Symantec Web Security Service Policy Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Translators' Tool
The Translator’s Tool Box A Computer Primer for Translators by Jost Zetzsche Version 9, December 2010 Copyright © 2010 International Writers’ Group, LLC. All rights reserved. This document, or any part thereof, may not be reproduced or transmitted electronically or by any other means without the prior written permission of International Writers’ Group, LLC. ABBYY FineReader and PDF Transformer are copyrighted by ABBYY Software House. Acrobat, Acrobat Reader, Dreamweaver, FrameMaker, HomeSite, InDesign, Illustrator, PageMaker, Photoshop, and RoboHelp are registered trademarks of Adobe Systems Inc. Acrocheck is copyrighted by acrolinx GmbH. Acronis True Image is a trademark of Acronis, Inc. Across is a trademark of Nero AG. AllChars is copyrighted by Jeroen Laarhoven. ApSIC Xbench and Comparator are copyrighted by ApSIC S.L. Araxis Merge is copyrighted by Araxis Ltd. ASAP Utilities is copyrighted by eGate Internet Solutions. Authoring Memory Tool is copyrighted by Sajan. Belarc Advisor is a trademark of Belarc, Inc. Catalyst and Publisher are trademarks of Alchemy Software Development Ltd. ClipMate is a trademark of Thornsoft Development. ColourProof, ColourTagger, and QA Solution are copyrighted by Yamagata Europe. Complete Word Count is copyrighted by Shauna Kelly. CopyFlow is a trademark of North Atlantic Publishing Systems, Inc. CrossCheck is copyrighted by Global Databases, Ltd. Déjà Vu is a trademark of ATRIL Language Engineering, S.L. Docucom PDF Driver is copyrighted by Zeon Corporation. dtSearch is a trademark of dtSearch Corp. EasyCleaner is a trademark of ToniArts. ExamDiff Pro is a trademark of Prestosoft. EmEditor is copyrighted by Emura Software inc. Error Spy is copyrighted by D.O.G. GmbH. FileHippo is copyrighted by FileHippo.com. -
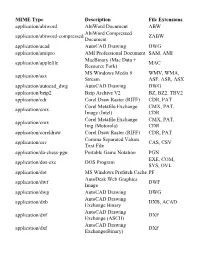
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Machine Learning in the Browser
Machine Learning in the Browser The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:38811507 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Machine Learning in the Browser a thesis presented by Tomas Reimers to The Department of Computer Science in partial fulfillment of the requirements for the degree of Bachelor of Arts in the subject of Computer Science Harvard University Cambridge, Massachusetts March 2017 Contents 1 Introduction 3 1.1 Background . .3 1.2 Motivation . .4 1.2.1 Privacy . .4 1.2.2 Unavailable Server . .4 1.2.3 Simple, Self-Contained Demos . .5 1.3 Challenges . .5 1.3.1 Performance . .5 1.3.2 Poor Generality . .7 1.3.3 Manual Implementation in JavaScript . .7 2 The TensorFlow Architecture 7 2.1 TensorFlow's API . .7 2.2 TensorFlow's Implementation . .9 2.3 Portability . .9 3 Compiling TensorFlow into JavaScript 10 3.1 Motivation to Compile . 10 3.2 Background on Emscripten . 10 3.2.1 Build Process . 12 3.2.2 Dependencies . 12 3.2.3 Bitness Assumptions . 13 3.2.4 Concurrency Model . 13 3.3 Experiences . 14 4 Results 15 4.1 Benchmarks . 15 4.2 Library Size . 16 4.3 WebAssembly . 17 5 Developer Experience 17 5.1 Universal Graph Runner . -

Embedded Linux for Thin Clients Next Generation (Elux® NG) Version 1.25
Embedded Linux for Thin Clients Next Generation (eLux® NG) Version 1.25 Administrator’s Guide Build Nr.: 23 UniCon Software GmbH www.myelux.com eLux® NG Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express consent of UniCon Software GmbH. © by UniCon 2005 Software GmbH. All rights reserved eLux is a registered trademark of UniCon Software GmbH in Germany. Accelerated-X is a trademark of Xi Graphics, Inc. Adobe, Acrobat Reader and PostScript are registered trademarks of Adobe Systems Incorporated in the United States and/or other countries. Broadcom is a registered trademark of Broadcom Corporation in the U.S. and/or other countries. CardOS is a registered trademark and CONNECT2AIR is a trademark of Siemens AG in Germany and/or other countries. Cisco and Aironet are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. Citrix, Independent Computing Architecture (ICA), Program Neighborhood, MetaFrame, and MetaFrame XP are registered trademarks or trademarks of Citrix Systems, Inc. in the United States and other countries. CUPS and the Common UNIX Printing System are the trademark property of Easy Software Products. DivX is a trademark of Project Mayo. Ericom and PowerTerm are registered trademarks of Ericom Software in the United States and/or other countries. Gemplus is a registered trademark and GemSAFE a trademark of Gemplus. -

Corel Wordperfect Office X7 R
Contents 1 | Introducing Corel WordPerfect Office X7 ................................ 1 2 | Customer profiles .................................................................... 3 3 | What’s included in the Standard Edition?............................... 5 4 | Key features ............................................................................. 9 Productivity.......................................................................................................... 9 Power ................................................................................................................ 12 Collaboration ..................................................................................................... 15 Value ................................................................................................................. 16 1 Introducing Corel® WordPerfect® Office X7 WordPerfect® Office X7 is a powerful, intuitive, and Collaboration highly compatible office suite that helps you do more with documents, spreadsheets, and presentations. WordPerfect Office has always been built to ensure More than 30 years since it first took the computing that you can easily collaborate and exchange your files world by storm, the legendary WordPerfect continues with others. to be trusted by governments, law firms, educational To that end, WordPerfect Office X7 offers extensive institutions, businesses, and consumers. support for more than 60 file formats, including the latest versions of Microsoft Office. Plus, its robust PDF Productivity import and -

ACS – the Archival Cytometry Standard
http://flowcyt.sf.net/acs/latest.pdf ACS – the Archival Cytometry Standard Archival Cytometry Standard ACS International Society for Advancement of Cytometry Candidate Recommendation DRAFT Document Status The Archival Cytometry Standard (ACS) has undergone several revisions since its initial development in June 2007. The current proposal is an ISAC Candidate Recommendation Draft. It is assumed, however not guaranteed, that significant features and design aspects will remain unchanged for the final version of the Recommendation. This specification has been formally tested to comply with the W3C XML schema version 1.0 specification but no position is taken with respect to whether a particular software implementing this specification performs according to medical or other valid regulations. The work may be used under the terms of the Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free to share (copy, distribute and transmit), and adapt the work under the conditions specified at http://creativecommons.org/licenses/by-sa/3.0/legalcode. Disclaimer of Liability The International Society for Advancement of Cytometry (ISAC) disclaims liability for any injury, harm, or other damage of any nature whatsoever, to persons or property, whether direct, indirect, consequential or compensatory, directly or indirectly resulting from publication, use of, or reliance on this Specification, and users of this Specification, as a condition of use, forever release ISAC from such liability and waive all claims against ISAC that may in any manner arise out of such liability. ISAC further disclaims all warranties, whether express, implied or statutory, and makes no assurances as to the accuracy or completeness of any information published in the Specification. -

Scene Graph Adapter
Scene Graph Adapter: An efficient Architecture to Improve Interoperability between 3D Formats and 3D Application Engines Rozenn Bouville Berthelot, Jérôme Royan, Thierry Duval, Bruno Arnaldi To cite this version: Rozenn Bouville Berthelot, Jérôme Royan, Thierry Duval, Bruno Arnaldi. Scene Graph Adapter: An efficient Architecture to Improve Interoperability between 3D Formats and 3D Application Engines. Web3D 2011 (16th International Conference on 3D Web technology), Jun 2011, Paris, France. pp.21- 30. inria-00586161 HAL Id: inria-00586161 https://hal.inria.fr/inria-00586161 Submitted on 6 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Scene Graph Adapter: An efficient Architecture to Improve Interoperability between 3D Formats and 3D Applications Engines Rozenn Bouville Berthelot∗ Jérôme Royan† Thierry Duval‡ Bruno Arnaldi§ Orange Labs and IRISA, Rennes, France Orange Labs France IRISA, Rennes, France IRISA, Rennes, France Figure 1: Our architecture allows the loading of any 3D graphics format simultaneously in any available rendering engine. The scene graph adapter is an interface that adapts a scene graph (SG) of a given format into a renderer scene graph and which also allows the rendering part to request this scene graph. -

Openoffice.Org News Highlights Table of Contents Octo Ber 2004
OpenOffice.org News Highlights Table of Contents Octo ber 2004 ................................................................................................ R eplacing FrameMaker with OOo Writer ............................................................................................. Ger mans claim Linux lowers costs ......................................................................................................... Ope n approach offers Mindef more choice ............................................................................................ Ball mer calls for horse-based attack on Star Office ............................................................................... Ope n for Business - The 2004 OfB Choice Awards .............................................................................. Sep tember 2004 ............................................................................................ Ope nOffice.org reveals marketing ambitions ......................................................................................... No nprofit brings Linux and open source to Hawaii ............................................................................... UK charity builds Linux network on a shoestring .................................................................................. N SW opens door to Linux offers ............................................................................................................ L eading Edge Forum Report 2004 - Open Source: Open for Business ................................................. -

Corel Wordperfect Office X5 Reviewer's Guide
Trusted by millions, it's everything you expect in an office suite Contents 1 | Introducing Corel WordPerfect Office X5 . 1 2 | Customer profiles . 3 3 | What’s included? . 4 4 | New and distinguishing features . 7 1 Introducing Corel® WordPerfect® Office X5 The productivity market has changed a lot in the productivity tools. While addressing emerging last 20 years; over the last two years, the pace of trends is critical, so is adding to the value of the that change has been exponential. New players core office suite. and business models have emerged that have expanded the scope of what is considered an office Drawing upon a rich history in office productivity productivity tool. And as functionality has innovation, Corel breaks new ground while still changed, so have users’ expectations. But as improving the most critical areas in the traditional always, the key to any new office suite is blending office suite, so users can do more with words, tools that users have come to rely on with new numbers, and ideas. Corel WordPerfect Office X5 features that fit into today’s workflow. redefines the office suite by providing: The Internet is impacting every technology • The ability to use WordPerfect® X5 in lockstep market because of its ability to connect people with document management systems, like ® ® and provide a vehicle for collaboration. Market Microsoft SharePoint . research indicates that business and government • Web Services integration, so users have the users are quickly adopting online tools to make time-saving capability of creating documents their organizations more collaborative and populated with data pulled from the Web. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Visualisation and Generalisation of 3D City Models
Visualisation and Generalisation of 3D City Models Bo Mao August 2010 TRITA SoM 2010-08 ISSN 1653-6126 ISRN KTH/SoM/-10/08/-SE ISBN 978-91-7415-715-4 © Bo Mao 2010 Licentiate Thesis Geoinformatics Division Department of Urban Planning and Environment Royal Institute of Technology (KTH) SE-100 44 STOCKHOLM, Sweden ii Abstract 3D city models have been widely used in different applications such as urban planning, traffic control, disaster management etc. Effective visualisation of 3D city models in various scales is one of the pivotal techniques to implement these applications. In this thesis, a framework is proposed to visualise the 3D city models both online and offline using City Geography Makeup Language (CityGML) and Extensible 3D (X3D) to represent and present the models. Then, generalisation methods are studied and tailored to create 3D city scenes in multi- scale dynamically. Finally, the quality of generalised 3D city models is evaluated by measuring the visual similarity from the original models. In the proposed visualisation framework, 3D city models are stored in CityGML format which supports both geometric and semantic information. These CityGML files are parsed to create 3D scenes and be visualised with existing 3D standard. Because the input and output in the framework are all standardised, it is possible to integrate city models from different sources and visualise them through the different viewers. Considering the complexity of the city objects, generalisation methods are studied to simplify the city models and increase the visualisation efficiency. In this thesis, the aggregation and typification methods are improved to simplify the 3D city models. -

Scalable Speculative Parallelization on Commodity Clusters
Scalable Speculative Parallelization on Commodity Clusters Hanjun Kim Arun Raman Feng Liu Jae W. Leey David I. August Departments of Electrical Engineering and Computer Science y Parakinetics Inc. Princeton University Princeton, USA Princeton, USA [email protected] {hanjunk, rarun, fengliu, august}@princeton.edu Abstract by the cluster is difficult. For these reasons, such programs have been deemed unsuitable for execution on clusters. While clusters of commodity servers and switches are the most popular form of large-scale parallel computers, many programs are Recent research has demonstrated that a combination of not easily parallelized for execution upon them. In particular, high pipeline parallelism (DSWP), thread-level speculation (TLS), inter-node communication cost and lack of globally shared memory and speculative pipeline parallelism (Spec-DSWP) can un- appear to make clusters suitable only for server applications with lock significant amounts of parallelism in general-purpose abundant task-level parallelism and scientific applications with regu- programs on shared memory systems [6, 24, 27, 29, 30, 32, lar and independent units of work. Clever use of pipeline parallelism (DSWP), thread-level speculation (TLS), and speculative pipeline 36, 37]. Pipeline parallelization techniques such as DSWP parallelism (Spec-DSWP) can mitigate the costs of inter-thread partition a loop in such a way that the critical path is executed communication on shared memory multicore machines. This paper in a thread-local fashion, with off-critical path data flowing presents Distributed Software Multi-threaded Transactional memory unidirectionally through the pipeline. The combination of these (DSMTX), a runtime system which makes these techniques applicable two factors makes the program execution highly insensitive to non-shared memory clusters, allowing them to efficiently address inter-node communication costs.