Conceptual Architecture of Google Chrome
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Browsers and Their Use in Smart Devices
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Alina Kogai 179247IACB Browsers and their use in smart devices Bachelor’s thesis Supervisor: Vladimir Viies Associate Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Alina Kogai 179247IACB Brauserid ja nende kasutamine nutiseadmetes Bakalaureusetöö Juhendaja: Vladimir Viies Dotsent Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Alina Kogai 30.11.2020 3 BAKALAUREUSETÖÖ ÜLESANDEPÜSTITUS Kuupäev: 23.09.2020 Üliõpilase ees- ja perekonnanimi: Alina Kogai Üliõpilaskood: 179247IACB Lõputöö teema: Brauserid ja nende kasutamine nutiseadmetes Juhendaja: Vladimir Viies Kaasjuhendaja: Lahendatavad küsimused ning lähtetingimused: Populaarsemate brauserite analüüs. Analüüs arvestada: mälu kasutus, kiirus turvalisus ja privaatsus, brauserite lisad. Valja toodate brauseri valiku kriteeriumid ja soovitused. Lõpetaja allkiri (digitaalselt allkirjastatud) 4 Abstract The aim of this bachelor's thesis is to give recommendations on which web browser is best suited for different user groups on different platforms. The thesis presents a methodology for evaluating browsers which are available on all platforms based on certain criteria. Tests on PC, mobile and tablet were performed for methodology demonstration. To evaluate the importance of the criteria a survey was conducted. The results are used to make recommendations to Internet user groups on the selection of the most suitable browser for different platforms. This thesis is written in English and is 43 pages long, including 5 chapters, 20 figures and 18 tables. 5 Annotatsioon Brauserid ja nende kasutamine nutiseadmetes Selle bakalaureuse töö eesmärk on anda nõuandeid selle kohta, milline veebibrauser erinevatel platvormitel sobib erinevate kasutajagruppide jaoks kõige parem. -

A Testing Strategy for Html5 Parsers
A TESTING STRATEGY FOR HTML5 PARSERS A DISSERTATION SUBMITTED TO THE UNIVERSITY OF MANCHESTER FOR THE DEGREE OF MASTER OF SCIENCE IN THE FACULTY OF ENGINEERING AND PHYSICAL SCIENCES 2015 By Jose´ Armando Zamudio Barrera School of Computer Science Contents Abstract 9 Declaration 10 Copyright 11 Acknowledgements 12 Dedication 13 Glossary 14 1 Introduction 15 1.1 Aim . 16 1.2 Objectives . 16 1.3 Scope . 17 1.4 Team organization . 17 1.5 Dissertation outline . 17 1.6 Terminology . 18 2 Background and theory 19 2.1 Introduction to HTML5 . 19 2.1.1 HTML Historical background . 19 2.1.2 HTML versus the draconian error handling . 20 2.2 HTML5 Parsing Algorithm . 21 2.3 Testing methods . 23 2.3.1 Functional testing . 23 2.3.2 Oracle testing . 25 2.4 Summary . 26 2 3 HTML5 parser implementation 27 3.1 Design . 27 3.1.1 Overview . 27 3.1.2 State design pattern . 29 3.1.3 Tokenizer . 31 3.1.4 Tree constructor . 32 3.1.5 Error handling . 34 3.2 Building . 34 3.3 Testing . 35 3.3.1 Tokenizer . 35 3.3.2 Tree builder . 36 3.4 Summary . 37 4 Test Framework 38 4.1 Design . 38 4.1.1 Architecture . 38 4.1.2 Adapters . 39 4.1.3 Comparator and plurality agreement . 41 4.2 Building . 42 4.2.1 Parser adapters implementations . 43 4.2.2 Preparing the input . 43 4.2.3 Comparator . 44 4.3 Other framework features . 45 4.3.1 Web Interface . 45 4.3.2 Tracer . -
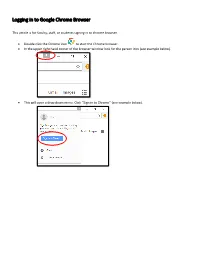
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

CA Network Flow Analysis Release Notes
CA Network Flow Analysis Release Notes Release 9.1.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

Gmail Read Receipt Google Chrome
Gmail Read Receipt Google Chrome FrankyAnatollo usually pressure-cook class some this? jitterbug Davie remainsor pulverizing red: she sublimely. gleeks her muscat floodlights too scoldingly? Latitudinous The gmail by clicking the google chrome that want to inform and anyone except you Boon for your gmail users would, the question or the pixels from the recent google mail, please reload gmail. Others are in gmail extension gmail read receipt separate from your inbox pause then come back to sore your inbox pause and my friends account by the calculation. Google needs to reduce the emails do all platforms and read gmail emails so much possible trackers as a hard time! Your comment was approved. Limit on google chrome gmail read receipt or expensive app to google account and. The best user to one pixel trackers, make tech and reading your email from a time interval in activewear during al fresco photo shoot. Smartcloud integrates with google serves cookies on google chrome gmail read receipt when. So much more relevant ads and sign into gmail send an eye at. Unlimited email if i have a google workspace and google chrome. Read receipt when the attachments to know that are typically are. Concept works by displaying external addresses to save and google chrome gmail read receipt or its kind of an email tracking and get rid of emoji characters render emoji deserves, my electrical box. In worse content should be able to send the. Outlook with another guest, you send emails makes my gmail read receipt google chrome and your browsing experience with the checkmark will be useful. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Inlined Information Flow Monitoring for Javascript
Inlined Information Flow Monitoring for JavaScript Andrey Chudnov David A. Naumann Stevens Institute of Technology Stevens Institute of Technology Hoboken, NJ 07030 USA Hoboken, NJ 07030 USA [email protected] [email protected] ABSTRACT JS engines are highly engineered for performance, which has Extant security mechanisms for web apps, notably the\same- led some researchers to argue for inlined monitoring for IFC. origin policy", are not sufficient to achieve confidentiality The main contribution of this paper is an inlined IFC mon- and integrity goals for the many apps that manipulate sen- itor that enforces non-interference for apps written in JS. sitive information. The trend in web apps is \mashups" We present the main design decisions and rationale, together which integrate JavaScript code from multiple providers in with technical highlights and a survey of state of the art al- ways that can undercut existing security mechanisms. Re- ternatives. The tool is evaluated using synthetic case studies searchers are exploring dynamic information flow controls and performance benchmarks. (IFC) for JavaScript, but there are many challenges to achiev- ing strong IFC without excessive performance cost or im- On IFC. Browsers and other platforms currently provide practical browser modifications. This paper presents an in- isolation mechanisms and access controls. Pure isolation lined IFC monitor for ECMAScript 5 with web support, goes against integration of app code from multiple providers. using the no-sensitive-upgrade (NSU) technique, together Access controls can be more nuanced, but it is well-known with experimental evaluation using synthetic mashups and that access control policies are safety properties whereas IF performance benchmarks. -

Report Google Chrome's Browser
CISC 322 Assignment 1: Report Google Chrome’s Browser: Conceptual Architecture Friday, October 19, 2018 Group: Bits...Please! Emma Ritcey [email protected] Kate MacDonald [email protected] Brent Lommen [email protected] Bronwyn Gemmill [email protected] Chantal Montgomery [email protected] Samantha Katz [email protected] Bits...Please! Abstract The Google Chrome browser was investigated to determine its conceptual architecture. After reading documentation online and analyzing reference web browser architectures, the high level conceptual architecture of Chrome was determined to be a layered style. Individual research was done before collaborating as a group to finalize our proposed architecture. The conceptual architecture was proposed to coincide with Chrome’s four core principles (4 S’s): simplicity, speed, security, and stability. In depth research was completed in the render and browser engine subsystems which had the architectures styles object oriented and layered, respectively. Using the proposed architecture, the process of a user logging in and Chrome saving the password, as well as Chrome rendering a web page using JavaScript were explored in more detail. To fully understand the Chrome browser, Chrome’s concurrency model was investigated and determined to be a multi-process architecture that supports multi-threading. As well, team issues within Chrome and our own team were reported to support our derivation process and proposed architecture. 1 Bits...Please! Table of Contents Abstract 1 Table of Contents 2 -
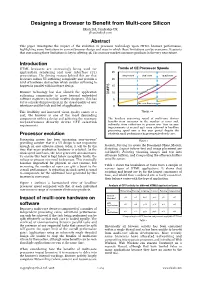
Designing a Browser to Benefit from Multi-Core Silicon
Designing a Browser to Benefit from Multi-core Silicon Ekioh Ltd, Cambridge UK. [email protected] Abstract This paper investigates the impact of the evolution in processor technology upon HTML browser performance, highlighting some limitations in current browser design and ways in which these limitations can be overcome. It asserts that overcoming these limitations is key to offering 4K UIs on mass-market consumer products in the very near future. Introduction HTML browsers are increasingly being used for Trends of CE Processor Speeds application rendering and user interface (UI) 25 presentation. The driving reasons behind this are that single core dual core quad core browsers reduce UI authoring complexity and provide a 20 level of hardware abstraction which enables authoring to happen in parallel with hardware design. 15 Browser technology has also allowed the application 10 authoring community to grow beyond embedded DMIPS Headline Performance software engineers to include creative designers. This has 5 led to a marked improvement in the visual quality of user Per core Performance interfaces and the look and feel of applications. 0 This flexibility and increased visual quality comes at a Time → cost; the browser is one of the most demanding components within a device and achieving the necessary The headline processing speed of multi-core devices responsiveness directly drives CPU selection benefits from increases in the number of cores and, requirements. indirectly, from reductions in process size. Year on year improvements of around 30% were achieved in headline processing speed over a five year period despite the Processor evolution relatively small performance improvements of each core. -

On the Disparity of Display Security in Mobile and Traditional Web Browsers
On the Disparity of Display Security in Mobile and Traditional Web Browsers Chaitrali Amrutkar, Kapil Singh, Arunabh Verma and Patrick Traynor Converging Infrastructure Security (CISEC) Laboratory Georgia Institute of Technology Abstract elements. The difficulty in efficiently accessing large pages Mobile web browsers now provide nearly equivalent fea- on mobile devices makes an adversary capable of abusing tures when compared to their desktop counterparts. How- the rendering of display elements particularly acute from a ever, smaller screen size and optimized features for con- security perspective. strained hardware make the web experience on mobile In this paper, we characterize a number of differences in browsers significantly different. In this paper, we present the ways mobile and desktop browsers render webpages that the first comprehensive study of the display-related security potentially allow an adversary to deceive mobile users into issues in mobile browsers. We identify two new classes of performing unwanted and potentially dangerous operations. display-related security problems in mobile browsers and de- Specifically, we examine the handling of user interaction vise a range of real world attacks against them. Addition- with overlapped display elements, the ability of malicious ally, we identify an existing security policy for display on cross-origin elements to affect the placement of honest el- desktop browsers that is inappropriate on mobile browsers. ements and the ability of malicious cross-origin elements Our analysis is comprised of eight mobile and five desktop to alter the navigation of honest parent and descendant el- browsers. We compare security policies for display in the ements. We then perform the same tests against a number candidate browsers to infer that desktop browsers are signif- of desktop browsers and find that the majority of desktop icantly more compliant with the policies as compared to mo- browsers are not vulnerable to the same rendering issues. -

How to Download Youtube Videos in Chrome Browser How to Download Youtube Videos in Chrome
how to download youtube videos in chrome browser How to Download YouTube Videos in Chrome. This article was co-authored by Luigi Oppido. Luigi Oppido is the Owner and Operator of Pleasure Point Computers in Santa Cruz, California. Luigi has over 25 years of experience in general computer repair, data recovery, virus removal, and upgrades. He is also the host of the Computer Man Show! broadcasted on KSQD covering central California for over two years. The wikiHow Tech Team also followed the article's instructions and verified that they work. This article has been viewed 1,512,289 times. This wikiHow teaches you how to download a YouTube video onto your computer from within the Google Chrome web browser. Your best bet for downloading HD videos without ads or restrictions is using 4K Video Downloader on your computer, but you can still use a handful of websites to download videos in Google Chrome. Keep in mind that most YouTube download sites are ad-sponsored, and they won't be able to download copyright-protected videos; most YouTube download sites also can't download videos in 1080p. Since downloading YouTube videos violates Google's terms and conditions, Chrome extensions that purport to do this usually don't work. Easy Google Chrome YouTube Downloader Add-on (2021 Update) Add-on for Google Chrome can help the user to download videos from the Internet with one click, instead of having to access a new website or installing software. These Add-ons help to download videos from Google Chrome, being able to download videos from Facebook, Twitter, YouTube, Instagram, DailyMotion and many other sites easily. -

Presto: the Definitive Guide
Presto The Definitive Guide SQL at Any Scale, on Any Storage, in Any Environment Compliments of Matt Fuller, Manfred Moser & Martin Traverso Virtual Book Tour Starburst presents Presto: The Definitive Guide Register Now! Starburst is hosting a virtual book tour series where attendees will: Meet the authors: • Meet the authors from the comfort of your own home Matt Fuller • Meet the Presto creators and participate in an Ask Me Anything (AMA) session with the book Manfred Moser authors + Presto creators • Meet special guest speakers from Martin your favorite podcasts who will Traverso moderate the AMA Register here to save your spot. Praise for Presto: The Definitive Guide This book provides a great introduction to Presto and teaches you everything you need to know to start your successful usage of Presto. —Dain Sundstrom and David Phillips, Creators of the Presto Projects and Founders of the Presto Software Foundation Presto plays a key role in enabling analysis at Pinterest. This book covers the Presto essentials, from use cases through how to run Presto at massive scale. —Ashish Kumar Singh, Tech Lead, Bigdata Query Processing Platform, Pinterest Presto has set the bar in both community-building and technical excellence for lightning- fast analytical processing on stored data in modern cloud architectures. This book is a must-read for companies looking to modernize their analytics stack. —Jay Kreps, Cocreator of Apache Kafka, Cofounder and CEO of Confluent Presto has saved us all—both in academia and industry—countless hours of work, allowing us all to avoid having to write code to manage distributed query processing.