Application-Specific Key Management Guidance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hello, and Welcome to This Presentation of the STM32MP1 Hash Processor
Hello, and welcome to this presentation of the STM32MP1 hash processor. 1 Hash peripheral is in charge of efficient computing of message digest. A digest is a fixed-length value computed from an input message. A digest is unique - it is virtually impossible to find two messages with the same digest. The original message cannot be retrieved from its digest. Hash digests and Hash-based Message Authentication Code (HMAC) are widely used in communication since they are used to guarantee the integrity and authentication of a transfer. 2 HASH1 is a secure peripheral (under ETZPC control through ETZPC_DECPROT0 bit 8) while HASH2 is a non secure peripheral. HASH1 instance can be allocated to: • The Arm® Cortex®-A7 secure core to be controlled in OP-TEE by the HASH OP-TEE driver or • The Arm® Cortex® -A7 non-secure core for using in Linux® with Linux Crypto framework HASH2 instance can be allocated to the Arm® Cortex®-M4 core to be controlled in the STM32Cube MPU Package using the STM32Cube HASH driver. HASH1 instance is used as boot device to support binary authentication. 3 The hash processor supports widely used hash functions including Message Digest 5 (MD5), Secure Hash Algorithm SHA-1 and the more recent SHA-2 with its 224- and 256-bit digest length versions. A hash can also be generated with a secrete-key to produce a message authentication code (MAC). The processor supports bit, byte and half-word swapping. It supports also automatic padding of input data for block alignment. The processor can be used in conjunction with the DMA for automatic processor feeding. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Downloaded on 2017-02-12T13:16:07Z HARDWARE DESIGNOF CRYPTOGRAPHIC ACCELERATORS
Title Hardware design of cryptographic accelerators Author(s) Baldwin, Brian John Publication date 2013 Original citation Baldwin, B.J., 2013. Hardware design of cryptographic accelerators. PhD Thesis, University College Cork. Type of publication Doctoral thesis Rights © 2013. Brian J. Baldwin http://creativecommons.org/licenses/by-nc-nd/3.0/ Embargo information No embargo required Item downloaded http://hdl.handle.net/10468/1112 from Downloaded on 2017-02-12T13:16:07Z HARDWARE DESIGN OF CRYPTOGRAPHIC ACCELERATORS by BRIAN BALDWIN Thesis submitted for the degree of PHD from the Department of Electrical Engineering National University of Ireland University College, Cork, Ireland May 7, 2013 Supervisor: Dr. William P. Marnane “What I cannot create, I do not understand” - Richard Feynman; on his blackboard at time of death in 1988. Contents 1 Introduction 1 1.1 Motivation...................................... 1 1.2 ThesisAims..................................... 3 1.3 ThesisOutline................................... 6 2 Background 9 2.1 Introduction.................................... 9 2.2 IntroductiontoCryptography. ...... 10 2.3 MathematicalBackground . ... 13 2.3.1 Groups ................................... 13 2.3.2 Rings .................................... 14 2.3.3 Fields.................................... 15 2.3.4 FiniteFields ................................ 16 2.4 EllipticCurves .................................. 17 2.4.1 TheGroupLaw............................... 18 2.4.2 EllipticCurvesoverPrimeFields . .... 19 2.5 CryptographicPrimitives&Protocols -

On the NIST Lightweight Cryptography Standardization
On the NIST Lightweight Cryptography Standardization Meltem S¨onmez Turan NIST Lightweight Cryptography Team ECC 2019: 23rd Workshop on Elliptic Curve Cryptography December 2, 2019 Outline • NIST's Cryptography Standards • Overview - Lightweight Cryptography • NIST Lightweight Cryptography Standardization Process • Announcements 1 NIST's Cryptography Standards National Institute of Standards and Technology • Non-regulatory federal agency within U.S. Department of Commerce. • Founded in 1901, known as the National Bureau of Standards (NBS) prior to 1988. • Headquarters in Gaithersburg, Maryland, and laboratories in Boulder, Colorado. • Employs around 6,000 employees and associates. NIST's Mission to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life. 2 NIST Organization Chart Laboratory Programs Computer Security Division • Center for Nanoscale Science and • Cryptographic Technology Technology • Secure Systems and Applications • Communications Technology Lab. • Security Outreach and Integration • Engineering Lab. • Security Components and Mechanisms • Information Technology Lab. • Security Test, Validation and • Material Measurement Lab. Measurements • NIST Center for Neutron Research • Physical Measurement Lab. Information Technology Lab. • Advanced Network Technologies • Applied and Computational Mathematics • Applied Cybersecurity • Computer Security • Information Access • Software and Systems • Statistical -

TS 102 176-1 V2.1.1 (2011-07) Technical Specification
ETSI TS 102 176-1 V2.1.1 (2011-07) Technical Specification Electronic Signatures and Infrastructures (ESI); Algorithms and Parameters for Secure Electronic Signatures; Part 1: Hash functions and asymmetric algorithms 2 ETSI TS 102 176-1 V2.1.1 (2011-07) Reference RTS/ESI-000080-1 Keywords e-commerce, electronic signature, security ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable Document Format (PDF). In case of dispute, the reference shall be the printing on ETSI printers of the PDF version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: http://portal.etsi.org/chaircor/ETSI_support.asp Copyright Notification No part may be reproduced except as authorized by written permission. -

<Document Title>
TLS Specification for Storage Systems Version 1.0.1 ABSTRACT: This document specifies the requirements and guidance for use of the Transport Layer Security (TLS) protocol in conjunction with data storage technologies. The requirements are intended to facilitate secure interoperability of storage clients and servers as well as non-storage technologies that may have similar interoperability needs. This document was developed with the expectation that future versions of SMI-S and CDMI could leverage these requirements to ensure consistency between these standards as well as to more rapidly adjust the security functionality in these standards. This document has been released and approved by the SNIA. The SNIA believes that the ideas, methodologies and technologies described in this document accurately represent the SNIA goals and are appropriate for widespread distribution. Suggestion for revision should be directed to http://www.snia.org/feedback/. SNIA Technical Position November 20, 2014 USAGE The SNIA hereby grants permission for individuals to use this document for personal use only, and for corporations and other business entities to use this document for internal use only (including internal copying, distribution, and display) provided that: 1. Any text, diagram, chart, table or definition reproduced shall be reproduced in its entirety with no alteration, and, 2. Any document, printed or electronic, in which material from this document (or any portion hereof) is reproduced shall acknowledge the SNIA copyright on that material, and shall credit the SNIA for granting permission for its reuse. Other than as explicitly provided above, you may not make any commercial use of this document, sell any or this entire document, or distribute this document to third parties. -
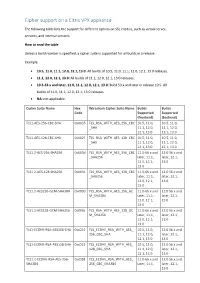
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Guidelines on Cryptographic Algorithms Usage and Key Management
EPC342-08 Version 7.0 4 November 2017 [X] Public – [ ] Internal Use – [ ] Confidential – [ ] Strictest Confidence Distribution: Publicly available GUIDELINES ON CRYPTOGRAPHIC ALGORITHMS USAGE AND KEY MANAGEMENT Abstract This document defines guidelines on cryptographic algorithms usage and key management. Document Reference EPC342-08 Issue Version 7.0 Date of Issue 22 November 2017 Reason for Issue Maintenance of document Produced by EPC Authorised by EPC Document History This document was first produced by ECBS as TR 406, with its latest ECBS version published in September 2005. The document has been handed over to the EPC which is responsible for its yearly maintenance. DISCLAIMER: Whilst the European Payments Council (EPC) has used its best endeavours to make sure that all the information, data, documentation (including references) and other material in the present document are accurate and complete, it does not accept liability for any errors or omissions. EPC will not be liable for any claims or losses of any nature arising directly or indirectly from use of the information, data, documentation or other material in the present document. Conseil Européen des Paiements AISBL– Cours Saint-Michel 30A – B 1040 Brussels Tel: +32 2 733 35 33 – Fax: +32 2 736 49 88 Enterprise N° 0873.268.927 – www.epc-cep.eu – [email protected] © 2016 Copyright European Payments Council (EPC) AISBL: Reproduction for non-commercial purposes is authorised, with acknowledgement of the source Table of Content MANAGEMENT SUMMARY ............................................................. 5 1 INTRODUCTION .................................................................... 7 1.1 Scope of the document ...................................................... 7 1.2 Document structure .......................................................... 7 1.3 Recommendations ............................................................ 8 1.4 Implementation best practices ......................................... -

Recommendation for Applications Using Approved Hash Algorithms
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-107 Title: Recommendation for Applications Using Approved Hash Algorithms Publication Date(s): February 2009 Withdrawal Date: August 2012 Withdrawal Note: SP 800-107 is superseded in its entirety by the publication of SP 800-107 Revision 1 (August 2012). Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: NIST Special Publication 800-107 Revision 1 Title: Recommendation for Applications Using Approved Hash Algorithms Author(s): Quynh Dang Publication Date(s): August 2012 URL/DOI: http://dx.doi.org/10.6028/NIST.SP.107r1 Additional Information (if applicable) Contact: Computer Security Division (Information Technology Lab) Latest revision of the SP 800-107 Rev. 1 (as of August 12, 2015) attached publication: Related information: http://csrc.nist.gov/ Withdrawal N/A announcement (link): Date updated: ƵŐƵƐƚϭϮ, 2015 NIST Special Publication 800-107 Recommendation for Applications Using Approved Hash Algorithms Quynh Dang Computer Security Division Information Technology Laboratory C O M P U T E R S E C U R I T Y February 2009 U.S. Department of Commerce Otto J. Wolff, Acting Secretary National Institute of Standards and Technology Patrick D. Gallagher, Deputy Director NIST SP 800-107 Abstract Cryptographic hash functions that compute a fixed- length message digest from arbitrary length messages are widely used for many purposes in information security. This document provides security guidelines for achieving the required or desired security strengths when using cryptographic applications that employ the approved cryptographic hash functions specified in Federal Information Processing Standard (FIPS) 180-3. -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session. -

TLS Security Upgrade Effective Thursday, May 3, 2018
TLS Security Upgrade Effective Thursday, May 3, 2018 You May Need to Upgrade Your Browser/Operating System to Ensure Online and Mobile Banking Functionality. Apple Bank is informing you of a change to our security protocol. We will be officially retiring TLS 1.0 security protocol support on all of our services and upgrading to TLS 1.1 or higher to align with industry best practices and ensure that your data continues to be highly secure. TLS stands for “Transport Layer Security.” It is a protocol that provides privacy and data integrity between two communicating applications. It’s the most widely deployed security protocol used today, and is used for web browsers and other applications that require data to be securely exchanged over a network. On or before May 3, 2018, we will disable the TLS 1.0 encryption protocol, which may prevent users like you from accessing some or all of your online and mobile banking functionality. This means that you may need to upgrade your browser/operating system to disable TLS 1.0 and use TLS 1.1 or higher. This security upgrade will not affect you in any other way. We want to make this process as smooth as possible for you with specific instructions below. Our primary goal for users is to maintain the highest possible security standards and help keep your data secure. Depending on your browser/device, you may need to upgrade to the following versions that support TLS 1.1 or higher. Browser • Microsoft Internet Explorer (IE): version 11 and higher • Microsoft Edge: all versions • Mozilla Firefox: version -
BIP Note 18 Binding Implementation Practice (BIP) Note
Superannuation Transaction Network BIP Note 18 Binding Implementation Practice (BIP) Note Title: TLS Configuration and Cryptography Date: 10 Nov 201 5 Standards Version: 1.0 Scope [ x ] transport layer Status: [ ] Draft [ ] message payload [x ] Ratified [ x ] security Live Date: 25 February 2016 On this date this BIP note will be binding on all participants 1. Change This document sets requirements for SSL/TLS configuration within the STN. 2. Reason for Change Secure message exchange within the STN is fully dependent on HTTPS protocol (HTTP over TLS). SSL 3.0 has existed for at least 15 years. It was superseded by TLS 1.0 which was in turn replaced by TLS 1.1 and TLS 1.2. Cryptography standards used in SSL and early versions of TLS are now deprecated and do not provide sufficient level of security. Clause 6.6(a) of Superannuation Data and Gateway Services Standards for Gateway Operators transaction within the Superannuation Transaction Network document requires STN gateways to use “a minimum level of protection of Transport Layer Security (TLS) of version 1.1 or above”. Majority of the STN gateways supports TLS versions 1.0 through 1.2 at the server side (some gateways still support SSL 3.0). However, only a few gateways support modern TLS versions at the client side resulting majority of transactions within the STN being sent through TLS 1.0 channel. In order to eliminate vulnerabilities of the obsolete SSL/TLS protocols, SSL 3.0 and TLS 1.0 must be completely disabled. Mozilla Foundation recommends not to include TLS 1.0 into “Modern” configuration set for web- servers and limits its usage only for backward-compatibility purposes (given that STN is P2P network with a limited number of participants, backward-compatibility issue is not relevant).