Microsoft Edge Release Date
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Quick Start Guide: Migrating to Always-On
QUICK START GUIDE: MIGRATING TO ALWAYS-ON SSL Now that Google has added a rank boost for Always-On SSL (AOSSL), it makes sense to enable HTTPS across your entire Website. But where do you start? DigiCert created this guide to give you an in-depth look on how AOSSL can help you and to get you started with implementing AOSSL on your own Website. GET YOUR COMPANY ON TOP WITH AOSSL We know you’re always looking for new ways to users immediately recognize them to mean security. make your company stick out—whether that’s in By ranking higher in Google, you will be driving search engine rankings or in your customer’s minds. more traffic; and with the added security benefits of And with Google’s recent announcement that HTTPS SSL your new users will feel confident on your site, everywhere is a factor in their ranking algorithm, SSL positively affecting conversion rates. can be part of your solution. HOW AOSSL BENEFITS YOU Unlike many of the ranking factors in Google’s search The HTTPS everywhere ranking signal is standalone algorithm that are vague or difficult to measure, and is independent from any of Google’s other ranking having HTTPS everywhere is a guaranteed way to get signals or algorithms. As soon as a new HTTPS page your site ranked above your competitors. And though is indexed by Google, you get a boost in your search it’s starting out as a lightweight signal, Google has ranking just because of the HTTPS URL. While this promised that the weight of SSL as a ranking factor doesn’t mean that your page will automatically jump will increase once webmasters have time to migrate up a few ranks in search results, it does mean that you their sites. -

Browsers and Their Use in Smart Devices
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Alina Kogai 179247IACB Browsers and their use in smart devices Bachelor’s thesis Supervisor: Vladimir Viies Associate Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Alina Kogai 179247IACB Brauserid ja nende kasutamine nutiseadmetes Bakalaureusetöö Juhendaja: Vladimir Viies Dotsent Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Alina Kogai 30.11.2020 3 BAKALAUREUSETÖÖ ÜLESANDEPÜSTITUS Kuupäev: 23.09.2020 Üliõpilase ees- ja perekonnanimi: Alina Kogai Üliõpilaskood: 179247IACB Lõputöö teema: Brauserid ja nende kasutamine nutiseadmetes Juhendaja: Vladimir Viies Kaasjuhendaja: Lahendatavad küsimused ning lähtetingimused: Populaarsemate brauserite analüüs. Analüüs arvestada: mälu kasutus, kiirus turvalisus ja privaatsus, brauserite lisad. Valja toodate brauseri valiku kriteeriumid ja soovitused. Lõpetaja allkiri (digitaalselt allkirjastatud) 4 Abstract The aim of this bachelor's thesis is to give recommendations on which web browser is best suited for different user groups on different platforms. The thesis presents a methodology for evaluating browsers which are available on all platforms based on certain criteria. Tests on PC, mobile and tablet were performed for methodology demonstration. To evaluate the importance of the criteria a survey was conducted. The results are used to make recommendations to Internet user groups on the selection of the most suitable browser for different platforms. This thesis is written in English and is 43 pages long, including 5 chapters, 20 figures and 18 tables. 5 Annotatsioon Brauserid ja nende kasutamine nutiseadmetes Selle bakalaureuse töö eesmärk on anda nõuandeid selle kohta, milline veebibrauser erinevatel platvormitel sobib erinevate kasutajagruppide jaoks kõige parem. -

Designing Secure Systems That People Can
15- SSL, PKIs, and Secure Communication Engineering & Public Policy Lorrie Cranor, Blase Ur, and Rich Shay March 3, 2015 05-436 / 05-836 / 08-534 / 08-734 Usable Privacy and Security 1 Today! • An introduction to SSL/TLS • An introduction to PKIs • Recent developments in this area • Usability issues • An activity to make it better 2 Overview • Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS) enable secure communication • Frequently encountered with web browsing (HTTPS) and more behind the scenes in app, VOIP, etc. 3 What we want to defend against • People snooping on our communications – The contents of what we’re sending – Session tokens (see, e.g., Firesheep) • Man-in-the-middle attacks – We want to authenticate that we are talking to the right site, not an imposter – Use certificates inside a public-key infrastructure 4 How we could obtain trust • Web of trust – People you already trust introduce you to people they trust – Can get complicated, doesn’t scale well – Less frequently seen in practice • Public-Key Infrastructure (PKI) – Certificates are issued by certificate authorities that bind cryptographic keys to identities 5 Public-Key Infrastucture • Binding of keys to identities can be done automatically or by humans 6 What does SSL look like to users? • Compare, e.g., the following: – https://www.google.com (normal certificate) – Go to Google images and then click on an image and see what happens (mixed content) – https://otalliance.org (EV certificate) 7 What does PKI look like to browsers? • Hundreds -

A Testing Strategy for Html5 Parsers
A TESTING STRATEGY FOR HTML5 PARSERS A DISSERTATION SUBMITTED TO THE UNIVERSITY OF MANCHESTER FOR THE DEGREE OF MASTER OF SCIENCE IN THE FACULTY OF ENGINEERING AND PHYSICAL SCIENCES 2015 By Jose´ Armando Zamudio Barrera School of Computer Science Contents Abstract 9 Declaration 10 Copyright 11 Acknowledgements 12 Dedication 13 Glossary 14 1 Introduction 15 1.1 Aim . 16 1.2 Objectives . 16 1.3 Scope . 17 1.4 Team organization . 17 1.5 Dissertation outline . 17 1.6 Terminology . 18 2 Background and theory 19 2.1 Introduction to HTML5 . 19 2.1.1 HTML Historical background . 19 2.1.2 HTML versus the draconian error handling . 20 2.2 HTML5 Parsing Algorithm . 21 2.3 Testing methods . 23 2.3.1 Functional testing . 23 2.3.2 Oracle testing . 25 2.4 Summary . 26 2 3 HTML5 parser implementation 27 3.1 Design . 27 3.1.1 Overview . 27 3.1.2 State design pattern . 29 3.1.3 Tokenizer . 31 3.1.4 Tree constructor . 32 3.1.5 Error handling . 34 3.2 Building . 34 3.3 Testing . 35 3.3.1 Tokenizer . 35 3.3.2 Tree builder . 36 3.4 Summary . 37 4 Test Framework 38 4.1 Design . 38 4.1.1 Architecture . 38 4.1.2 Adapters . 39 4.1.3 Comparator and plurality agreement . 41 4.2 Building . 42 4.2.1 Parser adapters implementations . 43 4.2.2 Preparing the input . 43 4.2.3 Comparator . 44 4.3 Other framework features . 45 4.3.1 Web Interface . 45 4.3.2 Tracer . -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -

The Tor Browser
TOR By: Qui Hao (Frank) Yu and Haseeb Choudhary Agenda What is Tor? The Tor Browser What does Tor provide its users? Tor with command line apps The history of Tor Tor vs. VPN What makes up the Tor network? What NOT to do with Tor How does Tor work? - Clients perspective - Onion service perspective What is Tor? Tor stands for The Onion Router It is a open source network run by volunteers which provides its users with enhanced privacy and security on the Internet. Guard Middle Exit Node Server Node What does Tor Provide its Users? ● Who are the users of Tor? Anyone who would like to enhance their privacy and security on the Internet ● What does Tor do to provide more privacy and security for its users? ● Tor prevents websites and other services from knowing your location ● Tor prevents someone monitoring your Internet traffic (e.g. ISP, someone on your home network) from learning where you’re going and what you’re receiving from where you go ● Tor routes your traffic through more than one Tor relay so that no single relay will know both who you are and where you’re going The History of Tor ● Principle of “Onion Routing” ○ Developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory. ○ Developed in mid-1990’s ○ Purpose: protecting U.S. intelligence communication Online ● Alpha version of Tor - The Onion Routing Project ○ Developed by Roger Dingledine, Paul Syverson, and Nick Mathewson ○ Launched on Sept 20th, 2002 ○ Releases a year later ● The Tor Project, Inc, founded in Dec, 2006 What -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -
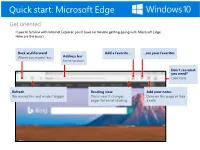
Quick Start: Microsoft Edge
Quick start: Microsoft Edge Get oriented If you’re familiar with Internet Explorer, you’ll have no trouble getting going with Microsoft Edge. Here are the basics. Back and Forward Add a favorite... ...see your favorites Where you expect ‘em. Address bar Same location. Don’t see what you need? Look here. Refresh Reading view Add your notes We moved this and made it bigger. This is new. It changes Draw on this page or take pages for easier reading. a note. Quick start: Microsoft Edge Microsoft Edge makes finding the needles in the internet’s haystack faster and easier. Find answers quickly by typing your question in the address bar. If we’ve got the answer, we’ll show it to you or make a suggestion. 1. Ask your question in the Address bar 2. Find your answer here 3. See other options here Quick start: Microsoft Edge If you’ve got a lot of web reading to do, switch to Reading view and give your eyes a break. Before After Need more contrast or a bigger font? To change settings, select More in the upper-right corner, select Settings, scroll to the Reading section and play with the options. Quick start: Microsoft Edge If you don’t always have internet access, add webpages that you want to read later to your Reading List and you’ll be able to get to them offline, too. 1. Add things to the list 2. Open the list Open a webpage > select the Favorites Hub button > Reading list . button > Reading list > Add. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Web Privacy Beyond Extensions
Web Privacy Beyond Extensions: New Browsers Are Pursuing Deep Privacy Protections Peter Snyder <[email protected]> Privacy Researcher at Brave Software In a slide… • Web privacy is a mess. • Privacy activists and researchers are limited by the complexity of modern browsers. • New browser vendors are eager to work with activists to deploy their work. Outline 1. Background Extension focus in practical privacy tools 2. Present Privacy improvements require deep browser modifications 3. Next Steps Call to action, how to keep improving Outline 1. Background Extension focus in practical privacy tools 2. Present Privacy improvements require deep browser modifications 3. Next Steps Call to action, how to keep improving Browsers are Complicated uBlock PrivacyBadger Disconnect AdBlock Plus Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Extensions as a Compromise uBlock PrivacyBadger Disconnect AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Privacy and Browser Extensions � • Successes! uBlock Origin, HTTPS Everywhere, Ghostery, Disconnect, Privacy Badger, EasyList / EasyPrivacy, etc… • Appealing Easy(er) to build, easy to share • Popular Hundreds of thousands of extensions, Millions of users Browser Extension Limitations � • Limited Capabilities Networking, request modification, rendering, layout, image processing, JS engine, etc… • Security and Privacy Possibly giving capabilities to malicious parties • Performance Limited to JS, secondary access Extensions vs Runtime uBlock PrivacyBadger Disconnect AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Under Explored Space uBlock PrivacyBadger Disconnect ? AdBlock Plus Runtime Extensions modifications Firefox Safari Privacy concern Chrome Edge / IE Browser maintenance experience Outline 1. Background Extension focus in practical privacy tools 2. -
Designing a Browser to Benefit from Multi-Core Silicon
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

The BEAST Wins Again: Why TLS Keeps Failing to Protect HTTP Antoine Delignat-Lavaud, Inria Paris Joint Work with K
The BEAST Wins Again: Why TLS Keeps Failing to Protect HTTP Antoine Delignat-Lavaud, Inria Paris Joint work with K. Bhargavan, C. Fournet, A. Pionti, P.-Y. Strub INTRODUCTION Introduction Cookie Cutter Virtual Host Confusion Crossing Origin Boundaries Shared Session Cache Shared Reverse Proxies SPDY Connection Pooling Triple Handshake Conclusion Why do we need TLS? 1. Authentication – Must be talking to the right guy 2. Integrity – Our messages cannot be tampered 3. Confidentiality – Messages are only legible to participants 4. Privacy? – Can’t tell who we are and what we talk about Why do we need TLS? 1. Authentication – Must be talking to the right guy Active Attacks 2. Integrity (MitM) – Our messages cannot be tampered 3. Confidentiality – Messages are only legible to participants Passive Attacks 4. Privacy? (Wiretapping) – Can’t tell who we are and what we talk about What websites expect of TLS • Web attacker – Controls malicious websites – User visits honest and malicious sites in parallel – Web/MitB attacks: CSRF, XSS, Redirection… • Network attacker – Captures (passive) and tampers (active) packets What websites expect of TLS • Web attacker – Controls malicious websites – User visits honest and malicious sites in parallel – Web/MitB attacks: CSRF, XSS, Redirection… • Network attacker Strictly stronger – Captures (passive) and tampers (active) packets What websites expect of TLS If a website W served over HTTP is secure against a Web attacker, then serving W over HTTPS makes it secure against a network attacker. What websites expect of TLS If a website W served over HTTP is secure against a Web attacker, then serving W over HTTPS makes it secure against a network attacker.