Space Details
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Component Design Recall: Problem with Subclassing
the gamedesigninitiative at cornell university Lecture 8 Component Design Recall: Problem with Subclassing Games have lots of classes Each game entity is different NPC Needs its own functionality (e.g. object methods) Human Orc Want to avoid redundancies Makes code hard to change Common source of bugs Human Human Orc Orc Warrior Archer Warrior Archer Might be tempted to subclass Common behavior in parents Redundant Behavior Specific behavior in children the gamedesigninitiative 2 Architecture Patterns at cornell university Recall: Problem with Subclassing Games have lots of classes Each game entity is different NPC Needs its own functionality (e.g. object methods) Warrior Archer Want to avoid redundancies Makes code hard to change Common source of bugs Human Orc Human Orc Warrior Warrior Archer Archer Might be tempted to subclass Common behavior in parents Redundant Behavior Specific behavior in children the gamedesigninitiative 3 Architecture Patterns at cornell university Alternative: Decorator Pattern New Functionality OriginalReference to Original Request Decorator Object Functionalitybase object Object the gamedesigninitiative 4 Architecture Patterns at cornell university Alternate: Delegation Pattern Original Reference to Request Delegate Object delegate Object Forward Request Inversion of the Decorator Pattern the gamedesigninitiative 5 Architecture Patterns at cornell university Issues with Static Typing Method in original class Original object class obj.request(arg1,…, argn) Original Reference to Request Delegate -

Learning Functional Programming in Scala Alvin Alexander
Learning Functional Programming in Scala Alvin Alexander A logical, step by step approach to learning functional programming Copyright Learning Functional Programming in Scala Copyright 2017 Alvin J. Alexander All rights reserved. No part of this book may be reproduced without prior written permission from the author. Disclaimer: This book is presented solely for educational purposes, and it’s also a work in progress. While best efforts have been used in prepar- ing this book, the author makes no representations or warranties of any kind and assume no liabilities of any kind with respect to the accuracy or completeness of the contents, and specifically disclaim any implied war- ranties of merchantability or fitness of use for a particular purpose. The author shall not be held liable or responsible to any person or entity with respect to any loss or incidental or consequential damages caused, or al- leged to have been caused, directly or indirectly, by the information or programs contained herein. Any use of this information is at your own risk. The advice and strategies contained herein may not be suitable for your situation. Version 0.1.1, published May 15, 2017 (The cover photo was taken on the Dalton Highway in Alaska, some- where between Fairbanks and Prudhoe Bay.) Contents 1 Changelog 1 2 Preface 3 3 Introduction (or, Why I Wrote This Book) 5 4 WhoThisBookisFor 11 5 Goals 15 6 Question Everything 23 7 Rules for Programming in this Book 33 8 One Rule for Reading this Book 39 9 What is “Functional Programming”? 41 10 What is This Lambda -

Game Architecture Revisited Recall: the Game Loop
the gamedesigninitiative at cornell university Lecture 8 Game Architecture Revisited Recall: The Game Loop Receive player input Process player actions Update 60 times/s Process NPC actions Interactions (e.g. physics) = 16.7 ms Cull non-visible objects Transform visible objects Draw Draw to backing buffer Display backing buffer the gamedesigninitiative 2 Architecture Revisited at cornell university The Game Loop Receive player input Process player actions Update Process NPC actions Interactions (e.g. physics) Almost everything is in loop Draw Except asynchronous actions Is enough for simple games How do we organize this loop? Do not want spaghetti code Distribute over programmers the gamedesigninitiative 3 Architecture Revisited at cornell university Model-View-Controller Pattern Controller Calls the • Updates model in methods of response to events • Updates view with model changes Model View • Defines/manages • Displays model the program data to the user/player • Responds to the • Provides interface controller requests for the controller the gamedesigninitiative 4 Architecture Revisited at cornell university The Game Loop and MVC Model: The game state Value of game resources Location of game objects Update View: The draw phase Rendering commands only Major computation in update Draw Controller: The update phase Alters the game state Vast majority of your code the gamedesigninitiative 5 Architecture Revisited at cornell university Application Structure Root Controller Ownership Subcontroller Subcontroller View Model Model -

Actors at Work Issue Date: 2016-12-15 Actors at Work Behrooz Nobakht
Cover Page The handle http://hdl.handle.net/1887/45620 holds various files of this Leiden University dissertation Author: Nobakht, Behrooz Title: Actors at work Issue Date: 2016-12-15 actors at work behrooz nobakht 2016 Leiden University Faculty of Science Leiden Institute of Advanced Computer Science Actors at Work Actors at Work Behrooz Nobakht ACTORS AT WORK PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit Leiden op gezag van de Rector Magnificus prof. dr. C. J. J. M. Stolker, volgens besluit van het College voor Promoties te verdedigen op donderdag 15 december 2016 klokke 11.15 uur door Behrooz Nobakht geboren te Tehran, Iran, in 1981 Promotion Committee Promotor: Prof. Dr. F.S. de Boer Co-promotor: Dr. C. P. T. de Gouw Other members: Prof. Dr. F. Arbab Dr. M.M. Bonsangue Prof. Dr. E. B. Johnsen University of Oslo, Norway Prof. Dr. M. Sirjani Reykjavik University, Iceland The work reported in this thesis has been carried out at the Center for Mathematics and Computer Science (CWI) in Amsterdam and Leiden Institute of Advanced Computer Science at Leiden University. This research was supported by the European FP7-231620 project ENVISAGE on Engineering Virtualized Resources. Copyright © 2016 by Behrooz Nobakht. All rights reserved. October, 2016 Behrooz Nobakht Actors at Work Actors at Work, October, 2016 ISBN: 978-94-028-0436-2 Promotor: Prof. Dr. Frank S. de Boer Cover Design: Ehsan Khakbaz <[email protected]> Built on 2016-11-02 17:00:24 +0100 from 397717ec11adfadec33e150b0264b0df83bdf37d at https://github.com/nobeh/thesis using: This is pdfTeX, Version 3.14159265-2.6-1.40.16 (TeX Live 2015/Debian) kpathsea version 6.2.1 Leiden University Leiden Institute of Advanced Computer Science Faculty of Science Niels Bohrweg 1 2333 CA and Leiden Contents I Introduction1 1 Introduction 3 1.1 Objectives and Architecture . -

Design Pattern Interview Questions
DDEESSIIGGNN PPAATTTTEERRNN -- IINNTTEERRVVIIEEWW QQUUEESSTTIIOONNSS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright © tutorialspoint.com Dear readers, these Design Pattern Interview Questions have been designed specially to get you acquainted with the nature of questions you may encounter during your interview for the subject of Design Pattern. As per my experience good interviewers hardly plan to ask any particular question during your interview, normally questions start with some basic concept of the subject and later they continue based on further discussion and what you answer: What are Design Patterns? Design patterns represent the best practices used by experienced object-oriented software developers. Design patterns are solutions to general problems that software developers faced during software development. These solutions were obtained by trial and error by numerous software developers over quite a substantial period of time. What is Gang of Four GOF? In 1994, four authors Erich Gamma, Richard Helm, Ralph Johnson and John Vlissides published a book titled Design Patterns - Elements of Reusable Object-Oriented Software which initiated the concept of Design Pattern in Software development. These authors are collectively known as Gang of Four GOF. Name types of Design Patterns? Design patterns can be classified in three categories: Creational, Structural and Behavioral patterns. Creational Patterns - These design patterns provide a way to create objects while hiding the creation logic, rather than instantiating objects directly using new opreator. This gives program more flexibility in deciding which objects need to be created for a given use case. Structural Patterns - These design patterns concern class and object composition. Concept of inheritance is used to compose interfaces and define ways to compose objects to obtain new functionalities. -

Design Specification for Delegation and Incentives in Cardano
Engineering Design Specification for Delegation and Incentives in Cardano–Shelley AN IOHK TECHNICAL REPORT Philipp Kant Lars Brunjes¨ Duncan Coutts [email protected] [email protected] [email protected] [email protected] April 11, 2019 Abstract This document describes the requirements and design for a delegation and incentives mechanism to be used in the Shelley release of Cardano. List of Contributors Lars Brunjes,¨ Jared Corduan, Duncan Coutts, Philipp Kant, Dimitris Karakostas, Aggelos Kiayias, Elias Koutsoupias, Mario Larangeira, Damian Nadales, Aikaterini-Panagiota Stouka. Contents 1 Purpose 4 2 Requirements 5 2.1 Functional Requirements . .5 2.1.1 Proof of Eligibility . .5 2.1.2 Visibility of Delegation on the Blockchain . .5 2.1.3 Restricting Chain Delegation . .5 2.1.4 Cheap Re-Delegation . .5 2.1.5 Neutral Addresses . .5 2.2 Security Requirements . .6 2.2.1 Sybil Attack Protection at Stake Pool Level . .6 2.2.2 Address Non-malleability . .6 2.2.3 Public Spending Keys Should not be Disclosed Prematurely . .6 2.2.4 Mitigate Key Exposure . .6 2.2.5 Handle Inactive Stake Pools . .6 2.2.6 Avoid Hard Transition . .6 2.2.7 Change Delegation Without Spending Key . .7 2.3 Non-functional Requirements . .7 2.3.1 Asymptotic space and time complexity . .7 2.3.2 Minimise economic attacks . .7 2.4 Requirements to Preserve Existing Features . .7 2.4.1 Master Recovery Key . .7 1 2.4.2 Address Recognition . .7 2.4.3 Wallet should be Runnable on Independent Devices . .7 2.4.4 Maintain Privacy . -

Five Considerations for Software Developers
FiveFive ConsiderationsConsiderations forfor SoftwareSoftware DevelopersDevelopers Kevlin Henney [email protected] Presented at Jfokus, Stockholm, 30th January 2008. Kevlin Henney [email protected] [email protected] Curbralan Ltd http://www.curbralan.com Voice: +44 117 942 2990 Fax: +44 870 052 2289 Agenda • Introduction • Consideration 1: Economy • Consideration 2: Visibility • Consideration 3: Spacing • Consideration 4: Symmetry • Consideration 5: Emergence • Outroduction 2 What general qualities in a software architecture help to promote its success? We can of course focus on fitness for purpose, cost of change, organisational acceptance, and so on, but are there broad considerations that can be kept in mind when looking at the structural and developmental side of an architecture? Those involved in software have a lot to keep in mind as they negotiate the worlds inside and outside of their code and the relationship between them. For those interested in improving the state of their art there are many (many) sources of specific recommendations they can use to sharpen their practice. This talk takes a step back from the busy, overpopulated and often overwhelming world of such recommendations to focus on five general considerations that can inform more detailed recommendations and specific decisions. Introduction StructuralSoftwareStructural engineering engineering engineering is is theis the the science science science an and dand art art art of of designingof designing designing and and and making, making, making, with with with economyeconomy and and elegance, elegance, buildings,applications, buildings, bridges, bridges, bridges, frameworks, frameworks, frameworks, and and and other other other similar similar similar structuresstructures so so that that they they can can safely safely resist resist the the forces forces to to which which they they may may be be subjected. -

Title: Foundation Patterns Authors: Dwight Deugo E-Mail: Deugo@Scs
Title: Foundation Patterns Authors: Dwight Deugo E-mail: [email protected] Address: School of Computer Science Carleton University 1125 Colonel By Drive Ottawa, Ontario, Canada, K1S 5B6 Telephone: (613) 520-2600 ext. 8438 (613) 520-4333 Fax: (613) 520-4334 Abstract: Many patterns depended on one important distinction: the distinction between an object's class and its type. For example, many patterns rely on interface inheritance, although, on examining their structures, most are described using implementation inheritance. The making of this implicit distinction gives evidence that there are patterns, fundamental to many, that live within other patterns and are at the foundation of good object-oriented principles. I give these patterns the name foundation patterns. I discuss two such foundation patterns: delegation and substitution, separating the two into their rightful positions, making clear what each patterns' role is in object-oriented design. Foundation Patterns Dwight Deugo [email protected] School of Computer Science Carleton University Introduction Although not mentioned, many patterns depend on one important distinction. This is the distinction between an object's class and its type. Stated another way, these patterns rely on interface inheritance rather than on implementation inheritance. Nevertheless, on examining their structures, most pattern descriptions use implementation inheritance. This is not surprising, since languages like Smalltalk and C++ do not explicitly support the notion of a type or a subtype within the language. Java is the exception to this, directly supporting interfaces and their inheritance, bringing attention to these well deserving topics. The making of this implicit distinction gives evidence that there are other patterns, fundamental to many, if not all patterns, which are either assumed and undocumented or still waiting to be discovered. -

Java Optimizations Using Bytecode Templates
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação Supervisor: Professor Doutor João Manuel Paiva Cardoso July 28, 2016 c Rubén Ramos Horta, 2016 Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação July 28, 2016 Resumo Aplicações móveis e embebidas funcionam em ambientes com poucos recursos e que estão sujeitos a constantes mudanças no seu contexto operacional. Estas características dificultam o desenvolvi- mento deste tipo de aplicações pois a volatilidade e as limitações de recursos levam muitas vezes a uma diminuição do rendimento e a um potencial aumento do custo computacional. Além disso, as aplicações que têm como alvo ambientes móveis e embebidos (por exemplo, Android) necessitam de adaptações e otimizações para fiabilidade, manutenção, disponibilidade, segurança, execução em tempo real, tamanho de código, eficiência de execução e também consumo de energia. Esta dissertação foca-se na otimização, em tempo de execução, de programas Java, com base na aplicação de otimizações de código baseadas na geração de bytecodes em tempo de execução, usando templates. Estes templates, fornecem geração de bytecodes usando informação apenas disponível em tempo de execução. Este artigo propõe uma estratégia para o desenvolvimento desses templates e estuda o seu impacto em diferentes plataformas. i ii Resumen Las aplicaciones móviles y embedded trabajan en entornos limitados de recursos y están sujetas a constantes cambios de escenario. Este tipo de características desafían el desarrollo de este tipo de aplicaciones en términos de volatibilidad y limitación de recursos que acostumbran a afec- tar al rendimiento y también producen un incremento significativo en el coste computacional. -

Überconf Westin Westminster June 19 - 22, 2012
ÜberConf Westin Westminster June 19 - 22, 2012 Tue, Jun. 19, 2012 Westminster I Westminster II Standley I Standley II Lake House Cotton Creek Meadowbrook I Meadowbrook II Windsor 8:00 - 9:00 AM EARLY REGISTRATION: PRE-CONFERENCE WORKSHOP ATTENDEES ONLY - WESTMINSTER BALLROOM FOYER 9:00 - 6:00 PM Programming iOS Workshop Android Web Application Domain-Driven Git Bootcamp with HTML 5 Christopher Judd Workshop Security Design (DDD) - An All-Day Venkat James Harmon Workshop Workshop Workshop Subramaniam Ken Sipe Paul Rayner Matthew McCullough 5:00 - 6:30 PM MAIN UBERCONF REGISTRATION - WESTMINSTER BALLROOM FOYER 6:30 - 8:30 PM DINNER/KEYNOTE - WESTMINSTER BALLROOM 3/4 7:30 - 8:30 PM Keynote: by Tim Berglund 8:30 - 10:30 PM OPENING NIGHT OUTDOOR RECEPTION - SOUTH COURTYARD ÜberConf Westin Westminster June 19 - 22, 2012 Wed, Jun. 20, 2012 Westminster I Westminster II Standley I Standley II Lake House Cotton Creek Meadowbrook I Meadowbrook II Windsor 7:00 - 8:00 AM 5K FUN RUN & POWER WALK - MEET IN LOBBY 7:30 - 8:30 AM BREAKFAST & LATE REGISTRATION - WESTMINSTER BALLROOM 3/4 8:30 - 10:00 AM Succeeding Scala for Professional Effective Spring NoSQL Build Lifecycle Developer guide OOP Principles The Who and with the Apache the Intrigued Javascript Workshop Smackdown 2012 Craftsmanship to the cloud Ken Sipe What of Agile - SOA stack Venkat development Craig Walls Tim Berglund Tools Pratik Patel Personas and Johan Edstrom Subramaniam for the Java Matthew Story Maps developer McCullough Nathaniel Schutta Peter Bell 10:00 - 10:30 AM MORNING BREAK 10:30 -
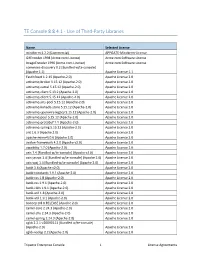
TE Console 8.8.4.1 - Use of Third-Party Libraries
TE Console 8.8.4.1 - Use of Third-Party Libraries Name Selected License mindterm 4.2.2 (Commercial) APPGATE-Mindterm-License GifEncoder 1998 (Acme.com License) Acme.com Software License ImageEncoder 1996 (Acme.com License) Acme.com Software License commons-discovery 0.2 [Bundled w/te-console] (Apache 1.1) Apache License 1.1 FastInfoset 1.2.15 (Apache-2.0) Apache License 2.0 activemQ-broker 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-camel 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-client 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-client 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-jms-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-kahadb-store 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-openwire-legacy 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemQ-spring 5.15.12 (Apache-2.0) Apache License 2.0 ant 1.6.3 (Apache 2.0) Apache License 2.0 apache-mime4j 0.6 (Apache 2.0) Apache License 2.0 avalon-framework 4.2.0 (Apache v2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 axis 1.4 [Bundled w/te-console] (Apache v2.0) Apache License 2.0 axis-jaxrpc 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 axis-saaj 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 batik 1.6 (Apache v2.0) Apache License 2.0 batik-constants 1.9.1 (Apache-2.0) Apache License 2.0 batik-css 1.8 (Apache-2.0) Apache License 2.0 batik-css 1.9.1 (Apache-2.0) Apache License 2.0 batik-i18n 1.9.1 (Apache-2.0) -
Resource-Oriented Computing W/ Netkernel
Resource-Oriented Computing w/ NetKernel : Software for the 21st Century Brian Sletten Zepheira, LLC [email protected] Speaker Qualifications Over 14 years of software development experience Has own software consulting company for design, mentoring, training and development Currently working in Semantic Web, AOP, Grid Computing, P2P and security consulting Pinky Committer Agenda What the heck is NetKernel? Why We Care NetKernel Overview NetKernel Languages Advanced Concepts Pinky What the heck is NetKernel? A micro-kernel based resource ecosystem built around the principles of REST, Unix Pipes and SOA Why We Care: The Simple Answer Most enterprise systems use XML and are built in Java and this is still too much of a pain Complicated Different Languages for different technologies Predicting scalability Why We Care : The Complicated Answer This is hard because of a general mismatch at the intersection of languages, data model, processing abstractions, architectural tiers, etc. Larger Trends Data formatted Code written 1970s 1980s 1990s 2000s NetKernel A Ground-Up Resource-oriented computing environment Modern, microkernel architecture Takes the best of REST, Unix Pipes, SOA Open Source w/ Dual License for non-open source uses Resource-Oriented Computing Everything is a Resource Everything is URI-Addressable (logical reference) “Computation” is the turning of logical resource references into physical representation Lossless conversion between representations REST Representational State Transfer Architectural style described in Roy Fielding’s