Some Human Factors in Codebreaking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?
Portland State University PDXScholar Young Historians Conference Young Historians Conference 2016 Apr 28th, 9:00 AM - 10:15 AM To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology? Hayley A. LeBlanc Sunset High School Follow this and additional works at: https://pdxscholar.library.pdx.edu/younghistorians Part of the European History Commons, and the History of Science, Technology, and Medicine Commons Let us know how access to this document benefits ou.y LeBlanc, Hayley A., "To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?" (2016). Young Historians Conference. 1. https://pdxscholar.library.pdx.edu/younghistorians/2016/oralpres/1 This Event is brought to you for free and open access. It has been accepted for inclusion in Young Historians Conference by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. To what extent did British advancements in cryptanalysis during World War 2 influence the development of computer technology? Hayley LeBlanc 1936 words 1 Table of Contents Section A: Plan of Investigation…………………………………………………………………..3 Section B: Summary of Evidence………………………………………………………………....4 Section C: Evaluation of Sources…………………………………………………………………6 Section D: Analysis………………………………………………………………………………..7 Section E: Conclusion……………………………………………………………………………10 Section F: List of Sources………………………………………………………………………..11 Appendix A: Explanation of the Enigma Machine……………………………………….……...13 Appendix B: Glossary of Cryptology Terms.…………………………………………………....16 2 Section A: Plan of Investigation This investigation will focus on the advancements made in the field of computing by British codebreakers working on German ciphers during World War 2 (19391945). -

Breaking the Enigma Cipher
Marian Rejewski An Application of the Theory of Permutations in Breaking the Enigma Cipher Applicaciones Mathematicae. 16, No. 4, Warsaw 1980. Received on 13.5.1977 Introduction. Cryptology, i.e., the science on ciphers, has applied since the very beginning some mathematical methods, mainly the elements of probability theory and statistics. Mechanical and electromechanical ciphering devices, introduced to practice in the twenties of our century, broadened considerably the field of applications of mathematics in cryptology. This is particularly true for the theory of permutations, known since over a hundred years(1), called formerly the theory of substitutions. Its application by Polish cryptologists enabled, in turn of years 1932–33, to break the German Enigma cipher, which subsequently exerted a considerable influence on the course of the 1939–1945 war operation upon the European and African as well as the Far East war theatres (see [1]–[4]). The present paper is intended to show, necessarily in great brevity and simplification, some aspects of the Enigma cipher breaking, those in particular which used the theory of permutations. This paper, being not a systematic outline of the process of breaking the Enigma cipher, presents however its important part. It should be mentioned that the present paper is the first publication on the mathematical background of the Enigma cipher breaking. There exist, however, several reports related to this topic by the same author: one – written in 1942 – can be found in the General Wladyslaw Sikorski Historical Institute in London, and the other – written in 1967 – is deposited in the Military Historical Institute in Warsaw. -

How I Learned to Stop Worrying and Love the Bombe: Machine Research and Development and Bletchley Park
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by CURVE/open How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park Smith, C Author post-print (accepted) deposited by Coventry University’s Repository Original citation & hyperlink: Smith, C 2014, 'How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park' History of Science, vol 52, no. 2, pp. 200-222 https://dx.doi.org/10.1177/0073275314529861 DOI 10.1177/0073275314529861 ISSN 0073-2753 ESSN 1753-8564 Publisher: Sage Publications Copyright © and Moral Rights are retained by the author(s) and/ or other copyright owners. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This item cannot be reproduced or quoted extensively from without first obtaining permission in writing from the copyright holder(s). The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the copyright holders. This document is the author’s post-print version, incorporating any revisions agreed during the peer-review process. Some differences between the published version and this version may remain and you are advised to consult the published version if you wish to cite from it. Mechanising the Information War – Machine Research and Development and Bletchley Park Christopher Smith Abstract The Bombe machine was a key device in the cryptanalysis of the ciphers created by the machine system widely employed by the Axis powers during the Second World War – Enigma. -

Tyringham Hall Tyringhamtyringham
Tyringham Hall TyringhamTyringham ... Buckinghamshire Hall Tyringham Hall by H. Hobson, March 1890 A magnificent Grade I Listed Soane Georgian Mansion with garden buildings and landscape by Lutyens 1 Tyringham Hall TyringhamTyringham ... Buckinghamshire Hall Central London: 45 miles Olney: 4.5 miles M1 (Junction 14): 5 miles Trains to London Euston from 35 minutes (Milton Keynes) International Airport: 25 miles (Luton) in all about 59.21 ACRES (23.966 HECTARES) Please note: Freehold 37.50 acres (15.18 hectares) Leasehold 21.71 acres (8.786 hectares) 4 Crispin Holborow Nick Ingle Savills London Savills Harpenden Tel: 0207 409 8881 Tel: 01582 465 002 Email: [email protected] Email: [email protected] Your attention is drawn to the Important Notice on the last page of the text. 5 6 The Bridge over the River Ouse The founTain To The fronT elevaTion of The house feaTuring Diana anD apollo 7 TyringhamTyRingham HallHALL SUMMARY Lutyens masterpieces and one of Europe’s largest reflecting pools. Tyringham Hall is a beautiful Grade I listed English stately home The majority of furniture and contents in the house, stable house built by Sir John Soane with gardens and garden buildings by Sir and grounds will be available by separate negotiation. Edwin Lutyens, one of only a handful of country houses that can lay claim to have been worked on by two of England’s greatest architects. SITUATION Tyringham Hall is situated in magnificent parkland setting The 18th century neo-classical villa includes 4 magnificently approximately 4.5 miles south of the picturesque market town of proportioned reception rooms, a kitchen, breakfast room and Olney and 5 miles from Junction 14 of the M1. -

Stdin (Ditroff)
Notes to accompany four Alan Turing videos 1. General The recent (mid-November 2014) release of The Imitation Game movie has caused the com- prehensive Alan Hodges biography of Turing to be reprinted in a new edition [1]. This biog- raphy was the basis of the screenplay for the movie. A more recent biography, by Jack Copeland [2], containing some new items of information, appeared in 2012. A more techni- cal work [3], also by Jack Copeland but with contributed chapters from other people, appeared in 2004. 2. The Princeton Years 1936–38. Alan Turing spent the years from 1936–38 at Princeton University studying mathematical logic with Prof. Alonzo Church. During that time Church persuaded Turing to extend the Turing Machine ideas in the 1936 paper and to write the results up as a Princeton PhD. You can now obtaing a copy of that thesis very easily [4] and this published volume contains extra chapters by Andrew Appel and Solomon Feferman, setting Turing’s work in context. (Andrew Appel is currently Chair of the Computer Science Dept. at Princeton) 3. Cryptography and Bletchley park There are many texts available on cryptography in general and Bletchley Park in particu- lar. A good introductory text for the entire subject is “The Code Book” by Simon Singh [5] 3.1. Turing’s Enigma Problem There are now a large number of books about the deciphering of Enigma codes, both in Hut 6 and Hut 8. A general overview is given by “Station X” by Michael Smith [6] while a more detailed treatment, with several useful appendices, can be found in the book by Hugh Sebag-Montefiore [7]. -
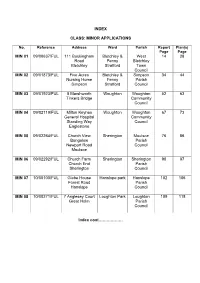
Index Class: Minor Applications Min 01 09/00637
INDEX CLASS: MINOR APPLICATIONS No. Reference Address Ward Parish Report Plan(s) Page Page MIN 01 09/00637/FUL 111 Buckingham Bletchley & West 14 28 Road Fenny Bletchley Bletchley Stratford Town Council MIN 02 09/01873/FUL Five Acres Bletchley & Simpson 34 44 Nursing Home Fenny Parish Simpson Stratford Council MIN 03 09/01923/FUL 8 Marshworth Woughton Woughton 52 63 Tinkers Bridge Community Council MIN 04 09/02119/FUL Milton Keynes Woughton Woughton 67 73 General Hospital Community Standing Way Council Eaglestone MIN 05 09/02264/FUL Church View Sherington Moulsoe 76 86 Bungalow Parish Newport Road Council Moulsoe MIN 06 09/02292/FUL Church Farm Sherington Sherington 90 97 Church End Parish Sherington Council MIN 07 10/00100/FUL Glebe House Hanslope park Hanslope 102 106 Forest Road Parish Hanslope Council MIN 08 10/00271/FUL 7 Anglesey Court Loughton Park Loughton 109 118 Great Holm Parish Council Index cont……………… CLASS: OTHER APPLICATIONS No. Reference Address Ward Parish Report Plan(s) Page Page OTH 01 09/01872/FUL 1 Rose Cottages Wolverton Wolverton & 122 130 Mill End Greenleys Wolverton Mill Town Council OTH 02 09/01907/FUL 6 Twyford Lane Walton park Walton 135 140 Walnut Tree parish Council OTH 03 09/02161/FUL 16 Stanbridge Stony Stony 143 148 Court Stratford Stratford Stony Stratford Town Council OTH 04 09/02217/FUL 220A Wolverton Linford North Great Linford 152 159 Road Parish Blakelands Council OTH 05 10/00117/FUL 98 High Street Olney Olney Town 162 166 Olney Council OTH 06 10/00049/FUL 63 Wolverton Newport Newport 168 174 Road Pagnell North Pagnell Newport Pagnell Town Council OTH 07 10/00056/FUL 24 Sitwell Close Newport Newport 177 182 Newport Pagnell Pagnell North Pagnell Town Council CLASS: OTHER APPLICATIONS – HOUSES IN MULTIPLE OCCUPATION No. -

THE-POLISH-TRACE-Ebook.Pdf
8 THE POLISH TRACE COMPOSED FROM COMMONLY AVAILABLE SOURCES BY LECH POLKOWSKI FOR IJCRS2017 FOREWORD It is a desire of many participants of conferences to learn as much as possible about the history and culture of he visited country and place and organizers try to satisfy this desire by providing excursions into attractive places and sites. IJCRS2017 also tries to take participants to historic sites of Warmia and Mazury and to show elements of local culture. As an innovation, we propose a booklet showing some achievements of Polish scientists and cryptographers, no doubt many of them are known universally, but some probably not. What bounds all personages described here is that they all suffered due to world wars, th efirst and the second. These wars ruined their homes, made them refugees and exiles, destroyed their archives and libraries, they lost many colleagues, friends and students but were lucky enough to save lives and in some cases to begin the career overseas. We begin with the person of Jan Czochralski, world famous metallurgist, discoverer of the technique of producing metal monocrystals `the Czochralski methode’ and inventor of duraluminum and the `bahnalloy’ who started his career and obtained its heights in Germany, later returned to Poland, became a professor at the Warsaw Polytechnical, played an important role in cultural life of Warsaw, lived in Warsaw through the second world war and the Warsaw Uprising of August-September 1944 and after the war was accused of cooperating ith occupying German forces and though judged innocent was literally erased from the public life and any information about him obliterated. -

Introduction to Public Key Cryptography and Clock Arithmetic Lecture Notes for Access 2010, by Erin Chamberlain and Nick Korevaar
1 Introduction to Public Key Cryptography and Clock Arithmetic Lecture notes for Access 2010, by Erin Chamberlain and Nick Korevaar We’ve discussed Caesar Shifts and other mono-alphabetic substitution ciphers, and we’ve seen how easy it can be to break these ciphers by using frequency analysis. If Mary Queen of Scots had known this, perhaps she would not have been executed. It was a long time from Mary Queen of Scots and substitution ciphers until the end of the 1900’s. Cryptography underwent the evolutionary and revolutionary changes which Si- mon Singh chronicles in The Code Book. If you are so inclined and have appropriate leisure time, you might enjoy reading Chapters 2-5, to learn some of these historical cryptography highlights: People came up with more complicated substitution ciphers, for example the Vigen`ere square. This Great Cipher of France baffled people for quite a while but a de- termined cryptographer Etienne Bazeries had a Eureka moment after three years of work, cracked the code, and possibly found the true identity of the Man in the Iron Mask, one of the great mysteries of the seventeeth century. Edgar Allan Poe and Sir Arthur Conan Doyle even dabbled in cryptanalysis. Secrecy was still a problem though because the key needed to be sent, and with the key anyone could encrypt and decrypt the messages. Frequency analysis was used to break all of these codes. In 1918 Scherbius invented his Enigma machine, but Alan Turing’s machine (the first computer?) helped in figuring out that supposedly unbreakable code, and hastened the end of the second World War. -

ANNEX a to ITEM 8 Central Bletchley Regeneration Strategy
ANNEX A TO ITEM 8 Central Bletchley Regeneration Strategy - Executive Summary Key Principles Use & activities Currently, Bletchley town centre remains comparatively unattractive to property developers and occupiers. The environment is out dated and creates a negative image for the town and its communities; reducing its ability to attract significant investment. This in turn has led to less people using the centre, creating lower expenditure and investment within the town. Bletchley needs to move forward from its existing primary role as a discount and value retailing location and strengthen its role as the second centre for the city of Milton Keynes. The challenge for the Framework is to create the conditions for Bletchley to promote itself as a place quite distinctive from the rest of Milton Keynes, yet complementary to CMK in its scale and richness of uses and activities. Achieving this will require the town to increase the diversity, quality and range of uses and activities offered in the centre. The Framework promotes the growth of key uses and activities including diversified mixed-use development; new retailing opportunities; residential town centre living; an evening economy with a range of restaurants, bars and cafes; employment opportunities to stimulate appropriate town centre employment; a new leisure centre and cultural and civic uses to fulfil Central Bletchley’s role as the city’s second centre. Access and Movement Pedestrian movement and cycle access throughout Central Bletchley is severely constrained by highly engineered road infrastructure, the railway station and sidings and through severance of Queensway caused by the Brunel Centre. Congested double roundabouts at Watling Street and Buckingham Road offer poor arrival points into the town and restrict car access into Bletchley. -

Polska Myśl Techniczna W Ii Wojnie Światowej
CENTRALNA BIBLIOTEKA WOJSKOWA IM. MARSZAŁKA JÓZEFA PIŁSUDSKIEGO POLSKA MYŚL TECHNICZNA W II WOJNIE ŚWIATOWEJ W 70. ROCZNICĘ ZAKOŃCZENIA DZIAŁAŃ WOJENNYCH W EUROPIE MATERIAŁY POKONFERENCYJNE poD REDAkcJą NAUkoWą DR. JANA TARCZYńSkiEGO WARSZAWA 2015 Konferencja naukowa Polska myśl techniczna w II wojnie światowej. W 70. rocznicę zakończenia działań wojennych w Europie Komitet naukowy: inż. Krzysztof Barbarski – Prezes Instytutu Polskiego i Muzeum im. gen. Sikorskiego w Londynie dr inż. Leszek Bogdan – Dyrektor Wojskowego Instytutu Techniki Inżynieryjnej im. profesora Józefa Kosackiego mgr inż. Piotr Dudek – Prezes Stowarzyszenia Techników Polskich w Wielkiej Brytanii gen. dyw. prof. dr hab. inż. Zygmunt Mierczyk – Rektor-Komendant Wojskowej Akademii Technicznej im. Jarosława Dąbrowskiego płk mgr inż. Marek Malawski – Szef Inspektoratu Implementacji Innowacyjnych Technologii Obronnych Ministerstwa Obrony Narodowej mgr inż. Ewa Mańkiewicz-Cudny – Prezes Federacji Stowarzyszeń Naukowo-Technicznych – Naczelnej Organizacji Technicznej prof. dr hab. Bolesław Orłowski – Honorowy Członek – założyciel Polskiego Towarzystwa Historii Techniki – Instytut Historii Nauki Polskiej Akademii Nauk kmdr prof. dr hab. Tomasz Szubrycht – Rektor-Komendant Akademii Marynarki Wojennej im. Bohaterów Westerplatte dr Jan Tarczyński – Dyrektor Centralnej Biblioteki Wojskowej im. Marszałka Józefa Piłsudskiego prof. dr hab. Leszek Zasztowt – Dyrektor Instytutu Historii Nauki Polskiej Akademii Nauk dr Czesław Andrzej Żak – Dyrektor Centralnego Archiwum Wojskowego im. -

STEM DISCOVERY: LONDON 8 Or 11 Days | England
® Learn more at Tour s for Girl Scouts eftours.com/girlscouts or call 800-457-9023 STEM DISCOVERY: LONDON 8 or 11 days | England Let STEM be your guide during your exploration of London. Uncover secret messages at Bletchley Park, the birthplace of modern information technology. Practice your sleuthing skills during a CSI-inspired forensics workshop. And plant your feet on two different hemispheres at the Royal Observatory in Greenwich, with the English capital as your backdrop. Make a special visit to Pax Lodge in Hampstead where you will participate in unique Girl Scout programming. EVERYTHING YOU GET: Full-time Tour Director Sightseeing: 2 sightseeing tours led by expert, licensed local guides (3 with extension) Entrances: London Eye, Science Museum/Natural History Museum, Tower of London, theater show, National Museum of Computing, Thames River Cruise, Royal Observatory; with extension: Louvre; Notre-Dame Cathedral Experiential learning: Forensics workshop, Stonehenge activities, Bletchley Park interactive workshop WAGGGS Centre visit: Pax Lodge All of the details are covered: Round-trip flights on major carriers; Comfortable motorcoach; Eurostar high-speed train with extension; 7 overnight stays in hotels with private bathrooms (9 with extension); European breakfast and dinner daily DAY 1: FLY OVERNIGHT TO ENGLAND DAY 2: LONDON – Meet your Tour Director at the airport in London, a city that has become one of the world’s great melting pots while maintaining a distinct character that’s all its own. – Take a walking tour of the city and ride the London Eye, a large Ferris wheel along the River Thames that offers panoramic views of the city. -

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6