Theater Battle Management Core System: Lessons for Systems Engineers Josiah R
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The National Infantry Museum Customer: Converting from Film to Digital Projection Helps Museum Fulfill Its Mission National Infantry Museum Foundation
The National Infantry Museum Customer: Converting from film to digital projection helps museum fulfill its mission National Infantry Museum Foundation Location: Columbus, GA Industry/Market: Museums Giant Screen Cinema Partner: D3D Cinema Requirements: • 4K resolution • High quality 3D viewing experience • Lower cost of operation • Reliable, long-term performance • Access to a wide range of digital Soldier trainees enjoy a 3D film at The National Infantry Museum & Soldier Center’s Giant Screen Theater content Photo credit: National Infantry Museum Foundation Summary: The National Infantry Museum From film to digital Foundation looked to upgrade the The National Infantry Museum & Soldier digital content but give it a real ‘wow’ giant screen theater in their National Center’s mission is to honor those who factor—but weren’t sure if it would fit Infantry Museum & Soldier Center serve by telling the stories of 240+ years their budget. from film to digital projection, in of military history. Keeping this history order to more closely align content alive in unforgettable ways helps museum Enter D3D Cinema to their mission, increase revenue visitors—from students of all ages and opportunities, and decrease Boy and Girl Scouts to church groups The Foundation turned to AV industry maintenance and operational costs. and active-duty service members—gain veterans D3D Cinema. With almost 20 a unique insight into what it means to be film-to-digital giant screen conversions a U.S. Army Infantryman. Products: in their portfolio, one of D3D’s founding • One dual-head Christie Solaria principles is to help clients ensure the In its prime, the museum’s film projection CP42LH 6P laser projection system long-term viability of their theaters. -

Los Veteranos—Latinos in WWII
Los Veteranos—Latinos in WWII Over 500,000 Latinos (including 350,000 Mexican Americans and 53,000 Puerto Ricans) served in WWII. Exact numbers are difficult because, with the exception of the 65th Infantry Regiment from Puerto Rico, Latinos were not segregated into separate units, as African Americans were. When war was declared on December 8, 1941, thousands of Latinos were among those that rushed to enlist. Latinos served with distinction throughout Europe, in the Pacific Theater, North Africa, the Aleutians and the Mediterranean. Among other honors earned, thirteen Medals of Honor were awarded to Latinos for service during WWII. In the Pacific Theater, the 158th Regimental Combat Team, of which a large percentage was Latino and Native American, fought in New Guinea and the Philippines. They so impressed General MacArthur that he called them “the greatest fighting combat team ever deployed in battle.” Latino soldiers were of particular aid in the defense of the Philippines. Their fluency in Spanish was invaluable when serving with Spanish speaking Filipinos. These same soldiers were part of the infamous “Bataan Death March.” On Saipan, Marine PFC Guy Gabaldon, a Mexican-American from East Los Angeles who had learned Japanese in his ethnically diverse neighborhood, captured 1,500 Japanese soldiers, earning him the nickname, the “Pied Piper of Saipan.” In the European Theater, Latino soldiers from the 36th Infantry Division from Texas were among the first soldiers to land on Italian soil and suffered heavy casualties crossing the Rapido River at Cassino. The 88th Infantry Division (with draftees from Southwestern states) was ranked in the top 10 for combat effectiveness. -
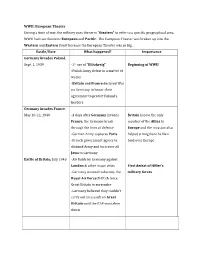
WWII: European Theater During a Time of War, the Military Uses the Term “Theaters” to Refer to a Specific Geographical Area
WWII: European Theater During a time of war, the military uses the term “theaters” to refer to a specific geographical area. WWII had two theaters: European and Pacific. The European Theater was broken up into the Western and Eastern Front because the European Theater was so big. Battle/Date What happened? Importance Germany invades Poland, Sept. 1, 1939 -1st use of “Blitzkreig” Beginning of WWII -Polish Army defeat in a matter of weeks -Britain and France declared War on Germany to honor their agreement to protect Poland’s borders Germany invades France, May 10-22, 1940 -3 days after Germany invades Britain is now the only France, the Germans break member of the Allies in through the lines of defense Europe and the invasion also -German Army captures Paris helped strengthen the Nazi -French government agrees to hold over Europe disband Army and turn over all Jews to Germany Battle of Britain, July 1940 -Air Raids by Germany against London & other major cities First defeat of Hitler’s -Germany wanted to destroy the military forces Royal Air Force(RAF) & force Great Britain to surrender -Germany believed they couldn’t carry out an assault on Great Britain until the RAF was taken down Battle of Stalingrad, -Germany invaded the Soviet Turning Point of the Eastern Begins August 1942, Ends Union and bombed the city of Front of the war: Soviet Union February 1943 Stalingrad beings to push Germany back -Soviet Union sent 1 million well supplied soldiers to Stalingrad -Germany moves into city and was unable to receive food and supplies. -

BATTLE-SCARRED and DIRTY: US ARMY TACTICAL LEADERSHIP in the MEDITERRANEAN THEATER, 1942-1943 DISSERTATION Presented in Partial
BATTLE-SCARRED AND DIRTY: US ARMY TACTICAL LEADERSHIP IN THE MEDITERRANEAN THEATER, 1942-1943 DISSERTATION Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy in the Graduate School of The Ohio State University By Steven Thomas Barry Graduate Program in History The Ohio State University 2011 Dissertation Committee: Dr. Allan R. Millett, Adviser Dr. John F. Guilmartin Dr. John L. Brooke Copyright by Steven T. Barry 2011 Abstract Throughout the North African and Sicilian campaigns of World War II, the battalion leadership exercised by United States regular army officers provided the essential component that contributed to battlefield success and combat effectiveness despite deficiencies in equipment, organization, mobilization, and inadequate operational leadership. Essentially, without the regular army battalion leaders, US units could not have functioned tactically early in the war. For both Operations TORCH and HUSKY, the US Army did not possess the leadership or staffs at the corps level to consistently coordinate combined arms maneuver with air and sea power. The battalion leadership brought discipline, maturity, experience, and the ability to translate common operational guidance into tactical reality. Many US officers shared the same ―Old Army‖ skill sets in their early career. Across the Army in the 1930s, these officers developed familiarity with the systems and doctrine that would prove crucial in the combined arms operations of the Second World War. The battalion tactical leadership overcame lackluster operational and strategic guidance and other significant handicaps to execute the first Mediterranean Theater of Operations campaigns. Three sets of factors shaped this pivotal group of men. First, all of these officers were shaped by pre-war experiences. -

This Index Lists the Army Units for Which Records Are Available at the Eisenhower Library
DWIGHT D. EISENHOWER LIBRARY ABILENE, KANSAS U.S. ARMY: Unit Records, 1917-1950 Linear feet: 687 Approximate number of pages: 1,300,000 The U.S. Army Unit Records collection (formerly: U.S. Army, U.S. Forces, European Theater: Selected After Action Reports, 1941-45) primarily spans the period from 1917 to 1950, with the bulk of the material covering the World War II years (1942-45). The collection is comprised of organizational and operational records and miscellaneous historical material from the files of army units that served in World War II. The collection was originally in the custody of the World War II Records Division (now the Modern Military Records Branch), National Archives and Records Service. The material was withdrawn from their holdings in 1960 and sent to the Kansas City Federal Records Center for shipment to the Eisenhower Library. The records were received by the Library from the Kansas City Records Center on June 1, 1962. Most of the collection contained formerly classified material that was bulk-declassified on June 29, 1973, under declassification project number 735035. General restrictions on the use of records in the National Archives still apply. The collection consists primarily of material from infantry, airborne, cavalry, armor, artillery, engineer, and tank destroyer units; roughly half of the collection consists of material from infantry units, division through company levels. Although the collection contains material from over 2,000 units, with each unit forming a separate series, every army unit that served in World War II is not represented. Approximately seventy-five percent of the documents are from units in the European Theater of Operations, about twenty percent from the Pacific theater, and about five percent from units that served in the western hemisphere during World War II. -

Unit I Spiral Exam – World War II (75 Points Total) PLEASE DO NO
Mr. Huesken 10th Grade United States History II Unit I Spiral Exam – World War II (75 points total) PLEASE DO NO WRITE ON THIS TEST DIRECTIONS – Please answer the following multiple-choice questions with the best possible answer. No answer will be used more than once. (45 questions @ 1 point each = 45 points) 1) All of the following were leaders of totalitarian governments in the 1930’s and 1940’s except: a. Joseph Stalin b. Francisco Franco. c. Benito Mussolini d. Neville Chamberlain. 2) In what country was the Fascist party and government formed? a. Italy b. Japan c. Spain d. Germany 3) The Battle of Britain forced Germany to do what to their war plans in Europe in 1942? a. Join the Axis powers. b. Fight a three-front war. c. Put off the invasion of Britain. d. Enter into a nonaggression pact with Britain. 4) The Nazis practiced genocide toward Jews, Gypsies, and other “undesirable” peoples in Europe. What does the term “genocide” mean? a. Acting out of anti-Semitic beliefs. b. Deliberate extermination of a specific group of people. c. Terrorizing of the citizens of a nation by a government. d. Killing of people for the express purpose of creating terror. 5) The term “blitzkrieg” was a military strategy that depended on what? a. A system of fortifications. b. Out-waiting the opponent. c. Surprise and quick, overwhelming force. d. The ability to make a long, steady advance. 6) In an effort to avoid a second “world war”, when did the Britain and France adopt a policy of appeasement toward Germany? a. -

Visitors Guide the Giant Screen Theater Presents Larger-Than-Life Online Store Movies, Documentaries and Stage Presentations
The National Infantry Museum is well designed for self- guided tours. This brochure will help you plan your visit, whether you intend to see every gallery or just portions of National Infantry the museum. Trained volunteers are stationed throughout the museum Museum and to direct you, answer your questions, and enhance your experience. Hours of Operation Soldier Center The museum is open Fife and Drum 9 a.m. - 5 p.m. Tuesday through Saturday Enjoy sandwiches, soups, salads and much more in a 11 a.m. - 5 p.m. Sunday casual atmosphere at the Fife and Drum restaurant and Closed Mondays except on federal holidays bar on the museum’s mezzanine level. Giant Screen Theater Visitors Guide The Giant Screen Theater presents larger-than-life Online Store movies, documentaries and stage presentations. Show Our Online Store is always open! schedules and ticket prices are posted at the Tickets Buy your souvenirs at counter. Looking for a snack? Enjoy popcorn, candy, hot dogs, nachos, ice cream and more at the Concessions www.nationalinfantrymuseum.org stand! Down Range This is where the action is! Try your hand at firing Giant Screen Theater weapons in a training simulator just like the Soldiers use, For information, call or embark on a virtual rescue mission in a real Humvee! 706-685-5800 or visit nationalinfantrymuseum.org Soldier Store Don’t forget to pick up a souvenir in the Soldier Store, operated by the famous military supply company, Ranger Joe’s. The Soldier Store is located near the museum’s entrance and is open during regular museum hours. -

The U.S. Military's Force Structure: a Primer
CHAPTER 2 Department of the Army Overview when the service launched a “modularity” initiative, the The Department of the Army includes the Army’s active Army was organized for nearly a century around divisions component; the two parts of its reserve component, the (which involved fewer but larger formations, with 12,000 Army Reserve and the Army National Guard; and all to 18,000 soldiers apiece). During that period, units in federal civilians employed by the service. By number of Army divisions could be separated into ad hoc BCTs military personnel, the Department of the Army is the (typically, three BCTs per division), but those units were biggest of the military departments. It also has the largest generally not organized to operate independently at any operation and support (O&S) budget. The Army does command level below the division. (For a description of not have the largest total budget, however, because it the Army’s command levels, see Box 2-1.) In the current receives significantly less funding to develop and acquire structure, BCTs are permanently organized for indepen- weapon systems than the other military departments do. dent operations, and division headquarters exist to pro- vide command and control for operations that involve The Army is responsible for providing the bulk of U.S. multiple BCTs. ground combat forces. To that end, the service is orga- nized primarily around brigade combat teams (BCTs)— The Army is distinct not only for the number of ground large combined-arms formations that are designed to combat forces it can provide but also for the large num- contain 4,400 to 4,700 soldiers apiece and include infan- ber of armored vehicles in its inventory and for the wide try, artillery, engineering, and other types of units.1 The array of support units it contains. -

Three Levels of War USAF College of Aerospace Doctrine, Research and Education (CADRE) Air and Space Power Mentoring Guide, Vol
Three Levels of War USAF College of Aerospace Doctrine, Research and Education (CADRE) Air and Space Power Mentoring Guide, Vol. 1 Maxwell AFB, AL: Air University Press, 1997 (excerpt) Modern military theory divides war into strategic, operational, and tactical levels.1 Although this division has its basis in the Napoleonic Wars and the American Civil War, modern theory regarding these three levels was formulated by the Prussians following the Franco- Prussian War. It has been most thoroughly developed by the Soviets.2 In American military circles, the division of war into three levels has been gaining prominence since its 1982 introduction in Army Field Manual (FM) 100-5, Operations.3 The three levels allow causes and effects of all forms of war and conflict to be better understood—despite their growing complexity.4 To understand modern theories of war and conflict and to prosecute them successfully, the military professional must thoroughly understand the three levels, especially the operational level, and how they are interrelated. The boundaries of the levels of war and conflict tend to blur and do not necessarily correspond to levels of command. Nevertheless, in the American system, the strategic level is usually the concern of the National Command Authorities (NCA) and the highest military commanders, the operational level is usually the concern of theater commands, and the tactical level is usually the focus of subtheater commands. Each level is concerned with planning (making strategy), which involves analyzing the situation, estimating friendly and enemy capabilities and limitations, and devising possible courses of action. Corresponding to the strategic, operational, and tactical levels of war and conflict are national (grand) strategy with its national military strategy subcomponent, operational strategy, and battlefield strategy (tactics). -

Beyond Borders: PLA Command and Control of Overseas Operations
July 2020 STRATEGIC FORUM National Defense University About the Author Dr. Phillip C. Saunders is Director of the Beyond Borders: PLA Center for the Study of Chinese Military Affairs, Institute for National Strategic Command and Control of Studies, at the National Defense University. Overseas Operations Key Points By Phillip C. Saunders ◆ Expanded Chinese economic inter- ests and the higher priority given to maritime interests are driving hina’s latest round of military reforms is driven primarily by Xi Jin- People’s Liberation Army (PLA) ef- ping’s ambition to reshape the People’s Liberation Army (PLA) to forts to develop power projection 信息化 capabilities. improve its ability to win informationized [xinxihua, ] wars ◆ The reorganization of the Chinese and to ensure that it remains loyal to the Chinese Communist Party (CCP). military in late 2015 explicitly C The reforms are unprecedented in their ambition and in the scale and scope sought to give the Central Mili- of the organizational changes. Virtually every part of the PLA now reports to tary Commission (CMC) and the theater commands responsibility different leaders, has had its mission and responsibilities changed, has lost or for conducting operations and gained subordinate units, or has undergone a major internal reorganization. The to relegate the services to force- building. However, the services relationships between and among the Central Military Commission (CMC) are trying to maintain operational departments, offices, and commissions, the services, and the theater commands responsibilities, including for over- 1 seas operations. (TCs) have all changed. The reforms established new joint command and con- ◆ The precise division of responsi- trol mechanisms and thus have important implications for how the PLA con- bilities and coordination mecha- ducts operations within and beyond China’s borders. -

Reconstructing Infantry Combat and Training in the European Theater of Operations
Student Publications Student Scholarship Spring 2020 Cives Arma Ferant: Reconstructing Infantry Combat and Training in the European Theater of Operations Phil R. Kaspriskie Gettysburg College Follow this and additional works at: https://cupola.gettysburg.edu/student_scholarship Part of the Military History Commons, and the United States History Commons Share feedback about the accessibility of this item. Recommended Citation Kaspriskie, Phil R., "Cives Arma Ferant: Reconstructing Infantry Combat and Training in the European Theater of Operations" (2020). Student Publications. 792. https://cupola.gettysburg.edu/student_scholarship/792 This is the author's version of the work. This publication appears in Gettysburg College's institutional repository by permission of the copyright owner for personal use, not for redistribution. Cupola permanent link: https://cupola.gettysburg.edu/student_scholarship/792 This open access student research paper is brought to you by The Cupola: Scholarship at Gettysburg College. It has been accepted for inclusion by an authorized administrator of The Cupola. For more information, please contact [email protected]. Cives Arma Ferant: Reconstructing Infantry Combat and Training in the European Theater of Operations Abstract A common theme in memoirs, oral histories, and other sources dealing with servicemen in World War II seems to be a focus on the experience of combat. Training, particularly individual training, is rarely discussed beyond a cursory mention, and if it is discussed at all, the overwhelming tendency is to paint a picture of half-trained cannon fodder, at best. This paper’s goal is twofold: First, explore methods of instruction at the individual and unit levels, and explain the reasoning behind the evolution of training as the Army Ground Forces’ understanding of contemporary warfare changed; second, provide a case study at the unit level by examining the combat record of the 28th Infantry Division as well as training experiences from retired soldiers in the infantry branch. -

Victory Misunderstood Stephen Biddle What the Gulf War Tells Us About the Future of Conflict
Victory Misunderstood Stephen Biddle What the Gulf War Tells Us about the Future of Conflict tions of the Gulf War‘s outcome are wrong. The orthodox view explains the war’s one-sidedness in terms of the Coalition’s strengths, especially its ad- vanced technology, which is often held to have destroyed the Iraqis’ equipment or broken their will without exposing Coalition forces to extensive close combat on the ground.’ The main rival explanation emphasizes Iraqi shortcomings, such as their weak morale, poor training and leadership, or numerical inferi- ority in the theater of war.2 Both schools appeared within a few months of the cease-fire, and have changed surprisingly little since then.3 The information Stephen Biddle is a member of the research staff at the Institute for Defense Analyses (IDA), Alexandria, Virginia. This analysis was supported by the IDA Central Research Program. The views expressed are those of the author, however, and do not necessarily represent positions of IDA, its management, or sponsors. The author would like to thank Richard Betts, Tami Davis Biddle, Eliot Cohen, Steven David, Peter Feaver, Wade Hinkle, Marshall Hoyler, Christopher Jehn, Chaim Kaufmann, Michael Leonard, H.R. McMaster, Jesse Orlansky Brad Roberts, Richard Swain, John Tillson, Robert Turrell, Victor Utgoff, Larry Welch, Caroline Ziemke, Robert Zirkle, and the members of the MIT DACS Program, the UNC Carolina Seminar, and the Triangle Universities Security Seminar for helpful comments on earlier drafts. Responsibility for any errors, however, remains the author’s alone. 1. See, eg., William J. Perry, “Desert Storm and Deterrence,” Foreign Affairs, Vol.