IEEE Reliability Society Technical Operations Annual Technology Report for 2008
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
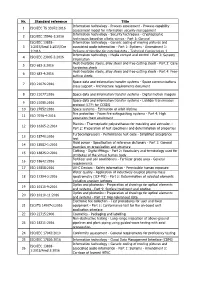
Nr. Standard Reference Title 1 ISO/IEC TS 33072:2016 Information Technology
Nr. Standard reference Title Information technology - Process assessment - Process capability 1 ISO/IEC TS 33072:2016 assessment model for information security management Information technology - Security techniques - Cryptographic 2 ISO/IEC 15946-1:2016 techniques based on elliptic curves - Part 1: General ISO/IEC 13818- Information technology - Generic coding of moving pictures and 3 1:2015/Amd 1:2015/Cor associated audio information - Part 1: Systems - Amendment 1: 1:2016 Delivery of timeline for external data - Technical Corrigendum 1 Information technology - Media context and control - Part 3: Sensory 4 ISO/IEC 23005-3:2016 information Heat-treatable steels, alloy steels and free-cutting steels - Part 3: Case- 5 ISO 683-3:2016 hardening steels Heat-treatable steels, alloy steels and free-cutting steels - Part 4: Free- 6 ISO 683-4:2016 cutting steels Space data and information transfer systems - Space communications 7 ISO 21076:2016 cross support - Architecture requirements document 8 ISO 21077:2016 Space data and information transfer systems - Digital motion imagery Space data and information transfer systems - Licklider transmission 9 ISO 21080:2016 protocol (LTP) for CCSDS 10 ISO 27852:2016 Space systems - Estimation of orbit lifetime Fire protection - Foam fire extinguishing systems - Part 4: High 11 ISO 7076-4:2016 expansion foam equipment Plastics - Thermoplastic polyurethanes for moulding and extrusion - 12 ISO 16365-2:2014 Part 2: Preparation of test specimens and determination of properties Turbocompressors - Performance test -

FI-STAR Deliverable D1.1 Has Already Discussed Legal Requirements Related to Data Security Breach Notifications
Ref. Ares(2014)706091 - 13/03/2014 Deliverable D2.1 Standardisation and Certification requirements Editor: Franck Le Gall, easy global markets Deliverable nature: Report (R) Dissemination level: Public (PU) (Confidentiality) Contractual delivery Dec. 2013 date: Actual delivery date: Jan. 2014 Suggested readers: Version: 1.1 Total number of 74 pages: Keywords: Standardisation, certification Abstract This document details the technical requirements resulting from existing standards and prepares future certification process. FI-STAR FP7-ICT-604691 D1.2 Standardisation and Certification requirements Disclaimer This document contains material, which is the copyright of certain FI-STAR consortium parties, and may not be reproduced or copied without permission. All FI-STAR consortium parties have agreed to full publication of this document. The commercial use of any information contained in this document may require a license from the proprietor of that information. Neither the FI-STAR consortium as a whole, nor a certain part of the FI-STAR consortium, warrant that the information contained in this document is capable of use, nor that use of the information is free from risk, accepting no liability for loss or damage suffered by any person using this information. This project has received funding from the European Union’s Seventh Framework Programme for research, technological development and demonstration under grant agreement no 604691. Impressum [Full project title] Future Internet Social and Technological Alignment Research [Short project -

Standards Action Layout SAV3645.Fp5
PUBLISHED WEEKLY BY THE AMERICAN NATIONAL STANDARDS INSTITUTE 25 West 43rd Street, NY, NY 10036 VOL. 36, #45 November 11, 2005 Contents American National Standards Call for Comment on Standards Proposals ................................................ 2 Call for Comment Contact Information ....................................................... 6 Initiation of Canvasses ................................................................................. 8 Final Actions.................................................................................................. 9 Project Initiation Notification System (PINS).............................................. 10 International Standards ISO Draft Standards ...................................................................................... 15 ISO Newly Published Standards .................................................................. 16 Proposed Foreign Government Regulations................................................ 18 Information Concerning ................................................................................. 19 Standards Action is now available via the World Wide Web For your convenience Standards Action can now be down- loaded from the following web address: http://www.ansi.org/news_publications/periodicals/standards _action/standards_action.aspx?menuid=7 American National Standards Call for comment on proposals listed This section solicits public comments on proposed draft new American National Standards, including the national adoption of Ordering Instructions -

Proceedings 2014 Download
EuroSPI² 2014 Proceedings Proceedings The papers in this book comprise the industrial proceedings of the EuroSPI² 2014 conference. They reflect the authors’ opinions and, in the interests of timely dissemination, are published as presented and without change. Their inclusion in this publication does not necessarily constitute endorsement by EuroSPI² and the publisher. DELTA Series about Process Improvement – ISBN 978-87-7398-157-3. EuroSPI² EuroSPI² is a partnership of large Scandinavian research companies and experience networks (SINTEF, DELTA, FiSMA), iSQI as a large German quality association, the American Society for Quality SW Division, and ISCN as the co-ordinating partner. The EuroSPI² conference presents and discusses results from systems, software and services process improvement and innovation (SPI) projects in industry and research, focusing on the gained benefits and the criteria for success. This year's event is the 21st of a series of conferences to which international researchers and professionals contribute their lessons learned and share their knowledge as they work towards the next higher level of software management professionalism. Since 2009 we have extended the scope of the conference from software process improvement to systems, software and service based process improvement. The Centre de Recherche Public Henri Tudor, Luxembourg, is the host of the EuroSPI² 2014 conference. CRP Henri Tudor is currently leading research projects in the areas of Advanced Materials Technologies, Health care technologies, Information -
Updated DEL2.2: Good Practices for Health Applications of Machine
INTERNATIONAL TELECOMMUNICATION UNION FG-AI4H-K-039 TELECOMMUNICATION STANDARDIZATION SECTOR ITU-T Focus Group on AI for Health STUDY PERIOD 2017-2020 Original: English WG(s): DAISAM E-meeting, 27-29 January 2021 DOCUMENT Source: Editors Title: Updated DEL2.2: Good practices for health applications of machine learning: Considerations for manufacturers and regulators Purpose: Discussion Contact: Luis Oala Email: [email protected] HHI Fraunhofer Germany Contact: Christian Johner Email: [email protected] Johner Institute for Healthcare IT Germany Contact: Pradeep Balachandran Email: [email protected] Technical Consultant (Digital Health) India Abstract: This document contains the latest draft of the FG-AI4H deliverable DEL02.2 "Good practices for health applications of machine learning: Considerations for manufacturers and regulators". This deliverable defines a set of guidelines intended to serve the AI solution developers/manufacturers on how to do conduct a comprehensive requirements analysis and to streamline the conformity assessment procedures to ensure regulatory compliance for the AI based Medical Devices (AI/ML-MD). International Telecommunication Union ITU-T FG-AI4H Deliverable TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (draft 27-01-2021) DEL2.2 Good practices for health applications of machine learning: Considerations for manufacturers and regulators - i - FG-AI4H-K-039 Summary This technical paper recommends a set of good machine learning practice guidelines to the manufacturers and regulators -
More on 2011 in the Annual Report
FRAUNHOFER INSTITUTE FOR EXPERIMentaL SOFTWARE ENGINEERING IESE ANNUAL REPORT 2011/2012 THE FRAUNHOFER INSTITUTE FOR EXPERIMENTAL SOFTWARE ENGINEERING IESE Fraunhofer Institute for Experimental Software Engineering IESE Fraunhofer-Platz 1 67663 Kaiserslautern Germany Phone +49 631 6800-6000 Fax +49 631 6800-1099 www.iese.fraunhofer.de Executive Director Prof. Dr. Dr. h. c. Dieter Rombach Software is a part of our lives. Embedded into everyday equipment, into living and working environments or modern means of transportation, countless processors and controllers make Scientific Director our lives simpler, safer, and more pleasant. We help organizations to develop software systems Prof. Dr.-Ing. that are reliable in every aspect, and provide empirical proof of the necessary processes, Peter Liggesmeyer methods, and techniques, emphasizing engineering-style principles such as measurability and transparency. Fraunhofer IESE in Kaiserslautern is one of the worldwide leading research institutes in the area of software and systems development. A major portion of the products offered by its collabora- tion partners is defined by software. These products range from automotive and transportation systems via automation and plant engineering, information systems, health care and medical systems to software systems for the public sector. The solutions allow flexible scaling. This makes the institute a competent technology partner for organizations of any size - from small companies to major corporations. Under the leadership of Prof. Dieter Rombach and Prof. Peter Liggesmeyer, Fraunhofer IESE has spent the last fifteen years making major contributions to strengthening the emerging IT hub Kaiserslautern. In the Fraunhofer Information and Communication Technology Group, it is cooperating with other Fraunhofer institutes on developing trend-setting key technologies for the future. -
Standards Action Layout SAV3847
PUBLISHED WEEKLY BY THE AMERICAN NATIONAL STANDARDS INSTITUTE 25 West 43rd Street, NY, NY 10036 VOL. 38, #47 November 23, 2007 Contents American National Standards Call for Comment on Standards Proposals................................................. 2 Call for Comment Contact Information........................................................ 6 Final Actions .................................................................................................. 8 Project Initiation Notification System (PINS) .............................................. 9 International Standards ISO Draft Standards....................................................................................... 12 ISO and IEC Newly Published Standards .................................................... 13 Proposed Foreign Government Regulations ................................................ 15 Information Concerning.................................................................................. 16 American National Standards Call for comment on proposals listed This section solicits public comments on proposed draft new American National Standards, including the national adoption of Ordering Instructions for "Call-for-Comment" Listings ISO and IEC standards as American National Standards, and on 1. Order from the organization indicated for the specific proposals to revise, reaffirm or withdraw approval of existing proposal. American National Standards. A draft standard is listed in this section under the ANSI-accredited standards developer (ASD) 2. Use the full -

ΩÓYE' G ¿Ƒä°T Iqgrh Øy Qó°Üj Øjôëñdg Áµ∏ªe
ΩÓYE’G ¿ƒÄ°T IQGRh øY Qó°üJ øjôëÑdG áµ∏ªe المراسلت ΩÉ©dG ±ô°ûªdG ᫪°SôdG IójôédG ΩÓYE’G ¿ƒÄ°T IQGRh 00973–17681493 :¢ùcÉa 26005 Ü .¢U øjôëÑdG áµ∏ªe–áeÉæªdG :»fhôàµdE’G ójôÑdG [email protected] الشتراكات ™jRƒàdG º°ùb ΩÓYE’G ¿ƒÄ°T IQGRh 00973 17871731- :¢ùcÉa 253 :Ü .¢U øjôëÑdG áµ∏ªe–áeÉæªdG øjôëÑdG áµ∏ªe–áeÉæªdG 26005 Ü .¢U á`«eƒµëdG á`©Ñ£ªdÉH â©`ÑWo Printed at the Government Printing Press PO.Box 26005 Manama, Kingdom of Bahrain 3 ملحق العدد: 3310 – الخميس 20 أبريل 2017 á°UÉN á«é«∏N á«æa íFGƒd OɪàYG ¿CÉ°ûH 2017 áæ°ùd (50) ºbQ QGôb 5 .........................................................................á«æWh á«æa íFGƒ∏c áë°üdG ´É£≤H ´É£≤H á°UÉN á«é«∏N á«æa íFGƒd OɪàYG ¿CÉ°ûH 2017 áæ°ùd (51) ºbQ QGôb 8 ........................................................ á«æWh á«æa íFGƒ∏c á«YGQõdGh á«FGò¨dG äÉéàæªdG á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (52) ºbQ QGôb 12 ................................á«æWh á«°SÉ«b äÉØ°UGƒªc ÉgOɪàYGh è«°ùædGh ∫õ¨dGh AÉ«ª«µdG ´É£≤H IQGO’G º¶f ´É£≤H á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (53) ºbQ QGôb 47 .....................................................................á«æWh á«°SÉ«b äÉØ°UGƒªc ÉgOɪàYGh á«FÉHô¡µdG Iõ¡LC’G ´É£≤H á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (54) ºbQ QGôb 51 ......................................................á«æWh á«°SÉ«b äÉØ°UGƒªc ÉgOɪàYGh á«fhôàµd’Gh á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (55) ºbQ QGôb 62 ............................á«æWh á«°SÉ«b äÉØ°UGƒªc ÉgOɪàYGh á«YGQõdGh á«FGò¨dG äÉéàæªdG ´É£≤H á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (56) ºbQ QGôb 71 .................................................á«æWh á«°SÉ«b äÉØ°UGƒªc ÉgOɪàYGh ¢ù«jÉ≤ªdG ´É£≤H á°UÉN á«dhO á«°SÉ«b äÉØ°UGƒe »æÑJ ¿CÉ°ûH 2017 áæ°ùd (57) ºbQ QGôb 92 ............................................... -

News Iso Standards: 2016/08
NEWS ISO STANDARDS: 2016/08 ISO 24624: 2016 165.00 € ISO 24624 Language resource management -- Transcription of spoken Buy language ISO 24678-6: 2016 141.00 € ISO 24678-6 Fire safety engineering -- Requirements governing Buy algebraic formulae -- Part 6: Flashover related phenomena ISO/IEC 29161: 2016 141.00 € ISO/IEC 29161 Information technology -- Data structure -- Unique Buy identification for the Internet of Things ISO 11031: 2016 189.00 € ISO 11031 Cranes -- Principles for seismically resistant design Buy ISO 11528: 2016 141.00 € ISO 11528 Buildings and civil engineering works -- Sealants -- Buy Determination of crazing and cracking following exposure to artificial or natural weathering ISO 7198: 2016 214.00 € ISO 7198 Cardiovascular implants and extracorporeal systems -- Buy Vascular prostheses -- Tubular vascular grafts and vascular patches ISO/IEC 30122-1: 2016 69.00 € ISO/IEC 30122-1 Information technology -- User interfaces -- Voice Buy commands -- Part 1: Framework and general guidance ISO 15858: 2016 69.00 € ISO 15858 UV-C Devices -- Safety information -- Permissible human Buy exposure ISO/TR 16203: 2016 69.00 € ISO/TR 16203 Corrosion of metals and alloys -- Guidelines for the Buy selection of methods for particle-free erosion corrosion testing in flowing liquids ISO/TR 16705: 2016 165.00 € ISO/TR 16705 Statistical methods for implementation of Six Sigma -- Buy Selected illustrations of contingency table analysis ISO 16706: 2016 69.00 € ISO 16706 Ships and marine technology -- Marine evacuation systems Buy -- Load calculations -

Optomed Oyj Jyri Leskelä Director Q&RA Yrttipellontie 1 Oulu, 90230
Optomed Oyj Jyri Leskelä Director Q&RA Yrttipellontie 1 Oulu, 90230 Finland Re: K201325 Trade/Device Name: Optomed Smartscope M5 with Optomed Smartscope FA Regulation Number: 21 CFR 886.1120 Regulation Name: Ophthalmic Camera Regulatory Class: Class II Product Code: HKI Dated: May 7, 2020 Received: May 18, 2020 Dear Jyri Leskelä: We have reviewed your Section 510(k) premarket notification of intent to market the device referenced above and have determined the device is substantially equivalent (for the indications for use stated in the enclosure) to legally marketed predicate devices marketed in interstate commerce prior to May 28, 1976, the enactment date of the Medical Device Amendments, or to devices that have been reclassified in accordance with the provisions of the Federal Food, Drug, and Cosmetic Act (Act) that do not require approval of a premarket approval application (PMA). You may, therefore, market the device, subject to the general controls provisions of the Act. Although this letter refers to your product as a device, please be aware that some cleared products may instead be combination products. The 510(k) Premarket Notification Database located at https://www.accessdata.fda.gov/scripts/cdrh/cfdocs/cfpmn/pmn.cfm identifies combination product submissions. The general controls provisions of the Act include requirements for annual registration, listing of devices, good manufacturing practice, labeling, and prohibitions against misbranding and adulteration. Please note: CDRH does not evaluate information related to contract liability warranties. We remind you, however, that device labeling must be truthful and not misleading. If your device is classified (see above) into either class II (Special Controls) or class III (PMA), it may be subject to additional controls. -

Specification Sheet
SPECIFICATION SHEET iViz is a powerful diagnostic tool all within the palm of your hand. The SonoSite iViz was designed to go with you, where you need it. With the iViz in your pocket, you will be ready to tackle those tough clinical questions, whether it be at the bedside or in the field. iViz delivers this value by combining excellent imaging performance, ultra-mobility and ergonomic one-handed operation. GENERAL SPECIFICATIONS STORAGE System Weight: 570 g (includes battery in system) 64 GB internal flash memory storage (potential to store 250,000 images or 4,000 4-second clips) Screen Size: 7"/17.8 cm high-resolution display dual Clip store capability (maximum single clip length: 30 seconds, touch screen prospective/ retrospective) Image Size: 1472 x 1104 pixels Cine review up to 256 frame-by-frame images MEASUREMENT TOOLS AND ANNOTATIONS Screen Resolution: 1920 x 1200 pixels Dynamic Range: Up to 170 dB 2D: Distance calipers, ellipse and manual trace M-Mode: Distance and time measurement, heart rate calculation Gray Scale: 256 shades User-selectable text labels HIPAA compliance: Comprehensive tool set User-defined, application specific annotations Multi-touch gestures Tap, Pinch and Expand, Swipe (Scroll), for system controls: Press, and Drag CONNECTIVITY (EXTERNAL DATA MANAGEMENT) System Boot up: < 35 secs Wireless Printing Operating System: Android 4.4.2 OS MicroUSB Thermal Index: TIB, TIC, TIS Bluetooth Capabilities Features: Rear and front camera SonoSite Patient Data Archival Software (PDAS) for Wireless/Wired Protective case -

NEUROTECHNOLOGIES for BRAIN-MACHINE INTERFACING IEEE SA Industry Connections Activity No
STANDARDS ROADMAP: NEUROTECHNOLOGIES FOR BRAIN-MACHINE INTERFACING IEEE SA Industry Connections Activity No. IC17-007 3 Park Avenue | New York, NY 10016-5997 | USA Trademarks and Disclaimers IEEE believes the information in this publication is accurate as of its publication date; such information is subject to change without notice. IEEE is not responsible for any inadvertent errors. The ideas and proposals in this specification are the respective author’s views and do not represent the views of the affiliated organization. The Institute of Electrical and Electronics Engineers, Inc. 3 Park Avenue, New York, NY 10016‐5997, USA Copyright © 2020 by The Institute of Electrical and Electronics Engineers, Inc. All rights reserved. Published February 2020. Printed in the United States of America. IEEE is a registered trademark in the U. S. Patent & Trademark Office, owned by The Institute of Electrical and Electronics Engineers, Incorporated. PDF: ISBN 978‐1‐5044‐6496‐3 STDVA24082 IEEE prohibits discrimination, harassment, and bullying. For more information, visit http://www.ieee.org/web/aboutus/whatis/policies/p9‐26.html. No part of this publication may be reproduced in any form, in an electronic retrieval system, or otherwise, without the prior written permission of the publisher. To order IEEE Press Publications, call 1‐800‐678‐IEEE. Find IEEE standards and standards‐related product listings at: http://standards.ieee.org ii Copyright © 2020 IEEE. All rights reserved. Notice and Disclaimer of Liability Concerning the Use of IEEE SA Industry Connections Documents This IEEE Standards Association (“IEEE SA”) Industry Connections publication (“Work”) is not a consensus standard document. Specifically, this document is NOT AN IEEE STANDARD.