File-System Implementation
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Allgemeines Abkürzungsverzeichnis
Allgemeines Abkürzungsverzeichnis L. -

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -

MSD FATFS Users Guide
Freescale MSD FATFS Users Guide Document Number: MSDFATFSUG Rev. 0 02/2011 How to Reach Us: Home Page: www.freescale.com E-mail: [email protected] USA/Europe or Locations Not Listed: Freescale Semiconductor Technical Information Center, CH370 1300 N. Alma School Road Chandler, Arizona 85224 +1-800-521-6274 or +1-480-768-2130 [email protected] Europe, Middle East, and Africa: Information in this document is provided solely to enable system and Freescale Halbleiter Deutschland GmbH software implementers to use Freescale Semiconductor products. There are Technical Information Center no express or implied copyright licenses granted hereunder to design or Schatzbogen 7 fabricate any integrated circuits or integrated circuits based on the 81829 Muenchen, Germany information in this document. +44 1296 380 456 (English) +46 8 52200080 (English) Freescale Semiconductor reserves the right to make changes without further +49 89 92103 559 (German) notice to any products herein. Freescale Semiconductor makes no warranty, +33 1 69 35 48 48 (French) representation or guarantee regarding the suitability of its products for any particular purpose, nor does Freescale Semiconductor assume any liability [email protected] arising out of the application or use of any product or circuit, and specifically disclaims any and all liability, including without limitation consequential or Japan: incidental damages. “Typical” parameters that may be provided in Freescale Freescale Semiconductor Japan Ltd. Semiconductor data sheets and/or specifications can and do vary in different Headquarters applications and actual performance may vary over time. All operating ARCO Tower 15F parameters, including “Typicals”, must be validated for each customer 1-8-1, Shimo-Meguro, Meguro-ku, application by customer’s technical experts. -

Netbackup ™ Enterprise Server and Server 8.0 - 8.X.X OS Software Compatibility List Created on September 08, 2021
Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List Created on September 08, 2021 Click here for the HTML version of this document. <https://download.veritas.com/resources/content/live/OSVC/100046000/100046611/en_US/nbu_80_scl.html> Copyright © 2021 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and NetBackup are trademarks or registered trademarks of Veritas Technologies LLC in the U.S. and other countries. Other names may be trademarks of their respective owners. Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List 2021-09-08 Introduction This Software Compatibility List (SCL) document contains information for Veritas NetBackup 8.0 through 8.x.x. It covers NetBackup Server (which includes Enterprise Server and Server), Client, Bare Metal Restore (BMR), Clustered Master Server Compatibility and Storage Stacks, Deduplication, File System Compatibility, NetBackup OpsCenter, NetBackup Access Control (NBAC), SAN Media Server/SAN Client/FT Media Server, Virtual System Compatibility and NetBackup Self Service Support. It is divided into bookmarks on the left that can be expanded. IPV6 and Dual Stack environments are supported from NetBackup 8.1.1 onwards with few limitations, refer technote for additional information <http://www.veritas.com/docs/100041420> For information about certain NetBackup features, functionality, 3rd-party product integration, Veritas product integration, applications, databases, and OS platforms that Veritas intends to replace with newer and improved functionality, or in some cases, discontinue without replacement, please see the widget titled "NetBackup Future Platform and Feature Plans" at <https://sort.veritas.com/netbackup> Reference Article <https://www.veritas.com/docs/100040093> for links to all other NetBackup compatibility lists. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Commonly Used Acronyms
Commonly Used Acronyms A Amperes AC Alternating Current CLA Carry Look-ahead Adder A/D Analog to Digital CMOS Complementary Metal-Oxide Semicon- ADC Analog to Digital Converter ductor AE Applications Engineer CP/M Control Program / Monitor AI Artificial Intelligence CPI Clocks Per Instruction ALU Arithmetic-Logic Unit CPLD Complex Programmable Logic Device AM Amplitude Modulation CPU Central Processing Unit AMD Advanced Micro Devices, Inc. CR Carriage Return ANSI American National Standards Institute CRC Cyclic Redundancy Code ARQ Automatic Retransmission reQuest CRQ Command Response Queue ASCII American Standard Code for Information CRT Cathode Ray Tube Interchange CS Chip Select / Check-Sum ASEE American Society for Engineering Educa- CSMA Carrier Sense Multiple-Access tion CSMA/CD Carrier Sense Multiple-Access with Colli- ASIC Application Specific Integrated Circuit sion Detect ASPI Advanced SCSI Programming Interface CSR Command Status Register ATDM Asynchronous Time Division Multiplexing CTS Clear To Send ATM Asynchronous Transfer Mode AUI Attached Unit Interface D Dissipation Factor D/A Digital to Analog B Magnetic Flux DAC Digital to Analog Converter BBS Bulletin Board System DAT Digital Audio Tape BCC Block Check Character dB (DB) deciBels BCD Binary Coded Decimal dBm dB referenced to 1 milliWatt BiCMOS Bipolar Complementary Metal-Oxide Semi- DC Direct Current conductor DCD Data Carrier Detect BIOS Basic Input / Output System DCE Data Circuit (Channel) Equipment BNC Bayonet Nut(?) Connector DD Double Density BPS/bps Bytes/bits -

File Systems
File Systems Tanenbaum Chapter 4 Silberschatz Chapters 10, 11, 12 1 File Systems Essential requirements for long-term information storage: • It must be possible to store a very large amount of information. • The information must survive the termination of the process using it. • Multiple processes must be able to access the information concurrently. 2 File Structure • None: – File can be a sequence of words or bytes • Simple record structure: – Lines – Fixed Length – Variable Length • Complex Structure: – Formatted documents – Relocatable load files • Who decides? 3 File Systems Think of a disk as a linear sequence of fixed-size blocks and supporting reading and writing of blocks. Questions that quickly arise: • How do you find information? • How do you keep one user from reading another’s data? • How do you know which blocks are free? 4 File Naming Figure 4-1. Some typical file extensions. 5 File Access Methods • Sequential Access – Based on a magnetic tape model – read next, write next – reset • Direct Access – Based on fixed length logical records – read n, write n – position to n – relative or absolute block numbers 6 File Structure Figure 4-2. Three kinds of files. (a) Byte sequence. (b) Record sequence. (c) Tree. 7 File Types • Regular Files: – ASCII files or binary files – ASCII consists of lines of text; can be displayed and printed – Binary, have some internal structure known to programs that use them • Directory – Files to keep track of files • Character special files (a character device file) – Related to I/O and model serial I/O devices • Block special files (a block device file) – Mainly to model disks File Types Figure 4-3. -

File Systems: Semantics & Structure What Is a File
5/15/2017 File Systems: Semantics & Structure What is a File 11A. File Semantics • a file is a named collection of information 11B. Namespace Semantics • primary roles of file system: 11C. File Representation – to store and retrieve data – to manage the media/space where data is stored 11D. Free Space Representation • typical operations: 11E. Namespace Representation – where is the first block of this file 11L. Disk Partitioning – where is the next block of this file 11F. File System Integration – where is block 35 of this file – allocate a new block to the end of this file – free all blocks associated with this file File Systems Semantics and Structure 1 File Systems Semantics and Structure 2 Data and Metadata Sequential Byte Stream Access • File systems deal with two kinds of information int infd = open(“abc”, O_RDONLY); int outfd = open(“xyz”, O_WRONLY+O_CREATE, 0666); • Data – the contents of the file if (infd >= 0 && outfd >= 0) { – e.g. instructions of the program, words in the letter int count = read(infd, buf, sizeof buf); Metadata – Information about the file • while( count > 0 ) { e.g. how many bytes are there, when was it created – write(outfd, buf, count); sometimes called attributes – count = read(infd, inbuf, BUFSIZE); • both must be persisted and protected } – stored and connected by the file system close(infd); close(outfd); } File Systems Semantics and Structure 3 File Systems Semantics and Structure 4 Random Access Consistency Model void *readSection(int fd, struct hdr *index, int section) { struct hdr *head = &hdr[section]; -
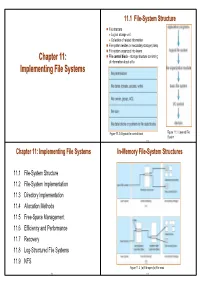
Chapter 11: Implementing File Systems In-Memory File-System Structures
11.1 File-System Structure File structure z Logical storage unit z Collection of related information File system resides on secondary storage (disks) File system organized into layers Chapter 11: File control block – storage structure consisting Chapter 11: of information about a file Implementing File Systems Figure 11.2 A typical file-control block Figure 11.1 Layered File System 11.3 Chapter 11: Implementing File Systems In-Memory File-System Structures 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space Management 11.6 Efficiency and Performance 11.7 Recovery 11.8 Log-Structured File Systems 11.9 NFS Figure 11.3 (a) File open (b) File read 11.2 11.4 Virtual File Systems 11.4 Allocation Methods Virtual File Systems (VFS) provide an object-oriented way of implementing file systems. VFS allows the same system call interface (API) to be used for different types of An allocation method refers to how disk blocks are file systems. allocated for files: The API is to the VFS interface, rather than any specific type of file system. 11.4.1 Contiguous allocation 11.4.2 Linked allocation 11.4.3 Indexed allocation Figure 11.4 Schematic View of Virtual File System 11.5 11.7 11.3 Directory Implementation 11.4.1 Contiguous Allocation Linear list of file names with pointer to the data blocks. Each file occupies a set of contiguous blocks on the disk z advantage: simple to program Advantages z disadvantage: time-consuming to execute z Simple – only require starting location (block #) and Hash Table – linear list with hash data structure. -

Linux Last Updated: 2018-09-11 Legal Notice Copyright © 2018 Veritas Technologies LLC
Storage Foundation 7.4 Configuration and Upgrade Guide - Linux Last updated: 2018-09-11 Legal Notice Copyright © 2018 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo are trademarks or registered trademarks of Veritas Technologies LLC or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This product may contain third-party software for which Veritas is required to provide attribution to the third-party (“Third-Party Programs”). Some of the Third-Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Refer to the third-party legal notices document accompanying this Veritas product or available at: https://www.veritas.com/about/legal/license-agreements The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Veritas Technologies LLC and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. VERITAS TECHNOLOGIES LLC SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. -

Allegato 2 Formati Di File E Riversamento
Formati di file e riversamento Allegato 2 al documento “Linee Guida sulla formazione, gestione e conservazione dei documenti informatici”. Sommario 1.1 Definizioni fondamentali 3 1.1.1 File, flussi digitali e buste-contenitori 4 1.1.2 Filesystem e metadati 5 1.1.3 Metadati e identificazione del formato 8 1. 2 Tassonomia 9 1.2.1 Tipologie di formati 9 1.2.2 Classificazione di formati 11 1.2.3 Formati generici e specifici 14 2.1 Documenti impaginati 21 2.1.1 Raccomandazioni per la produzione di documenti 33 2.2 Ipertesti 34 2.2.1 Raccomandazioni per la produzione di documenti 41 2.3 Dati strutturati 42 2.3.1 Raccomandazioni per la produzione di documenti 52 2.4 Posta elettronica 53 2.4.1 Raccomandazioni per la produzione di documenti 55 2.5 Fogli di calcolo e presentazioni multimediali 55 2.5.1 Raccomandazioni per la produzione di documenti 59 2.6 Immagini raster 60 2.6.1 Raccomandazioni per la produzione di documenti 74 2.7 Immagini vettoriali e modellazione digitale 77 2.7.1 Raccomandazioni per la produzione di documenti 84 2.8 Caratteri tipografici 84 2.8.1 Raccomandazioni per la produzione di documenti 86 2.9 Audio e musica 87 2.9.1 Raccomandazioni per la produzione di documenti 92 2.10 Video 93 2.10.1 Raccomandazioni per la produzione di documenti 102 2.11 Sottotitoli, didascalie e dialoghi 103 2.11.1 Raccomandazioni per la produzione di documenti 108 2.12 Contenitori e pacchetti di file multimediali 108 2.12.1 Raccomandazioni per la produzione di documenti 131 2.13 Archivi compressi 132 2.13.1 Raccomandazioni per la produzione di documenti 138 2.14 Documenti amministrativi 138 2.15 Applicazioni e codice sorgente 142 2.16 Applicazioni crittografiche 142 3.1 Valutazione di interoperabilità 147 3.2 Indice di interoperabilità 149 3.3 Riversamento 150 1 Introduzione 1.