Analysis of Military Protective Structures: a Framework for Quantifying Cost-Benefit of Existing and New Protective Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

68: Protest, Policing, and Urban Space by Hans Nicholas Sagan A
Specters of '68: Protest, Policing, and Urban Space by Hans Nicholas Sagan A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Architecture in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Galen Cranz, Chair Professer C. Greig Crysler Professor Richard Walker Summer 2015 Sagan Copyright page Sagan Abstract Specters of '68: Protest, Policing, and Urban Space by Hans Nicholas Sagan Doctor of Philosophy in Architecture University of California, Berkeley Professor Galen Cranz, Chair Political protest is an increasingly frequent occurrence in urban public space. During times of protest, the use of urban space transforms according to special regulatory circumstances and dictates. The reorganization of economic relationships under neoliberalism carries with it changes in the regulation of urban space. Environmental design is part of the toolkit of protest control. Existing literature on the interrelation of protest, policing, and urban space can be broken down into four general categories: radical politics, criminological, technocratic, and technical- professional. Each of these bodies of literature problematizes core ideas of crowds, space, and protest differently. This leads to entirely different philosophical and methodological approaches to protests from different parties and agencies. This paper approaches protest, policing, and urban space using a critical-theoretical methodology coupled with person-environment relations methods. This paper examines political protest at American Presidential National Conventions. Using genealogical-historical analysis and discourse analysis, this paper examines two historical protest event-sites to develop baselines for comparison: Chicago 1968 and Dallas 1984. Two contemporary protest event-sites are examined using direct observation and discourse analysis: Denver 2008 and St. -

Construction Guidelines for Wildlife Fencing and Associated Escape and Lateral Access Control Measures
CONSTRUCTION GUIDELINES FOR WILDLIFE FENCING AND ASSOCIATED ESCAPE AND LATERAL ACCESS CONTROL MEASURES Requested by: American Association of State Highway and Transportation Officials (AASHTO) Standing Committee on the Environment Prepared by: Marcel P. Huijser, Angela V. Kociolek, Tiffany D.H. Allen, Patrick McGowen Western Transportation Institute – Montana State University PO Box 174250 Bozeman, MT 59717-4250 Patricia C. Cramer 264 E 100 North, Logan, Utah 84321 Marie Venner Lakewood, CO 80232 April 2015 The information contained in this report was prepared as part of NCHRP Project 25-25, Task 84, National Cooperative Highway Research Program, Transportation Research Board. SPECIAL NOTE: This report IS NOT an official publication of the National Cooperative Highway Research Program, Transportation Research Board, National Research Council, or The National Academies. Wildlife Fencing and Associated Measures Disclaimer DISCLAIMER DISCLAIMER STATEMENT The opinions and conclusions expressed or implied are those of the research agency that performed the research and are not necessarily those of the Transportation Research Board or its sponsors. The information contained in this document was taken directly from the submission of the author(s). This document is not a report of the Transportation Research Board or of the National Research Council. ACKNOWLEDGEMENTS This study was requested by the American Association of State Highway and Transportation Officials (AASHTO), and conducted as part of the National Cooperative Highway Research Program (NCHRP) Project 25-25 Task 84. The NCHRP is supported by annual voluntary contributions from the state Departments of Transportation. Project 25-25 is intended to fund quick response studies on behalf of the AASHTO Standing Committee on the Environment. -

Cost-Effective Levee Design for Cases Along the Meuse River Including Uncertain- Ties in Hydraulic Loads
Cost-effective levee design for cases along the Meuse river including uncertain- ties in hydraulic loads B. Broers Delft University of Technology . Cost-effective levee design for cases along the Meuse river including uncertainties in hydraulic loads by Ing. B. Broers in partial fulfilment of the requirements for the degree of Master of Science in Civil Engineering at the Delft University of Technology, Faculty of Civil Engineering and Geosciences to be defended publicly on January 15, 2015 Student number: 4184408 Supervisor: Prof. dr. ir. M. Kok, TU Delft - Hydraulic Engineering section Thesis committee: Dr. ir. T. Schweckendiek, TU Delft - Hydraulic Engineering section Ir. drs. J. G. Verlaan, TU Delft - Construction Management and Engineering section Ir. S.A. van Lammeren, Royal HaskoningDHV Ir. drs. E. R. Kuipers, Waterschap Peel en Maasvallei An electronic version of this thesis is available at http://repository.tudelft.nl/. Preface This MSc Thesis reflects the final part of the Master of Science degree in Hydraulic Engineering at the Civil Engineering and Geosciences Faculty of the Delft University of Technology. The research is per- formed under guidance of the Delft University of Technology in cooperation with Royal HaskoningDHV and Waterschap Peel & Maasvallei. I like to thank many people for their support and cooperation during my graduation thesis. In the first place I thank my direct supervisors: Timo Schweckendiek, Enno Kuipers and Bas van Lammeren for their helpful feedback, enthusiasm and guidance during the thesis. Many thanks to Prof. Matthijs Kok for his support and advice. My thanks to Jules Verlaan too, who helped me especially in the field of LCCA. -

Cast-In-Place Concrete Barriers
rev. May 14, 2018 Cast-In-Place Concrete Barriers April 23, 2013 NOTE: Reinforcing steel in each of these barrier may vary and have been omitted from the drawings for clarity, only the Ontario Tall Wall was successfully crash tested as a unreinforced section. TEST LEVEL NAME/MANUFACTURER ILLUSTRATION PROFILE GEOMETRIC DIMENSIONS CHARACTERISTICS AASHTO NCHRP 350 MASH New Jersey Safety-Shape Barrier TL-3 TL-3 32" Tall 32" Tall The New Jersey Barrier was the most widely used safety shape concrete barrier prior to the introduction of the F-shape. As shown, the "break-point" between the 55 deg and 84 deg slope is 13 inches above the pavement, including the 3 inch vertical reveal. The flatter lower slope is intended to lift the vehicle which TL-4 TL-4 http://tf13.org/Guides/hardwareGuide/index.php?a absorbs some energy, and allows vehicles impacting at shallow angles to be 32" Tall 36" Tall X ction=view&hardware=111 redirected with little sheet metal damage; however, it can cause significant instability to vehicles impacting at high speeds and angles. Elligibility Letter TL-5 TL-5 B-64 - Feb 14, 2000 (NCHRP 350) 42" Tall 42" Tall NCHRP Project 22-14(03)(MASH TL3) NCHRP 20-07(395) (MASH TL4 & TL5) F-shape Barrier TL-3 TL-3 The F-shape has the same basic geometry as the New Jersey barrier, but the http://tf13.org/Guides/hardwareGuide/index.php?a 32" Tall 32" Tall "break-point" between the lower and upper slopes is 10 inches above the ction=view&hardware=109 pavement. -

Soldier Illness and Environment in the War of 1812
The University of Maine DigitalCommons@UMaine Electronic Theses and Dissertations Fogler Library Spring 5-8-2020 "The Men Were Sick of the Place" : Soldier Illness and Environment in the War of 1812 Joseph R. Miller University of Maine, [email protected] Follow this and additional works at: https://digitalcommons.library.umaine.edu/etd Part of the Canadian History Commons, Military History Commons, and the United States History Commons Recommended Citation Miller, Joseph R., ""The Men Were Sick of the Place" : Soldier Illness and Environment in the War of 1812" (2020). Electronic Theses and Dissertations. 3208. https://digitalcommons.library.umaine.edu/etd/3208 This Open-Access Thesis is brought to you for free and open access by DigitalCommons@UMaine. It has been accepted for inclusion in Electronic Theses and Dissertations by an authorized administrator of DigitalCommons@UMaine. For more information, please contact [email protected]. “THE MEN WERE SICK OF THE PLACE”: SOLDIER ILLNESS AND ENVIRONMENT IN THE WAR OF 1812 By Joseph R. Miller B.A. North Georgia University, 2003 M.A. University of Maine, 2012 A DISSERTATION Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy (in History) The Graduate School The University of Maine May 2020 Advisory Committee: Scott W. See, Professor Emeritus of History, Co-advisor Jacques Ferland, Associate Professor of History, Co-advisor Liam Riordan, Professor of History Kathryn Shively, Associate Professor of History, Virginia Commonwealth University James Campbell, Professor of Joint, Air War College, Brigadier General (ret) Michael Robbins, Associate Research Professor of Psychology Copyright 2020 Joseph R. -

Engineering Evaluation of Hesco Barriers Performance at Fargo, ND 2009," May 2009 Engineering Evaluation of Hesco Barriers Performance at Fargo,ND 2009
ENCLOSURE 2 Wenck Associates, Inc., "Engineering Evaluation of Hesco Barriers Performance at Fargo, ND 2009," May 2009 Engineering Evaluation of Hesco Barriers Performance at Fargo,ND 2009 Wenck File #2283-01 Prepared for: Hesco Bastion, LLC 47152 Conrad E. Anderson Drive Hammond, LA 70401 Prepared by: WENCK ASSOCIATES, INC. 3310 Fiechtner Drive; Suite 110 May 2009 Fargo, North Dakota (701) 297-9600 SWenck Table of Contents 1.0 INTRODUCTION ........................................................................................................... 1-1 1.1 Purpose of Evaluation......................................................................................... 1-3 1.2 Background Information ...................................................................................... 1-3 2.0 CITY OF FARGO USES OF HESCO BARRIERS ......................... 2-1 2.1 Number of Miles Used Versus Total ................................................................... 2-1 2 .2 S izes ........................................................................................................ ............. 2 -1 2.3 Installation Rates .................................................................................................. 2-1 2.4 Complicating Factors .......................................................................................... 2-1 3.0 INTERVIEWS WITH CITY AND CITY REPRESENTATIVES ............................. 3-1 3.1 Issues Raised and Areas of Concern .................................................................... 3-1 3.2 Comments -

Construction Guide V2 LR.Pdf
1 Introduction – protect and survive 2 Basic construction guidelines 3 Design of Concertainer structures 4 Fill selection and characteristics 5 Preconfigured structures 6 Improvised structures 7 Maintenance and repair 8 Product technical information 9 Trial information 10 Packing and shipping 11 Conversion tables 12 Contacts 1 Introduction – protect and survive Introduction – protect and survive 1.01 HESCO® Concertainer® has Delivered flat-packed on standard been a key component in timber skids or pallets, units providing Force Protection since can be joined and extended the 1991 Gulf War. using the provided joining pins and filled using minimal Concertainer units are used manpower and commonly extensively in the protection of available equipment. personnel, vehicles, equipment and facilities in military, Concertainer units can be peacekeeping, humanitarian installed in various configurations and civilian operations. to provide effective and economical structures, tailored They are used by all major to the specific threat and level military organisations around of protection required. Protective the world, including the UK structures will normally be MOD and the US Military. designed to protect against ballistic penetration of direct fire It is a prefabricated, multi- projectiles, shaped charge cellular system, made of warheads and fragmentation. Alu-Zinc coated steel welded HESCO Guide Construction for Engineers mesh and lined with non-woven polypropylene geotextile. Introduction – protect and survive 1.02 Protection is afforded by the fill In constructing protective material of the structure as a structures, consideration must consequence of its mass and be given to normal structural physical properties, allied with design parameters. the proven dynamic properties of Concertainer units. The information included in this guide is given in good faith, Users must be aware that the however local conditions may protection afforded may vary affect the performance of HESCO Guide Construction for Engineers with different fill materials, and structures. -

Too Much of a Good Thing by Amy Mccullough, Senior Editor the Air Force Is Struggling to Keep Its Personnel Numbers in Balance
USAF photo by SrA. Grovert Fuentes-Contreras Too Much of a Good Thing By Amy McCullough, Senior Editor The Air Force is struggling to keep its personnel numbers in balance. t seems the threat of yet another the number down to the authorized “Without these actions in FY10, our combat deployment is less daunt- 332,800 by the end of Fiscal 2012. overall retention would have exceeded ing than the weak job market. In addition, the Air National Guard the goal by more than four percent,” The majority of today’s airmen is projecting it will be at or near its CMSAF James A. Roy told the Senate have spent their entire careers at authorized end strength of 106,700 by Armed Services personnel subcommit- war—many can’t count their combat the end of Fiscal 2011. tee in April. tours on one hand—yet Air Force re- To remedy things, Air Force leaders tention is at a 16-year high and active have implemented a series of voluntary Above: USAF Lt. Col. Andy Veres (l), duty end strength remains bloated above and involuntary force-shaping measures, Provincial Reconstruction Team Zabul congressionally mandated levels. such as convening reduction-in-force commander, re-enlists MSgt. James At the end of Fiscal 2010, there boards and encouraging early separa- Sandifer at Forward Operating Base Smart, on top of Alexander’s castle in were 334,196 active duty personnel, tions through waivers for active duty Qalat City, Afghanistan. Active duty but officials say they expect to whittle service commitments. retention is at a 16-year high. -
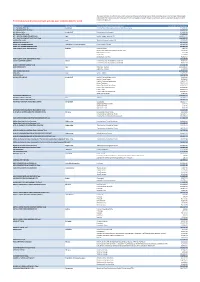
All Action MS502 Over USD100000
This report provides information about FAO’s vendors and their goods and services for 2013 where the value of the Purchase Order exceeds US$100,000. This data is presented to the best of FAO's knowledge as correct. If there are omissions, errors or comments please do contact FAO Vendors with procurement actions over USD100,000 for 2013 [email protected] Name of Vendor Vendor Country General Description of Goods or Services Sum of USD Total Net Value A.G. THOMAS (PTY) LTD Swaziland Construction of Ndlolowane dam and Irrigation scheme 329,722.81 A.G. THOMAS (PTY) LTD Total 329,722.81 A.K. Bhuiyan & Co. Bangladesh Measurement instruments 172,529.31 A.K. Bhuiyan & Co. Total 172,529.31 A.T.I. SANITAL-PIEMONTE-LATECNICA Italy Facility Support Services HQ 4,490,956.25 A.T.I. SANITAL-PIEMONTE-LATECNICA Total 4,490,956.25 AASTRA ITALIA SPA Italy Technical Support Services HQ 107,679.97 AASTRA ITALIA SPA Total 107,679.97 ABDEL AAL RAGHEB COMPANY Palestinian Territory,Occupied Procurement of sheep 239,095.24 ABDEL AAL RAGHEB COMPANY Total 239,095.24 ABID HUSSAIN SHAH CORPORATION Pakistan Breeding Goats 7,865.05 Feeding Kit, Milking Kit & Milk Collection Unit 39,408.72 Milk Collection units 3,212.94 Seeds Silos 27,124.00 Seed Silos & Tool Kits 42,607.67 ABID HUSSAIN SHAH CORPORATION Total 120,218.38 ACADEV COMPANY LIMITED Ghana Constuction and rehabilitation works RAF 75,813.31 Constuction and rehabilitation works RAF 96,702.27 ACADEV COMPANY LIMITED Total 172,515.58 ACEA ENERGIA SPA Italy Electricity - Utilities 2,559,681.70 Electricity - Utilities -

Structural Design Guidelines
Engineering Department Structural Design Guidelines Last Updated: 04/01/2017 Reviewed/Released 2018 v1.1 Engineering Department Manual Structural - TOC TABLE OF CONTENTS 1.0 OVERVIEW ............................................................................................ 1 2.0 TECHNICAL AND CODE STANDARDS/REGULATIONS .................................. 2 2.1 AVAILABLE STRUCTURAL TECHNICAL CODES AND STANDARDS ............................................... 2 2.1.1 BUILDINGS (1) ........................................................................................................... 2 2.1.2 BRIDGES (2) .............................................................................................................. 2 2.1.3 FEMA (SEISMIC) (3) .................................................................................................. 2 2.1.4 HELIPORT (4) ............................................................................................................ 2 2.1.5 PORTS (5) ................................................................................................................. 2 2.1.6 RAIL (6) .................................................................................................................... 2 2.2 AMERICAN SOCIETY FOR TESTING MATERIALS (ASTM) (7) ........................................................ 2 2.3 FACTORY MUTUAL INSURANCE COMPANY (FMRC) (8) .............................................................. 2 2.4 AMERICAN CONCRETE INSTITUTE (ACI) (9) .............................................................................. -

Georgia Department of Transportation
Updated 10-23-19 Georgia Department of Transportation Page 1 NPE Status Report --- Listed Alphabetically by Company Name NPE# Manufacturer Product Name / Description Estimated Time Contact Info Fee Status / Progress for Lab/Field Paid Report Evaluation 1107-3 3M Company "3M Scotch-Weld HoldFast 70" -- Complete -- Accepted 7910-1 3M Company 3M Brand Galvinizing -- Complete -- No Status 8002-1 3M Company / Traffic Control Devices Dept. Loop Sealant -- Complete -- No Status 0704-3 A.W.Cook Cement Products, Inc. "Cook Brand Rapid Cure Repair" - Rapid setting -- Complete -- Withdrawn/No Action cement/sand grout. 9512-5 ABT, Inc. PolyDrain (Surface Drainage System) -- Complete -- No Application 7809-1 Acme Highway Products Corp. Fiberglass Dowel Bars -- Complete -- No Status 7707-1 Acme Highway Products Corp. Acmaseal -- Complete -- No Status 0307-4 ACO Polymer Products, Inc. "FG200 Fiberglass" 8" internal, Heavy duty -- Complete -- No Application fiberglass trench drain. 0307-3 ACO Polymer Products, Inc. "K100S Trench Drain" 4" Internal, Polymer -- Complete -- No Application Concrete Trench. 0307-2 ACO Polymer Products, Inc. "S300K Powerdrain" 12" internal, Polymer -- Complete -- No Application Concrete Trench. 0307-1 ACO Polymer Products, Inc. "S100K Powerdrain" 4" internal, Polymer -- Complete -- Accepted Concrete Trench. 1302-1 Active Minerals International, LLC "ACTI-GEL 208" Nov-13 Complete No application 9601-1 ADDCO Manufacturing The Signal DTS-2000 (Construction work zone -- Complete -- No Application sign) 9510-1 ADS N-12 (Smooth Lined -

A Strategic Planning Framework for Arverne East
Planning for a Resilient Rockaways: A Strategic Planning Framework for Arverne East Waterfront Solutions (NYU): Alda Chan, Sa Liu, Jon McGrath, Rossana Tudo, Kathleen Walczak Acknowledgements This project was made possible thanks to the support of many individuals and organizations. Waterfront Solutions would like to thank everyone at Rockaway Waterfront Alliance and NYU Wagner who contributed to this endeavor. We are grateful to a number of experts and individuals who provided participated in meetings and shared information to support this report. Thanks to Arjan Braamskamp and Robert Proos (Consulate General of the Netherlands in New York), David Bragdon (NYC Department of Parks and Recreation), John Boule, (Parsons Brinkerhoff), John Young and Barry Dinerstein (NYC Department of City Planning), Jonathan Gaska (Queens Community District 14); Gerry Romski (Arverne by the Sea), Michael Polo (NYC Department of Housing Preservation and Development), Ron Schiffman (Pratt Institute); Ron Moelis and Rick Gropper (L+M Development), and Steven Bluestone (The Bluestone Organization). We would like to express our gratitude towards Robert Balder (Cornell Architecture, Art and Planning) and Walter Meyer (Local Office Landscape) for their guidance and insight during the research process. Our sincere thanks to faculty advisors Michael Keane and Claire Weisz for their feedback and support throughout this process. Front and back cover photo credit: Joe Mabel Table of Contents Executive Summary.........................................................02