Download the App [26]
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

The Development and Validation of the Game User Experience Satisfaction Scale (Guess)
THE DEVELOPMENT AND VALIDATION OF THE GAME USER EXPERIENCE SATISFACTION SCALE (GUESS) A Dissertation by Mikki Hoang Phan Master of Arts, Wichita State University, 2012 Bachelor of Arts, Wichita State University, 2008 Submitted to the Department of Psychology and the faculty of the Graduate School of Wichita State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy May 2015 © Copyright 2015 by Mikki Phan All Rights Reserved THE DEVELOPMENT AND VALIDATION OF THE GAME USER EXPERIENCE SATISFACTION SCALE (GUESS) The following faculty members have examined the final copy of this dissertation for form and content, and recommend that it be accepted in partial fulfillment of the requirements for the degree of Doctor of Philosophy with a major in Psychology. _____________________________________ Barbara S. Chaparro, Committee Chair _____________________________________ Joseph Keebler, Committee Member _____________________________________ Jibo He, Committee Member _____________________________________ Darwin Dorr, Committee Member _____________________________________ Jodie Hertzog, Committee Member Accepted for the College of Liberal Arts and Sciences _____________________________________ Ronald Matson, Dean Accepted for the Graduate School _____________________________________ Abu S. Masud, Interim Dean iii DEDICATION To my parents for their love and support, and all that they have sacrificed so that my siblings and I can have a better future iv Video games open worlds. — Jon-Paul Dyson v ACKNOWLEDGEMENTS Althea Gibson once said, “No matter what accomplishments you make, somebody helped you.” Thus, completing this long and winding Ph.D. journey would not have been possible without a village of support and help. While words could not adequately sum up how thankful I am, I would like to start off by thanking my dissertation chair and advisor, Dr. -

New York CITY
New York CITY the 123rd Annual Meeting American Historical Association NONPROFIT ORG. 400 A Street, S.E. U.S. Postage Washington, D.C. 20003-3889 PAID WALDORF, MD PERMIT No. 56 ASHGATENew History Titles from Ashgate Publishing… The Chronicle of Ibn al-Athir The Long Morning of Medieval Europe for the Crusading Period New Directions in Early Medieval Studies Edited by Jennifer R. Davis, California Institute from al-Kamil fi’l-Ta’rikh. Part 3 of Technology and Michael McCormick, The Years 589–629/1193–1231: The Ayyubids Harvard University after Saladin and the Mongol Menace Includes 25 b&w illustrations Translated by D.S. Richards, University of Oxford, UK June 2008. 366 pages. Hbk. 978-0-7546-6254-9 Crusade Texts in Translation: 17 June 2008. 344 pages. Hbk. 978-0-7546-4079-0 The Art, Science, and Technology of Medieval Travel The Portfolio of Villard de Honnecourt Edited by Robert Bork, University of Iowa (Paris, Bibliothèque nationale and Andrea Kann AVISTA Studies in the History de France, MS Fr 19093) of Medieval Technology, Science and Art: 6 A New Critical Edition and Color Facsimile Includes 23 b&w illustrations with a glossary by Stacey L. Hahn October 2008. 240 pages. Hbk. 978-0-7546-6307-2 Carl F. Barnes, Jr., Oakland University Includes 72 color and 48 b&w illustrations November 2008. 350 pages. Hbk. 978-0-7546-5102-4 The Medieval Account Books of the Mercers of London Patents, Pictures and Patronage An Edition and Translation John Day and the Tudor Book Trade Lisa Jefferson Elizabeth Evenden, Newnham College, November 2008. -

Real-Time Traveler Information Market Assessment White Paper
Real-Time Traveler Information Market Assessment White Paper Publication No.: FHWA-JPO-10-055 EDL Document No.: 14961 February 22, 2010 Submitted by: This page left intentionally blank Notice This document is disseminated under the sponsorship of the U.S. Department of Transportation in the interest of information exchange. The U.S. Government assumes no liability for the use of the information contained in this document. This report does not constitute a standard, specification, or regulation. The U.S. Government does not endorse products of manufacturers. Trademarks or manufacturers’ names appear in this report only because they are considered essential to the objective of the document. Quality Assurance Statement The U.S. Department of Transportation (DOT) provides high-quality information to serve Government, industry, and the public in a manner that promotes public understanding. Standards and policies are used to ensure and maximize the quality, objectivity, utility, and integrity of its information. The US DOT periodically reviews quality issues and adjusts its programs and processes to ensure continuous quality improvement. Acknowledgements Interviews were conducted with industry experts, with each focused on one of the four traveler information modes—traffic, transit, parking, and intermodal/freight. The Intelligent Transportation System (ITS) Joint Program Office (JPO) thanks the following experts with whom interviews were conducted: Traffic Name Organization Cy Smith AirSage Matt Wright AirSage Greg Larson California Department -

Mobile LBS: Status Update & Platform Assessment
Wireless Media Mobile LBS: Status Update & Platform Assessment Wireless Media Strategies (WMS) Report Snapshot This report provides Strategy Analytics’ high-level outlook for handset-based location-based services. Rising GPS penetration, the growing popularity of taxi- sharing, carpooling, and ride-sharing apps, third-party content integration into popular map applications, and the emerging wearables device category provide opportunities for growth and development in mobile LBS. This report also includes an update of our assessment of global location-platform leaders, HERE, Google, TomTom and Apple. November 2016 Nitesh Patel +441908423621 Tel: Email: [email protected] www.strategyanalytics.com Wireless Media Contents 1. Executive Summary 3 2. Key Trends in Mobile LBS 4 2.1 Reported Mobile LBS Use and Adoption 5 2.2 Mobile Maps & Direction Use in Context 6 2.3 Mobile Location Capability to Boost Emerging Market Opportunities 9 2.3.1 GPS handset penetration rises in the entry tier 9 2.4 New Trends in Urban Mobility 10 2.5 From Maps & Navigation to All-in-One Travel Planning Apps 11 2.6 Wearables Remain a Growth Opportunity 13 3. Location Platform Benchmark Update 16 3.1 Overall Assessment 21 Exhibits Exhibit 1: Overall Mobile Map & Directions Use in Context: Asia, Europe, and the US ............................................... 6 Exhibit 2: Regular Mobile Map & Directions Use in Context: Asia, Europe, and the US .............................................. 8 Exhibit 3: Mobile Map & Directions Use across All Countries ...................................................................................... 8 Exhibit 4 Rising Penetration of GPS Handsets by Price Tier ...................................................................................... 10 Exhibit 5 Global Wearable Device Sales by Type ...................................................................................................... 14 Exhibit 6 The Relative Strengths & Weaknesses of Major Location Platforms .......................................................... -

It Spot Issue
[ Spot❘2016-06 ] 2016 ICT Spot Issue Ⅰ. 브렉시트 선언과 ICT산업 영향 Ⅱ. 스마트폰 카메라의 진화, 3D카메라 <CP Issue> IMS2016을 통해 살펴보는 전파기술의 최신 동향 목 차 ICT SPOT ISSUE 2016-06 Ⅰ. 브렉시트 선언과 ICT산업 영향 ································· 1 1. Brexit 발표 후 경제 지표 변화 ································································· 2 2. 미국 금융위기 사례를 통한 Brexit 영향 검토 ··········································· 5 3. Brexit의 ICT산업 파급효과 ········································································· 6 4. 정책적 시사점 ··························································································· 11 Ⅱ. 스마트폰 카메라의 진화, 3D카메라 ························ 12 1. 3D로 진화하는 스마트폰 카메라 ··························································· 13 2. 스마트폰용 3D 카메라 기술 개요 및 개발 동향 ···································· 15 3. 맺음말 ······································································································· 23 <CP Issue> IMS2016을 통해 살펴보는 전파기술의 최신 동향 1. IMS2016 개요 ························································································ 26 2. 이동전화: 탄생과 소멸 ············································································· 31 3. mm-Wave: 미래로 연결되는 관문 ·························································· 35 4. GaN: 고전력 반도체 혁신 ······································································ 41 5. 패러다임 이동: SW기반 플랫폼 ······························································· 47 6. 시사점과 제언 ··························································································· -

GAMING GLOBAL a Report for British Council Nick Webber and Paul Long with Assistance from Oliver Williams and Jerome Turner
GAMING GLOBAL A report for British Council Nick Webber and Paul Long with assistance from Oliver Williams and Jerome Turner I Executive Summary The Gaming Global report explores the games environment in: five EU countries, • Finland • France • Germany • Poland • UK three non-EU countries, • Brazil • Russia • Republic of Korea and one non-European region. • East Asia It takes a culturally-focused approach, offers examples of innovative work, and makes the case for British Council’s engagement with the games sector, both as an entertainment and leisure sector, and as a culturally-productive contributor to the arts. What does the international landscape for gaming look like? In economic terms, the international video games market was worth approximately $75.5 billion in 2013, and will grow to almost $103 billion by 2017. In the UK video games are the most valuable purchased entertainment market, outstripping cinema, recorded music and DVDs. UK developers make a significant contribution in many formats and spaces, as do developers across the EU. Beyond the EU, there are established industries in a number of countries (notably Japan, Korea, Australia, New Zealand) who access international markets, with new entrants such as China and Brazil moving in that direction. Video games are almost always categorised as part of the creative economy, situating them within the scope of investment and promotion by a number of governments. Many countries draw on UK models of policy, although different countries take games either more or less seriously in terms of their cultural significance. The games industry tends to receive innovation funding, with money available through focused programmes. -

Purchase Intent Predicts Stock Performance
Purchase Intent Predicts Stock Performance LikeFolio Purchase Intent Strategies Performance Report EDITION: APRIL 2018 TABLE OF CONTENTS LIKEFOLIO OVERVIEW ........................................................................................................... 1 PURCHASE INTENT (PI) METRIC & SIGNAL CALCULATION .................................................... 2 Purchase Intent (PI) Metric Definition & Examples ........................................................................ 2 Purchase Intent Signal Calculation .................................................................................................. 3 TRADING STRATEGIES UTILIZING LIKEFOLIO PI SIGNAL ....................................................... 4 Earnings Trading Strategy ................................................................................................................ 5 Active Trading Strategies ................................................................................................................. 6 Portfolio Strategy – Top-8 Long vs Bottom-8 Short ..................................................................... 12 Combined Portfolio ......................................................................................................................... 13 SUMMARY .......................................................................................................................... 15 CONTACT INFORMATION .................................................................................................... 16 LEGAL DISCLAIMERS.......................................................................................................... -

Game Developer Power 50 the Binding November 2012 of Isaac
THE LEADING GAME INDUSTRY MAGAZINE VOL19 NO 11 NOVEMBER 2012 INSIDE: GAME DEVELOPER POWER 50 THE BINDING NOVEMBER 2012 OF ISAAC www.unrealengine.com real Matinee extensively for Lost Planet 3. many inspirations from visionary directors Spark Unlimited Explores Sophos said these tools empower level de- such as Ridley Scott and John Carpenter. Lost Planet 3 with signers, artist, animators and sound design- Using UE3’s volumetric lighting capabilities ers to quickly prototype, iterate and polish of the engine, Spark was able to more effec- Unreal Engine 3 gameplay scenarios and cinematics. With tively create the moody atmosphere and light- multiple departments being comfortable with ing schemes to help create a sci-fi world that Capcom has enlisted Los Angeles developer Kismet and Matinee, engineers and design- shows as nicely as the reference it draws upon. Spark Unlimited to continue the adventures ers are no longer the bottleneck when it “Even though it takes place in the future, in the world of E.D.N. III. Lost Planet 3 is a comes to implementing assets, which fa- we defi nitely took a lot of inspiration from the prequel to the original game, offering fans of cilitates rapid development and leads to a Old West frontier,” said Sophos. “We also the franchise a very different experience in higher level of polish across the entire game. wanted a lived-in, retro-vibe, so high-tech the harsh, icy conditions of the unforgiving Sophos said the communication between hardware took a backseat to improvised planet. The game combines on-foot third-per- Spark and Epic has been great in its ongoing weapons and real-world fi rearms. -

Google Cheat Sheet
Way Cool Apps Your Guide to the Best Apps for Your Smart Phone and Tablet Compiled by James Spellos President, Meeting U. [email protected] http://www.meeting-u.com twitter.com/jspellos scoop.it/way-cool-tools facebook.com/meetingu last updated: November 15, 2016 www.meeting-u.com..... [email protected] Page 1 of 19 App Description Platform(s) Price* 3DBin Photo app for iPhone that lets users take multiple pictures iPhone Free to create a 3D image Advanced Task Allows user to turn off apps not in use. More essential with Android Free Killer smart phones. Allo Google’s texting tool for individuals and groups...both Android, iOS Free parties need to have Allo for full functionality. Angry Birds So you haven’t played it yet? Really? Android, iOS Freemium Animoto Create quick, easy videos with music using pictures from iPad, iPhone Freemium - your mobile device’s camera. $5/month & up Any.do Simple yet efficient task manager. Syncs with Google Android Free Tasks. AppsGoneFree Apps which offers selection of free (and often useful) apps iPhone, iPad Free daily. Most of these apps typically are not free, but become free when highlighted by this service. AroundMe Local services app allowing user to find what is in the Android, iOS Free vicinity of where they are currently located. Audio Note Note taking app that syncs live recording with your note Android, iOS $4.99 taking. Aurasma Augmented reality app, overlaying created content onto an Android, iOS Free image Award Wallet Cloud based service allowing user to update and monitor all Android, iPhone Free reward program points. -
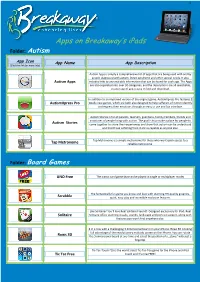
Apps on Breakaway's Ipads
1 Apps on Breakaway’s iPads Folder: Autism App Icon App Name App Description (Click the link for more info) Autism Apps is simply a comprehensive list of apps that are being used with and by people diagnosed with autism, Down syndrome and other special needs. It also Autism Apps includes links to any available information that can be found for each app. The Apps are also separated into over 30 categories, and the descriptions are all searchable, so any type of app is easy to find and download. In addition to an improved version of the original game, AutismXpress Pro features 2 AutismXpress Pro totally new games, which are both also designed to help sufferers of Autism identify and express their emotions through an easy to use and fun interface. Autism Stories is for all parents, teachers, guardians, family members, friends and associates of people living with autism. The goal is to provide a place for people to Autism Stories come together to share their experiences and show that autism can be understood and that those suffering from it are as capable as anyone else. Tap Metronome is a simple metronome for those who want quick access to a Tap Metronome reliable metronome. Folder: Board Games UNO Free The classic card game that can be played in single or multiplayer modes The fantastically fun game you know and love with stunning HD-quality graphics, Scrabble quick, easy play and incredible exclusive features. Like Solitaire? You'll love Real Solitaire Free HD. Designed exclusively for iPad, Real Solitaire Solitaire offers stunning visuals, sounds, landscape and portrait support, along with features you won't find anywhere else. -

Head Into Battle with Angry Birds Epic – out Now Worldwide!
Head into battle with Angry Birds Epic – out now worldwide! Rovio’s epic role-playing game set to take over the world across multiple platforms. Espoo, Finland -- June 12th 2014 -- Today marks the global launch of Angry Birds Epic, Rovio’s first role-playing game featuring the iconic Angry Birds characters as legendary heroes. In this epic adventure, players get to explore a fantasy version of Piggy Island full of mysterious caves, tropical beaches, frosty mountains and loads of other exciting locations. Can our feathered heroes topple King Pig, Wiz Pig and Prince Porky to save their eggs from being scrambled? In Angry Birds Epic, players get to transform the birds into truly legendary adventurers. They can craft weird and wacky weapons, upgrade characters, armor and potions, all while wearing some pretty silly hats. The rich crafting system, gripping campaign and challenging endgame offer buckets of fun for both casual gamers and die-hard RPG fans. “The Angry Birds characters are a perfect fit for a role-playing game because they have strong personalities and individual superpowers. They are almost like character classes from the get go”, said Jami Laes, Executive Vice President of Games, Rovio Entertainment. “Angry Birds Epic isn’t straight-up fantasy, but we have kept that weird and surprising Rovio humor in there. Get ready to head into battle with some pretty wacky equipment and powers under your belt!” Angry Birds Epic is a free-to-play game and was soft launched in Canada, Australia, New Zealand and Singapore earlier this year. The game is free and it can be downloaded from Apple App Store, Google Play, Windows Phone Store and Amazon AppStore. -

Recreation, Sports, and Leisure
Recreation, Sports, and Leisure Name of App Platform Description Angry Birds 2 IOS Use the slingshot to fling birds at the piggies' towers and bring them crashing down to save the precious eggs. Choose which bird to fling when, play with friends, take on multi stage levels, and compete and collaborate with players around the globe. Clips iOS Clips is a free app for making fun videos to share with friends and family. With a few taps you can create and send a video message or tell a quick story with artistic filters, animated text, music, emoji, and fun stickers featuring characters from Star Wars, Disney•Pixar and more. Colorful - Calm Coloring Book IOS The only coloring book where you make relaxing music while you color. Plenty of FREE content to enjoy: free daily image and a free image in each category Disney Crossy Road iOS DISNEY CROSSY ROAD is an arcade game that will remind older gamers of the classic Frogger and put Disney's library of characters into a totally new world Disney Frozen Free Fall Game iOS Play 1,000+ exciting levels in Disney's amazing puzzle game, Frozen Free Fall! ... Join Anna, Elsa, Olaf and more of your favorite characters on a puzzle journey to slide and match-3 hundreds of icy puzzles Disney Junior Appisodes iOS The Disney Junior Appisodes app allows preschoolers to experience the magic of watching, playing and interacting directly with their favorite Disney Junior TV shows in a whole new way! ... Mickey Mouse Clubhouse Appisodes featuring "Quest for the Cyrstal Mickey" & "Mickey and Donald Have a Farm" episodes.