Announcement
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Startup Relationships Typologies 23 1.3.1 One-Off Events and Sharing Resources 24 1
POLITECNICO DI MILANO School of Industrial and Information Engineering Master of Science in Management Engineering CORPORATE-STARTUP COLLABORATION FOR DIGITAL INNOVATION: EMPIRICAL ANALYSIS ON THE ITALIAN MARKET Supervisor: Prof. Mariano CORSO Co-supervisor: Ing. Alessandra LUKSCH Master Graduation Thesis by: Francesco COSTA Matr. 872092 Filippo PASCAZIO Matr. 872018 Academic Year 2017/2018 Index Acknowledgements 4 Abstract 5 Executive summary 6 1. LITERATURE REVIEW 10 1.0 Review methodology 10 1.1 Disruptive Innovation & Digital Innovation 11 1.2 Introduction to Open Innovation 15 1.2.1 Startups as partners of innovation 21 1.3 Corporate - startup relationships typologies 23 1.3.1 One-off Events and Sharing Resources 24 1. One-off events 24 2. Sharing resources 26 1.3.2 Startup programs 27 1. Outside-in startup programs 28 2. Inside-out startup programs 29 1.3.3 Procurement & Partnerships 31 • Procurement 31 • Co-marketing arrangements: Co-branding 33 • Co-development 37 1.3.4 Business support: accelerators & incubators 39 1. Business incubators 40 2. Business accelerators 43 1.3.5 Investment (CVC) 45 1.3.6 Acquisitions 47 1. Acqui-hiring 48 1.4 Critical evaluation of the different relationships 50 1.4.1 One-off Events and Sharing Resources 50 1. One-off Events 50 2. Sharing resources 51 1.4.2 Startup programs 52 1. Outside-in startup programs 52 2. Inside-out startup programs 52 1.4.3 Procurement & Partnerships 53 • Procurement 53 • Co-marketing arrangements: Co-branding 54 • Co-development agreements 55 1.4.4 Accelerators & Incubators 56 1. Incubators 56 2. Accelerators 57 1.4.5 Investment (CVC) 57 1.4.6 Acquisitions 58 1. -

Huiswerk Linux: Sendmail Virtual User Instellen
Huiswerk Linux: Sendmail virtual user instellen Als professioneel administrator wil je zo min mogelijk gebruikers op je Linux machine hebben. Echte Linux gebruikers hebben login-rechten op jouw server en kunnen schade aanrichten op jouw machine. Het is in de meeste gevallen niet nodig om voor iedere klant een gebruikersaccount aan te maken. De meeste klanten willen alleen dat hun e-mail werkt. De opdracht voor deze week is: maak een virtual user voor het testdomein.nl aan. Over virtual users Het nadeel van het instellen van Virtual Hosts is dat alle gebruikers geldig zijn voor ieder e-mail domein dat je aanmaakt. Stel dat je een e-mail domein ( virtual host ) voor een klant aanmaakt, zodat zij e-mail kan ontvangen via dit domein. Dit betekent dat andere gebruikers ook e-mail kunnen ontvangen voor datzelfde domein. Dit veroorzaakt veel extra spam. Het handige van virtual users is dat ze alleen bestaan voor het domein waarvoor ze zijn aangemaakt. Het sudo mechanisme Het configureren van Linux doen we namens de super-user . We moeten daarom tijdelijk inloggen als Administrator. Cygwin gebruikers Andere Linux gebruikers Sudo voor Cygwin gebruikers: rechts-klik op het icoon van de Sudo voor gebruikers van andere Linux-versies ( Ubuntu , Cygwin terminal, en kies voor Als administrator uitvoeren . Lubuntu , Kubuntu , Android , Gentoo , Debian , etc): start een Zorg er ook voor dat de Sendmail daemon is gestart: terminal met de toetsencombinatie <Ctrl><Alt>-T. We gebruiken het commando sudo om in te loggen met het su service sendmail start (become Super User) commando. Daardoor blijven we ingelogd: sudo su Feature controleren Sendmail wordt geconfigureerd via het bestand /etc/mail/sendmail.cf . -

The Art of Unix Programming Next the Art of Unix Programming
The Art of Unix Programming Next The Art of Unix Programming Eric Steven Raymond Thyrsus Enterprises <[email protected]> Copyright © 2003 Eric S. Raymond Revision History Revision 0.0 1999 esr Public HTML draft, first four chapters only. Revision 0.1 16 November 2002 esr First DocBook draft, fifteen chapters. Released to Mark Taub at AW. Revision 0.2 2 January 2003 esr First manuscript walkthrough at Chapter 7. Released to Dmitry Kirsanov at AW production. Revision 0.3 22 January 2003 esr First eighteen-chapter draft. Manuscript walkthrough at Chapter 12. Limited release for early reviewers. Revision 0.4 5 February 2003 esr Release for public review. Revision 0.41 11 February 2003 esr Corrections and additions to Mac OS case study. A bit more about binary files as caches. Added cite of Butler Lampson. Additions to history chapter. Note in futures chapter about C and exceptions. Many typo fixes. Revision 0.42 12 February 2003 esr Add fcntl/ioctl to things Unix got wrong. Dedication To Ken Thompson and Dennis Ritchie, because you inspired me. Table of Contents Requests for reviewers and copy-editors Preface Who Should Read This Book How To Use This Book Related References Conventions Used In This Book Our Case Studies Author's Acknowledgements I. Context 1. Philosophy Culture? What culture? The durability of Unix The case against learning Unix culture What Unix gets wrong What Unix gets right Open-source software Cross-platform portability and open standards The Internet The open-source community Flexibility in depth Unix is fun to hack The lessons of Unix can be applied elsewhere Basics of the Unix philosophy Rule of Modularity: Write simple parts connected by clean interfaces. -

Targeting Plan for Attracting the Top Tech Companies to GM
Targeting Plan for Attracting the Top Tech Companies to GM Andrew Toolan, Head of Creative Digital and Tech, MIDAS September 2018 Contents Executive Summary……………………………………………………………………………………………………………….p1 Which Companies to Target ……………………………………………………………………………………………….p2 Top 21 Companies……………………………………………………………………………………………………………….p3 Type of Information Researched………………………………………………………………………………………….p4 Other Tech Targeting Campaigns……………………………………………………………………………………….p7 Planning Stages and Deadlines…..……………………………………………………………………………………….p9 Appendix: Company Profiles: GAFAM……………………………….………………………………………………………………….p10 Company Profiles: NATU…………………………….……………………………………………………………………….p31 Company Profiles: BAT…………………………….…………………………………………………………………………..p48 Company Profiles: Forbes 2018 List………………………………..…………………………………………………..p61 Executive Summary This paper sets out a plan for building more strategic relationships between Greater The new opportunities could come from innovation driven projects that address a company’s Manchester (GM) and the worlds largest tech companies. The aim is that closer collaboration focus, areas of interest and their challenges. It could also come via market opportunities by will ultimately lead to increased levels of partnerships, investment and job creation. partnering with GM and its various institutions on areas such as ‘digitisation and delivery of public services’. These opportunities will be positioned with the inward investment pitch but MIDAS have selected 21 companies that in 2018, were either the largest tech firms by market help GM stand out from our competitor locations by being more tailored to company needs. capitalisation, major brands or the key employers/job creators within their sector. In order to This Top 21 campaign will run in parallel (and compliment) other tech targeting campaigns develop a more strategic approach we need to get a better understanding of these such as the CDT Sub-Sector Campaign; NexGen Campaign and Emerging Tech/Data City companies in terms of their goals, challenges and areas of focus. -

The Healthy Programmer - Get Fit
Early praise for The Healthy Programmer Joe Kutner offers practical, readable, and well-researched advice for those who sit at a keyboard. I’ve incorporated his health-and-fitness regimen into my writing routine. ➤ Dr. Steve Overman Professor of Physical Education (retired), Jackson State University Health and programming should go together like a horse and carriage. You can’t have one without the other. In our sedentary office work, we often forget that an absence of health is as bad as a lack of programming skills. Joe points out a dozen areas where you and I can do better. Every office worker should read this book and self-reflect on health improvements. ➤ Staffan Nöteberg Author of Pomodoro Technique Illustrated This book introduced me to the term conditioned hypereating. It felt life-changing. Being aware of this has made it easier to experiment with smaller, less-ambitious changes that actually have a chance at succeeding. I’m very curious to see where this puts me a year from now. ➤ Katrina Owen Developer, Jumpstart Lab The Healthy Programmer is excellent. In many ways it’s a spiritual continuation of The Hacker’s Diet. ➤ Stephen Ball Senior Rails programmer, PhishMe, Inc. The Healthy Programmer Get Fit, Feel Better, and Keep Coding Joe Kutner The Pragmatic Bookshelf Dallas, Texas • Raleigh, North Carolina Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. -

INSIDE HORTON, KANSAS Special Tax Hometown of Section Kevin & Included in Angela Strube Holton Recorder Subscribers This Edition
SALUTE TON INSIDE HORTON, KANSAS Special tax Hometown of section Kevin & included in Angela Strube Holton Recorder subscribers this edition. for 30 years. CSerin te acson County Community for years See pages 8-9. Volume 153, Issue 6 HOLTON, KANSAS • Wednesday, January 22, 2020 14 Pages $1.00 Livestock Expo is Saturday In previous years, Holton veterinarian Tim Parks was one of the fea tured presenters at the Jackson Coun ty Livestock Association’s annual Livestock Exposition. This year, Parks — who owned and operated Heartland Veterinary Clinic in Holton from 1998 to 2015 — will be the featured speaker at the 35thannual Livestock Expo, set for this District court cases Saturday at the Northeast Kansas Heritage Complex south of down about 24 percent Holton. Doors to the Heritage By Brian Sanders Much of the decrease Complex’s exhibition hall will After seeing a dramatic in the 2019 total could open at 5 p.m. for the expo’s rise from 2017 to 2018 be found in the number steak dinner, which will be in the number of cases of criminal misdemeanor served from 5:30 p.m. to 7 p.m. handled in Jackson County cases — 187, which was The program will begin District Court, 2019 was less than half of the 2018 at 6 p.m. and feature Parks, a somewhat quieter year total of 411 misdemeanors representing Mer ck Animal in comparison, thanks in handled by court personnel. Health. The program will also part to sizable decreases Felony cases were up feature the announcement of in criminal misdemeanor slightly, from 294 in 2018 JCLA’s Distinguished Stockman filings and traffic tickets. -

Love Notes Fall 2012 | Volume 28
Love Notes Fall 2012 | volume 28 Latest News & Events A Publication of Ronald McDonald House Charities® of Tampa Bay, Inc. Inspiring family stories Love Notes • Fall 2012 1 2012 RMHC BOARD OF TRUSTEES OFFICERS Edward Ameen, Chairman Ana Wallrapp, President John Iwanicki, Vice-President Claudia Straw, Treasurer Diane Keane, Secretary Dan Honegger, Immediate Past President MEMBERS Pam Barber Message from the William Cassidy Kristy Chase-Tozer Executive Director Tina Dyakon Steve Eaves Brian Ford This year marks another milestone anniversary in our Chris Frost Ronald McDonald House program, the 20th anniversary of Steve Griggs the Tampa House. Since opening the doors in 1982, this Jeff Harring House has cared for 6,000 families whose children received Stacy Howell treatment at Tampa General, St. Joseph’s Children’s and Harry Hutt Shriners hospitals. 300 families stay at Tampa’s House George Meyer annually, greeted each day by one of the 100 volunteers Dan Paone Bonnie Patchen who give of their time to make this program possible. Tom Powers Richard Reeves We can never say enough about our volunteers. Last year, 341 volunteers greeted Bob Sanders families at our four Houses, facilitated registrations, helped with laundry and cleaning Don Schreyer chores, administrative duties, toy sorting, shopping, decorating, etc. With only a small Julie S. Stapf core staff of 21 for all four Houses & administration, we would not be able to operate Tom Waters 80 bedrooms at our Ronald McDonald Houses and care for the needs of our families Susan Wendt without them. Many special event volunteers help us raise the much-needed dollars Jill Wolf to operate, as well as hundreds of community groups and individuals who ensure our JANICE L. -

2020 Strategic Plan Ever Upward
2020 STRATEGIC PLAN EVER UPWARD WE ARE NEW YORK’S LAW SCHOOL SINCE 1891 Our Story Lower Manhattan is home to Wall Street, the global markets, tech companies, government agencies, high-profile courts, andjust one law school: New York Law School (NYLS). NYLS has been a downtown institution since its founding in 1891. Its original campus was the Equitable Building at 120 Broadway. Today, the School inhabits an iconic, high-tech glass building adjoined to two historic buildings at 185 West Broadway, a vibrant corner of Tribeca. Through economic highs and lows, and amid dramatic changes to the legal profession and legal education, NYLS has remained a destination for thousands of committed people from all means to pursue the study of law. And with the tools NYLS provided, graduates of the School have built modern New York. The School’s alumni include U.S. Senator and New Deal architect Robert F. Wagner Sr.; U.S. Supreme Court Justice John Marshall Harlan II; Emilio Nunez, New York’s first Latino judge; Julius Archibald, New York’s first African American State Senator; Barbara Watson, the first African American and first woman to serve as a U.S. Assistant Secretary of State; Hon. Judith Sheindlin (television’s “Judge Judy”); Maurice R. (Hank) Greenberg, Former Chairman and CEO of American International Group and Chairman and CEO of C.V. Starr & Company, Inc.; Zygi Wilf, owner of the Minnesota Vikings; Vincent Viola, owner of the Florida Panthers; Marc Lasry, Co-Founder and CEO of Avenue Capital Group and co-owner of the Milwaukee Bucks; Charles E. -
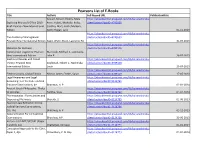
Pearsons List of E-Books
Pearsons List of E-Books Title Authors Full Record URL PublicationDate Grauer, Robert; Poatsy, Mary https://ebookcentral.proquest.com/lib/banarashinduu Exploring Microsoft Office 2010 Anne; Hulett, Michelle; Krebs, /detail.action?docID=4742025 Brief: Pearson New International Cynthia; Mast, Keith; Mulbery, Edition Keith; Hogan, Lynn 01-11-2013 https://ebookcentral.proquest.com/lib/banarashinduu The Anatomy Coloring Book: /detail.action?docID=4742630 Pearson New International Edition Kapit, Wynn; Elson, Lawrence M. 31-07-2013 https://ebookcentral.proquest.com/lib/banarashinduu Materials for Civil and /detail.action?docID=4789156 Construction Engineers: Pearson Mamlouk, Michael S.; Zaniewski, New International Edition John P. 26-07-2013 Electronic Devices and Circuit https://ebookcentral.proquest.com/lib/banarashinduu Theory: Pearson New Boylestad, Robert L.; Nashelsky, /detail.action?docID=4789158 International Edition Louis 23-07-2013 https://ebookcentral.proquest.com/lib/banarashinduu Electric Circuits, Global Edition Nilsson James; Riedel, Susan /detail.action?docID=4789159 17-05-2013 Legal Awareness and Legal https://ebookcentral.proquest.com/lib/banarashinduu Reasoning : For the CLAT and LLB /detail.action?docID=5124761 Entrance Examinations, 4e Bhardwaj, A. P. 01-01-2014 Ancient Greek Philosophy : Thales https://ebookcentral.proquest.com/lib/banarashinduu to Socrates Tankha, Vijay /detail.action?docID=5124762 01-01-2014 Pharmaceutics : Formulations and https://ebookcentral.proquest.com/lib/banarashinduu Dispensing Pharmacy Bharath, S. /detail.action?docID=5124765 01-06-2013 Pearson Legal Refresher for the https://ebookcentral.proquest.com/lib/banarashinduu Judicial Services Examinations, /detail.action?docID=5124766 2/e, The Bhardwaj, A. P. 01-12-2013 General English For Competitive https://ebookcentral.proquest.com/lib/banarashinduu Examinations Bhardwaj, A.P. -

Country Women Piracy Gambit
$6.95 (U.S.), $8.95 (CAN.), £5.50 (U.K.), 8.95 (EUROPE), Y2,500 (JAPAN) aw CL V) W z HI CCVR H 3 -DIGIT 9011 'IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIII I IIIIIII #90807GEE374EM002# BLBD 893 A06 B0093 001 MAR 04 2 MONTY GREENLY 3740 ELM AVE # A LONG BEACH CA 90807 -3402 111 UMW r THE INTERNATIONAL NEWSWEEKLY OF MUSIC, VIDEO AND HOME ENTERTAINMENT www.billboard.com JULY 5, 2003 Shal aTwzin at the HOT SPOTS recent Country Music Aw r Is. The Mercury Piracy Gambit artist is the lone female with a current top 10 country single. Raises Stakes RIAA Lawsuit Strategy Risks Consumer Backlash BY BILL HOLLAND and BRIAN GARRITY WASHINGTON, D.C.-The music 5 'Phoenix Rising industry's promised blitzkreig of law- suits against Internet song swappers- The new "Marry Potter and the including file-sharing teens-could Order of the Phoenix" flies out quickly become a legal quagmire. of retail outlets in record num- some critics warn. bers: 5 m Ilion in 24 hours. But with frustration levels running high after months of fruitless educa- tional campaigns, the industry is hell- bent on raising the stakes in the war on music pirates. As it launched its newest offensive June 25, the industry picked up a major ally in Congress. Rep. Lamar Smith, R- Texas, the anti -piracy cham- (Continued on page 74) Majors' Woes Continue 5 Jam On It Country Women Gov't Mule's Warren Haynes is Talks among the artists helping Along With Merger this summer's hot jam band Lose Hit Magic BY MATTHEW BENZ tour to jell. -

Retail and Hospitality
RETAIL AND HOSPITALITY In an increasingly competitive world, what is giving leading retailers an edge? Technology providers like Microsoft and its ecosys- tem of retail partners offer tools that drive end-to-end engagement with the customer – from initial acqui- sition, through strategic early engagement to highly personalised shopping experiences that secure long- term brand loyalty and ongoing repeat business. In the pages that follow we take a closer look at the latest innovations happening within the retail, consumer goods and hospitality markets. 149 FEATURE Defining the perfect customer journey Truly knowing and understanding your customers with the help of intelligent tools, such as artificial intelligence and machine learning, is the key to delivering the ultimate shopping experience in today’s retail environment, says Microsoft’s Cath Brands BY REBECCA GIBSON hy do some online shoppers click on personalised experience for those who shop in a t-shirt, spend a long time looking at the digital and physical stores.” Wit, but leave the retailer’s website emp- Defining the perfect customer experience is a ty-handed? Is it because the t-shirt is too expen- critical step for retailers like Fabletics if they want sive? Is there a low-quality product image and to differentiate their brand from the competition insufficient information to make an informed and achieve ongoing success – regardless of decision? Or is the check-out process too long whether they operate e-commerce sites, physical and complicated? stores or both. Online activewear retailer Fabletics has come “The ‘perfect’ shopping journey is different up with a unique way to answer these questions: for everyone, but all consumers expect it to be opening more than 24 physical stores across intuitive, seamless and frustration-free,” notes the US equipped with devices connected to Brands. -

The Corporate Esg Guide: a 360 View on the Current Landscape and Trends
THE CORPORATE ESG GUIDE: A 360 VIEW ON THE CURRENT LANDSCAPE AND TRENDS DR ELENA ZHARIKOVA AND PATRICK MITCHELL investor-update.com THE CORPORATE ESG GUIDE: A 360 VIEW ON THE CURRENT LANDSCAPE AND TRENDS Environmental, Social, and Governance (ESG) concerns are increasingly prominent in shareholders’ minds; however, the market is saturated with differing views and opinions spread across articles and papers focusing on individual topics. About Investor Update We have researched, analysed and summarised the latest Investor Update is made up of some the most experienced issues, attitudes and trends across the entire ESG community individuals in the shareholder intelligence space. to cut through the noise and enable you to make better We offer corporates and their advisors customised solutions informed decisions on this important topic in one, concise ranging from timely shareholder identification and investor document to be used as a guide and reference tool. targeting to comprehensive, in-depth perception studies, proxy solicitation and ESG benchmarking reporting. Part I serves as a corporate guide examining the main ESG For further information on our services, visit our website market trends. It outlines the main challenges investors and investor-update.com, call us on +44 20 3371 1177 or email us corporates encounter on their ESG journey and provides at [email protected]. an overview of current prominent global ESG standards, disclosure frameworks, and upcoming regulation. investor-update.com Part II presents the views from ESG specialists, drawn from 35 interviews with prominent investors, corporates, rating agencies and advisors. They shared their perspectives on the key ESG issues ranging from ESG ratings to investor engagement and the EU Taxonomy.