Cloud, Virtualization, Data Storage Networking Fundementals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Dell Storage Aims to Redefine the Economics of Enterprise Storage Today and Tomorrow
WHITE PAPER How Dell Storage Aims to Redefine the Economics of Enterprise Storage Today and Tomorrow Sponsored by: Dell Laura DuBois November 2015 EXECUTIVE SUMMARY Today's IT leaders face pressure to reduce infrastructure cost, increase operational efficiency, and provide faster response to the business while evolving from traditional to new IT infrastructure models. It is with these imperatives in mind that storage executives continue to move virtualized workloads to hyperconverged, cloud-based, and/or lower-cost storage approaches. The challenge for these storage professionals is in managing both traditional SAN and NAS storage environments that exist today while evolving to software-defined, server-based, and workload-driven storage approaches in the future. This IDC White Paper analyzes how Dell Storage is helping its customers meet these cost and operational challenges by laying out a vision for redefining the economics of storage. To achieve this, Dell is integrating best-of-breed technologies including flash optimization, data placement, and storage efficiency techniques into a common storage architecture, offering easy capacity expansion to reduce overprovisioning. From a solution perspective, Dell Storage is offering flash performance with the economics of disk as well as innovative licensing models. And from a platform perspective, Dell — as a leading x86 server supplier — is well positioned to leverage its server expertise to offer new storage architectures. As Dell strives to execute on its mission, the company is accelerating the availability of these optimal design attributes from across the Dell Storage portfolio. Dell Storage continues to invest in its existing storage portfolio and customer base. These investments not only provide investment protection today but also enable Dell Storage customers to transition, over time if they choose, to new IT infrastructure and software-defined storage models in the future. -

DELL INC. Darren Thomas, VP & GM of Enterprise Storage
DELL INC. Darren Thomas, VP & GM of Enterprise Storage Business Raymond James IT Supply Chain Conference December 14, 2010 at 7:15 a.m. CT Brian Alexander, Raymond James: Good morning, everybody. Welcome to the Raymond James IT Supply Chain Conference. If I haven't met you, I'm Brian Alexander, and I'm one of the analysts at Raymond James. I cover the supply chain, which includes hardware distribution and EMS. Thanks, everybody, for coming. I think this is our 11th annual event here at Raymond James. The Conference has a long tradition prior to Raymond James. I think we've been doing this for about 20 plus years. Hopefully, you'll find the mix of companies will give you unique insights into demand trends and inventory trends and come away with a lot of good investment ideas. Many of you have come a long way and braved the weather, so we really appreciate all of you being here today. Just a little bit about the lay of the land, we have a very full day. We have 18 company presentations, most of which are followed by breakout sessions. If you could refer to the pocket guides for details on times and presenters and whether there is a breakout. There are also signs outside the breakout rooms that'll let you know. We're running two tracks. Track One is this room, this is Aster Two, and breakouts for this room are right next door in Aster One. Track Two is the Whitney Room, which is just across the hall, and the breakouts for the Whitney Room are in the Manhattan Room. -

Dell Equallogic Fs7500: Unified Storage Simplifies File Sharing and Accelerates Virtualization January 2012
SOLUTION BRIEF DELL EQUALLOGIC FS7500: UNIFIED STORAGE SIMPLIFIES FILE SHARING AND ACCELERATES VIRTUALIZATION JANUARY 2012 With the introduction of the FS7500 NAS appliance for the EqualLogic PS Series, Dell customers now have a unified storage option to further reduce management overhead and improve efficiency. All too often, companies have been forced to de- ploy different storage platforms for different needs: NAS for file-based applications and user file shares and SAN for block-based applications and high-performance virtualized workloads. The FS7500 changes the game. Your unified storage solution should let you easily scale your file shares to handle today’s tremen- dous growth in unstructured data. It should also accelerate and simplify your virtualization efforts by giving you the freedom to choose the best storage protocol for each virtual workload based on your unique application requirements, skill sets, and existing storage investments. Moreover, your unified storage must handle unpredictable and spiky bursts in demand, without run- ning into traditional limits on file system size or adding more work for storage administrators. Per- formance must scale linearly with capacity, and you shouldn’t end up with islands of misfit and ineffi- cient storage due to the limitations of any one array architecture. In this technology brief, we explore how Dell’s customers can benefit from the addition of scale-out NAS to the leading scale-out iSCSI SAN storage family. UNIFIED VIRTUALIZED STORAGE: THE BEST OF BOTH STORAGE WORLDS In the virtual world, storage administrators need more from their networked storage: It must handle the massive growth in unstructured file data of various types It must help to virtualize more workloads without compromising storage efficiency Traditionally, customers have often chosen distinct storage solutions for these challenges. -

Netbackup ™ Enterprise Server and Server 8.0 - 8.X.X OS Software Compatibility List Created on September 08, 2021
Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List Created on September 08, 2021 Click here for the HTML version of this document. <https://download.veritas.com/resources/content/live/OSVC/100046000/100046611/en_US/nbu_80_scl.html> Copyright © 2021 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and NetBackup are trademarks or registered trademarks of Veritas Technologies LLC in the U.S. and other countries. Other names may be trademarks of their respective owners. Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List 2021-09-08 Introduction This Software Compatibility List (SCL) document contains information for Veritas NetBackup 8.0 through 8.x.x. It covers NetBackup Server (which includes Enterprise Server and Server), Client, Bare Metal Restore (BMR), Clustered Master Server Compatibility and Storage Stacks, Deduplication, File System Compatibility, NetBackup OpsCenter, NetBackup Access Control (NBAC), SAN Media Server/SAN Client/FT Media Server, Virtual System Compatibility and NetBackup Self Service Support. It is divided into bookmarks on the left that can be expanded. IPV6 and Dual Stack environments are supported from NetBackup 8.1.1 onwards with few limitations, refer technote for additional information <http://www.veritas.com/docs/100041420> For information about certain NetBackup features, functionality, 3rd-party product integration, Veritas product integration, applications, databases, and OS platforms that Veritas intends to replace with newer and improved functionality, or in some cases, discontinue without replacement, please see the widget titled "NetBackup Future Platform and Feature Plans" at <https://sort.veritas.com/netbackup> Reference Article <https://www.veritas.com/docs/100040093> for links to all other NetBackup compatibility lists. -
Chapter 11: Implementing File Systems In-Memory File-System Structures
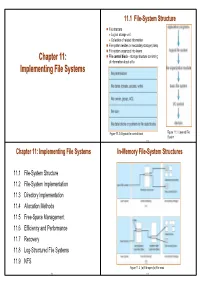
11.1 File-System Structure File structure z Logical storage unit z Collection of related information File system resides on secondary storage (disks) File system organized into layers Chapter 11: File control block – storage structure consisting Chapter 11: of information about a file Implementing File Systems Figure 11.2 A typical file-control block Figure 11.1 Layered File System 11.3 Chapter 11: Implementing File Systems In-Memory File-System Structures 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space Management 11.6 Efficiency and Performance 11.7 Recovery 11.8 Log-Structured File Systems 11.9 NFS Figure 11.3 (a) File open (b) File read 11.2 11.4 Virtual File Systems 11.4 Allocation Methods Virtual File Systems (VFS) provide an object-oriented way of implementing file systems. VFS allows the same system call interface (API) to be used for different types of An allocation method refers to how disk blocks are file systems. allocated for files: The API is to the VFS interface, rather than any specific type of file system. 11.4.1 Contiguous allocation 11.4.2 Linked allocation 11.4.3 Indexed allocation Figure 11.4 Schematic View of Virtual File System 11.5 11.7 11.3 Directory Implementation 11.4.1 Contiguous Allocation Linear list of file names with pointer to the data blocks. Each file occupies a set of contiguous blocks on the disk z advantage: simple to program Advantages z disadvantage: time-consuming to execute z Simple – only require starting location (block #) and Hash Table – linear list with hash data structure. -

2010 Dell Analyst Meeting
2010 Dell Analyst Meeting June 24, 2010 Welcome Rob Williams Director, Investor Relations Forward-Looking Statements Special note As discussed in our Form 10-Q filed with the SEC on June 10, 2008, in connection with ongoing settlement discussions between the company and the SEC staff, the parties have discussed a settlement framework relating to the previously reported SEC investigation. However, due to the sensitive, confidential and continuing nature of these discussions, we will not be commenting on or answering questions regarding the status of the SEC investigation or the potential settlement as it relates to the company or any individual employees, but rather we welcome you to review the public disclosures contained in the company’s filings with the SEC for more information. Forward Looking Statements: Statements in this presentation that relate to future results and events (including statements about Dell’s future financial and operating performance, anticipated customer demand including client refresh timing and scope, enterprise solutions strategies, other operating strategies, strategic investments, sales volumes, stock buybacks, currency fluctuations, pricing, component cost and availability, and operating synergies as well as the financial guidance with respect to revenue, non-GAAP operating income and cash flow from operations) are “forward-looking statements” within the meaning of the Private Securities Litigation Reform Act of 1995 and are based on Dell's current expectations. In some cases, you can identify these statements -

Linux Last Updated: 2018-09-11 Legal Notice Copyright © 2018 Veritas Technologies LLC
Storage Foundation 7.4 Configuration and Upgrade Guide - Linux Last updated: 2018-09-11 Legal Notice Copyright © 2018 Veritas Technologies LLC. All rights reserved. Veritas and the Veritas Logo are trademarks or registered trademarks of Veritas Technologies LLC or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This product may contain third-party software for which Veritas is required to provide attribution to the third-party (“Third-Party Programs”). Some of the Third-Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Refer to the third-party legal notices document accompanying this Veritas product or available at: https://www.veritas.com/about/legal/license-agreements The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Veritas Technologies LLC and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. VERITAS TECHNOLOGIES LLC SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. -

Storage Foundation Cluster File System Release Notes
Veritas Storage Foundation™ Cluster File System Release Notes HP-UX 5.0 Maintenance Pack 1 Veritas Storage Foundation Cluster File System Release Notes Copyright © 2007 Symantec Corporation. All rights reserved. Storage Foundation Cluster File System 5.0 Maintenance Pack 1 Symantec, the Symantec logo, Veritas, and Veritas Storage Foundation are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THIS DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID, SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be “commercial computer software” and “commercial computer software documentation” as defined in FAR Sections 12.212 and DFARS Section 227.7202. Symantec Corporation 20330 Stevens Creek Blvd. Cupertino, CA 95014 www.symantec.com Printed in the United States of America. Third-party legal notices Third-party software may be recommended, distributed, embedded, or bundled with this Symantec product. -

Symantec™ Cluster Server 6.1 Bundled Agents Reference Guide - Solaris
Symantec™ Cluster Server 6.1 Bundled Agents Reference Guide - Solaris July 2015 Symantec™ Cluster Server Bundled Agents Reference Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Product version: 6.1 Document version: 6.1 Rev 3 Legal Notice Copyright © 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Veritas, Veritas Storage Foundation, CommandCentral, NetBackup, Enterprise Vault, and LiveUpdate are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. -

Ada 3.10 Sp1
Compatibility Guide ADA 3.10 SP1 Atempo Paris Headquarters |23 Avenue Carnot, 91300 MASSY|Tél: +33 164 868 300 |[email protected] N°1 EUROPEAN SOFTWARE VENDOR FOR DATA PROTECTION ATEMPO.COM Compatibility Guide Author : Louis-Frederic Laszlo ADA 3.10 SP1 Diffusion : Public Date : 11/02/2020 Details of this document Title ADA 3.10 SP1 Type Compatibility Guide Date 11/02/2020 Author Louis-Frederic Laszlo Classification Public Status Released Versions 01/08/2019 Release ADA 3.9 SP2 11/02/2020 Release ADA 3.10 11/02/2020 Release ADA 3.10 SP1 Atempo Paris Headquarters |23 Avenue Carnot, 91300 MASSY|Tél: +33 164 868 300 |[email protected] N°1 EUROPEAN SOFTWARE VENDOR FOR DATA PROTECTION ATEMPO.COM Compatibility Guide Author : Louis-Frederic Laszlo ADA 3.10 SP1 Diffusion : Public Date : 11/02/2020 Table of contents 01. General Information ........................................................................................................................... 4 02. Important Notices ............................................................................................................................... 4 03. Atempo-Digital Archive – Server ...................................................................................................... 5 04. Atempo-Digital Archive – Agent ....................................................................................................... 5 05. Atempo-Digital Archive – Administration Console ........................................................................ 7 06. Atempo-Digital Archive – Native -

Lunworks for Solaris Version 1.0
Document: 313429201 LUNWorks for Solaris Version 1.0 Installation Manual LUNWorks for Solaris Version 1.0 Installation Manual Information contained in this publication is subject to change. In the event of changes, the publication will be revised. Comments concerning its contents should be directed to: Information Development Storage Technology Corporation One StorageTek Drive Louisville, CO 80028-2201 USA Information Control Statement: The information in this document is confidential and proprietary to Storage Technology Corporation and may be used only under terms of the product license or nondisclosure agreement. The information in this document, including any associated software program, may not be disclosed, disseminated, or distributed in any manner without written consent of Storage Technology Corporation. Limitations on Warranties and Liability: This document neither extends nor creates warranties of any nature, expressed or implied. Storage Technology Corporation cannot accept any responsibility for your use of the information in this document or for your use of any associated software program. You are responsible for backing up your data. You should be careful to ensure that your use of the information complies with all applicable laws, rules, and regulations of the jurisdictions in which it is used. No part or portion of this document may be reproduced in any manner or in any form without the written permission of Storage Technology Corporation. © 2000, Storage Technology Corporation, Louisville, CO, USA. All rights reserved. -

The Evolution of File Systems
The Evolution of File Systems Thomas Rivera, Hitachi Data Systems Craig Harmer, April 2011 SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individuals may use this material in presentations and literature under the following conditions: Any slide or slides used must be reproduced without modification The SNIA must be acknowledged as source of any material used in the body of any document containing material from these presentations. This presentation is a project of the SNIA Education Committee. Neither the Author nor the Presenter is an attorney and nothing in this presentation is intended to be nor should be construed as legal advice or opinion. If you need legal advice or legal opinion please contact an attorney. The information presented herein represents the Author's personal opinion and current understanding of the issues involved. The Author, the Presenter, and the SNIA do not assume any responsibility or liability for damages arising out of any reliance on or use of this information. NO WARRANTIES, EXPRESS OR IMPLIED. USE AT YOUR OWN RISK. The Evolution of File Systems 2 © 2012 Storage Networking Industry Association. All Rights Reserved. 2 Abstract The File Systems Evolution Over time additional file systems appeared focusing on specialized requirements such as: data sharing, remote file access, distributed file access, parallel files access, HPC, archiving, security, etc. Due to the dramatic growth of unstructured data, files as the basic units for data containers are morphing into file objects, providing more semantics and feature- rich capabilities for content processing This presentation will: Categorize and explain the basic principles of currently available file system architectures (e.g.