Best Practices in Information Governance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Micro Focus Retain Social
Micro Focus Retain Social www.microfocus.com/products/retain-social-archiving What Does It Do? Micro Focus® Retain™ Social provides archiving, monitoring, and data insights. This enables organizations to perform eDiscovery, review messages in context, and help determine the tone of all posts and pictures for Facebook, Twitter, LinkedIn, Instagram, Flickr, Pinterest, and Google+. Plus, you get archiving for all YouTube and Vimeo videos and comments. Retain Social ensures that your social media communication data is compliant with archiving regulations. Retain Social archives all Facebook, Twitter, YouTube, LinkedIn, Instagram, Flickr, Vimeo, Pinterest and Google+ posts into one central repository. The entire social media history is captured in its original context, allowing you to see message threads, view photos, and watch videos as they originally appeared. Retain Social provides configurable rules that allow you to control the retention period of archived data. This solution gives you immediate and complete access to all your company social media communication data. Search, perform eDiscovery, and export social media communication data from the central archive, along with your employees’ email, and mobile message data. Social Media Search Results in Retain Top Business Drivers 1 2 3 4 5 Need to easily and affordably Need to ensure compliance with Need to reduce costs and liability if Need to perform eDiscovery on Need oversight on company social archive social media data strict industry regulations social media is involved in litigation social media communication data media postings from one central location Micro Focus Retain Social www.microfocus.com/products/retain-social-archiving Customer Profile for a Good Opportunity Primary Competitors Organizations using social media and those involved in the Smarsh Actiance decision making process: IT Manager, Director of IT, and CIO. -

Unified Security Gateway™ 5.1 Release Notes
Unified Security Gateway ™ 5.1 Release Notes September, 2012 This document contains information on the new features in this release and Known Issues and Limitations, and supplements the documentation included with the product. For the most recent updates to this information, please refer to the latest USG Release Notes located at the following download site: https://members.actiance.com Contents What’s New in USG 5.1 Key Features in USG 5.0.4 Key Features in USG 5.0.3 QFE Key Features in USG 5.0.2 Key Features in USG 5.0.1 Key Features in USG 5.0 Key Features in USG 4.2 Key Features in USG 4.1.1 SP Key Features in USG 4.1.1 Key Features in USG 4.1 Key Features in USG 4.0 Support Issues Fixed in USG 5.1 Support Issues Fixed in USG 5.0.4 Support Issues Fixed in USG 5.0.3 Support Issues Fixed in USG 5.0 Support Issues Fixed in USG 4.2 Support Issues Fixed in USG 4.1.1 SP Support Issues Fixed in USG 4.0 Known Issues and Limitations Actiance Proprietary and Confidential Page 1 of 42 Unified Security Gateway Release Notes What’s New in USG 5.1 Release Date: September, 2012 Transcripts cleanup: Consistency in the rendering the transcript format. IIROC template: Out of the box IIROC policy template for compliance. New role: A new role, AdminLite, is available for accessing the Configuration tab. Transcript export options: SFTP support for exporting transcripts. Enhancement: WebProxy certificate upload/download enhancement in a cluster setup Key Features in USG 5.0.4 Release Date: July, 2012 Direct support upgrade from USG 5.0 9071 to USG 5.0.4 New Features: ° Administrative Roles download CSV ° Audit logs ° Password Policy ° Upstream Proxy support Socialite Enable Merges: ° Access to Unauthorized User Report for Reporter, Group reporter, System Administrator Roles: Reporter role now has visibility to all reports including the reports that are currently visible under Configurations tab. -
Passport to Business Solutions 2015 FINRA Advertising Regulation Conference
Passport to Business Solutions 2015 FINRA Advertising Regulation Conference Visit all 10 exhibitors… Yeah? …and receive a gift! How to Use Your Passport Bring the passport with you when visiting the exhibitors in the 1. Grand Ballroom Foyer. Collect stamps from each exhibitor 2. you visit. Submit the last page with all stamps at the conference 3. registration desk. Receive 4.a special gift. Disclaimer: Use of any products, services and/or materials offered by these exhibitors does not ensure compliance regulatory requirements or create a safe harbor from regulatory responsibility. FINRA does not endorse these exhibitors or the products, services and/or materials they offer, and firms are not obligated to use them. Actiance www.actiance.com Actiance is a leader in communications compliance, archiving and analytics. We provide compliance across the broadest set of communications and social channels with insights on what’s being captured. Actiance customers manage over 500 million daily conversations across 70 channels and growing. Customers include the top 10 U.S., top 5 Canadian, top 8 European and top 3 Asian banks. The Actiance advantage is customers stay ahead of compliance and uncover patterns and relationships hidden within their data. Docupace Technologies www.docupace.com Docupace Technologies is the premier provider of secure, compliant electronic processing, and cyber security solutions for financial services firms and their advisors. The company created and implemented the industry’s first Web-based, SEC/FINRA compliant Straight-thru-Processing (STP) platform. Driven by increased levels of competition, privacy issues, document protection and government regulation, industry-leading firms are adopting the company’s solutions in order to sustain profitability and audit- risk assurance. -

Techclub Collaboration
TechClub Collaboration Jaroslav Martan [email protected] Agenda • Cisco – Microsoft Interoperability • Cisco video device in MS Teams conference • Cisco plugins for MS Teams • Webex Teams Security • Compliance & DLP • Anti-malware • Hybrid Data Security Cisco + Microsoft Creating better experiences, together. © 2020 Cisco and/or its affiliates. All rights reserved. Cisco Public Client vs. Workload choice Email & Video calendar meetings Meetings Using Microsoft Teams as a client does not prevent the use Office of Cisco for multiple workloads: productivity • Video endpoints (Webex Rooms) • Meetings (Webex Meetings) Calling • Calling (on prem & cloud options) File Workload integrations based storage on Microsoft supported APIs Team Video collaboration devices Devices © 2020 Cisco and/or its affiliates. All rights reserved. Cisco Public Video Integration for Microsoft Teams Cisco + Microsoft Partnership for Meetings Cisco will be a certified 1 Microsoft CVI partner Cisco and Microsoft Microsoft Teams will work have come together 2 with Cisco Webex Rooms via to deliver a better user modern web technologies experience © 2020 Cisco and/or its affiliates. All rights reserved. Cisco Public Video endpoints joining Microsoft Teams meetings SIP-capable video endpoints can join Microsoft Teams meetings (hosted by my company) via CVI Cloud Gateway Richer, seamless meeting experience, without requiring 3rd party interop Cisco Webex web-engine capable devices* can join B2B Microsoft Teams meetings Limited experience on Cisco devices using Microsoft Teams meeting web app *Must be cloud registered or cloud aware © 2020 Cisco and/or its affiliates. All rights reserved. Cisco Public Video Integration for Microsoft Teams Microsoft Cloud Video Interop Joining Microsoft Teams meetings – CVI gateway One Button to Push experience © 2020 Cisco and/or its affiliates. -

Actiance Supervision
Actiance Supervision Identify risk faster and more eectively Financial Services firms connect with clients over a variety of channels such as IM, chat, LinkedIn, Symphony, Slack, and Microsoft Skype for Business. However, many still rely Key Features on outdated supervisory review tools that were designed solely for email. This results in longer review queues, higher Expressive policies to reduce false positives false positive rates, and less time devoted to resolving real compliance issues. Collaborative workspace for Google-like review experience Actiance Supervision provides: Intelligent Circuit Breakers to manage review volume · TrueComplianceTM (full binary, near-native form) capture of Self-service, customizable reporting and analytics 80+ communications channels, while preserving full con- dashboards versational context · Moderated supervisory pre-review of Facebook, LinkedIn, Twitter, and enterprise social networks · High-speed search and filtering of full conversational snapshots across all communications channels · Random sampling and lexicon-based supervision of policies defined globally or by network, location, group, or user · Reduced false positive rates through expressive policies that can be applied globally or uniquely to each communications channel To learn more, contact an account executive at (888) 349-3223 or at [email protected] www.actiance.com Actiance Supervision: Identify Risk Faster and more Eectively “Actiance is well-suited for enterprises with the most complex regulatory challenges” - Gartner Enterprise Archiving -

Cloud Archiving for Dummies® Actiance Special Edition
These materials are © 2015 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Cloud Archiving For Dummies Actiance Special Edition By Bill Tolson with David Seidl, Scott Whitney, and Trevor Starr These materials are © 2015 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Cloud Archiving For Dummies®, Actiance Special Edition Published by John Wiley & Sons, Inc. 111 River St. Hoboken, NJ 07030‐5774 www.wiley.com Copyright © 2015 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748‐6011, fax (201) 748‐6008, or online at http://www.wiley.com/go/permissions. Trademarks: Wiley, For Dummies, the Dummies Man logo, The Dummies Way, Dummies.com, Making Everything Easier, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc., and/or its affiliates in the United States and other countries, and may not be used without written permission. Actiance and the Actiance logo are trademarks or registered trademarks of Actiance, Inc. All other trademarks are the property of their respective owners. John Wiley & Sons, Inc., is not associated with any product or vendor mentioned in this book. -

(12) United States Patent (10) Patent No.: US 8.484.338 B2 Paster (45) Date of Patent: Jul
USOO8484.338B2 (12) United States Patent (10) Patent No.: US 8.484.338 B2 Paster (45) Date of Patent: Jul. 9, 2013 (54) APPLICATION DETECTION 2005/0010765 A1 1/2005 Swander et al. ARCHITECTURE AND TECHNIOUES 2005, 0193429 A1 9/2005 Demopoulos et al. 2005/025 1856 Al 1 1/2005 Araujo et al. 2007/0071015 A1 3/2007 Wang et al. (75) Inventor: Steven B. Paster, San Carlos, CA (US) 2007/0220064 A1 9/2007 Najork 2007,0299777 A1 12/2007 Shraim et al. (73) Assignee: Actiance, Inc., Belmont, CA (US) 2008/0034073 A1 2/2008 McCloy et al. 2008, OO82662 A1 4/2008 Dandliker et al. (*) Notice: Subject to any disclaimer, the term of this 3.s: A. 2. Wikman et al. past S.listed under 35 2008/0196085 A1 8/2008 Nagoya et al. .S.C. 154(b) by 806 days. 2009,0006592 A1 1/2009 Carter ........................... 709,223 2009 OO64330 A1 3/2009 Shraim et al. (21) Appl. No.: 12/568,073 2009/0070872 A1 3/2009 Cowings et al. 2009 OO77648 A1 3, 2009 Swander et al. (22) Filed: Sep. 28, 2009 2009.0109845 A1 4/2009 Andreasen et al. ........... 370,230 O O OTHER PUBLICATIONS (65) Prior Publication Data Genova, Z., and Christensen, K.J., “Using signatures to improve US 201O/OO85883 A1 Apr. 8, 2010 URL routing.” Performance, Computing, and Communications Con Relatedelated U.S. Application DatUata ference, 21st IEEE International, 2002, pp. 45-52. (60) Provisional application No. 61/102.343, filed on Oct. Primary Examiner — Thomas Dailey 2, 2008. Assistant Examiner — Ebrahim Golabbakhsh (74) Attorney, Agent, or Firm — Kilpatrick Townsend & (51) Int. -

10 Software and Cloud Services Providers to Consider for Your GDPR Compliance Needs
MARKET PERSPECTIVE 10 Software and Cloud Services Providers to Consider for Your GDPR Compliance Needs Andrew Smith Angela Gelnaw Carla Arend Duncan Brown Archana Venkatraman EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: GDPR Regulations Create New Opportunity Source: IDC, 2017 August 2017, IDC #US42277417 NEW MARKET DEVELOPMENTS AND DYNAMICS GDPR Accelerates Storage, Compliance, and Security Modernization GDPR enforcement begins May 25, 2018. The EU-wide regulation streamlines many of the complex local and regional regulations already in place and updates the laws around data collection and security to be more applicable and relevant to modern businesses using a range of cloud, mobile, and social technologies. From all the GDPR articles, IDC has distilled four major implications for organizations processing the personal data of EU-located data subjects: . Heftier noncompliance fines. The fine for noncompliance has been set at a maximum of €20 million or 4% of global revenue (whichever is higher). This takes noncompliance of personal data protection into anti-bribery and anti-money-laundering levels, making data protection a boardroom issue, not an IT issue. Mandatory notification of breach. Mandatory breach notification rules (common in the United States and other countries) are now introduced to the EU. A company must notify relevant authorities within 72 hours of discovering a breach and affected data subjects "without undue delay." This presents two challenges for organizations: the ability to effectively discover and document a breach quickly (most breaches are discovered months after they occur) and managing public relations after a breach. A company needs to plan for a breach and have a well-thought-out process not only for the technical remediation but also dealing with regulator, customer, and media concerns. -
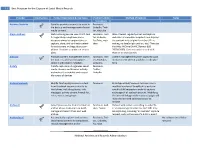
Best Practices for Social Media Capture
11 Best Practices for the Capture of Social Media Records Provider Paid Service Product Description & Use Cases Platforms Able Method of Capture Notes to Capture Actiance Socialite Socialite provides products to assist in Facebook, the backup and management of social LinkedIn, Twit- media content. ter, YouTube Aleph Archives Web archiving service uses CAMA tool Facebook, Twit- Web crawlers regularly crawl and capture for regulatory compliance and e- ter, LinkedIn, web sites as complete snapshots and displays discovery aimed at corporations to YouTube, web- the content in its original form (no URL re- capture, store, and sort web content sites writing, no JavaScript injection, etc.) They use for e-discovery and regulatory com- the Web ARChive (WARC) format (ISO pliance. Provides a number of service 28500:2009). Content can be stored with plans. them or on own servers. Alfresco Provides content management within Facebook, Twit- Content management system captures social the tool. It is unclear if it captures ter, YouTube, media content when it publishes to the plat- content with related metadata. websites, form. Archify Archify captures and organizes social Facebook, media streams and browser activity Twitter, and makes it searchable and accessi- LinkedIn ble across all devices. ArchiveFacebook Mozilla Firefox plug-in saves content Facebook Prototype called Facebook Archiver uses a from Facebook accounts directly to modified version of ScrapBook to perform hard drives, including photos, info, specific AJAX requests in order to capture messages, activity stream, friends list, each page of a Facebook account. Modifying notes, events and groups. the internal linkage of the captured pages will make the archived collection easier to browse. -

Socialite Make Social Networking Easy and More Effective for Everyone in Your Organization, While Meeting the Needs of Your Compliance, Legal, and Security Teams
Product Overview Socialite Make social networking easy and more effective for everyone in your organization, while meeting the needs of your compliance, legal, and security teams. With Socialite, your organization can rest assured that it has the security, governance, and compliance it requires for its employees to share and engage on social networks. Engage and share with your audience Marketing and selling socially requires solutions that help your business units improve engagement. Provide teams with the ability to listen to and engage clients on social More information: networks directly from desktop browsers, mobile devices; and from the Socialite portal and Socialite app for iPhone and iPad. Users can share content from your organization’s library of pre-approved articles and measure the impact of the content they share. That helps them improve their relevancy so they can become trusted sources of information for existing and actiance.com/socialite prospective clients. Make social networks part of any platform Not everyone uses social networks the same way, or in the same place. Socialite allows [email protected] your organization to integrate its compliance and social sharing capabilities with the apps and portals your marketers and sellers use every day. This ensures they have access to the solutions and social networks they need without making them change the way they work. 888.349.3223 Control features with granular policies Decide which features groups or individuals can access while browsing social network websites on your corporate network. From unrestricted to read-only access, Socialite gives you the flexibility to customize policies for Facebook, LinkedIn, Twitter, Google+ and facebook.com/Actiance YouTube that meet your unique requirements. -

Upgrading from Microsoft OCS to Lync the Ideal Time to Address Your Social Business Needs Executive Summary
Upgrading from Microsoft OCS to Lync The Ideal Time to Address Your Social Business Needs Executive Summary Microsoft Unified Communications (UC) users are migrating from Office a single mouse click. These advances make Lync UC more valuable to Communications Server (OCS) to Microsoft Lync to take advantage of the corporations, putting sales in real-time contact with potential customers, many new features incorporated into Lync, especially new voice features enhancing support for existing customers, enabling hiring managers to such as support for common area phones, enhanced emergency service contact prospects and work with new hires, and allowing marketing to (E-911), new VoIP support that makes Lync a suitable replacement for engage with prospects in a new way. As UC value and access expands PBX, and new voice features for select public instant messaging platforms. beyond the enterprise to embrace public networks, so do the concerns over Where Microsoft OCS delivered federation for different consumer UC managing access for security and compliance. platforms so users could connect in real-time using instant messaging and chat, Microsoft Lync adds Public IM Connectivity (PIC), giving users As enterprises deploy Lync to take advantage of richer communications integrated voice with public instant messaging (IM) platforms such as Live with public IM networks and UC clients, it creates a need for more robust Messenger which now supports more than 300 million users. Microsoft’s security. Migration from Microsoft OCS to Lync is the ideal time to assess acquisition of Skype, which now boasts about 700 million users, promises the security of your unified communications, especially as it relates to an to extend Lync access even further. -
Passport to Business Solutions 2015 FINRA Annual Conference
Passport to Business Solutions 2015 FINRA Annual Conference Visit at least 30 exhibitors… Yeah? …and receive a special gift! How to Use Your Passport Bring the passport with you when visiting the exhibitors 1. on level 4. Collect stamps from each exhibitor 2. you visit. Submit the last page with at least 30 stamps at the conference 3. registration desk. Receive a 4. special gift. Disclaimer: Use of any products, services and/or materials offered by these exhibitors does not ensure compliance regulatory requirements or create a safe harbor from regulatory responsibility. FINRA does not endorse these exhibitors or the products, services and/or materials they offer, and firms are not obligated to use them. ACA Compliance Group www.acacompliancegroup.com ACA Compliance Group is a leading provider of regulatory compliance products and solutions, cybersecurity and risk assessments, performance services, and technology solutions to regional, national and global firms in the financial services industry. With offices worldwide, ACA clients include leading broker-dealers, investment advisers, private fund managers, commodity trading advisers and investment companies. Actiance, Inc. www.actiance.com Actiance provides a platform that helps firms meet their regulatory requirements by controlling, capturing, archiving and making e-discoverable all forms of electronic communications (email, unified communications, instant messages, collaboration tools and social media). With more than 1,600 clients, three out of four people working in financial services in North America work for a firm with an Actiance solution. BasisCode Compliance www.basiscode.com BasisCode Compliance is an enterprise, compliance and audit platform that offers broker-dealers an integrated suite of multiple rule-based compliance functions.