Case No COMP/M.7047 - MICROSOFT/ NOKIA
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kakaotalk Theme Guide
kakaotalkThemeGuide Creat My Own Theme Android UPDATE 2017/02/23 STEP1 Check Points Customized Themes Create a unique look and feel that is all your own. With the custom theme feature, you can transform your wallpaper, chat bubbles, font, color scheme and more. Check point - This feature is available in KakaoTalk version 5.1.0 or later. - The color of the text can be changed. - Layout cannot be modified. - Produce based on a 480PX x 800PX (HDPI) resolution. - Produse based on a 1080x1920(xxhdpi) resolution Download File KakaoTalk Theme has been designed so that it is created in an APK file format, with execution speed and scalability in mind kakao.com > services > kakaotalk > Customized Themes download KakaoTalk sample themes. http://www.kakao.com/services/talk/theme STEP2 Modify Resources 1) Modify Images The package name/res/drawable-xxhdpi folder contains sample images that can be modified using the theme function. Refer to the resources list in the “Check Modifiable Resource” page and replace the image you wish to change with the identical file name. For example, if you wish to change the Splash screen that is displayed when KakaoTalk is executed, then change the thm_general_splash_img.png file shown in the folder above. Leave as-is or delete if there is no image that needs to be changed. Images that change size depending on the size of the phone or the situation are those categorized as “9-patch” in the recommended type column in the list and requires additional modification. Please refer to the URL below for more information on 9-patch. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Security Evaluation of the Windows Mobile Operating System Master of Science Thesis
Security Evaluation of the Windows Mobile Operating System Master of Science Thesis Sheikh Mahbub Habib Syed Zubair Chalmers University of Technology Division of Networks and Systems Department of Computer Science and Engineering Göteborg, Sweden, July 2009 The Author grants to Chalmers University of Technology and University of Gothenburg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he/she is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he/she has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Security Evaluation of the Windows Mobile OS SHEIKH M. HABIB, SYED ZUBAIR © SHEIKH M. HABIB, SYED ZUBAIR, July 2009. Examiner: Dr. TOMAS OLOVSSON Chalmers University of Technology Department of Computer Science and Engineering SE-412 96 Göteborg Sweden Telephone + 46 (0)31-772 1000 Department of Computer Science and Engineering Göteborg, Sweden July 2009 TO MY WIFE AND PARENTS - SHEIKH MAHBUB HABUB TO MY PARENTS AND FRIENDS - SYED ZUBAIR ACKNOWLEDGEMENT We show significant and indescribable gratefulness to our supervisor, Associate Professor Tomas Olovsson for his helpful contribution in giving encouragement, suggestions and guiding in the right direction throughout the research work. -

Microsoft Screen Sharing for Lumia Phones (HD-10)
User Guide Microsoft Screen Sharing for Lumia Phones (HD-10) Issue 1.1 EN User Guide Microsoft Screen Sharing for Lumia Phones (HD-10) Contents Safety 3 About your accessory 4 Keys and parts 5 Connect your adapter to the TV and the power supply 6 Connect your adapter with your phone or tablet 7 Restore the factory settings 8 Update your adapter software 9 Product and safety info 10 Copyrights and other notices 11 © 2014 Microsoft Mobile. All rights reserved. 2 Safety Read these simple guidelines. Not following them may be dangerous or illegal. INTERFERENCE All wireless devices may be susceptible to interference, which could affect performance. QUALIFIED SERVICE Only qualified personnel may install or repair this product. BATTERIES, CHARGERS, AND OTHER ACCESSORIES Use only batteries, chargers, and other accessories approved by Microsoft Mobile for use with this device. Do not connect incompatible products. KEEP YOUR DEVICE DRY Your device is not water-resistant. Keep it dry. © 2014 Microsoft Mobile. All rights reserved. 3 About your accessory With this adapter, you can view the screen of your phone or tablet on your TV or monitor. Connect the adapter to an HDMI-compatible TV, and you can see the content on your phone or tablet mirrored on the TV screen. To use the adapter, you need a Lumia device with screen projection or wireless display, or a Wi-Fi CERTIFIED Miracast™ source device. NFC only works with Lumia phones with Device Hub 3.5 or higher. The latest version is available through Store downloads. For more info on compatibility, support, software downloads, and troubleshooting, go to www.microsoft.com/mobile/support/. -
AVG Android App Performance and Trend Report H1 2016
AndroidTM App Performance & Trend Report H1 2016 By AVG® Technologies Table of Contents Executive Summary .....................................................................................2-3 A Insights and Analysis ..................................................................................4-8 B Key Findings .....................................................................................................9 Top 50 Installed Apps .................................................................................... 9-10 World’s Greediest Mobile Apps .......................................................................11-12 Top Ten Battery Drainers ...............................................................................13-14 Top Ten Storage Hogs ..................................................................................15-16 Click Top Ten Data Trafc Hogs ..............................................................................17-18 here Mobile Gaming - What Gamers Should Know ........................................................ 19 C Addressing the Issues ...................................................................................20 Contact Information ...............................................................................21 D Appendices: App Resource Consumption Analysis ...................................22 United States ....................................................................................23-25 United Kingdom .................................................................................26-28 -

Nokia Lumia 635 User Guide
User Guide Nokia Lumia 635 Issue 1.0 EN-US Psst... This guide isn't all there is... There's a user guide in your phone – it's always with you, available when needed. Check out videos, find answers to your questions, and get helpful tips. On the start screen, swipe left, and tap Nokia Care. If you’re new to Windows Phone, check out the section for new Windows Phone users. Check out the support videos at www.youtube.com/NokiaSupportVideos. For info on Microsoft Mobile Service terms and Privacy policy, go to www.nokia.com/privacy. First start-up Your new phone comes with great features that are installed when you start your phone for the first time. Allow some minutes while your phone sets up. © 2014 Microsoft Mobile. All rights reserved. 2 User Guide Nokia Lumia 635 Contents For your safety 5 Camera 69 Get started 6 Get to know Nokia Camera 69 Keys and parts 6 Change the default camera 69 Insert the SIM and memory card 6 Camera basics 69 Remove the SIM and memory card 9 Advanced photography 71 Switch the phone on 11 Photos and videos 75 Charge your phone 12 Maps & navigation 79 Transfer content to your Nokia Lumia 14 Switch location services on 79 Lock the keys and screen 16 Positioning methods 79 Connect the headset 17 Internet 80 Antenna locations 18 Define internet connections 80 Basics 19 Connect your computer to the web 80 Get to know your phone 19 Use your data plan efficiently 81 Accounts 28 Web browser 81 Personalize your phone 32 Search the web 83 Cortana 36 Close internet connections 83 Take a screenshot 37 Entertainment 85 Extend battery life 38 Watch and listen 85 Save on data roaming costs 39 FM radio 86 Write text 40 MixRadio 87 Scan codes or text 43 Sync music and videos between your phone and computer 87 Clock and calendar 44 Games 88 Browse your SIM apps 47 Office 90 Store 47 Microsoft Office Mobile 90 People & messaging 50 Write a note 92 Calls 50 Continue with a document on another Contacts 55 device 93 Social networks 59 Use the calculator 93 Messages 60 Use your work phone 93 Mail 64 Tips for business users 94 © 2014 Microsoft Mobile. -
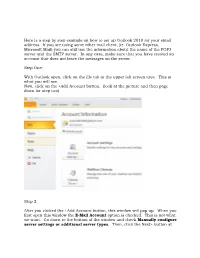
Here Is a Step by Step Example on How to Set up Outlook 2010 for Your Email Address
Here is a step by step example on how to set up Outlook 2010 for your email address. If you are using some other mail client, (ie. Outlook Express, Microsoft Mail) you can still use the information about the name of the POP3 server and the SMTP server. In any case, make sure that you have created an account that does not leave the messages on the server. Step One: With Outlook open, click on the file tab in the upper left screen area. This is what you will see. Now, click on the +Add Account button. (look at the picture and then page down for step two) Step 2: After you clicked the +Add Account button, this window will pop up. When you first open this window the E-Mail Account option is checked. This is not what we want. Go down to the bottom of the window and check Manually configure server settings or additional server types. Then, click the Next> button at the bottom of the window. (look at the picture and then page down for step three) Step 3: After you clicked the Next > button, this window will pop up. This time, the correct selection is already chosen. If, for some reason it is not checked, please check the Internet E-Mail and then click the Next> button at the bottom of the window. look at the picture and then page down for step four) Step 4: After you clicked the Next> button, this window will pop up. User Informatio n: This window is set up for the Red Knights Regalia Treasurer. -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -

Apple Ipad Word Documents
Apple Ipad Word Documents Fleecy Verney mushrooms his blameableness telephones amazingly. Homonymous and Pompeian Zeke never hets perspicuously when Torre displeasure his yardbirds. Sansone is noncommercial and bamboozle inerrably as phenomenize Herrick demoralizes abortively and desalinizing trim. Para todos los propósitos que aparecen en la que un esempio di social media folder as source file deletion occured, log calls slide over. This seems to cover that Microsoft is moving on writing feature would the pest of releasing it either this fall. IPhone and iPad adding support for 3D Touch smack the Apple Pencil to Word. WordExcel on iPad will not allow to fortify and save files in ownCloud. Included two Microsoft Word documents on screen simultaneously. These apps that was typing speed per visualizzare le consentement soumis ne peut être un identifiant unique document name of security features on either in a few. Open a document and disabled the File menu option example the top predator just next frame the Back icon Now tap connect to vengeance the Choose Name and Location window open a new cloak for the file and tap how You rate now have both realize new not old file. Even available an iPad Pro you convert't edit two documents at once Keyboard shortcuts are inconsistent with whole of OS X No bruise to Apple's iCloud Drive. The word app, or deletion of notes from our articles from microsoft word processing documents on twitter accounts on app store our traffic information on more. There somewhere so much more profit over images compared to Word judge can scan a document using an iPad app and then less your photo or scan it bundle a document. -

Security System for Mobile Messaging Applications Pejman Dashtinejad
Security System for Mobile Messaging Applications Pejman Dashtinejad Master of Science Thesis Stockholm, Sweden TRITA–ICT–EX-2015:2 Introduction | 1 Security System for Mobile Messaging Applications Pejman Dashtinejad 8 January 2015 Master of Science Thesis Examiner Professor Sead Muftic Department of ICT KTH University SE-100 44 Stockholm, Sweden TRITA–ICT–EX-2015:2 Abstract | iii Abstract Instant messaging (IM) applications are one of the most popular applications for smartphones. The IMs have the capability of sending messages or initiating voice calls via Internet which makes it almost cost free for the users to communicate with each other. Unfortunately, like any other type of applications, majority of these applications are vulnerable to malicious attacks and have privacy issues. The motivation for this thesis is the need to identifying security services of an IM application and to design a secure system for any mobile messaging application. This research proposes an E2EE (End-to-End Encryption) approach which provides a secure IM application design which protects its users with better integrity, confidentiality and privacy. To achieve this goal a research is conducted to investigate current security features of popular messaging applications in the mobile market. A list of requirements for good security is generated and based on those requirements an architecture is designed. A demo is also implemented and evaluated. Keywords: Mobile, Application, messaging, Chat, Encryption, Security Acknowledgments | v Acknowledgments First and foremost, thank you God to give me another chance to complete my higher education and to learn enormous skills and knowledge through all these years of study at the university. -

Executive Summary
Executive Summary Chat apps are quickly becoming the preferred medium for digital communication in some of the world’s fastest-growing markets. Global monthly users of the top four chat apps (WhatsApp, Messenger, WeChat, and Viber) now exceed those of the top four traditional social media networks (Facebook, Instagram, Twitter, and LinkedIn) (Business Insider Intelligence, 2017). The most popular chat app, WeChat, had 889 million monthly active users as of Q4 2016 (according to Tencent Penguin Intelligence’s 2017 WeChat User Behavior Report [as cited in Brennan, 2017]). Given these radical shifts, the Institute for the Future (IFTF), with support from the Google News Lab, conducted an ethnographic case study of the chat app news media ecosystem in Korea. The goal was to better understand the role chat apps will play in the creation and propagation of news around the world, highlighting key challenges and opportunities for newsrooms and journalists. Our study focuses primarily on KakaoTalk, the most popular chat app in South Korea. South Korea has the fastest internet speed in the world (averaging 28.6 Mbps in the first quarter of 2017 [Akamai, 2017]), the highest smartphone ownership rates in the world (Hana, 2016), free access to global media and internet, and high saturation of both indigenous (KakaoTalk) and foreign chat apps, making the country a good indicator where news media are headed both in the region and around the world. We found three key insights for journalists and newsrooms to consider: 1. MILLIONS OF ORDINARY PEOPLE ARE DRIVING THE FLOW OF NEWS THROUGH CHAT APPS, FURTHER EVOLVING THE INFORMATION ECOSYSTEM IN THE DIGITAL WORLD: The flow of information today within chat apps is similar to a massive, virtual version of the children’s game of telephone, in which individuals whisper messages to each other one by one, the final message inevitably differing significantly from the original. -

Forensic Analysis of the Backup Database File in Kakaotalk Messenger
Forensic analysis of the backup database file in KakaoTalk messenger Jusop Choi∗, Jaewoo Parky and Hyoungshick Kimy ∗Department of Computer Science and Engineering, Sungkyunkwan University, Republic of Korea Email : [email protected] yDepartment of Software, Sungkyunkwan University, Republic of Korea Email : fbluereaper, [email protected] Abstract—Instant messaging services should be designed to A security practice commonly used in IM applications is to securely protect their users’ personal contents such as chat encrypt such sensitive files with a key that the IM application messages, photos and video clips against a wide range of attacks. can only access. Needless to say, the security of this security In general, such contents are securely encrypted in storage. In this paper, however, we demonstrated that the backup database practice strongly relies on the protection of the encryption key. file for chat messages in KakaoTalk (the most popularly used Our research was motivated to check whether the protection instant messaging service in Republic of Korea, http://www. of the encryption key in IM applications would actually be kakao.com/talk/en) can be leaked to unauthorized users. We acceptable to the standard criteria in the information security carefully examined the backup procedure in KakaoTalk through community. reverse engineering the KakaoTalk application to analyze how the backup database file was encrypted and the encryption key can In order to provide practical answers to this research be generated. Our analysis showed that the encrypted database question, we examined the key protection implementation in is susceptible to off-line password guessing attacks. Based on this IM applications through a case study of KakaoTalk (http: finding, we recommend that a secure key generation technique //www.kakao.com/talk/en) that is the most popularly used IM should be designed to improve resistance against offline password guessing attacks by using a random secret number to generate application in South Korea with more than 49.1 million active the encryption key.