FOCUS: Shedding Light on the High Search Response Time in the Wild
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browsers and Their Use in Smart Devices
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Alina Kogai 179247IACB Browsers and their use in smart devices Bachelor’s thesis Supervisor: Vladimir Viies Associate Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Alina Kogai 179247IACB Brauserid ja nende kasutamine nutiseadmetes Bakalaureusetöö Juhendaja: Vladimir Viies Dotsent Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Alina Kogai 30.11.2020 3 BAKALAUREUSETÖÖ ÜLESANDEPÜSTITUS Kuupäev: 23.09.2020 Üliõpilase ees- ja perekonnanimi: Alina Kogai Üliõpilaskood: 179247IACB Lõputöö teema: Brauserid ja nende kasutamine nutiseadmetes Juhendaja: Vladimir Viies Kaasjuhendaja: Lahendatavad küsimused ning lähtetingimused: Populaarsemate brauserite analüüs. Analüüs arvestada: mälu kasutus, kiirus turvalisus ja privaatsus, brauserite lisad. Valja toodate brauseri valiku kriteeriumid ja soovitused. Lõpetaja allkiri (digitaalselt allkirjastatud) 4 Abstract The aim of this bachelor's thesis is to give recommendations on which web browser is best suited for different user groups on different platforms. The thesis presents a methodology for evaluating browsers which are available on all platforms based on certain criteria. Tests on PC, mobile and tablet were performed for methodology demonstration. To evaluate the importance of the criteria a survey was conducted. The results are used to make recommendations to Internet user groups on the selection of the most suitable browser for different platforms. This thesis is written in English and is 43 pages long, including 5 chapters, 20 figures and 18 tables. 5 Annotatsioon Brauserid ja nende kasutamine nutiseadmetes Selle bakalaureuse töö eesmärk on anda nõuandeid selle kohta, milline veebibrauser erinevatel platvormitel sobib erinevate kasutajagruppide jaoks kõige parem. -

A Testing Strategy for Html5 Parsers
A TESTING STRATEGY FOR HTML5 PARSERS A DISSERTATION SUBMITTED TO THE UNIVERSITY OF MANCHESTER FOR THE DEGREE OF MASTER OF SCIENCE IN THE FACULTY OF ENGINEERING AND PHYSICAL SCIENCES 2015 By Jose´ Armando Zamudio Barrera School of Computer Science Contents Abstract 9 Declaration 10 Copyright 11 Acknowledgements 12 Dedication 13 Glossary 14 1 Introduction 15 1.1 Aim . 16 1.2 Objectives . 16 1.3 Scope . 17 1.4 Team organization . 17 1.5 Dissertation outline . 17 1.6 Terminology . 18 2 Background and theory 19 2.1 Introduction to HTML5 . 19 2.1.1 HTML Historical background . 19 2.1.2 HTML versus the draconian error handling . 20 2.2 HTML5 Parsing Algorithm . 21 2.3 Testing methods . 23 2.3.1 Functional testing . 23 2.3.2 Oracle testing . 25 2.4 Summary . 26 2 3 HTML5 parser implementation 27 3.1 Design . 27 3.1.1 Overview . 27 3.1.2 State design pattern . 29 3.1.3 Tokenizer . 31 3.1.4 Tree constructor . 32 3.1.5 Error handling . 34 3.2 Building . 34 3.3 Testing . 35 3.3.1 Tokenizer . 35 3.3.2 Tree builder . 36 3.4 Summary . 37 4 Test Framework 38 4.1 Design . 38 4.1.1 Architecture . 38 4.1.2 Adapters . 39 4.1.3 Comparator and plurality agreement . 41 4.2 Building . 42 4.2.1 Parser adapters implementations . 43 4.2.2 Preparing the input . 43 4.2.3 Comparator . 44 4.3 Other framework features . 45 4.3.1 Web Interface . 45 4.3.2 Tracer . -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session. -

“Hidden Backdoor” in Qihoo 360 Secure Browser
Independent Report on Alledged “Hidden Backdoor” in Qihoo 360 Secure Browser . IDF Laboratory Release Date: November 25, 2012 INTELLIGENCE DEFENSE FRIENDS LABORATORY http://www.idf.cn IDF Laboratory Version: <1.4> Independent Report on Alledged “Hidden Backdoor” in Qihoo 360 Date: <24/11/2012> Secure Browser Document Sign:IDF-REPDOC-20121124 Copyright Statement This research report is complied by IDF laboratory, unless it is published and agreed, its copyright belongs to IDF laboratory. While the quoted parts in the report belong to the original writer or corresponding units. Without the permission of IDF laboratory and the writer, any unit and individual are not allowed to transfer the contents of this report or use for other purpose, and this report is only for the reference of the industry research without commercial purposes. Welcome your criticism and correction. IDF Laboratory (Intelligence Defense Friends Laboratory) is a technical civil club for the enthusiasts of network information security, the backbone of which is made up of professionals, technicians and hobbyists from relevant fields. The research direction of IDF mainly focus on: the technical fields such as the development tendency of Internet threat, terminal security management, communication security of wireless network, botnet, as well as product research. IDF laboratory provides universal education of computer security knowledge for a great many enthusiasts of network information security, participates in the evaluation of the technology and market research for the products and development trends of relevant fields within the industry objectively and independently, thus providing the platform and bridge for the enthusiasts of network information security to be grow up as professional security or technical employees. -
Designing a Browser to Benefit from Multi-Core Silicon
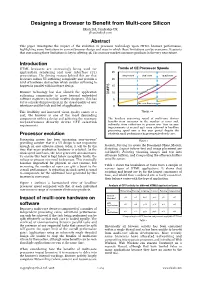
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

Attack Surface Analysis and Code Coverage Improvement for Fuzzing
This document is downloaded from DR‑NTU (https://dr.ntu.edu.sg) Nanyang Technological University, Singapore. Attack surface analysis and code coverage improvement for fuzzing Peng, Lunan 2019 Peng, L. (2019). Attack surface analysis and code coverage improvement for fuzzing. Master's thesis, Nanyang Technological University, Singapore. https://hdl.handle.net/10356/105642 https://doi.org/10.32657/10356/105642 Downloaded on 07 Oct 2021 23:08:40 SGT Attack Surface Analysis and Code Coverage Improvement for Fuzzing PENG LUNAN School of Physical and Mathematical Sciences 2019 Attack Surface Analysis and Code Coverage Improvement for Fuzzing PENG LUNAN School of Physical and Mathematical Sciences A thesis submitted to the Nanyang Technological University in partial fulfillment of the requirements for the degree of Master of Science 2019 Supervisor Declaration Statement I have reviewed the content and presentation style of this thesis and declare it of sufficient grammatical clarity to be examined. To the best of my knowledge, the thesis is free of plagiarism and the research and writing are those of the candidate’s except as acknowledged in the Author Attribution Statement. I confirm that the investigations were conducted in accord with the ethics policies and integrity standards of Nanyang Technological University and that the research data are presented honestly and without prejudice. Date Wu Hongjun Abstract As cybercrime becoming a worldwide threat in the past decades, research on cyber- security keeps attracting a great deal of attention. During a long time competition between attackers and defenders, vulnerability detection has been considered as the decisive pre-step for both sides. Among the massive methodologies of vulnerability detection, fuzzing test has demonstrated its outstanding performance on finding bugs automatically and effectively. -

China Tech Food Chain
Information Technology / Asia ex Japan 15 November 2013 Standing out from the crowd China Tech Food Chain • We expect investors to focus on China smartphones, tablets, Positive (unchanged) components, and mobile Internet/services in 2014 Neutral • On our forecasts, smartphone and tablet shipments will grow by 43% and 42% YoY, respectively Negative • Our top stock picks for 2014 are: Mediatek, SK Hynix, Tencent, Lenovo and Sunny Optical How do we justify our view? See important disclosures, including any required research certifications, beginning on page 60 China Tech Food Chain 15 November 2013 Contents Standing out from the crowd in 2014 ..........................................................................................3 China Smartphone Sector ............................................................................................................ 5 China Tablet Sector ..................................................................................................................... 8 China Components Sector ......................................................................................................... 10 China Mobile Service/Internet sector ........................................................................................ 12 China smartphone supply chain directory ................................................................................. 15 Company Section AAC Technologies ................................................................................................................... 16 Lenovo -
QNX Web Browser
PRODUCT BRIEF QNX Web Browser The QNX Web Browser, based on the Blink rendering engine, is a state-of-the-art browser designed to address performance, reliability, memory footprint, and security requirements of embedded systems. With a heritage of best-in-class browser technology from BlackBerry, the QNX Web Browser enables a wide range of uses from pure document viewers and video players, to feature-rich application environments in systems such as infotainment head units and in-flight entertainment units. The browser employs a modular, component based architecture that leverages QNX Neutrino® Realtime Operating System’s advanced memory protection, security mechanisms, and concurrency to provide reliable, robust, and responsive performance. Overview Benefits Web applications have been widely used on PCs and mobile • Highly secure browser designed with most advanced QNX devices. These applications are now surfacing in embedded SDP 7.0 security mechanisms systems due to the large developer base to draw from, as well as • Up to 35% lower memory footprint when compared to a general ease of development, deployment, and portability of web Linux-based implementation technologies. Consequently, web browsers are becoming a central • Fully-integrated with other QNX technologies including: component of modern-day embedded systems. o Video playback capabilities of QNX Multimedia Suite To provide an optimal web experience in an embedded system, o Location manager service for geolocation the browser must enable high performance and stability within the o QNX CAR Platform for Infotainment confines of limited system memory. Also of vital importance is adaptability. That is, to ensure a continued optimal browsing • Customization for fine grain control of features, behavior and experience, web browsers must keep pace with upstream appearance development. -

A Multi-Year Quest for the Best Web Test ACT I History of Debugging Protocols 2012 St
A multi-year quest for the best web test ACT I History of Debugging Protocols 2012 St. Petersburg 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Chrome DevTools Team 2012: Web Inspector Protocol 2012: Web Inspector Protocol Web Inspector protocol 2013: Chrome Forked WebKit! 2013: Chrome DevTools Protocol 2015: Chrome DevTools Protocol - 273 methods - 98 events - Used by IDEs for debugging - Used by Chrome Driver internally 2015 San Francisco 2015 San Francisco 2015 San Francisco 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging 2015: V8 Debugging ~1.5 years of work! 2015: V8 Debugging 2016: node.js debugging! 2017: Chrome Headless 2017: Chrome Headless 2017: Chrome Headless 2017: Puppeteer 2017: Cross-Browser Puppeteer 2018: puppeteer-firefox “Juggler” protocol 2018: puppeteer-firefox “Juggler” protocol 2019: puppeteer-firefox Remote Debugging Protocols Web Inspector protocol (2009 - ...) Chrome DevTools protocol (2013 - ...) Juggler “Juggler” protocol (2018 - ...) ACT II Browser vs Browser Engine Browser Browser Browser Browser Engine Browser Browser Engine Browser Engines 2020 Chromium (2008 – ...) WebKit (1998 – ...) Gecko (1997 – ...) Browser Engines 2020 Chromium (2008 – ...) Trident (1997 - 2014) WebKit (1998 – ...) EdgeHTML (2014 – 2018) Gecko (1997 – ...) Browser Engines Market Share 2020 Market Share Dynamics 2020 Market Share Dynamics 2020 Web Testing = 3 Browser Engines Chrome / Chromium Safari / WebKit Firefox / Gecko ACT III Web Testing Drama Web Testing Web Testing Web Testing Web Testing + headless Web Testing + headless Web Testing DOES NOT EXIST * + headless Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #1: WebKit Headful ❌ Headless ❌ ❌ ❌ Problem #2: Automation Technology WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. WebDriver Chrome DevTools Protocol WebInspector protocol Juggler protocol Problem #2: Automation Technology Permissions, Geolocation, ServiceWorkers, Network, …. -

Security Evaluation of Multi-Factor Authentication in Comparison with the Web Authentication API
Hochschule Wismar University of Applied Sciences Technology, Business and Design Faculty of Engineering, Department EE & CS Course of Studies: IT-Security and Forensics Master’s Thesis for the Attainment of the Academic Degree Master of Engineering (M. Eng.) Security Evaluation of Multi-Factor Authentication in Comparison with the Web Authentication API Submitted by: September 30, 2019 From: Tim Brust born xx/xx/xxxx in Hamburg, Germany Matriculation number: 246565 First supervisor: Prof. Dr.-Ing. habil. Andreas Ahrens Second supervisor: Prof. Dr. rer. nat. Nils Gruschka Purpose of This Thesis The purpose of this master’s thesis is an introduction to multi-factor authentication, as well as to the conventional methods of authentication (knowledge, possession, biometrics). This introduction includes technical functionality, web usability, and potential security threats and vulnerabilities. Further, this thesis will investigate whether the Web Authentication API is suit- able as an alternative or possible supplement to existing multi-factor authentication methods. The question has to be answered to what extent the Web Authentication API can increase security and user comfort. An evaluation of the security of the Web Authentication API in comparison with other multi-factor authentication solutions plays a crucial role in this thesis. Abstract Internet users are at constant risk, given that data breaches happen nearly daily. When a breached password is re-used, it renders their whole digital identity in dan- ger. To counter these threats, the user can deploy additional security measures, e.g., multi-factor authentication. This master’s thesis introduces and compares the multi- factor authentication solutions, one-time passwords, smart cards, security keys, and the Universal Second Factor protocol with a focus on their security. -

HTML5 Developer's Guide
QNX® SDK for Apps and Media 1.0 QNX® SDK for Apps and Media 1.0 HTML5 Developer's Guide ©2012–2014, QNX Software Systems Limited, a subsidiary of BlackBerry Limited. All rights reserved. QNX Software Systems Limited 1001 Farrar Road Ottawa, Ontario K2K 0B3 Canada Voice: +1 613 591-0931 Fax: +1 613 591-3579 Email: [email protected] Web: http://www.qnx.com/ QNX, QNX CAR, Momentics, Neutrino, and Aviage are trademarks of BlackBerry Limited, which are registered and/or used in certain jurisdictions, and used under license by QNX Software Systems Limited. All other trademarks belong to their respective owners. Electronic edition published: Tuesday, August 5, 2014 HTML5 Developer's Guide Table of Contents About This Guide .......................................................................................................................5 Typographical conventions .................................................................................................6 Technical support .............................................................................................................8 Chapter 1: SDK Overview ............................................................................................................9 Chapter 2: Browser Engine ........................................................................................................11 CSS3 support .................................................................................................................14 HTML5 elements ............................................................................................................15 -

Conceptual Architecture of Mozilla Firefox 6
Conceptual Architecture of Mozilla Firefox 6 Presented by Fully Optimized eXperience Group Members: James Brereton – 06069736, [email protected] Gordon Krull – 06003108, [email protected] Rob Staalduinen – 06009513, [email protected] Katie Tanner – 06060472, [email protected] Prepared for CISC 322, Queen’s University at Kingston, Ontario, Canada October 24th, 2011 Table of Contents ABstract .........................................................................................................................…... 3 Introduction ........................................................................................................................3 Research Overview and Derivation Process .........................................................4 Conceptual Architecture of Firefox ...........................................................................4 XUL and XULRunner ...........................................................................................6 GecKo .........................................................................................................................7 Data Persistence ................................................................................................11 XPCOM ...................................................................................................................12 Display BacKend (GTK+ Adapter and LiBraries) .................................13 Sequence Diagrams ......................................................................................................13 Lessons Learned