Optimization of Base Location and Patrol Routes for Unmanned Aerial Vehicles in Border Intelligence, Surveillance and Reconnaissance
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Annual Report 2016
GROUP OVERVIEW Founded in 1999, Kaisa Group Holdings Ltd. (the “Company” or “Kaisa”) and its subsidiaries (collectively the “Group”) are large-scale integrated property developer. The shares of the Company commenced trading on the Main Board of The Stock Exchange of Hong Kong Limited on 9 December 2009. Over the years, the Group has been primarily focusing on urban property development. The scope of its business covers property development, commercial operation, hotel management and property management services with products comprising residential properties, villas, offices, serviced apartments, integrated commercial buildings and mega urban complexes. Founded in Shenzhen, the Group has expanded to cover the economically-vibrant cities and regions, including the Pearl River Delta, the Yangtze River Delta, the Western China Region, the Central China region and the Pan-Bohai Bay Rim. Kaisa is committed to the core values of “professionalism, innovation, value and responsibility” by actively participating in a wide range of urban development projects in China and we believe it will inject creativity into China’s urbanisation process. We believe our brand “Kaisa” remains to be our pledge to carry out high quality property developments, to surpass the industry’s standards and requirements, and of devotion to customer satisfaction. CONTENTS 2 CORPORATE INFORMATION 4 MILESTONES 6 AWARDS 10 CHAIRMAN’S STATEMENT 14 MANAGEMENT DISCUSSION AND ANALYSIS 22 PROJECT PORTFOLIO — SUMMARY 50 DIRECTORS AND SENIOR MANAGEMENT 55 ENVIRONMENTAL, SOCIAL AND GOVERNANCE REPORT 62 CORPORATE GOVERNANCE REPORT 75 REPORT OF THE DIRECTORS 86 INDEPENDENT AUDITOR’S REPORT 91 CONSOLIDATED STATEMENT OF PROFIT OR LOSS AND OTHER COMPREHENSIVE INCOME 92 CONSOLIDATED STATEMENT OF FINANCIAL POSITION 94 CONSOLIDATED STATEMENT OF CHANGES IN EQUITY 95 CONSOLIDATED STATEMENT OF CASH FLOWS 96 NOTES TO THE CONSOLIDATED FINANCIAL STATEMENTS 186 FINANCIAL SUMMARY 2 KAISA GROUP HOLDINGS LTD. -

2015 Annual Report New Business Opportunities and Spaces Which Rede Ne Aesthetic Standards Breathe New Life Into Throbbing and a New Way of Living
MISSION (Stock Code: 00917) TRANSFORMING CITY VISTAS CREATING MODERN We have dedicated ourselves in rejuvenating old city neighbourhood through comprehensive COMMUNITIES redevelopment plans. As a living embodiment of We pride ourselves on having created China’s cosmopolitan life, these mixed-use redevel- large-scale self contained communities opments have been undertaken to rejuvenate the that nurture family living and old city into vibrant communities character- promote a healthy cultural ised by eclectic urban housing, ample and social life. public space, shopping, entertain- ment and leisure facilities. SPURRING BUSINESS REFINING LIVING OPPORTUNITIES We have developed large-scale multi- LIFESTYLE purpose commercial complexes, all Our residential communities are fully equipped well-recognised city landmarks that generate with high quality facilities and multi-purpose Annual Report 2015 new business opportunities and spaces which redene aesthetic standards breathe new life into throbbing and a new way of living. We enable owners hearts of Chinese and residents to experience the exquisite metropolitans. and sensual lifestyle enjoyed by home buyers around the world. Annual Report 2015 MISSION (Stock Code: 00917) TRANSFORMING CITY VISTAS CREATING MODERN We have dedicated ourselves in rejuvenating old city neighbourhood through comprehensive COMMUNITIES redevelopment plans. As a living embodiment of We pride ourselves on having created China’s cosmopolitan life, these mixed-use redevel- large-scale self contained communities opments have -

Vietnamese Female Spouses' Language Use Patterns in Self Initiated Admonishment Sequences in Bilingual Taiwanese Families* L
Novitas-ROYAL (Research on Youth and Language), 2014, 8(1), 77-96. VIETNAMESE FEMALE SPOUSES’ LANGUAGE USE PATTERNS IN SELF INITIATED ADMONISHMENT SEQUENCES IN BILINGUAL TAIWANESE FAMILIES* Li-Fen WANG1 Abstract: This paper aims to identify how Taiwanese and Mandarin (the two dominant languages in Taiwan) are used as interactional resources by Vietnamese female spouses in bilingual Taiwanese families. Three Vietnamese-Taiwanese transnational families (a total of seventeen people) participated in the research, and mealtime talks among the Vietnamese wives and their Taiwanese family members were audio-/video-recorded. Conversation analysis (CA) was adopted to analyse the seven hours of data collected. It was found that the Vietnamese participants orient to Taiwanese and Mandarin as salient resources in admonishment sequences. Specifically, it was identified that the two languages serve as contextualisation cues and framing devices in the Vietnamese participants’ self-initiated admonishment sequences. Keywords: Conversation analysis, cross-border marriage, intercultural communication Özet: Bu çalışma, Tayvanca ve Çince’nin (Tayvan’daki yaygın iki dil) iki dil konuşan Tayvanlı ailelerdeki Vietnamlı kadın eşler tarafından etkileşimsel kaynak olarak nasıl kullanıldığını göstermeyi amaçlamaktadır. Üç Vietnamlı-Tayvanlı aile araştırmaya katılmıştır (toplamda on yedi kişi), ve Vietnamlı kadınlar ve onların Tayvanlı aile üyeleri arasındaki yemek zamanı konuşmaları sesli ve görüntülü olarak kaydedilmiştir. Toplanan yedi saatlik veriyi analiz etmek -

Development of High-Speed Rail in the People's Republic of China
ADBI Working Paper Series DEVELOPMENT OF HIGH-SPEED RAIL IN THE PEOPLE’S REPUBLIC OF CHINA Pan Haixiao and Gao Ya No. 959 May 2019 Asian Development Bank Institute Pan Haixiao is a professor at the Department of Urban Planning of Tongji University. Gao Ya is a PhD candidate at the Department of Urban Planning of Tongji University. The views expressed in this paper are the views of the author and do not necessarily reflect the views or policies of ADBI, ADB, its Board of Directors, or the governments they represent. ADBI does not guarantee the accuracy of the data included in this paper and accepts no responsibility for any consequences of their use. Terminology used may not necessarily be consistent with ADB official terms. Working papers are subject to formal revision and correction before they are finalized and considered published. The Working Paper series is a continuation of the formerly named Discussion Paper series; the numbering of the papers continued without interruption or change. ADBI’s working papers reflect initial ideas on a topic and are posted online for discussion. Some working papers may develop into other forms of publication. Suggested citation: Haixiao, P. and G. Ya. 2019. Development of High-Speed Rail in the People’s Republic of China. ADBI Working Paper 959. Tokyo: Asian Development Bank Institute. Available: https://www.adb.org/publications/development-high-speed-rail-prc Please contact the authors for information about this paper. Email: [email protected] Asian Development Bank Institute Kasumigaseki Building, 8th Floor 3-2-5 Kasumigaseki, Chiyoda-ku Tokyo 100-6008, Japan Tel: +81-3-3593-5500 Fax: +81-3-3593-5571 URL: www.adbi.org E-mail: [email protected] © 2019 Asian Development Bank Institute ADBI Working Paper 959 Haixiao and Ya Abstract High-speed rail (HSR) construction is continuing at a rapid pace in the People’s Republic of China (PRC) to improve rail’s competitiveness in the passenger market and facilitate inter-city accessibility. -

High-Speed Rail Services in Asia
THE ASIAN JOURNAL Journal of Transport and Infrastructure Volume 1 January 2019 Special Issue JOURNAL OF HIGH SPEED RAIL SERVICES IN ASIA TRANSPORT(A Joint Publication of ADBI and AND AITD) High-Speed Rail and Station Area Development INFRASTRShreyas P Bharule Illustrating Spillover Effects of Infrastructure Naoyuki Yoshino, Nuobu Renzhi and Umid Abidhadjaev Modeling Spatiotemporal Urban Spillover Effect of HSR Infrastructure Development Satoshi Miyazawa, K E Seetha Ram and Jetpan Wetwitoo Japan: HSR’s Agglomeration Impact Jetpan Wetwitoo Development of HSR in People’s Republic of China Haixiao Pan and Gao Ya HSR Effect on Urban Spatial Correlation: A Big Data Analysis of People’s Republic of China’s Largest Urban Agglomeration Ji Han Japan: Integrated Land Development and Passenger Railway Operation Fumio Kurosaki Spill-Over and Straw Effects of HSR K E Seetha Ram and Shreyas P Bharule High Speed Rail in India: The Stepping Stone to Enhanced Mobility Anjali Goyal THE ASIAN JOURNAL Journal of Transport and Infrastructure Volume 1 January 2019 Special Issue HIGH SPEED RAIL SERVICES IN ASIA (A Joint Publication of ADBI and AITD) ASIAN INSTITUTE OF ASIAN DEVELOPMENT BANK TRANSPORT DEVELOPMENT INSTITUTE THE ASIAN JOURNAL Editorial Board K. L. Thapar (Chairman) Prof. S. R. Hashim Dr. Y. K. Alagh T.C.A. Srinivasa-Raghavan © January 2019, Asian Institute of Transport Development, New Delhi. All rights reserved ISSN 0971-8710 The views expressed in the publication are those of the authors and do not necessarily reflect the views of the organizations to which they belong or that of the Board of Governors of the Institute or its member countries. -

PLECO: an English-Chinese Dictionary App That Allows You To
Apps to install: PLECO: An English-Chinese dictionary app that allows you to write the Chinese in characters or pinyin (Chinese words with Latin characters), and will pronounce the Chinese for you. Shanghai is surprisingly easy to get around with English only, but Pleco might come in handy, particularly at small restaurants. Explore Shanghai: Metro map of Shanghai Packing: Prepare for cool and wet (a lot like a Pacific northwest winter). Electronics: Check any electric/electronic stuff to see if you need an adapter. China is on 220 volts, 50 Hz. You can bring an adapter with you or purchase one here for cheap. VPN: If you want access to Google and/or Facebook, buy a VPN service. One subscription will cover up to three devices. ExpressVPN: $12.95 per month MoleVPN: $3.00 per week $5.00 per month Not as reliable as ExpressVPN, but probably fine short term. Transportation: Taxi: readily available all over the city. Green light on top: ready for Customers. Red light or no light on top: currently busy or not in service. Starting fee is 16 RMB for the first 3km. Give the following directions to your driver to return to campus (the faculty club is the red star on the map below). 出租车司机,您好! 请送这位外籍客人至: 上海交通大学 徐汇校区 教师活动中心 地址:上海市 华山路1954号 Metro: Most cost efficient way to get around in Shanghai. A short trip is 3 RMB, and a long one is 6 RMB. Directions to campus from the Metro: Disembark at either the Jiao Tong University station on lines 10 and 11 or at the Xu Jia Hui station on lines 1, 9, and 11. -

Download Download
The 18th International Planning History Society Conference - Yokohama, July 2018 Historical Analysis of Urban Public Transportation Development in Modern Tianjin (1902-1949) Yili Zhao*, Lin Feng**, Yanchen Sun***, Kun Song*** * PhD, Tianjin University, [email protected] ** Lecture, Tianjin University, [email protected] *** PhD, Tianjin University, [email protected] **** Professor, Tianjin University, [email protected] Tianjin was the earliest city opening urban public transport lines in China. Urban public transportation had profound impacts on urban construction and on the formation of urban structure in Tianjin from 1902 to 1949. Based on the background of urban development, this paper firstly divides the evolution process of public transportation represented by tramways and buses into three periods from the perspectives of the distribution, quantity and operation status of public transportation lines. It then analyses the strong influence of public transportation on urban roads construction from the view of the increased municipal income, road widening, improvement of pavement quality, and bridges construction and maintenance. Finally, by using qualitative and quantitative analysis and superposing the related statistical data with the historical map, it analyses the relationship among public transportation line density, land value partition and basic urban structure, and certifies they were highly relative. In conclusion, the paper argues that Tianjin urban public transport network was based on trams and supplemented by buses, and not only planning ideas but also advanced municipal technologies from the West like public transportation system were also indispensable supports in the process of urban modernization in Chinese modern treaty ports. Key words: Urban Public Transportation, Modern Tianjin, Tram, Roads Construction, Urban Structure Introduction The transformation of Chinese modern treaty ports was closely related to western planning ideas of the time. -

Return of Organization Exempt from Income Tax OMB No
EXTENDED TO MAY 15, 2019 Return of Organization Exempt From Income Tax OMB No. 1545-0047 Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except private foundations) 2017 Department of the Treasury | Do not enter social security numbers on this form as it may be made public. Open to Public Internal Revenue Service | Go to www.irs.gov/Form990 for instructions and the latest information. Inspection A For the 2017 calendar year, or tax year beginning JUL 1, 2017 and ending JUN 30, 2018 B Check if C Name of organization D Employer identification number applicable: Address change YALE-CHINA ASSOCIATION, INC. Name change Doing business as 06-0646971 Initial return Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Final return/ 442 TEMPLE ST. BOX 208223 203-432-0880 termin- ated City or town, state or province, country, and ZIP or foreign postal code G Gross receipts $ 1,615,629. Amended X return NEW HAVEN, CT 06520-8223 H(a) Is this a group return Applica- tion F Name and address of principal officer:DAVID YOUTZ for subordinates? ~~ Yes X No pending 442 TEMPLE STREET, NEW HAVEN, CT 06520 H(b) Are all subordinates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( )§ (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: | WWW.YALECHINA.ORG H(c) Group exemption number | K Form of organization: X Corporation Trust Association Other | L Year of formation: 1901 M State of legal domicile: CT Part I Summary 1 Briefly describe the organization's mission or most significant activities: THE YALE-CHINA ASSOCIATION INSPIRES PEOPLE TO LEARN AND SERVE TOGETHER. -

Return of Organization Exempt from Income
OMB No. 1545-0047 Form 990 Return of Organization Exempt From Income Tax Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except private foundations) 2017 ▶ Do not enter social security numbers on this form as it may be made public. Open to Public Department of the Treasury Internal Revenue Service ▶ Go to www.irs.gov/Form990 for instructions and the latest information. Inspection A For the 2017 calendar year, or tax year beginning 07/01 , 2017, and ending 06/30 , 20 18 B Check if applicable: C Name of organization MERCY CORPS D Employer identification number Address change Doing business as 91-1148123 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 45 SW ANKENY STREET 503-896-5000 Final return/terminated City or town, state or province, country, and ZIP or foreign postal code Amended return PORTLAND, OR, 97204 G Gross receipts $ 310,386,162 Application pending F Name and address of principal officer: Beth deHamel H(a) Is this a group return for subordinates? Yes No 45 SW Ankeny Street, Portland, OR 97204 H(b) Are all subordinates included? Yes No I Tax-exempt status: ✔ 501(c)(3) 501(c) ( ) ◀ (insert no.) 4947(a)(1) or 527 If “No,” attach a list. (see instructions) J Website: ▶ WWW.MERCYCORPS.ORG H(c) Group exemption number ▶ K Form of organization: Corporation Trust Association Other ▶ L Year of formation: 1981 M State of legal domicile: WA Part I Summary 1 Briefly describe the organization’s mission or most significant activities: Mercy Corps is a leading global organization powered by the belief that a better world is possible. -

Shenyang for Hong Kong People Who Are Working, Living and Doing Business in the Mainland
Practical Guide for Hong Kong People Living in the Mainland – Shenyang For Hong Kong people who are working, living and doing business in the Mainland The Office of the Government of the Hong Kong Special Administrative Region in Beijing About the Office of the Government of the Hong Kong Special Administrative Region in Beijing (BJO) The BJO was formally set up under the Basic Other Contacts Law of the Hong Kong Special Administrative Assistance to Hong Kong Residents Unit Region (HKSAR) on 4 March 1999. Its main The Immigration Department of the functions include: Government of the HKSAR • Further enhancing the HKSAR Government’s Hotline: (852) 1868 liaison and communication with the Central Fax: (852) 2519 3536 People’s Government, Mainland authorities, Address: 9/F, Immigration Tower, and provinces, municipalities, autonomous 7 Gloucester Road, Wan Chai, regions under the purview of the BJO Hong Kong • Facilitating exchange and cooperation in business and other aspects between Hong Kong Economic and Trade Office in Hong Kong and the Mainland Chengdu (CDETO) • Promoting Hong Kong to people of the Tel: (86 28) 8676 8301 Mainland Fax: (86 28) 8676 8300 • Processing applications for entry to Address: 38/F, Tower 1, Plaza Central, Hong Kong 8 Shuncheng Street, • Providing practical assistance to Hong Kong Yan Shi Kou, Chengdu, people in distress in the Mainland Sichuan Province, China (Postal code: 610016) The BJO is organised into seven divisions, namely: Hong Kong Economic and Trade Office in • Economic Affairs, Trade and Liaison Division -
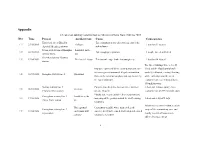
Appendix 83 Cases on Subway Construction Accidents in China from 2001 to 2019 NO
Appendix 83 cases on subway construction accidents in China from 2001 to 2019 NO. Time Project Accident type Cause Consequence Earthwork site at Zhuzilin The continuous scour of heavy rain caused the (1) 25/05/2001 Collapse 1 dead and 1 injured depot of Shenzhen subway soil to loosen Luban road station of Shanghai Landslide in the (2) 20/08/2001 Not enough precipitation 4 people buried and killed subway line 4 pit Shenzhen subway Guomao (3) 19/04/2002 Mechanical injury Traction wire rope broke into two pieces 2 dead and 4 injured station The three buildings were severely Improper command by the construction unit, on- tilted, and the flood control wall site management personnel illegal construction, partially collapsed, causing flooding (4) 01/07/2003 Shanghai subway line 4 Quicksand flaws in the construction plan, and supervision by of the cofferdam and the direct the supervision unit economic loss was estimated to be 150 million yuan Beijing subway line 5 Construction discipline was not strict, workers 3 dead and 1 minor injury, direct (5) 08/10/2003 Overturn Chongwenmen station operate illegally economic loss of 297 thousand yuan Muddy soil, heavy rainfall led to expansion and Guangzhou subway line 3 Landslide in the (6) 17/03/2004 loosening of the ground around the shaft causing 1 dead and delay of 5 days Panyu Dashi station pit landslides Subsidence occurred within a certain Underground Continuous rainfall, water immersed in the Guangzhou subway line 3 range of the surrounding area, and (7) 01/04/2004 continuous wall concrete brick -

Handbook on High-Speed Rail and Quality of Life
HANDBOOK ON HIGH-SPEED RAIL AND QUALITY OF LIFE Edited by Yoshitsugu Hayashi, KE Seetha Ram, and Shreyas Bharule ASIAN DEVELOPMENT BANK INSTITUTE Handbook on High-Speed Rail and Quality of Life Edited by Yoshitsugu Hayashi, KE Seetha Ram, and Shreyas Bharule ASIAN DEVELOPMENT BANK INSTITUTE © 2020 Asian Development Bank Institute All rights reserved. ISBN 978-4-89974-201-2 (Print) ISBN 978-4-89974-202-9 (PDF) The views in this publication do not necessarily reflect the views and policies of the Asian Development Bank Institute (ADBI), its Advisory Council, ADB’s Board or Governors, or the governments of ADB members. ADBI does not guarantee the accuracy of the data included in this publication and accepts no responsibility for any consequence of their use. ADBI uses proper ADB member names and abbreviations throughout and any variation or inaccuracy, including in citations and references, should be read as referring to the correct name. By making any designation of or reference to a particular territory or geographic area, or by using the term “recognize,” “country,” or other geographical names in this publication, ADBI does not intend to make any judgments as to the legal or other status of any territory or area. Users are restricted from reselling, redistributing, or creating derivative works without the express, written consent of ADBI. The Asian Development Bank recognizes "China" as the People's Republic of China, "Korea" as the Republic of Korea, and "Vietnam" as Viet Nam. Note: In this publication, “$” refers to US dollars. Asian Development Bank Institute Kasumigaseki Building 8F 3-2-5, Kasumigaseki, Chiyoda-ku Tokyo 100-6008, Japan www.adbi.org Contents Tables, Figures, and Boxes vi Contributors xvi Preface xix Acknowledgments xxi Abbreviations xxii Introduction 1 Naoyuki Yoshino, Shreyas Bharule, Yoshitsugu Hayashi, and KE Seetha Ram PART I: Frontiers of Modeling the Spillover Effects of High-Speed Rail for Quality of Life Key Messages 15 1.