Data Communications & Networks Session 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
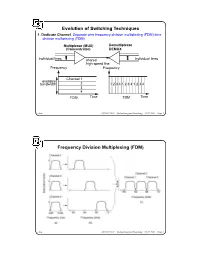
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

Mapping Networks and Services Proc
Mapping Networks and Services Proc. INET ´93 J.S. Quarterman Mapping Networks and Services John S. Quarterman1 Smoot Carl-Mitchell2 Gretchen Phillips3 Abstract I . Introduction Four global networks carry most of the Computer networking is widespread, supported by international network traffic; FidoNet, UUCP, the global Matrix of interconnected computer BITNET, and the Internet. The first step in networks such as the Internet, BITNET, UUCP, looking at these networks involves collecting and FidoNet. Perhaps 20,000,000 people use this appropriate data for each and performing some global Matrix of computer networks, and several consistency checking. The data for these maps major global computer networks are growing was initially derived from their node lists exponentially, rapidly reaching new countries and (BITNET and FidoNet) or host lists (UUCP). The new classes of users. This growth prompts Internet data came from a domain walk by Mark network users and service providers to ask Lottor. questions like: The data available from the node lists, public d Where are these users? maps and the domain walk is not in a format that d What is the magnitude of the various network is readily usable for this type of mapping. Each communities? map or other source of network information tends d What are the available services? to include different details. We have correlated the d How are services distributed? data by using telephone country codes, area codes d And, finally, how can this data be represented and local exchanges for determining locations. A in a meaningful graphical way? more complete discussion of the methods is We have chosen Latin America and the Caribbean available in issues of Matrix News[5-7] (ALyC) as the geographic region for discussing these issues and demonstrating the mapping of II . -

Net Neutrality Reloaded
Luca Belli Editor Net Neutrality Reloaded: Net Neutrality Reloaded: Zero Rating, Specialised Service, Ad Blocking and Traffic Management Zero Rating, Specialised Service, Annual Report of the UN IGF Dynamic Coalition on Net Neutrality Ad Blocking and Traffic Management Luca Belli Editor Annual Report of the UN IGF This Report is the 2016 outcome of the IGF Dynamic Coalition on Network Neutrality (DCNN). The Report gathers a series of case studies on a variety Dynamic Coalition of net neutrality issues from the perspective of different stakeholders. The double purpose of this report is to trigger meaningful discussion on net on Net Neutrality neutrality trends, while providing informative material that may be used by researchers, policy-makers and civil society alike. Researchers, practitioners and policy-makers regularly contribute to the DCNN report, providing a wide range of heterogeneous views. Preface by Tim Wu In 2016, Zero Rating was by large the most debated net neutrality issue, as reflected by the considerable number of contributions focusing on the topic within this report. Such high number of analyses on zero rating seems particularly useful to meet the increasing demand of research exploring the pros and cons of price discrimination practices. Furthermore, the report examines other very relevant and discussed topics, such as specialised services, ad blocking and reasonable traffic management, providing useful insight on some of the most recent policy evolutions in a variety of countries. Net Neutrality Reloaded: Zero Rating, -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz-Allen-Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

Research on the System Structure of IPV9 Based on TCP/IP/M
International Journal of Advanced Network, Monitoring and Controls Volume 04, No.03, 2019 Research on the System Structure of IPV9 Based on TCP/IP/M Wang Jianguo Xie Jianping 1. State and Provincial Joint Engineering Lab. of 1. Chinese Decimal Network Working Group Advanced Network, Monitoring and Control Shanghai, China 2. Xi'an, China Shanghai Decimal System Network Information 2. School of Computer Science and Engineering Technology Ltd. Xi'an Technological University e-mail: [email protected] Xi'an, China e-mail: [email protected] Wang Zhongsheng Zhong Wei 1. School of Computer Science and Engineering 1. Chinese Decimal Network Working Group Xi'an Technological University Shanghai, China Xi'an, China 2. Shanghai Decimal System Network Information 2. State and Provincial Joint Engineering Lab. of Technology Ltd. Advanced Network, Monitoring and Control e-mail: [email protected] Xi'an, China e-mail: [email protected] Abstract—Network system structure is the basis of network theory, which requires the establishment of a link before data communication. The design of network model can change the transmission and the withdrawal of the link after the network structure from the root, solve the deficiency of the transmission is completed. It solves the problem of original network system, and meet the new demand of the high-quality real-time media communication caused by the future network. TCP/IP as the core network technology is integration of three networks (communication network, successful, it has shortcomings but is a reasonable existence, broadcasting network and Internet) from the underlying will continue to play a role. Considering the compatibility with structure of the network, realizes the long-distance and the original network, the new network model needs to be large-traffic data transmission of the future network, and lays compatible with the existing TCP/IP four-layer model, at the a solid foundation for the digital currency and virtual same time; it can provide a better technical system to currency of the Internet. -
Circuit-Switched Coherence
Circuit-Switched Coherence ‡Natalie Enright Jerger, ‡Mikko Lipasti, and ?Li-Shiuan Peh ‡Electrical and Computer Engineering Department, University of Wisconsin-Madison ?Department of Electrical Engineering, Princeton University Abstract—Circuit-switched networks can significantly lower contention, overall system performance can degrade by 20% the communication latency between processor cores, when or more. This latency sensitivity coupled with low link uti- compared to packet-switched networks, since once circuits are set up, communication latency approaches pure intercon- lization motivates our exploration of circuit-switched fabrics nect delay. However, if circuits are not frequently reused, the for CMPs. long set up time and poorer interconnect utilization can hurt Our investigations show that traditional circuit-switched overall performance. To combat this problem, we propose a hybrid router design which intermingles packet-switched networks do not perform well, as circuits are not reused suf- flits with circuit-switched flits. Additionally, we co-design a ficiently to amortize circuit setup delay. This observation prediction-based coherence protocol that leverages the exis- motivates a network with a hybrid router design that sup- tence of circuits to optimize pair-wise sharing between cores. The protocol allows pair-wise sharers to communicate di- ports both circuit and packet switching with very fast circuit rectly with each other via circuits and drives up circuit reuse. reconfiguration (setup/teardown). Our preliminary results Circuit-switched coherence provides overall system perfor- show this leading to up to 8% improvement in overall system mance improvements of up to 17% with an average improve- performance over a packet-switched fabric. ment of 10% and reduces network latency by up to 30%. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Multimedia, Internet, On-Line
Section IV: Multimedia, the Internet, and On-Line Services High-End Digital Video Applications Larry Amiot Electronic and Computing Technologies Division Argonne National Laboratory The emphasis of this paper is on the high-end applications Internet and Intranet that are driving digital video. The research with which I am involved at Argonne National Laboratory is not done on dig- The packet video networks which currently support many ital video per se, but rather on how the research applications applications such as file transfer, Mbone video (talking at the laboratory drive its requirements for digital video. The heads), and World Wide Web browsing are limiting for high- paper will define what digital video is, what some of its com- quality video because of the low throughput one can achieve ponents are, and then discuss a few applications that are dri- via the Internet or intranets. Examples of national packet ving the development of these components. The focus will be switched networks developed in the last several years include on what digital video means to individuals in the research the National Science Foundation Network (NSFNet). The and education community. Department of Energy had its own network called ESNET, and the National Aeronautics and Space Administration The Digital Video Environment (NASA) had a network as well. Recently, the NSFNet was de- commissioned, and commercial interests are now starting to In 1996, a group of people from several universities in the fill that void. Research and education communities are find- Midwest and from Argonne formed a Video Working Group. ing, however, that this new commercial Internet is too re- This body tried to define the areas of digital video of impor- stricting and does not meet their throughput requirements; it tance to their institutions. -

F. Circuit Switching
CSE 3461: Introduction to Computer Networking and Internet Technologies Circuit Switching Presentation F Study: 10.1, 10.2, 8 .1, 8.2 (without SONET/SDH), 8.4 10-02-2012 A Closer Look At Network Structure: • network edge: applications and hosts • network core: —routers —network of networks • access networks, physical media: communication links d. xuan 2 1 The Network Core • mesh of interconnected routers • the fundamental question: how is data transferred through net? —circuit switching: dedicated circuit per call: telephone net —packet-switching: data sent thru net in discrete “chunks” d. xuan 3 Network Layer Functions • transport packet from sending to receiving hosts application transport • network layer protocols in network data link network physical every host, router network data link network data link physical data link three important functions: physical physical network data link • path determination: route physical network data link taken by packets from source physical to dest. Routing algorithms network network data link • switching: move packets from data link physical physical router’s input to appropriate network data link application router output physical transport network data link • call setup: some network physical architectures require router call setup along path before data flows d. xuan 4 2 Network Core: Circuit Switching End-end resources reserved for “call” • link bandwidth, switch capacity • dedicated resources: no sharing • circuit-like (guaranteed) performance • call setup required d. xuan 5 Circuit Switching • Dedicated communication path between two stations • Three phases — Establish (set up connection) — Data Transfer — Disconnect • Must have switching capacity and channel capacity to establish connection • Must have intelligence to work out routing • Inefficient — Channel capacity dedicated for duration of connection — If no data, capacity wasted • Set up (connection) takes time • Once connected, transfer is transparent • Developed for voice traffic (phone) g. -

STUDENT INTERACTION with MINITEL TELECOMMUNICATIONS Joann Hammadou University of Rhode Island
STUDENT INTERACTION WITH MINITEL TELECOMMUNICATIONS JoAnn Hammadou University of Rhode Island The Promise of Telecommunications of how to carry on multilevels of instruction Telecommunications seem to offer an simultaneously. This option may improve ideal solution to several thorny educational the teacher's ability to provide tasks for problems: (1) how to provide up-to-date students at one level of proficiency that will cultural info171Ultion to students when the continue to move them forward while teacher'sownculturalinformationmaydate teacher-centered work continues with an to much earlier personal trips abroad, (2) other group. For example, telecommunica how to provide up-to-date foreign language tions from a computer workstation have informationinspecializedareas outside of the been used to correspond with native speak teacher's realm of personal experience (e.g., ers abroad, to generate authentic reading nursing, business or engineering), and (3) texts· on up-to-the minute news topics, to howtoprovidestudentsin the United States research specialized topics (such as busi with authentic contexts in which to develop ness, science or education), to simulate buy their fledgling language skills. Telecom ing and selling or to actually order goods munications may, therefore, help provide from abroad, and to serve as an example of experiences and information to students that technology in daily life in Europe. are otherwise difficult to obtain. These calls for the use of telecommuni Telecommunications might also be one cations are subsumed under the larger call solution to a logistics nighbnare that teach to educators to incorporate the use of tech ers often face. With a 1982 survey, Brickel nology in education. -

How Special Librarians Really Use the Internet: Summary of Findings and Implications for the Library of the Future
DOCUILIff RESUME ED 345 751 IR 054 097 AUTHOR Ladner, Sharyn J.; Tillman, Hope N. TITLE How Special Librarians Really Use the Internet: Summary of Findings and Implications for the Library of the Future. PUB DATE 29 Nar 92 NOTE 12p.; "This report was posted on March 29, 1992, to nine computer conferences where call for participation announcements had been posted in the summer of 1991: BUSLIB-L, LIBREF-L, LIfflES, NEDLIB-L, PACS-L, LAW-LIB, LIBADMIN, MAPS-L, and PANnet." AVAILABLE FROM Internet, through anonymous file transfer protocol (ftp), using the following location (hydra.uwo.ca), directory (LibSoft), and filename (SPEC underscore Libs.txt). PUB TYPE Reports - Research/Technical (143) EDRS PRICE NF01/PC01 Plus Postage. DESCRIPTORS Access to Information; *Computer Networks; Databases; *Electronic Rail; Electronic Publishing; Information Networks; *Librarians; Library Surveys; Online Searching; Online Systems; *Special Libraries; Telecommunications; Teleconferencing; User Needs (Information); *Use Studies IDENTIFIERS BITNET; *INTERNET ABSTRACT A five-page electronic questionnaire was sent to 113 special librarians who responded to "Call for Participation" announcements posted on nine computer conferences in July 1991 and a similar announcement in the August 1991 issue of the monthly newsletter of the Special Libraries Association. Fifty-four librarians completed the questionnaire, which sought information on the computer conferences to which they subscribed; the length of time they had been using either BITNET or the Internet; and the type of training they had had in using either of the two networks. In addition, the respondents were asked to rank five functions or capabilities available on either BITNET or Internet--electronic mail and computer forums, remote database searching, file transiur and data exchange, research and publication on the Internet--by extent of use.