The American Terrorist: Everything You Need to Know to Be a Subject Matter Expert
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

CITY of COOS BAY CITY COUNCIL Agenda Staff Report
CITY OF COOS BAY CITY COUNCIL Agenda Staff Report MEETING DATE AGENDA ITEM NUMBER September 17, 2013 Continued from August 6, 2013 TO: Mayor Shoji and City Councilors FROM: Rodger Craddock, City Manager eJlC ISSUE: Should the City of Coos Bay enact a resolution calling for the repeal of the National Defense Authorization Act of 2012 (NOAA), and direct City employees not to enforce or assist in the enforcement of the Act. BACKGROUND On August 6, 2013, several individuals including Tom McKirgan (Coquille) and Rob Taylor (Bandon) made a presentation to the Council regarding their concerns over the constitutionality of the National Defense Authorization Act of 2012 (NOAA), and they have requested that the City of Coos Bay pass their proposed resolution which would call for the repeal of the Act as well as prohibit the City through its police force from enforcing the Act or assisting others such as the Federal Government in enforcing the Act within the City. Attached you will find a copy of the August 61h report provided to the Council which includes the following: 1. Agenda staff report prepared by City Attorney Nathan McClintock (attachment one) 2. Letter to the Council from Rob Taylor, Connie Martin, and Tom McKirgen (attachment two) 3. Proposed resolution (attachment three) During the presentation on August 6, 2013, Mr. McKirgan provided the following documents to the Council for their review and consideration: 1. Wikipedia article on Brandon Mayfield and his arrest in 2004. (attachment four) 2. Document titled "Myths and Deceptions about the NOAA FY2012" (attachment five) 3. Unsigned letter presumably to the Council (attachment six) By a majority vote, the Council decided to postpone consideration of the matter to a future meeting. -

Central Intelligence Agency (CIA) Freedom of Information Act (FOIA) Case Log October 2000 - April 2002
Description of document: Central Intelligence Agency (CIA) Freedom of Information Act (FOIA) Case Log October 2000 - April 2002 Requested date: 2002 Release date: 2003 Posted date: 08-February-2021 Source of document: Information and Privacy Coordinator Central Intelligence Agency Washington, DC 20505 Fax: 703-613-3007 Filing a FOIA Records Request Online The governmentattic.org web site (“the site”) is a First Amendment free speech web site and is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file. The public records published on the site were obtained from government agencies using proper legal channels. Each document is identified as to the source. Any concerns about the contents of the site should be directed to the agency originating the document in question. GovernmentAttic.org is not responsible for the contents of documents published on the website. 1 O ct 2000_30 April 2002 Creation Date Requester Last Name Case Subject 36802.28679 STRANEY TECHNOLOGICAL GROWTH OF INDIA; HONG KONG; CHINA AND WTO 36802.2992 CRAWFORD EIGHT DIFFERENT REQUESTS FOR REPORTS REGARDING CIA EMPLOYEES OR AGENTS 36802.43927 MONTAN EDWARD GRADY PARTIN 36802.44378 TAVAKOLI-NOURI STEPHEN FLACK GUNTHER 36810.54721 BISHOP SCIENCE OF IDENTITY FOUNDATION 36810.55028 KHEMANEY TI LEAF PRODUCTIONS, LTD. -

Framing 'Jihadjane'
What’s Love Got To Do With It? Framing ‘JihadJane’ in the US Press Maura Conway Dublin City University, Ireland Lisa McInerney University of Limerick, Ireland Abstract The purpose of this article is to compare and contrast the US press coverage accorded to female terrorist plotter, Colleen LaRose, with that of two male terrorist plotters in order to test whether assertions in the academic literature regarding media treatment of women terrorists stand up to empirical scrutiny. The authors employed TextSTAT software to generate frequency counts of all words contained in 150 newspaper reports on their three subjects and then slotted relevant terms into categories fitting the commonest female terrorist frames, as identified by Nacos’s article in Studies in Conflict and Terrorism (2005). The authors’ findings confirm that women involved in terrorism receive significantly more press coverage and are framed vastly differently in the US press than their male counterparts. Keywords: female, framing, gender, jihadi, Colleen LaRose, newspapers, press, terrorism, women __________________________________________________________________________________ Introduction This article analyses US press reports on a woman and two men arrested in the US in 2009 and 2010 for their parts in three separate jihadi terrorist plots. The female plotter is widely known as ‘JihadJane’, which was an online pseudonym for Colleen LaRose, an American woman charged with four terrorism-related offences and taken into custody by US law enforcement at Philadelphia International Airport on her return from Europe in October 2009 (Shiffman, 2011).[1] LaRose is accused of using the internet to recruit individuals for the purpose of engaging in violent jihad, to include the murder of Swedish cartoonist Lars Vilks. -
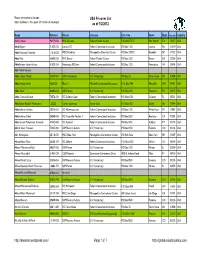
USA Prisoner List As of 1/2/2012 Page
Please remember to include USA Prisoner List return address in the upper left corner of envelope as of 1/2/2012 Name Number Prison Line one Line Two Town State Postcode Country Aafia Siddiqui 90279-054 FMC Carswell Federal Medical Center P.O. Box 27137 Fort Worth TX 76127 USA Abad Elfgeeh 31523-053 Loretto FCI Federal Correction Institution PO Box 1000 Loretto PA 15940 USA Abdel Hameed Shehadeh 11815-022 MDC Brooklyn Metropolitan Detention Center PO Box 329002 Brooklyn NY 11232 USA Abdel Nur 64655-053 FMC Butner Federal Medical Center PO Box 1600 Butner NC 27509 USA Abdelhaleem Hasan Ashqar 41500-054 Petersburg FCI Low Federal Correction Institution PO Box 1000 Petersburg VA 23804 USA Abdi Mahdi Hussein Abdul Hakim Murad 37437-054 USP Terre Haute U.S. Penitentiary PO Box 33 Terre Haute IN 47808 USA Abdul Hamin Awkal A267328 Man CI Mansfield Correctional Institution P. O. Box 788 Mansfield OH 44901 USA Abdul Kadir 64656-053 USP Canaan U.S. Penitentiary P.O. Box 300 Waymart PA 18472 USA Abdul Tawala Alishtari 70276-054 FCI Coleman Low Federal Correctional Institution P.O. Box 1031 Coleman FL 33521 USA Abdulhakim Mujahid Muhammad 150550 Varner Supermax Varner Unit P.O. Box 400 Grady AR 71644 USA Abdulrahman Farhane 58376-054 FCI Allenwood Low Federal Correctional Institution PO Box 1000 White Deer PA 17887 USA Abdulrahman Odeh 26548-050 FCI Victorville Medium II Federal Correctional Institution PO Box 5300 Adelanto CA 92301 USA Abdurahman Muhammad Alamoudi 47042-083 FCI Ashland Federal Correction Institution PO Box 6001 Ashland KY 41105 USA Adham Amin Hassoun 72433-004 USP Florence Admax U.S. -

Obstructing Justice: the Rise and Fall of the AEDPA*
AGARWAL.DOC 9/17/2019 11:04 AM Obstructing Justice: The Rise and Fall of the AEDPA* TABLE OF CONTENTS I. INTRODUCTION .................................................................................................. 840 II. THE CURRENT POLITICAL LANDSCAPE: PUSHING FORWARD DESPITE PUBLIC DISSENT ................................................... 843 III. THE AEDPA OF 1996 ........................................................................................ 850 A. At Issue: Prohibiting Material Support to Designated Foreign Terrorist Organizations .......................................... 850 B. Major Constitutional Victories: The Rise of the AEDPA ........................................................................................... 857 1. Under the First Amendment: Guilt by Association ........................... 858 2. Under the First Amendment: Political Advocacy and the Question of Scrutiny ............................................................. 863 3. Under the First Amendment: Vagueness ........................................... 866 IV. HITTING A BRICK WALL: THE FALL OF THE AEDPA .......................................... 871 A. National Security: Abridging Procedural Due Process to Foreign Terrorist Organizations .................................... 878 B. Crisis Legislation: The Age-Old Conflict Between Civil Liberties and National Security ....................................................... 882 1. Distinguishing the Alien and Sedition Acts ....................................... 886 2. Distinguishing Japanese -

Darpa Starts Sleuthing out Disloyal Troops
UNCLASSIFIED (U) FBI Tampa Division CI Strategic Partnership Newsletter JANUARY 2012 (U) Administrative Note: This product reflects the views of the FBI- Tampa Division and has not been vetted by FBI Headquarters. (U) Handling notice: Although UNCLASSIFIED, this information is property of the FBI and may be distributed only to members of organizations receiving this bulletin, or to cleared defense contractors. Precautions should be taken to ensure this information is stored and/or destroyed in a manner that precludes unauthorized access. 10 JAN 2012 (U) The FBI Tampa Division Counterintelligence Strategic Partnership Newsletter provides a summary of previously reported US government press releases, publications, and news articles from wire services and news organizations relating to counterintelligence, cyber and terrorism threats. The information in this bulletin represents the views and opinions of the cited sources for each article, and the analyst comment is intended only to highlight items of interest to organizations in Florida. This bulletin is provided solely to inform our Domain partners of news items of interest, and does not represent FBI information. In the JANUARY 2012 Issue: Article Title Page NATIONAL SECURITY THREAT NEWS FROM GOVERNMENT AGENCIES: American Jihadist Terrorism: Combating a Complex Threat p. 2 Authorities Uncover Increasing Number of United States-Based Terror Plots p. 3 Chinese Counterfeit COTS Create Chaos For The DoD p. 4 DHS Releases Cyber Strategy Framework p. 6 COUNTERINTELLIGENCE/ECONOMIC ESPIONAGE THREAT ITEMS FROM THE PRESS: United States Homes In on China Spying p. 6 Opinion: China‟s Spies Are Catching Up p. 8 Canadian Politician‟s Chinese Crush Likely „Sexpionage,‟ Former Spies Say p. -

JIHAD Pag 1-10 Revazut.Qxd
JIHADUL ISLAMIC DE LA "|NFRÂNGEREA TERORII" {I "R+ZBOIUL SFÂNT" LA "SPERAN}A LIBERT+}II" JIHADUL ISLAMIC 1 Foto coperta I • SHEIKH MAWLANA MUHAMMAD HISHAM COD CNCSIS 270 ANDREESCU, ANGHEL Jihadul Islamic de la ''|nfrângerea terorii'' [i ''R=zboiul Sfânt''ANDREESCU, la ''speran]a ANGHEL libert=]ii'' / Anghel Andreescu, NicolaeJihadul Radu. Islamic - Bucure[ti: de la ''|nfrângerea Editura Ministerului terorii'' [i ''R=zboiulInternelor [iSfânt'' Reformei la Administrative,''speran]a libert=]ii'' 2008 / Anghel Andreescu, Bibliogr.Nicolae Radu. - Bucure[ti: Editura Ministerului Internelor ISBN[i Reformei 978-973-745-011-1 Administrative, 2008 Bibliogr. I.ISBN Radu, 978-973-745-011-1 Nicolae 329.7(¡411.21)I. Radu, Nicolae Jihad 329.7(¡411.21) Jihad Opera]ii editoriale: colectiv Editura MIRA Tip=rit: Tipografia Codex Anghel ANDREESCU, Nicolae RADU 2 Chestor general de poli]ie Comisar [ef prof. univ. dr. Anghel ANDREESCU conf. univ. dr. Nicolae RADU JIHADULJIHADUL ISLAMICISLAMIC DE LA "|NFRÂNGEREA TERORII" {I "R+ZBOIUL SFÂNT" LA "SPERAN}A LIBERT+}II" BUCURE{TI – 2008 – JIHADUL ISLAMIC 3 Cuprins Gând pentru toleran]= . 9 Prefa]= . 11 Introducere . 15 Introduction . 29 Introduction . 43 Lista abrevieri . 59 Capitolul 1 De la Islam la cunoa[terea Jihadului . 65 Cât de bine cunoa[tem Islamul? . 65 Unicitatea lui Allah . 79 |n numele credin]ei . 96 Calea spre Mecca . 98 Ebraismul confirmat . 103 Moartea Profetului . .104 Urma[ii lui Mahomed . 106 Dinastia Abbasida [i civiliza]ia islamic= . 109 |n=l]are [i dec=dere . 110 {ii]i [i suni]i . 111 Religia \ntre [ii]i [i suni]i . 113 Cartea Sfânt= a Islamului . 115 Nemurirea sufletului . -

30 Terrorist Plots Foiled: How the System Worked Jena Baker Mcneill, James Jay Carafano, Ph.D., and Jessica Zuckerman
No. 2405 April 29, 2010 30 Terrorist Plots Foiled: How the System Worked Jena Baker McNeill, James Jay Carafano, Ph.D., and Jessica Zuckerman Abstract: In 2009 alone, U.S. authorities foiled at least six terrorist plots against the United States. Since Septem- ber 11, 2001, at least 30 planned terrorist attacks have Talking Points been foiled, all but two of them prevented by law enforce- • At least 30 terrorist plots against the United ment. The two notable exceptions are the passengers and States have been foiled since 9/11. It is clear flight attendants who subdued the “shoe bomber” in 2001 that terrorists continue to wage war against and the “underwear bomber” on Christmas Day in 2009. America. Bottom line: The system has generally worked well. But • President Obama spent his first year and a half many tools necessary for ferreting out conspiracies and in office dismantling many of the counterter- catching terrorists are under attack. Chief among them are rorism tools that have kept Americans safer, key provisions of the PATRIOT Act that are set to expire at including his decision to prosecute foreign ter- the end of this year. It is time for President Obama to dem- rorists in U.S. civilian courts, dismantlement of onstrate his commitment to keeping the country safe. Her- the CIA’s interrogation abilities, lackadaisical itage Foundation national security experts provide a road support for the PATRIOT Act, and an attempt map for a successful counterterrorism strategy. to shut down Guantanamo Bay. • The counterterrorism system that has worked successfully in the past must be pre- served in order for the nation to be successful In 2009, at least six planned terrorist plots against in fighting terrorists in the future. -

9-11 and Terrorist Travel- Full
AND TERRORIST TRAVEL Staff Report of the National Commission on Terrorist Attacks Upon the United States 9/11 AND TERRORIST TRAVEL Staff Report of the National Commission on Terrorist Attacks Upon the United States By Thomas R. Eldridge Susan Ginsburg Walter T. Hempel II Janice L. Kephart Kelly Moore and Joanne M. Accolla, Staff Assistant Alice Falk, Editor Note from the Executive Director The Commission staff organized its work around specialized studies, or monographs, prepared by each of the teams. We used some of the evolving draft material for these studies in preparing the seventeen staff statements delivered in conjunction with the Commission’s 2004 public hearings. We used more of this material in preparing draft sections of the Commission’s final report. Some of the specialized staff work, while not appropriate for inclusion in the report, nonetheless offered substantial information or analysis that was not well represented in the Commission’s report. In a few cases this supplemental work could be prepared to a publishable standard, either in an unclassified or classified form, before the Commission expired. This study is on immigration, border security and terrorist travel issues. It was prepared principally by Thomas Eldridge, Susan Ginsburg, Walter T. Hempel II, Janice Kephart, and Kelly Moore, with assistance from Joanne Accolla, and editing assistance from Alice Falk. As in all staff studies, they often relied on work done by their colleagues. This is a study by Commission staff. While the Commissioners have been briefed on the work and have had the opportunity to review earlier drafts of some of this work, they have not approved this text and it does not necessarily reflect their views. -

The Concept of Safe Havens in Salafi-Jihadi Strategy by Murad Batal Al-Shishani
VOLUME VII, ISSUE 27 u SEPTEMBER 11, 2009 IN THIS ISSUE: BRIEFS...................................................................................................................................1 THE IMPLICATIONS OF ABDUL AZIZ AL-HAKIm’S DEATH FOR IRAQI SECURITY By Babak Rahimi...................................................................................................................3 DID SOMALIA’S AL-SHABAAB PLAN TO ATTACK THE AUSTRALIAN MILITARY? By Raffaello Pantucci.....................................................................................................4 Abdul Aziz al-Hakim, Head of Iraqithe Supreme Awakening Council Council of Iraq THE CONCEPT OF SAFE HAVENS IN SALAFI-JIHADI STRATEGY By Murad Batal al-Shishani.................................................................................................6 Terrorism Monitor is a publication of The Jamestown Foundation. AT THE CENTER OF THE STORM: AN INTERVIEW WITH AFGHANISTan’S The Terrorism Monitor is LIEUTENANT GENERAL HADI KHALID -- PART ONE designed to be read by policy- By Derek Henry Flood...........................................................................................................8 makers and other specialists yet be accessible to the general public. The opinions expressed within are solely those of the authors and do not necessarily ISLAMISTS WARN FRANCE AGAINST MILITARY ROLE IN SOMALIA reflect those of The Jamestown Foundation. With al-Shabaab extremists threatening to try a captured French security advisor in Somalia under their version of -

How Anwar Al-Awlaki Became the Face of Western Jihad
As American as Apple Pie: How Anwar al-Awlaki Became the Face of Western Jihad Alexander Meleagrou-Hitchens Foreword by Lord Carlile of Berriew QC A policy report published by the International Centre for the Study of Radicalisation and Political Violence (ICSR) ABOUT ICSR The International Centre for the Study of Radicalisation and Political Violence (ICSR) is a unique partnership in which King’s College London, the University of Pennsylvania, the Interdisciplinary Center Herzliya (Israel), the Regional Center for Conflict Prevention Amman (Jordan) and Georgetown University are equal stakeholders. The aim and mission of ICSR is to bring together knowledge and leadership to counter the growth of radicalisation and political violence. For more information, please visit www.icsr.info. CONTACT DETAILS For questions, queries and additional copies of this report, please contact: ICSR King’s College London 138 –142 Strand London WC2R 1HH United Kingdom T. +44 (0)20 7848 2065 F. +44 (0)20 7848 2748 E. [email protected] Like all other ICSR publications, this report can be downloaded free of charge from the ICSR website at www.icsr.info. © ICSR 2011 AUTHOR’S NOTE This report contains many quotes from audio lectures as well as online forums and emails. All of these have been reproduced in their original syntax, including all spelling and grammatical errors. Contents Foreword 2 Letter of Support from START 3 Glossary of Terms 4 Executive Summary 6 Chapter 1 Introduction 9 Chapter 2 Methodology and Key Concepts 13 Social Movement Theory 13 Framing and -

Download Thepdf
Volume 59, Issue 5 Page 1395 Stanford Law Review KEEPING CONTROL OF TERRORISTS WITHOUT LOSING CONTROL OF CONSTITUTIONALISM Clive Walker © 2007 by the Board of Trustees of the Leland Stanford Junior University, from the Stanford Law Review at 59 STAN. L. REV. 1395 (2007). For information visit http://lawreview.stanford.edu. KEEPING CONTROL OF TERRORISTS WITHOUT LOSING CONTROL OF CONSTITUTIONALISM Clive Walker* INTRODUCTION: THE DYNAMICS OF COUNTER-TERRORISM POLICIES AND LAWS................................................................................................ 1395 I. CONTROL ORDERS ..................................................................................... 1403 A. Background to the Enactment of Control Orders............................... 1403 B. The Replacement System..................................................................... 1408 1. Control orders—outline................................................................ 1408 2. Control orders—contents and issuance........................................ 1411 3. Non-derogating control orders..................................................... 1416 4. Derogating control orders............................................................ 1424 5. Criminal prosecution.................................................................... 1429 6. Ancillary issues............................................................................. 1433 7. Review by Parliament and the Executive...................................... 1443 C. Judicial Review..................................................................................