The Datacenter As a Computer: an Introduction to The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application for a Certificate of Eligibility to Employ Child Performers
Division of Labor Standards Permit and Certificate Unit Harriman State Office Campus Building 12, Room 185B Albany, NY 12240 www.labor.ny.gov Application for a Certificate of Eligibility to Employ Child Performers A. Submission Instructions A Certificate of Eligibility to Employ Child Performers must be obtained prior to employing any child performer. Certificates are renew able every three (3) years. To obtain or renew a certificate: • Complete Parts B, C, D and E of this application. • Attach proof of New York State Workers’ Compensation and Disability Insurance. o If you currently have employees in New York, you must provide proof of coverage for those New York State w orkers by attaching copies of Form C-105.2 and DB-120.1, obtainable from your insurance carrier. o If you are currently exempt from this requirement, complete Form CE-200 attesting that you are not required to obtain New York State Workers’ Compensation and Disability Insurance Coverage. Information on and copies of this form are available from any district office of the Workers’ Compensation Board or from their w ebsite at w ww.wcb.ny.gov, Click on “WC/DB Exemptions,” then click on “Request for WC/DB Exemptions.” • Attach a check for the correct amount from Section D, made payable to the Commissioner of Labor. • Sign and mail this completed application and all required documents to the address listed above. If you have any questions, call (518) 457-1942, email [email protected] or visit the Department’s w ebsite at w ww.labor.ny.gov B. Type of Request (check one) New Renew al Current certificate number _______________________________________________ Are you seeking this certificate to employ child models? Yes No C. -

Program #6: Word Count
CSc 227 — Program Design and Development Spring 2014 (McCann) http://www.cs.arizona.edu/classes/cs227/spring14/ Program #6: Word Count Due Date: March 11 th, 2014, at 9:00 p.m. MST Overview: The UNIX operating system (and its variants, of which Linux is one) includes quite a few useful utility programs. One of those is wc, which is short for Word Count. The purpose of wc is to give users an easy way to determine the size of a text file in terms of the number of lines, words, and bytes it contains. (It can do a bit more, but that’s all of the functionality that we are concerned with for this assignment.) Counting lines is done by looking for “end of line” characters (\n (ASCII 10) for UNIX text files, or the pair \r\n (ASCII 13 and 10) for Windows/DOS text files). Counting words is also straight–forward: Any sequence of characters not interrupted by “whitespace” (spaces, tabs, end–of–line characters) is a word. Of course, whitespace characters are characters, and need to be counted as such. A problem with wc is that it generates a very minimal output format. Here’s an example of what wc produces on a Linux system when asked to count the content of a pair of files; we can do better! $ wc prog6a.dat prog6b.dat 2 6 38 prog6a.dat 32 321 1883 prog6b.dat 34 327 1921 total Assignment: Write a Java program (completely documented according to the class documentation guidelines, of course) that counts lines, words, and bytes (characters) of text files. -

“Where the Internet Lives” Data Centers As Cloud Infrastructure
C HAPTER 3 “Where the Internet Lives” Data Centers as Cloud Infrastructure JN OEN IFER H LT AND PATRICK VONDERAU mblazoned with the headline “Transparency,” Google released dozens of Einterior and exterior glossy images of their data centers on the company’s website in 2012. Inviting the public to “come inside” and “see where the In- ternet lives,” Google proudly announced they would reveal “what we’re made of— inside and out” by offering virtual tours through photo galleries of the tech- nology, the people, and the places making up their data centers.1 Google’s tours showed the world a glimpse of these structures with a series of photographs showcasing “the physical Internet,” as the site characterized it. The pictures consisted mainly of slick, artful images of buildings, wires, pipes, servers, and dedicated workers who populate the centers. Apple has also put the infrastructure behind its cloud services on display for the digital audience by featuring a host of infographics, statistics, and polished inside views of the company’s “environmentally responsible” data center fa- cilities on its website.2 Facebook, in turn, features extensive photo and news coverage of its global physical infrastructure on dedicated Facebook pages, while Microsoft presents guided video tours of their server farms for free download on its corporate website.3 Even smaller data centers like those owned by Eu- ropean Internet service provider Bahnhof AB, located in Sweden, are increas- ingly on digital exhibit, with their corporate parents offering various images of server racks, cooling and power technology, or even their meeting rooms, Copyright © ${Date}. -

Google's Hyperscale Data Centres and Infrastructure Ecosystem in Europe
GOOGLE’S HYPERSCALE DATA CENTRES AND INFRASTRUCTURE ECOSYSTEM IN EUROPE Economic impact study CLIENT: GOOGLE SEPTEMBER 2019 AUTHORS Dr Bruno Basalisco, Managing economist, Head of Digital Economy service Martin Bo Westh Hansen, Managing economist, Head of Energy & Climate service Tuomas Haanperä, Managing economist Erik Dahlberg, Senior economist Morten May Hansen, Economist Joshua Brown, Analyst Laurids Leo Münier, Analyst 0 Malthe Faber Laursen, Analyst Helge Sigurd Næss-Schmidt, Partner EXECUTIVE SUMMARY Digital transformation is a defining challenge and opportunity for the European economy, provid- ing the means to reinvent and improve how firms, consumers, governments, and citizens interact and do business with each other. European consumers, firms, and society stand to benefit from the resulting innovative products, processes, services, and business models – contributing to EU productivity. To maximise these benefits, it is key that the private and public sector can rely on an advanced and efficient cloud value chain. Considerable literature exists on cloud solutions and their transformative impact across the econ- omy. This report contributes by focusing on the analysis of the cloud value chain, taking Google as a relevant case study. It assesses the economic impact of the Google European hyperscale data cen- tres and related infrastructures which, behind the scenes, underpin online services such as cloud solutions. Thus, the report is an applied analysis of these infrastructure layers “above the cloud” (upstream inputs to deliver cloud solutions) and quantifies Google’s European economic contribu- tion associated with these activities. Double-clicking the cloud Services, such as Google Cloud, are a key example of a set of solutions that can serve a variety of Eu- ropean business needs and thus support economic productivity. -

DC Console Using DC Console Application Design Software
DC Console Using DC Console Application Design Software DC Console is easy-to-use, application design software developed specifically to work in conjunction with AML’s DC Suite. Create. Distribute. Collect. Every LDX10 handheld computer comes with DC Suite, which includes seven (7) pre-developed applications for common data collection tasks. Now LDX10 users can use DC Console to modify these applications, or create their own from scratch. AML 800.648.4452 Made in USA www.amltd.com Introduction This document briefly covers how to use DC Console and the features and settings. Be sure to read this document in its entirety before attempting to use AML’s DC Console with a DC Suite compatible device. What is the difference between an “App” and a “Suite”? “Apps” are single applications running on the device used to collect and store data. In most cases, multiple apps would be utilized to handle various operations. For example, the ‘Item_Quantity’ app is one of the most widely used apps and the most direct means to take a basic inventory count, it produces a data file showing what items are in stock, the relative quantities, and requires minimal input from the mobile worker(s). Other operations will require additional input, for example, if you also need to know the specific location for each item in inventory, the ‘Item_Lot_Quantity’ app would be a better fit. Apps can be used in a variety of ways and provide the LDX10 the flexibility to handle virtually any data collection operation. “Suite” files are simply collections of individual apps. Suite files allow you to easily manage and edit multiple apps from within a single ‘store-house’ file and provide an effortless means for device deployment. -

How to Find out the IP Address of an Omron
Communications Middleware/Network Browser How to find an Omron Controller’s IP address Valin Corporation | www.valin.com Overview • Many Omron PLC’s have Ethernet ports or Ethernet port options • The IP address for a PLC is usually changed by the programmer • Most customers do not mark the controller with IP address (label etc.) • Very difficult to communicate to the PLC over Ethernet if the IP address is unknown. Valin Corporation | www.valin.com Simple Ethernet Network Basics IP address is up to 12 digits (4 octets) Ex:192.168.1.1 For MOST PLC programming applications, the first 3 octets are the network address and the last is the node address. In above example 192.168.1 is network address, 1 is node address. For devices to communicate on a simple network: • Every device IP Network address must be the same. • Every device node number must be different. Device Laptop EX: Omron PLC 192.168.1.1 192.168.1.1 Device Laptop EX: Omron PLC 127.27.250.5 192.168.1.1 Device Laptop EX: Omron PLC 192.168.1.3 192.168.1.1 Valin Corporation | www.valin.com Omron Default IP Address • Most Omron Ethernet devices use one of the following IP addresses by default. Omron PLC 192.168.250.1 OR 192.168.1.1 Valin Corporation | www.valin.com PING Command • PING is a way to check if the device is connected (both virtually and physically) to the network. • Windows Command Prompt command. • PC must use the same network number as device (See previous) • Example: “ping 172.21.90.5” will test to see if a device with that IP address is connected to the PC. -

HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan
HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan Lectures 1,2,3 [email protected] 1 Lecture 1 • Files and directories. • Introduce a number of simple UNIX commands for manipulation of files and directories. • communicating with remote machines [email protected] 2 What is LINUX • LINUX is the operating system (OS) kernel. • Sitting on top of the LINUX OS are a lot of utilities that help you do stuff. • You get a ‘LINUX distribution’ installed on your desktop/laptop. This is a sloppy way of saying you get the OS bundled with lots of useful utilities/applications. • Use LINUX to mean anything from the OS to the distribution we are using. • UNIX is an operating system that is very similar to LINUX (same command names, sometimes slightly different functionalities of commands etc). – There are usually enough subtle differences between LINUX and UNIX versions to keep you on your toes (e.g. Solaris and LINUX) when running applications on multiple platforms …be mindful of this if you use other UNIX flavours. – Mac OS X is based on a UNIX distribution. [email protected] 3 Accessing a machine • You need a user account you should all have one by now • can then log in at the terminal (i.e. sit in front of a machine and type in your user name and password to log in to it). • you can also log in remotely to a machine somewhere else RAL SLAC CERN London FNAL in2p3 [email protected] 4 The command line • A user interfaces with Linux by typing commands into a shell. -

Useful Tai Ls Dino
SCIENCE & NATURE Useful Tails Materials Pictures of a possum, horse, lizard, rattlesnake, peacock, fish, bird, and beaver What to do 1. Display the animal pictures so the children can see them. 2. Say the following sentences. Ask the children to guess the animal by the usefulness of its tail. I use my tail for hanging upside down. (possum) I use my tail as a fly swatter. (horse) When my tail breaks off, I grow a new one. (lizard) I shake my noisy tail when I am about to strike. (rattlesnake) My tail opens like a beautiful fan. (peacock) I use my tail as a propeller. I cannot swim without it. (fish) I can’t fly without my tail. (bird) I use my powerful tail for building. (beaver) More to do Ask the children if they can name other animals that have tails. Ask them how these animals’Downloaded tails might by [email protected] useful. from Games: Cut out the tailsProFilePlanner.com of each of the animals. Encourage the children to pin the tails on the pictures (like “Pin the Tail on the Donkey”). Dotti Enderle, Richmond, TX Dino Dig Materials Plastic or rubber dinosaurs or bones Sand Wide-tip, medium-sized paintbrushes Plastic sand shovels Small plastic buckets Clipboards Paper Pencil or pens 508 The GIANT Encyclopedia of Preschool Activities for Four-Year-Olds Downloaded by [email protected] from ProFilePlanner.com SCIENCE & NATURE What to do 1. Beforehand, hide plastic or rubber dinosaurs or bones in the sand. 2. Give each child a paintbrush, shovel, and bucket. 3. -

Shell Variables
Shell Using the command line Orna Agmon ladypine at vipe.technion.ac.il Haifux Shell – p. 1/55 TOC Various shells Customizing the shell getting help and information Combining simple and useful commands output redirection lists of commands job control environment variables Remote shell textual editors textual clients references Shell – p. 2/55 What is the shell? The shell is the wrapper around the system: a communication means between the user and the system The shell is the manner in which the user can interact with the system through the terminal. The shell is also a script interpreter. The simplest script is a bunch of shell commands. Shell scripts are used in order to boot the system. The user can also write and execute shell scripts. Shell – p. 3/55 Shell - which shell? There are several kinds of shells. For example, bash (Bourne Again Shell), csh, tcsh, zsh, ksh (Korn Shell). The most important shell is bash, since it is available on almost every free Unix system. The Linux system scripts use bash. The default shell for the user is set in the /etc/passwd file. Here is a line out of this file for example: dana:x:500:500:Dana,,,:/home/dana:/bin/bash This line means that user dana uses bash (located on the system at /bin/bash) as her default shell. Shell – p. 4/55 Starting to work in another shell If Dana wishes to temporarily use another shell, she can simply call this shell from the command line: [dana@granada ˜]$ bash dana@granada:˜$ #In bash now dana@granada:˜$ exit [dana@granada ˜]$ bash dana@granada:˜$ #In bash now, going to hit ctrl D dana@granada:˜$ exit [dana@granada ˜]$ #In original shell now Shell – p. -

What Is UNIX? the Directory Structure Basic Commands Find
What is UNIX? UNIX is an operating system like Windows on our computers. By operating system, we mean the suite of programs which make the computer work. It is a stable, multi-user, multi-tasking system for servers, desktops and laptops. The Directory Structure All the files are grouped together in the directory structure. The file-system is arranged in a hierarchical structure, like an inverted tree. The top of the hierarchy is traditionally called root (written as a slash / ) Basic commands When you first login, your current working directory is your home directory. In UNIX (.) means the current directory and (..) means the parent of the current directory. find command The find command is used to locate files on a Unix or Linux system. find will search any set of directories you specify for files that match the supplied search criteria. The syntax looks like this: find where-to-look criteria what-to-do All arguments to find are optional, and there are defaults for all parts. where-to-look defaults to . (that is, the current working directory), criteria defaults to none (that is, select all files), and what-to-do (known as the find action) defaults to ‑print (that is, display the names of found files to standard output). Examples: find . –name *.txt (finds all the files ending with txt in current directory and subdirectories) find . -mtime 1 (find all the files modified exact 1 day) find . -mtime -1 (find all the files modified less than 1 day) find . -mtime +1 (find all the files modified more than 1 day) find . -
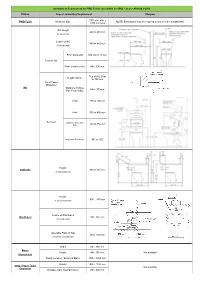
Summary of Requirement for PWD Toilets (Not Within an SOU) – As Per AS1428.1-2009
Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram 1900 mm wide x PWD Toilet Minimum Size NOTE: Extra space may be required to allow for the a washbasin. 2300 mm long WC Height 460 to 480 mm (to top of seat) Centre of WC 450 to 460 mm (from side wall) From back wall 800 mm ± 10 mm Front of WC From cistern or like Min. 600 mm Top of WC Seat Height of Zone to 700 mm Toilet Paper Dispenser WC Distance of Zone Max. 300mm from Front of QC Height 150 to 200 mm Width 350 to 400 mm Backrest Distance above WC Seat 120 to 150 mm Angle from Seat Hinge 90° to 100° Height Grabrails 800 to 810 mm (to top of grab rail) Height 800 – 830 mm (to top of washbasin) Centre of Washbasin Washbasin Min. 425 mm (from side wall) Operable Parts of Tap Max. 300 mm (from front of washbasin) Width Min. 350 mm Mirror Height Min. 950 mm Not available (if provided) Fixing Location / Extent of Mirror 900 – 1850 mm Height 900 – 1100 mm Soap / Paper Towel Not available Dispenser Distance from Internal Corner Min. 500 mm Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram Height 1200 – 1350 mm PWD Clothes Hook Not available Distance from Internal Corner Min. 500 mm Height 800 – 830 mm As vanity bench top Width Min. 120 mm Depth 300 – 400 mm Shelves Not available Height 900 – 1000 mm As separate fixture (if within any required Width 120 – 150 mm circulation space) Length 300 – 400 mm Width Min. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10