The Art of Unix Programming Next the Art of Unix Programming
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Huiswerk Linux: Sendmail Virtual User Instellen
Huiswerk Linux: Sendmail virtual user instellen Als professioneel administrator wil je zo min mogelijk gebruikers op je Linux machine hebben. Echte Linux gebruikers hebben login-rechten op jouw server en kunnen schade aanrichten op jouw machine. Het is in de meeste gevallen niet nodig om voor iedere klant een gebruikersaccount aan te maken. De meeste klanten willen alleen dat hun e-mail werkt. De opdracht voor deze week is: maak een virtual user voor het testdomein.nl aan. Over virtual users Het nadeel van het instellen van Virtual Hosts is dat alle gebruikers geldig zijn voor ieder e-mail domein dat je aanmaakt. Stel dat je een e-mail domein ( virtual host ) voor een klant aanmaakt, zodat zij e-mail kan ontvangen via dit domein. Dit betekent dat andere gebruikers ook e-mail kunnen ontvangen voor datzelfde domein. Dit veroorzaakt veel extra spam. Het handige van virtual users is dat ze alleen bestaan voor het domein waarvoor ze zijn aangemaakt. Het sudo mechanisme Het configureren van Linux doen we namens de super-user . We moeten daarom tijdelijk inloggen als Administrator. Cygwin gebruikers Andere Linux gebruikers Sudo voor Cygwin gebruikers: rechts-klik op het icoon van de Sudo voor gebruikers van andere Linux-versies ( Ubuntu , Cygwin terminal, en kies voor Als administrator uitvoeren . Lubuntu , Kubuntu , Android , Gentoo , Debian , etc): start een Zorg er ook voor dat de Sendmail daemon is gestart: terminal met de toetsencombinatie <Ctrl><Alt>-T. We gebruiken het commando sudo om in te loggen met het su service sendmail start (become Super User) commando. Daardoor blijven we ingelogd: sudo su Feature controleren Sendmail wordt geconfigureerd via het bestand /etc/mail/sendmail.cf . -

Computers&Electronics
Computers&Electronics EPTEMBER 1983 formerly Popular Electronics $1 75 Improving Timex/Sinclair Data -Tape Loading Sony's New Personal Desktop Computer System Computerized Video Drawings Made Easy One -Shot Testing of Multiple Circuit Points 11-11,.# 1 1 1 .\\I. 1 r1 I A i f - .... f-7'I '1TTTT7 . II 1 ] _P .I- P _ 1 110S6 t!J OtJI1ndn7 210 OCOr131121nW 0519 0 N21060 é't 113N)121y0 1 o 1,873O OTbT T60W0S19 )1210 260i0^z view 140 14 7 1t ating System Simplified BUY A BANANA. SAVE A BUNCH. Meet the Banana',"the very business reports, etc.) tractor tough, versatile, portable, and feed (for precise alignment and reliable dot-matrix printer from quick loading), parallel or serial Gorilla:" interface (take your pick), self - At $249.95 retail it's an ideal inking ribbon cassette (for long and inexpensive companion for life and easy installation), 10 personal computers like Apple portable pounds in weight, and (or Apple"look alikes'such as compatibility with so many of the Franklin""orAlbern, most popular personal computers Commodore; "I'll S-80,` Kaypro;" on the market. Timex," Osborne;'etc. Plus its print head features a After that, it's merely com- unique single -hammer design that parable to other printers that can eliminates a lot of moving parts, to cost up to three times as much: eliminate a lot of annoying repairs. 10" carriages (to handle standard That's the Banana: silly name, 9'/2" paper), 80 columns, graphics serious service. It's everything capability, 10 characters per inch the expensive dot-matrix printers (expandable to 5 cpi) draft -quality are.. -

Lecture #2 "Computer Systems Big Picture"
18-600 Foundations of Computer Systems Lecture 2: “Computer Systems: The Big Picture” John P. Shen & Gregory Kesden 18-600 August 30, 2017 CS: AAP CS: APP ➢ Recommended Reference: ❖ Chapters 1 and 2 of Shen and Lipasti (SnL). ➢ Other Relevant References: ❖ “A Detailed Analysis of Contemporary ARM and x86 Architectures” by Emily Blem, Jaikrishnan Menon, and Karthikeyan Sankaralingam . (2013) ❖ “Amdahl’s and Gustafson’s Laws Revisited” by Andrzej Karbowski. (2008) 8/30/2017 (©J.P. Shen) 18-600 Lecture #2 1 18-600 Foundations of Computer Systems Lecture 2: “Computer Systems: The Big Picture” 1. Instruction Set Architecture (ISA) a. Hardware / Software Interface (HSI) b. Dynamic / Static Interface (DSI) c. Instruction Set Architecture Design & Examples 2. Historical Perspective on Computing a. Major Epochs of Modern Computers b. Computer Performance Iron Law (#1) 3. “Economics” of Computer Systems a. Amdahl’s Law and Gustafson’s Law b. Moore’s Law and Bell’s Law 8/30/2017 (©J.P. Shen) 18-600 Lecture #2 2 Anatomy of Engineering Design SPECIFICATION: Behavioral description of “What does it do?” Synthesis: Search for possible solutions; pick best one. Creative process IMPLEMENTATION: Structural description of “How is it constructed?” Analysis: Validate if the design meets the specification. “Does it do the right thing?” + “How well does it perform?” 8/30/2017 (©J.P. Shen) 18-600 Lecture #2 3 [Gerrit Blaauw & Fred Brooks, 1981] Instruction Set Processor Design ARCHITECTURE: (ISA) programmer/compiler view = SPECIFICATION • Functional programming model to application/system programmers • Opcodes, addressing modes, architected registers, IEEE floating point IMPLEMENTATION: (μarchitecture) processor designer view • Logical structure or organization that performs the ISA specification • Pipelining, functional units, caches, physical registers, buses, branch predictors REALIZATION: (Chip) chip/system designer view • Physical structure that embodies the implementation • Gates, cells, transistors, wires, dies, packaging 8/30/2017 (©J.P. -

Objective Is
Lehigh Preserve Institutional Repository Design of a microprocessor-based emulsion polymerization process control facility Dimitratos, John N. 1987 Find more at https://preserve.lib.lehigh.edu/ This document is brought to you for free and open access by Lehigh Preserve. It has been accepted for inclusion by an authorized administrator of Lehigh Preserve. For more information, please contact [email protected]. Design of a Microprocessor-based Emulsion Polymerization Process Control Facility A research report written in partial fulfillment of the requirements for the degree of Master of Science in Chemical F:ngim·ering, Lehigh University, Bethlehem, Pennsylvania by John N. Dimitratos June 1987 ,. Design of a Microprocessor-based Emulsion Polymerization .. ,_.,,-•• ·, ,, -i •:>:.·.:':' Process Control Facility ' A research report written in partial fulfillment of the requirements for the degree of Master of Science in Chemical Engineering, Lehigh University, Bethlehem, Pennsylvania by John N. Dimitratos June 1987 •1 to my father and my brother there art times when it is hard to decide what should be chosen at what price, and what endured in return for what reward. Perhaps it is still harder to stick to the decision Aristotle (384-322 B.C) Ethics, Book Ill. Abstract The explosion of microcomputer technology and the recent developments in software and hardware products introduce a new horizon of capabilities for the process control engineer. However, taking advantage of this new technology is not something easily done. H the process control engineer has to undertake such a project soon he will have to deal with the different languages the software engineer and the plant operator use. -

The Healthy Programmer - Get Fit
Early praise for The Healthy Programmer Joe Kutner offers practical, readable, and well-researched advice for those who sit at a keyboard. I’ve incorporated his health-and-fitness regimen into my writing routine. ➤ Dr. Steve Overman Professor of Physical Education (retired), Jackson State University Health and programming should go together like a horse and carriage. You can’t have one without the other. In our sedentary office work, we often forget that an absence of health is as bad as a lack of programming skills. Joe points out a dozen areas where you and I can do better. Every office worker should read this book and self-reflect on health improvements. ➤ Staffan Nöteberg Author of Pomodoro Technique Illustrated This book introduced me to the term conditioned hypereating. It felt life-changing. Being aware of this has made it easier to experiment with smaller, less-ambitious changes that actually have a chance at succeeding. I’m very curious to see where this puts me a year from now. ➤ Katrina Owen Developer, Jumpstart Lab The Healthy Programmer is excellent. In many ways it’s a spiritual continuation of The Hacker’s Diet. ➤ Stephen Ball Senior Rails programmer, PhishMe, Inc. The Healthy Programmer Get Fit, Feel Better, and Keep Coding Joe Kutner The Pragmatic Bookshelf Dallas, Texas • Raleigh, North Carolina Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. -

INSIDE HORTON, KANSAS Special Tax Hometown of Section Kevin & Included in Angela Strube Holton Recorder Subscribers This Edition
SALUTE TON INSIDE HORTON, KANSAS Special tax Hometown of section Kevin & included in Angela Strube Holton Recorder subscribers this edition. for 30 years. CSerin te acson County Community for years See pages 8-9. Volume 153, Issue 6 HOLTON, KANSAS • Wednesday, January 22, 2020 14 Pages $1.00 Livestock Expo is Saturday In previous years, Holton veterinarian Tim Parks was one of the fea tured presenters at the Jackson Coun ty Livestock Association’s annual Livestock Exposition. This year, Parks — who owned and operated Heartland Veterinary Clinic in Holton from 1998 to 2015 — will be the featured speaker at the 35thannual Livestock Expo, set for this District court cases Saturday at the Northeast Kansas Heritage Complex south of down about 24 percent Holton. Doors to the Heritage By Brian Sanders Much of the decrease Complex’s exhibition hall will After seeing a dramatic in the 2019 total could open at 5 p.m. for the expo’s rise from 2017 to 2018 be found in the number steak dinner, which will be in the number of cases of criminal misdemeanor served from 5:30 p.m. to 7 p.m. handled in Jackson County cases — 187, which was The program will begin District Court, 2019 was less than half of the 2018 at 6 p.m. and feature Parks, a somewhat quieter year total of 411 misdemeanors representing Mer ck Animal in comparison, thanks in handled by court personnel. Health. The program will also part to sizable decreases Felony cases were up feature the announcement of in criminal misdemeanor slightly, from 294 in 2018 JCLA’s Distinguished Stockman filings and traffic tickets. -

Modern Computer Architectures Lecture-1: Introduction
Modern Computer Architectures Lecture-1: Introduction Sandeep Kumar Panda Asso.Prof. IT Department CEB,BBSR 1 Introduction – Computer performance has been increasing phenomenally over the last five decades. – Brought out by Moore’s Law: ● Transistors per square inch roughly double every eighteen months. – Moore’s law is not exactly a law: ● But, has held good for nearly 50 years. 2 Introduction Cont… ● If commercial aircrafts had similar performance increase over the last 50 years, we should have: – Commercial planes flying at 1000 times the supersonic speed. – Aircrafts of the size of a chair. – Costing couple of thousand rupees only. 3 Moore’s Law Gordon Moore (co-founder of Intel) predicted in 1965: “Transistor density of minimum cost semiconductor chips would Moore’s Law: it’s worked for double roughly every 18 months.” a long time. Transistor density is correlated to processing speed. 4 Trends Related to Moore’s Law Cont… • Processor performance: • Twice as fast after every 2 years (roughly). • Memory capacity: • Twice as much after every 18 months (roughly). 5 Interpreting Moore’s Law ● Moore's law is not about just the density of transistors on a chip that can be achieved: – But about the density of transistors at which the cost per transistor is the lowest. ● As more transistors are made on a chip: – The cost to make each transistor reduces. – But the chance that the chip will not work due to a defect rises. ● Moore observed in 1965 there is a transistor density or complexity: – At which "a minimum cost" is achieved. 6 Integrated Circuits Costs IC cost = Die cost + Testing cost + Packaging cost Final test yield Final test yield: Fraction of packaged dies which pass the final testing state. -

Netpages White.Pdf
White NetPages NetPages™ is a directory for the Internet modeled after the phone book—with blue, white, and yellow pages sections. In the printed version, all three sections are together. In the e-book version, the White Netpages are one book and the Blue and Yellow NetPages are one book. To access the Blue and Yellow NetPages, send mail to [email protected] for sites. Directory of email addresses for individuals & businesses on the Internet How to Make a White NetPages Listing To add your name to NetPages, send this information to [email protected]. Last name: First name: Email address: Organization name: Job title: City: State: Country: Email address used for business, per- sonal, or both: Your listing will be sent to you via email for verification publishing. Yellow NetPages listings are available for business or organizations. Contact Aldea for pricing. If you have any questions or comments, write to [email protected] or call 1-800-TO ALDEA (619-943-0101). All listees will be notified of the electronic Internet “pickup” spot after its publication. How to get more information about NetPages NetPages is published in March and September. Hardcopy NetPages are distributed at major trade shows and by U.S. mail. Electronic versions are available online (locations to be advised). •General Aldea information [email protected] •Distribution information [email protected] •Add yourself to NetPages [email protected] •Remove yourself from NetPages [email protected] •Receive a copy of frequently asked questions (FAQ) [email protected] •Request a hardcopy of NetPages from: Aldea Communications, Inc. -

Alexander Stepanov Notes on Programming 10/3/2006 Preface
Alexander Stepanov Notes on Programming 10/3/2006 Preface.............................................................................................................................. 2 Lecture 1. Introduction .............................................................................................. 3 Lecture 2. Designing fvector_int ....................................................................... 8 Lecture 3. Continuing with fvector_int ......................................................... 24 Lecture 4. Implementing swap.............................................................................. 36 Lecture 5. Types and type functions .................................................................. 43 Lecture 6. Regular types and equality............................................................... 51 Lecture 7. Ordering and related algorithms .................................................... 56 Lecture 8. Order selection of up to 5 objects ................................................. 64 Lecture 9. Function objects.................................................................................... 69 Lecture 10. Generic algorithms ............................................................................ 78 10.1. Absolute value ............................................................................................. 78 10.2. Greatest common divisor........................................................................ 83 10.2.1. Euclid’s algorithm.............................................................................. -
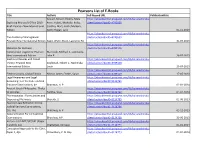
Pearsons List of E-Books
Pearsons List of E-Books Title Authors Full Record URL PublicationDate Grauer, Robert; Poatsy, Mary https://ebookcentral.proquest.com/lib/banarashinduu Exploring Microsoft Office 2010 Anne; Hulett, Michelle; Krebs, /detail.action?docID=4742025 Brief: Pearson New International Cynthia; Mast, Keith; Mulbery, Edition Keith; Hogan, Lynn 01-11-2013 https://ebookcentral.proquest.com/lib/banarashinduu The Anatomy Coloring Book: /detail.action?docID=4742630 Pearson New International Edition Kapit, Wynn; Elson, Lawrence M. 31-07-2013 https://ebookcentral.proquest.com/lib/banarashinduu Materials for Civil and /detail.action?docID=4789156 Construction Engineers: Pearson Mamlouk, Michael S.; Zaniewski, New International Edition John P. 26-07-2013 Electronic Devices and Circuit https://ebookcentral.proquest.com/lib/banarashinduu Theory: Pearson New Boylestad, Robert L.; Nashelsky, /detail.action?docID=4789158 International Edition Louis 23-07-2013 https://ebookcentral.proquest.com/lib/banarashinduu Electric Circuits, Global Edition Nilsson James; Riedel, Susan /detail.action?docID=4789159 17-05-2013 Legal Awareness and Legal https://ebookcentral.proquest.com/lib/banarashinduu Reasoning : For the CLAT and LLB /detail.action?docID=5124761 Entrance Examinations, 4e Bhardwaj, A. P. 01-01-2014 Ancient Greek Philosophy : Thales https://ebookcentral.proquest.com/lib/banarashinduu to Socrates Tankha, Vijay /detail.action?docID=5124762 01-01-2014 Pharmaceutics : Formulations and https://ebookcentral.proquest.com/lib/banarashinduu Dispensing Pharmacy Bharath, S. /detail.action?docID=5124765 01-06-2013 Pearson Legal Refresher for the https://ebookcentral.proquest.com/lib/banarashinduu Judicial Services Examinations, /detail.action?docID=5124766 2/e, The Bhardwaj, A. P. 01-12-2013 General English For Competitive https://ebookcentral.proquest.com/lib/banarashinduu Examinations Bhardwaj, A.P. -
11 De Febrero De 2010 SISTEMAS OPERATIVOS Nivel 5 Traducción
11 de febrero de 2010 SISTEMAS OPERATIVOS Nivel 5 Nivel de lenguaje orientado al problema Traducción (compilador) Nivel de lenguaje Nivel 4 ensamblador Traducción ensamblador Nivel de de Nivel 3 maquina del sistema operativo Interpretación parcial (S.O) Nivel de maquina Nivel 2 del sistema convencional Interpretación microprogramación Nivel 1 Nivel de microprogramació Los microprogramas son ejecutados directamente por la máquinan Nivel 0 Nivel de lógica digital Maquina Real Sistemas Operativos Como maquina ampliada: es el software cuya función es presentar al usuario el equivalente de una maquina virtual (N3) que sea más fácil de programar que el hardware implícito. Como manejo de recursos: Es el administrador de los recursos ofrecidos por el hardware para lograr un eficiente rendimiento de los mismos. Es un programa o conjunto de programas que actúan como intermediarios entre usuarios y el hardware del computador. Clase de sistemas operativos 17 de febrero Ejecución de una orden: EDIT FUENTE.TXT • Entrada de orden • Interprete de comandos y ejecución del programa • Verifica presencia de Edit en memoria sino lo pasa a un subsistema de archivos( tamaño) • El gestor de memoria asigna memoria • El cargador lo carga • Se crea el BCP • El BCP se matricula en la lista de procesos listos • El planificador elije el programa para ejecución • EDIT solicita al SO la apertura de fuente .txt • Se registra fuente.txt en archivos activos • Dialogo Teclado-pantalla • Termina: guarda, cierre, libera memoria Área de memoria de intercambio –Bufer Objetivos buscados del sistema operativo • Eficiencia: hacer las cosas con la menor cantidad de recursos • Robustez: Capaz de responder a todas las exigencias de los usuarios,” Aguante el uso y el abuso” • Escalabilidad: Capaz de atender volúmenes pequeños y grandes de trabajo, crece dependiendo de las exigencias. -

The Genesis of the Mainframe Bob O. Evans
The Genesis of the Mainframe Bob O. Evans 1 Introduction by Wilhelm G. Spruth In 1927 the German author Stefan Zweig published a short book labeled “Sternstunden der Menschheit” (world hours of mankind). In it he descripes 14 historical events that changed history forever. I have always believed the appearance of System /360 in 1964 has been such an event, changing the direction of the computer industry in more ways than anything else in the last 50 years. The design of the S/360 architecture is rightfully credited to Gene Amdahl, Gerry Blaauw and Fred Brooks. Bob O. Evans has been the IBM executive who made it happen. It is impossible to have met Bob O. Evans and not been impressed. He was forceful, decisive, intelligent, an excellent engineer with a broad vision, an uncanny capability to understand the most complex issues, and an outstanding leader for the people working for him. He also had an overpowering personality. I will be forever grateful for his guidance. In 2002 I learned Bob O. Evans had written his memoirs, had considered to publish them as a book, and had been adviced by his friends not to do so, because the text contained too much sensitive material. I contacted Evans and asked him if I could read the manuscript. He gracefully consented and e-mailed me a copy. Bob O. Evans died in 2004. I believe Bob O. Evans personal account on such a monumental event as the S/360 announcement should be made available. Thus in 2007 I asked his son Douglas B.