Live Block Device Operations in QEMU
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effective Virtual CPU Configuration with QEMU and Libvirt
Effective Virtual CPU Configuration with QEMU and libvirt Kashyap Chamarthy <[email protected]> Open Source Summit Edinburgh, 2018 1 / 38 Timeline of recent CPU flaws, 2018 (a) Jan 03 • Spectre v1: Bounds Check Bypass Jan 03 • Spectre v2: Branch Target Injection Jan 03 • Meltdown: Rogue Data Cache Load May 21 • Spectre-NG: Speculative Store Bypass Jun 21 • TLBleed: Side-channel attack over shared TLBs 2 / 38 Timeline of recent CPU flaws, 2018 (b) Jun 29 • NetSpectre: Side-channel attack over local network Jul 10 • Spectre-NG: Bounds Check Bypass Store Aug 14 • L1TF: "L1 Terminal Fault" ... • ? 3 / 38 Related talks in the ‘References’ section Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications What this talk is not about 4 / 38 Related talks in the ‘References’ section What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications 4 / 38 What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications Related talks in the ‘References’ section 4 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP QEMU QEMU VM1 VM2 Custom Disk1 Disk2 Appliance ioctl() KVM-based virtualization components Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP Custom Appliance KVM-based virtualization components QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) Custom Appliance KVM-based virtualization components libvirtd QMP QMP QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 libguestfs (guestfish) Custom Appliance KVM-based virtualization components OpenStack, et al. -

Red Hat Enterprise Linux 7 7.1 Release Notes
Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Legal Notice Copyright © 2015 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Dave Brolley William Cohen Roland Grunberg Aldy Hernandez Karsten Hopp Jakub Jelinek Developer Guide Jeff Johnston Benjamin Kosnik Aleksander Kurtakov Chris Moller Phil Muldoon Andrew Overholt Charley Wang Kent Sebastian Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Edition 0 Author Dave Brolley [email protected] Author William Cohen [email protected] Author Roland Grunberg [email protected] Author Aldy Hernandez [email protected] Author Karsten Hopp [email protected] Author Jakub Jelinek [email protected] Author Jeff Johnston [email protected] Author Benjamin Kosnik [email protected] Author Aleksander Kurtakov [email protected] Author Chris Moller [email protected] Author Phil Muldoon [email protected] Author Andrew Overholt [email protected] Author Charley Wang [email protected] Author Kent Sebastian [email protected] Editor Don Domingo [email protected] Editor Jacquelynn East [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. -

Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Robert Krátký Red Hat Customer Content Services [email protected] Don Domingo Red Hat Customer Content Services Jacquelynn East Red Hat Customer Content Services Legal Notice Copyright © 2016 Red Hat, Inc. and others. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Version 6.10.4.1/OCT.12.2018 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Copyright © 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks of Symantec Corp. or its affiliates in the U.S. and other coun- tries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. Symantec Corporation 350 Ellis Street Mountain View, CA 94043 www.symantec.com Policy Guide/Page 4 Symantec Web Security Service Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology as well as the WebPulse™ cloud com- munity of over 75 million users. -

Virtualization Best Practices
SUSE Linux Enterprise Server 15 SP1 Virtualization Best Practices SUSE Linux Enterprise Server 15 SP1 Publication Date: September 24, 2021 Contents 1 Virtualization Scenarios 2 2 Before You Apply Modifications 2 3 Recommendations 3 4 VM Host Server Configuration and Resource Allocation 3 5 VM Guest Images 25 6 VM Guest Configuration 36 7 VM Guest-Specific Configurations and Settings 42 8 Xen: Converting a Paravirtual (PV) Guest to a Fully Virtual (FV/HVM) Guest 45 9 External References 49 1 SLES 15 SP1 1 Virtualization Scenarios Virtualization oers a lot of capabilities to your environment. It can be used in multiple scenarios. To get more details about it, refer to the Book “Virtualization Guide” and in particular, to the following sections: Book “Virtualization Guide”, Chapter 1 “Virtualization Technology”, Section 1.2 “Virtualization Capabilities” Book “Virtualization Guide”, Chapter 1 “Virtualization Technology”, Section 1.3 “Virtualization Benefits” This best practice guide will provide advice for making the right choice in your environment. It will recommend or discourage the usage of options depending on your workload. Fixing conguration issues and performing tuning tasks will increase the performance of VM Guest's near to bare metal. 2 Before You Apply Modifications 2.1 Back Up First Changing the conguration of the VM Guest or the VM Host Server can lead to data loss or an unstable state. It is really important that you do backups of les, data, images, etc. before making any changes. Without backups you cannot restore the original state after a data loss or a misconguration. Do not perform tests or experiments on production systems. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -

Virtualization
Virtualization Rich Jones & Mark McLoughlin 2009-06-27 @ 11:00 What? ● Guest virtual machines ● Run multiple OSes on a single host ● Support from modern hardware Why? ● Test rawhide ● Play with other distros ● Run windows ● Server consolidation ● Migration How? ● yum groupinstall Virtualization ● virt-manager Previously - Xen ● Standalone hypervisor ● Paravirtualization ● Dom0 not upstream Now - KVM ● kvm.ko ● VM is just a process ● Uses Intel VT or AMD SVM ● Paravirt too ● Simple, secure, fast Cool Features ● Save/restore ● Live migration ● PCI/USB device assignment ● Swapable guest memory ● Ballooning ● KSM libvirt ● A VM management API ● e.g. list VMs, start/stop VM ● XML format to describe VMs ● Hypervisor independent - KVM, Xen, LXC, VirtualBox, UML, ESX, ... libvirt – There's More ● Storage and networking management too – Storage pools and volumes – Virtual networks – Host network interface configuration ● Remote management ● Language bindings – C, Python, Perl, Ruby, OCaml, Java, C# Virtual Machine Manager ● Simple UI ● Easy to create a VM ● Monitoring ● Hotplug ● Remote management virt-install ● Kick off a guest install from the command line $> virt-install -n MyGuest -m 512 \ --disk pool=default,size=8 \ --network:default \ -l http://download.fedoraproject.org/.../x86_64/os Misc. Tools ● virt-clone/virt-image/virt-convert ● xenner – run Xen guests in KVM ● virt-top – 'top' for VMs ● virt-ps/virt-uname/virt-dmesg – poke VMs Get Involved ● list: [email protected] ● http://fedoraproject.org/wiki/Virtualization ● #virt on irc.oftc.net -

The Open Virtual Machine Format Whitepaper for OVF Specification
The Open Virtual Machine Format Whitepaper for OVF Specification version 0.9 OVF Whitepaper 0.9 VMware, Inc. 3401 Hillview Ave., Palo Alto CA, 94304 USA Tel 877-486-9273 Fax 650-427-5001 www.vmware.com XenSource, Inc. 2300 Geng Road, Suite 2500, Palo Alto, CA 94303 www.xensource.com Copyright © VMware, Inc. and XenSource, Inc. All rights reserved. VMware, the VMware “boxes” logo and design, Virtual SMP and VMotion are registered trademarks or trademarks of VMware, Inc. in the United States and/or other jurisdictions. Xen, XenSource, the “Circle Xen” logo and derivatives thereof are registered trademarks or trademarks of XenSource, Inc. in the United States and other countries. Microsoft, Windows and Windows NT are registered trademarks of Microsoft Corporation. Linux is a registered trademark of Linus Torvalds. All other marks and names mentioned herein may be trademarks of their respective companies. No part of this specification (whether in hardcopy or electronic form) may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of VMware, Inc. (VMware), and XenSource, Inc. (XenSource) except as otherwise permitted under copyright law or the terms of that certain Teaming and Non-Disclosure Agreement between VMware and XenSource dated March 23, 2007, as amended from time to time. Please note that the content in this specification is protected under copyright law even if it is not distributed with software -

FVD: a High-Performance Virtual Machine Image Format for Cloud
FVD: a High-Performance Virtual Machine Image Format for Cloud Chunqiang Tang IBM T.J. Watson Research Center [email protected] http://www.research.ibm.com/people/c/ctang/ Note: This paper describes the copy-on-write, copy- 1 Introduction on-read, and adaptive prefetching capabilities of FVD. The compact image capability of FVD is described Cloud Computing is widely considered as the next big separately in a companion paper entitled “Compact thing in IT evolution. In a Cloud like Amazon EC2 [1], Image Support in Fast Virtual Disk (FVD)”, which the storage space for virtual machines’ virtual disks can is available at https://researcher.ibm.com/ be allocated from multiple sources: the host’s direct- researcher/view project.php?id=1852 attached storage (DAS, i.e., local disk), network-attached storage (NAS), or storage area network (SAN). These op- Abstract tions offer different performance, reliability, and avail- ability at different prices. DAS is at least several times This paper analyzes the gap between existing hyper- cheaper than NAS and SAN, but DAS limits the avail- visors’ virtual disk capabilities and the requirements in ability and mobility of VMs. a Cloud, and proposes a solution called FVD (Fast Vir- tual Disk). FVD consists of an image format and a To get the best out of the different technologies, a block device driver designed for QEMU. Despite the ex- Cloud usually offers a combination of block-device stor- istence of many popular virtual machine (VM) image age services to VMs. For instance, Amazon Web Ser- formats, FVD came out of our unsatisfied needs in the vices (AWS) [2] offers to a VM both ephemeral storage IBM Cloud. -

An Updated Overview of the QEMU Storage Stack
An Updated Overview of the QEMU Storage Stack Stefan Hajnoczi ± [email protected] Open Virtualization IBM Linux Technology Center 2011 Linux is a registered trademark of Linus Torvalds. The topic ● What is the QEMU storage stack? ● Configuring the storage stack ● Recent and future developments – “Cautionary statement regarding forward- looking statements” QEMU and its uses ● “QEMU is a generic and open source machine emulator and virtualizer” – http://www.qemu.org/ ● Emulation: – For cross-compilation, development environments – Android Emulator, shipping in an Android SDK near you ● Virtualization: – KVM and Xen use QEMU device emulation Storage in QEMU ● Devices and media: – Floppy, CD-ROM, USB stick, SD card, harddisk ● Host storage: – Flat files (img, iso) ● Also over NFS – CD-ROM host device (/dev/cdrom) – Block devices (/dev/sda3, LVM volumes, iSCSI LUNs) – Distributed storage (Sheepdog, Ceph) QEMU -drive option qemu -drive if=ide|virtio|scsi, file=path/to/img, cache=writethrough|writeback|none|unsafe ● Storage interface is set with if= ● Path to image file or device is set with path= ● Caching mode is set with cache= ● More on what this means later, but first the picture of the overall storage stack... The QEMU storage stack Application ·Application and guest kernel work similar to bare metal. File system & block layer ·Guest talks to QEMU via Driver emulated hardware. Hardware emulation ·QEMU performs I/O to an image file on behalf of the Image format (optional) guest. File system & block layer ·Host kernel treats guest I/O like any userspace Driver application. Guest QEMU Host Seeing double ● There may be two file systems. -
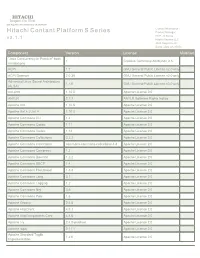
Hitachi Contant Platform S Series Product Manager HCP - S Series V 3
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Contant Platform S Series Product Manager HCP - S Series v 3 . 1 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified "Java Concurrency in Practice" book 1 Creative Commons Attribution 2.5 annotations ACPI 1.7 GNU General Public License v2.0 only ACPI Daemon 2.0.30 GNU General Public License v2.0 only Advanced Linux Sound Architecture 1.1.6 GNU General Public License v3.0 only (ALSA) ant-antlr 1.10.5 Apache License 2.0 ANTLR 2.7.7 ANTLR Software Rights Notice Apache Ant 1.10.5 Apache License 2.0 Apache Ant + JUnit 4 1.10.5 Apache License 2.0 Apache Commons CLI 1.4 Apache License 2.0 Apache Commons Codec 1.11 Apache License 2.0 Apache Commons Codec 1.14 Apache License 2.0 Apache Commons Collections 3.2.2 Apache License 2.0 Apache Commons Collections commons-commons-collections-4.4 Apache License 2.0 Apache Commons Compress 1.2 Apache License 2.0 Apache Commons Daemon 1.2.2 Apache License 2.0 Apache Commons DBCP 1.4 Apache License 2.0 Apache Commons FileUpload 1.3.3 Apache License 2.0 Apache Commons Lang 3.1 Apache License 2.0 Apache Commons Logging 1.2 Apache License 2.0 Apache Commons Net 3.6 Apache License 2.0 Apache Commons Pool 1.6 Apache License 2.0 Apache Groovy 2.4.8 Apache License 2.0 Apache HttpClient 4.5.3 Apache License 2.0 Apache HttpComponents Core 4.4.6 Apache License 2.0 Apache Ivy 2.4.0-patched Apache License 2.0 Apache log4j 2.11.1 Apache License 2.0 Apache Standard Taglib