs for debugging - Used by Chrome Driver internally 2015 San Francisco 2015 San Francisco 2015 San Francisco 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging ~1.5 years of work! 2015: V8 Debugging 2016: node.js debugging! 2017: Chrome Headless 2017: Chrome Headless 2017: Chrome Headless 2017: Puppeteer 2017: Cross-Browser Puppeteer 2018: puppeteer-firefox “Juggler” protocol 2018: puppeteer-firefox “Juggler” protocol 2019: puppeteer-firefox Remote Debugging Protocols Web Inspector protocol (2009 - ...) Chrome DevTools protocol (2013 - ...) Juggler “Juggler” protocol (2018 - ...) ACT II Browser vs Browser Engine Browser Browser Browser Browser Engine Browser Browser Engine Browser Engines 2020 Chromium (2008 – ...) WebKit (1998 – ...) Gecko (1997 – ...) Browser Engines 2020 Chromium (2008 – ...) Trident (1997 - 2014) WebKit (1998 – ...) EdgeHTML (2014 – 2018) Gecko (1997 – ...) Browser Engines Market Share 2020 Market Share Dynamics 2020 Market Share Dynamics 2020 Web Testing = 3 Browser Engines Chrome / Chromium Safari / WebKit Firefox / Gecko ACT III Web Testing Drama Web Testing Web Testing Web Testing Web Testing + headless Web Testing + headless Web Testing DOES NOT EXIST * + headless Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #2: Automation Technology WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. -

3000 Applications
Uila Supported Applications and Protocols updated March 2021 Application Protocol Name Description 01net.com 05001net plus website, is a Japanese a French embedded high-tech smartphonenews site. application dedicated to audio- 050 plus conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also classifies 10086.cn the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese cloudweb portal storing operated system byof theYLMF 115 Computer website. TechnologyIt is operated Co. by YLMF Computer 115.com Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr ThisKorean protocol shopping plug-in website classifies 11st. the It ishttp operated traffic toby the SK hostPlanet 123people.com. Co. 123people.com Deprecated. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt ChineseLithuanian web news portal portal 163. It is operated by NetEase, a company which pioneered the 163.com development of Internet in China. 17173.com Website distributing Chinese games. 17u.com 20Chinese minutes online is a travelfree, daily booking newspaper website. available in France, Spain and Switzerland. 20minutes This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Checkout (acquired by Verifone) provides global e-commerce, online payments 2Checkout and subscription billing solutions. -

Master Thesis (60 Credits)
UNIVERSITETET I OSLO Department of Informatics Technology, Organization and Learning Email-Practices and Coordination in an Expanding Innovative Organization Master Thesis (60 credits) Jan Henrik Helmers May, 2009 Abstract The use of email has become increasingly popular during the last two decades. For some companies, email is how they communicate and coordinate their work. I have studied the Norwegian company Opera Software and the email practices of its employees, using qualitative methods and lightweight statistics. I argue that the Opera Software employees have become email professionals as a result of the large email volume. They have adapted a company-wide practice of using mailing lists, enabling them to be easily reachable through direct email while at the same time not being drowned in the constant stream of incoming email. I argue that as the company continues to expand, the practice of relying solely on email for coordination is reaching its limits. The mailing lists are segregated and fragmented into new forms, which has potentially limiting consequences for the company’s ability to innovate. Keywords: email, media richness, communication, innovative organizations, work practices, expanding organizations, email overload 2 Preface This thesis is the final deliveryfor completing my study of Technology, Organization and Learning (TOOL), an interdisciplinary program, at the University of Oslo. It is the culmination of several years of study. Bycombining the studies of informatics, sociology and pedagogics, I have deepened my understanding of the complex interplay between technology, its users and the organization surrounding it. My thesis draws inspiration and motivation from working with information technology (IT) professionals, but it is mostly relying on sociological theories for its findings and discussions.