Virtualization Guide Virtualization Guide SUSE Linux Enterprise Server 15 SP2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effective Virtual CPU Configuration with QEMU and Libvirt
Effective Virtual CPU Configuration with QEMU and libvirt Kashyap Chamarthy <[email protected]> Open Source Summit Edinburgh, 2018 1 / 38 Timeline of recent CPU flaws, 2018 (a) Jan 03 • Spectre v1: Bounds Check Bypass Jan 03 • Spectre v2: Branch Target Injection Jan 03 • Meltdown: Rogue Data Cache Load May 21 • Spectre-NG: Speculative Store Bypass Jun 21 • TLBleed: Side-channel attack over shared TLBs 2 / 38 Timeline of recent CPU flaws, 2018 (b) Jun 29 • NetSpectre: Side-channel attack over local network Jul 10 • Spectre-NG: Bounds Check Bypass Store Aug 14 • L1TF: "L1 Terminal Fault" ... • ? 3 / 38 Related talks in the ‘References’ section Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications What this talk is not about 4 / 38 Related talks in the ‘References’ section What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications 4 / 38 What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications Related talks in the ‘References’ section 4 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP QEMU QEMU VM1 VM2 Custom Disk1 Disk2 Appliance ioctl() KVM-based virtualization components Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP Custom Appliance KVM-based virtualization components QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) Custom Appliance KVM-based virtualization components libvirtd QMP QMP QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 libguestfs (guestfish) Custom Appliance KVM-based virtualization components OpenStack, et al. -

Red Hat Enterprise Linux 7 7.1 Release Notes
Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Legal Notice Copyright © 2015 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Dave Brolley William Cohen Roland Grunberg Aldy Hernandez Karsten Hopp Jakub Jelinek Developer Guide Jeff Johnston Benjamin Kosnik Aleksander Kurtakov Chris Moller Phil Muldoon Andrew Overholt Charley Wang Kent Sebastian Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Edition 0 Author Dave Brolley [email protected] Author William Cohen [email protected] Author Roland Grunberg [email protected] Author Aldy Hernandez [email protected] Author Karsten Hopp [email protected] Author Jakub Jelinek [email protected] Author Jeff Johnston [email protected] Author Benjamin Kosnik [email protected] Author Aleksander Kurtakov [email protected] Author Chris Moller [email protected] Author Phil Muldoon [email protected] Author Andrew Overholt [email protected] Author Charley Wang [email protected] Author Kent Sebastian [email protected] Editor Don Domingo [email protected] Editor Jacquelynn East [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. -

Linux for Zseries: Device Drivers and Installation Commands (March 4, 2002) Summary of Changes
Linux for zSeries Device Drivers and Installation Commands (March 4, 2002) Linux Kernel 2.4 LNUX-1103-07 Linux for zSeries Device Drivers and Installation Commands (March 4, 2002) Linux Kernel 2.4 LNUX-1103-07 Note Before using this document, be sure to read the information in “Notices” on page 207. Eighth Edition – (March 2002) This edition applies to the Linux for zSeries kernel 2.4 patch (made in September 2001) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Summary of changes .........v Chapter 5. Linux for zSeries Console || Edition 8 changes.............v device drivers............27 Edition 7 changes.............v Console features .............28 Edition 6 changes ............vi Console kernel parameter syntax .......28 Edition 5 changes ............vi Console kernel examples ..........28 Edition 4 changes ............vi Usingtheconsole............28 Edition 3 changes ............vii Console – Use of VInput ..........30 Edition 2 changes ............vii Console limitations ............31 About this book ...........ix Chapter 6. Channel attached tape How this book is organized .........ix device driver ............33 Who should read this book .........ix Tapedriverfeatures...........33 Assumptions..............ix Tape character device front-end........34 Tape block -

Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Robert Krátký Red Hat Customer Content Services [email protected] Don Domingo Red Hat Customer Content Services Jacquelynn East Red Hat Customer Content Services Legal Notice Copyright © 2016 Red Hat, Inc. and others. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Virtualization Best Practices
SUSE Linux Enterprise Server 15 SP1 Virtualization Best Practices SUSE Linux Enterprise Server 15 SP1 Publication Date: September 24, 2021 Contents 1 Virtualization Scenarios 2 2 Before You Apply Modifications 2 3 Recommendations 3 4 VM Host Server Configuration and Resource Allocation 3 5 VM Guest Images 25 6 VM Guest Configuration 36 7 VM Guest-Specific Configurations and Settings 42 8 Xen: Converting a Paravirtual (PV) Guest to a Fully Virtual (FV/HVM) Guest 45 9 External References 49 1 SLES 15 SP1 1 Virtualization Scenarios Virtualization oers a lot of capabilities to your environment. It can be used in multiple scenarios. To get more details about it, refer to the Book “Virtualization Guide” and in particular, to the following sections: Book “Virtualization Guide”, Chapter 1 “Virtualization Technology”, Section 1.2 “Virtualization Capabilities” Book “Virtualization Guide”, Chapter 1 “Virtualization Technology”, Section 1.3 “Virtualization Benefits” This best practice guide will provide advice for making the right choice in your environment. It will recommend or discourage the usage of options depending on your workload. Fixing conguration issues and performing tuning tasks will increase the performance of VM Guest's near to bare metal. 2 Before You Apply Modifications 2.1 Back Up First Changing the conguration of the VM Guest or the VM Host Server can lead to data loss or an unstable state. It is really important that you do backups of les, data, images, etc. before making any changes. Without backups you cannot restore the original state after a data loss or a misconguration. Do not perform tests or experiments on production systems. -

Virtualization
Virtualization Rich Jones & Mark McLoughlin 2009-06-27 @ 11:00 What? ● Guest virtual machines ● Run multiple OSes on a single host ● Support from modern hardware Why? ● Test rawhide ● Play with other distros ● Run windows ● Server consolidation ● Migration How? ● yum groupinstall Virtualization ● virt-manager Previously - Xen ● Standalone hypervisor ● Paravirtualization ● Dom0 not upstream Now - KVM ● kvm.ko ● VM is just a process ● Uses Intel VT or AMD SVM ● Paravirt too ● Simple, secure, fast Cool Features ● Save/restore ● Live migration ● PCI/USB device assignment ● Swapable guest memory ● Ballooning ● KSM libvirt ● A VM management API ● e.g. list VMs, start/stop VM ● XML format to describe VMs ● Hypervisor independent - KVM, Xen, LXC, VirtualBox, UML, ESX, ... libvirt – There's More ● Storage and networking management too – Storage pools and volumes – Virtual networks – Host network interface configuration ● Remote management ● Language bindings – C, Python, Perl, Ruby, OCaml, Java, C# Virtual Machine Manager ● Simple UI ● Easy to create a VM ● Monitoring ● Hotplug ● Remote management virt-install ● Kick off a guest install from the command line $> virt-install -n MyGuest -m 512 \ --disk pool=default,size=8 \ --network:default \ -l http://download.fedoraproject.org/.../x86_64/os Misc. Tools ● virt-clone/virt-image/virt-convert ● xenner – run Xen guests in KVM ● virt-top – 'top' for VMs ● virt-ps/virt-uname/virt-dmesg – poke VMs Get Involved ● list: [email protected] ● http://fedoraproject.org/wiki/Virtualization ● #virt on irc.oftc.net -

An Updated Overview of the QEMU Storage Stack
An Updated Overview of the QEMU Storage Stack Stefan Hajnoczi ± [email protected] Open Virtualization IBM Linux Technology Center 2011 Linux is a registered trademark of Linus Torvalds. The topic ● What is the QEMU storage stack? ● Configuring the storage stack ● Recent and future developments – “Cautionary statement regarding forward- looking statements” QEMU and its uses ● “QEMU is a generic and open source machine emulator and virtualizer” – http://www.qemu.org/ ● Emulation: – For cross-compilation, development environments – Android Emulator, shipping in an Android SDK near you ● Virtualization: – KVM and Xen use QEMU device emulation Storage in QEMU ● Devices and media: – Floppy, CD-ROM, USB stick, SD card, harddisk ● Host storage: – Flat files (img, iso) ● Also over NFS – CD-ROM host device (/dev/cdrom) – Block devices (/dev/sda3, LVM volumes, iSCSI LUNs) – Distributed storage (Sheepdog, Ceph) QEMU -drive option qemu -drive if=ide|virtio|scsi, file=path/to/img, cache=writethrough|writeback|none|unsafe ● Storage interface is set with if= ● Path to image file or device is set with path= ● Caching mode is set with cache= ● More on what this means later, but first the picture of the overall storage stack... The QEMU storage stack Application ·Application and guest kernel work similar to bare metal. File system & block layer ·Guest talks to QEMU via Driver emulated hardware. Hardware emulation ·QEMU performs I/O to an image file on behalf of the Image format (optional) guest. File system & block layer ·Host kernel treats guest I/O like any userspace Driver application. Guest QEMU Host Seeing double ● There may be two file systems. -
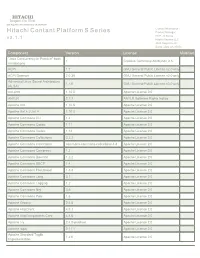
Hitachi Contant Platform S Series Product Manager HCP - S Series V 3
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Contant Platform S Series Product Manager HCP - S Series v 3 . 1 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified "Java Concurrency in Practice" book 1 Creative Commons Attribution 2.5 annotations ACPI 1.7 GNU General Public License v2.0 only ACPI Daemon 2.0.30 GNU General Public License v2.0 only Advanced Linux Sound Architecture 1.1.6 GNU General Public License v3.0 only (ALSA) ant-antlr 1.10.5 Apache License 2.0 ANTLR 2.7.7 ANTLR Software Rights Notice Apache Ant 1.10.5 Apache License 2.0 Apache Ant + JUnit 4 1.10.5 Apache License 2.0 Apache Commons CLI 1.4 Apache License 2.0 Apache Commons Codec 1.11 Apache License 2.0 Apache Commons Codec 1.14 Apache License 2.0 Apache Commons Collections 3.2.2 Apache License 2.0 Apache Commons Collections commons-commons-collections-4.4 Apache License 2.0 Apache Commons Compress 1.2 Apache License 2.0 Apache Commons Daemon 1.2.2 Apache License 2.0 Apache Commons DBCP 1.4 Apache License 2.0 Apache Commons FileUpload 1.3.3 Apache License 2.0 Apache Commons Lang 3.1 Apache License 2.0 Apache Commons Logging 1.2 Apache License 2.0 Apache Commons Net 3.6 Apache License 2.0 Apache Commons Pool 1.6 Apache License 2.0 Apache Groovy 2.4.8 Apache License 2.0 Apache HttpClient 4.5.3 Apache License 2.0 Apache HttpComponents Core 4.4.6 Apache License 2.0 Apache Ivy 2.4.0-patched Apache License 2.0 Apache log4j 2.11.1 Apache License 2.0 Apache Standard Taglib -

Red Hat Enterprise Linux 7 7.9 Release Notes
Red Hat Enterprise Linux 7 7.9 Release Notes Release Notes for Red Hat Enterprise Linux 7.9 Last Updated: 2021-08-17 Red Hat Enterprise Linux 7 7.9 Release Notes Release Notes for Red Hat Enterprise Linux 7.9 Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

A High-Performance Virtual Machine Filesystem Monitor in Cloud-Assisted Cognitive Iot
A high-performance virtual machine filesystem monitor in cloud-assisted cognitive IoT Dongyang Zhana, Lin Yea , Hongli Zhanga, Binxing Fanga,b, Huhua Lia, Yang Liua, Xiaojiang Duc, Mohsen Guizanid aSchool of Computer Science and Technology, Harbin Institute of Technology, Harbin, 150001, China bInstitute of Electronic and Information Engineering of UESTC in GuangdongDongguan Guangdong 523808, China cDepartment of Computer and Information Sciences, Temple University, Philadelphia, PA 19122, USA dDepartment of Electrical and Computer Engineering, University of Idaho, Moscow, ID, USA Abstract Cloud-assisted Cognitive Internet of Things has powerful data analytics abilities based on the computing and data storage capabilities of cloud virtual machines, which makes protecting virtual machine filesystem very important for the whole system security. Agentless periodic filesystem monitors are optimal solutions to protect cloud virtual machines because of the secure and low-overhead features. However, most of the periodic monitors usually scan all of the virtual machine filesystem or protected files in every scanning poll, so lots of secure files are scanned again and again even though they are not corrupted. In this paper, we propose a novel agentless periodic filesystem monitor framework for virtual machines with different image formats to improve the performance of agentless periodic monitors. Our core idea is to minimize the scope of the scanning files in both file integrity checking and virus detection. In our monitor, if a file is considered secure, it will not be scanned when it has not been modified. Since our monitor only scans the newly created and modified files, it can check less files than other filesystem monitors. -

Mesh Lab Manual
MESH LAB MANUAL Mesh Lab Manual (Linux) Version 0.3 May 2009 Written by David Johnson and Kevin Duff PAGE 1 OF 43 MESH LAB MANUAL Table of Contents 1 NOTATION USED IN THIS LAB MANUAL.............................................................4 2 GETTING STARTED................................................................................................5 2.1 ACCESS TO THE MESH SERVER.................................................................................5 2.2 ETIQUETTE AND SHARING THE MESH...........................................................................5 2.2.1 Checking Who Else is Logged Into The Server..........................................5 2.2.2 Sending an Instant Message to Other Users..............................................6 2.2.3 Modifying the Login Message......................................................................6 3 DESCRIPTION OF THE LAB SETUP.....................................................................7 4 ARCHITECTURE OF THE LABORATORY..........................................................10 4.1 THE FREE BSD SERVER (172.20.1.1)...................................................................11 4.2 THE LINUX SERVER (UBUNTU) (172.20.1.4)............................................................11 4.3 THE 3COM SWITCH (172.20.1.2).......................................................................12 4.4 THE POWER DISTRIBUTION UNIT (PDU) (172.20.1.3)...............................................12 5 HOW THE NODES BOOT THEIR OPERATING SYSTEM...................................13