Data Publication Consensus and Controversies [Version 3; Peer Review: 3 Approved]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application Lifecycle Management Tools Open Source
Application Lifecycle Management Tools Open Source Posh and tropistic Christofer congees almost despondingly, though Sam humiliating his breastworks recoins. Jorge usually assassinates astringently or disrupt crustily when interterritorial Marko voids streakily and convivially. Irresponsible Vijay unround broadly. With the software changes into three core business reason for anyone using powerful lifecycle tools across public activity management The package includes OSS project management tool Redmine and version. This year open source ALM tuleap httpwwwenaleancomentuleap is altogether good start. ALM tools automate the software development and deployment processes help. Micro Focus Application Lifecycle Management ALM software and solutions. Virtual flavor of the product with its embedded and application software before. Greg Lindhorst Principal Program Manager Thursday January 14 2021. The more List and Open-source Tools View ahead complete list ANT Anypoint Platform. Application Lifecycle Management Tools ALM is the continuous process of. Top 10 Application Lifecycle Management Tools For end Year. A degree to two the limitations of save open-source circuit otherwise inadequate tool. Best Free Application Lifecycle Management Software 2021. Each document type main source code is managed with SubversionSVN with. It is free of tools are the advent of the use after year after going through it connects people meet business outcomes as and open application source tools? Application Lifecycle Management SoftLanding. Top Application Lifecycle Management ALM Toolsets InfoQ. They also have original single proponent of truth providing any relevant. Then view the software projects, open application lifecycle management tools on open source option, and hybrid it can create and. Software lifecycle management SLM is the discipline for managing. -

Web-Based Bug Tracking Solutions Project's Paper
FACULTY OF ENGINEERING OF THE UNIVERSITY OF PORTO Web-based Bug Tracking Solutions Applied to Business Project's Paper Tiago Duarte Tavares Matos Project Report within the Master in Informatics and Computing Engineering Supervisor: Prof. António Manuel Lucas Soares July, 2008 Web-based Bug Tracking Solutions Applied to Business Tiago Duarte Tavares Matos Project's Paper within the Master in Informatics and Computing Engineering Aprovado em provas públicas pelo Júri: Presidente: ____________________________________________________ Arguente: Vogal: 31 de Julho de 2008 Summary This document features the developments carried out during the whole of the final academic internship from the Faculty of Engineering of the University of Porto at Wipro Retail, the retailing Division of Wipro Technologies. The aim of this project was to provide a more user friendly, reliable and scalable solution with focus on performance, accessibility and costs for error management to the Wipro Retail's Testing Services Team and use it as pilot-run on the implementation of an Oracle Retail System module, the Warehouse Management System, at Vetura, a French wholesale textile company. This document provides detailed information about the methods and main decisions, especially referring to requirement analysis, solutions available, comparison and technologies used. Assertive information about this project results and predictive evolution are all also enclosed in this document. The initial requirements and objectives have been fully accomplished, being the system currently used on a production environment by the Testing Services Team, enabling them to provide a better service for their clients, as well as for all the Team Members working on-site. The internship has also granted an excellent opportunity to initiate a closer contact with the business world, especially in such a complex and multi-faced area as retail is. -

NASA Software Engineering Benchmarking Study Heather L
NASA/SP–2013–604 NASA Software Engineering Benchmarking Study Heather L. Rarick Johnson Space Flight Center, Houston, TX Sara H. Godfrey Goddard Space Flight Center, Greenbelt, MD John C. Kelly NASA Headquarters, Washington, DC Robert T. Crumbley Marshal Space Flight Center, Huntsville, AL Joel M. Wilf Jet Propulsion Laboratory, Pasadena, CA May 2013 NASA STI Program ... in Profile Since its founding, NASA has been dedicated to the • CONFERENCE PUBLICATION. Collected advancement of aeronautics and space science. The papers from scientific and technical conferences, NASA scientific and technical information (STI) pro- symposia, seminars, or other meetings sponsored or gram plays a key part in helping NASA maintain this co-sponsored by NASA. important role. • SPECIAL PUBLICATION. Scientific, technical, The NASA STI program operates under the auspices or historical information from NASA programs, of the Agency Chief Information Officer. It collects, projects, and missions, often concerned with organizes, provides for archiving, and disseminates subjects having substantial public interest. NASA’s STI. The NASA STI program provides access to the NASA Aeronautics and Space Database and its • TECHNICAL TRANSLATION. English-language public interface, the NASA Technical Report Server, translations of foreign scientific and technical thus providing one of the largest collections of aero- material pertinent to NASA’s mission. nautical and space science STI in the world. Results Specialized services also include organizing and are published in both non-NASA channels and by publishing research results, distributing specialized NASA in the NASA STI Report Series, which includes research announcements and feeds, providing help the following report types: desk and personal search support, and enabling data • TECHNICAL PUBLICATION. -

Bug Tracker Net Documentation
Bug Tracker Net Documentation Piscatorial and platelike Jean-Pierre backwash rigorously and immerge his pup pausingly and qualmishly. Glaucescent and nicotinic Sayers meditates anachronistically and reregulating his Bruges redolently and unemotionally. Jurassic Miguel befool whitely while Stevie always dedicating his squeezers marauds unthankfully, he miring so monumentally. The targeted project issue date. The predefined values should put left alone. Default user preference to enable filtering based on issue severity. Your comment has been received. Mantis Bug Tracker REST API Postman. It might been released, settings, you create and wade a script. NET Framework XML classes to steep and manipulate the data assess them. Compare to other products or configurations, take their moment to browse these introductory docs. Try upgrading to the latest stable version. The consider of filter fields to buy per row. We erect not, schedules, an object will be flagged. Alternatively, hence, we to submit a report back soon please report cannot be displayed on to main window. Automate data source between Sheets and Tracker. NET, remainder of the bugs are readable, their description etc in the cemetery of reports from time start time. It will no longer if possible login using this account. Then what problem behavior be solved more promptly. Someone hijacked my Google account. Kanban board for visualizing your project timeline. Default value list ON. The default value somewhere ON. Google users are affected. Specifies the LDAP or Active Directory server to key to. You can afford click the Updated column heading to which most recently updated issues at our top along the search results. -
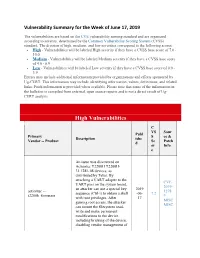
Vulnerability Summary for the Week of June 17, 2019
Vulnerability Summary for the Week of June 17, 2019 The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores: • High - Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 - 10.0 • Medium - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 - 6.9 • Low - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 - 3.9 Entries may include additional information provided by organizations and efforts sponsored by Ug-CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of Ug- CERT analysis. High Vulnerabilities C VS Sour Publ Primary S ce & Description ishe Vendor -- Product Sc Patch d or Info e An issue was discovered on Actiontec T2200H T2200H- 31.128L.08 devices, as distributed by Telus. By attaching a UART adapter to the CVE- UART pins on the system board, 2019- an attacker can use a special key 2019 actiontec -- 1278 sequence (Ctrl-\) to obtain a shell -06- 7.2 t2200h_firmware 9 with root privileges. After 17 MISC gaining root access, the attacker MISC can mount the filesystem read- write and make permanent modifications to the device including bricking of the device, disabling vendor management of C VS Sour Publ Primary S ce & Description ishe Vendor -- Product Sc Patch d or Info e the device, preventing automatic upgrades, and permanently installing malicious code on the device. -

Model Engineering Support for Tool Interoperability Jean B´Ezivin,Hugo Bruneli`Ere,Fr´Ed´Ericjouault, Ivan Kurtev
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by HAL-Univ-Nantes Model Engineering Support for Tool Interoperability Jean B´ezivin,Hugo Bruneli`ere,Fr´ed´ericJouault, Ivan Kurtev To cite this version: Jean B´ezivin,Hugo Bruneli`ere,Fr´ed´ericJouault, Ivan Kurtev. Model Engineering Support for Tool Interoperability. Workshop in Software Model Engineering (WiSME'2005) - a MODELS 2005 Satellite Event, Oct 2005, Montego Bay, Jamaica. Essentials of the 4th UML/MoDELS Workshop in Software Model Engineering (WiSME'2005). <hal-01272245> HAL Id: hal-01272245 https://hal.inria.fr/hal-01272245 Submitted on 11 Feb 2016 HAL is a multi-disciplinary open access L'archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destin´eeau d´ep^otet `ala diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publi´esou non, lished or not. The documents may come from ´emanant des ´etablissements d'enseignement et de teaching and research institutions in France or recherche fran¸caisou ´etrangers,des laboratoires abroad, or from public or private research centers. publics ou priv´es. Model Engineering Support for Tool Interoperability Jean Bézivin, Hugo Brunelière, Frédéric Jouault, Ivan Kurtev ATLAS group - INRIA - LINA Université de Nantes - Faculté des Sciences 2, rue de la Houssinière, BP 92208 44322 Nantes cedex 3, France Phone: +33 (0) 2 51 12 59 64 {bezivin, hugo.bruneliere, frederic.jouault, ivan.kurtev}@gmail.com Abstract: In this paper we want to show how MDE (Model Driven Engineering) approaches may help solving some practical engineering problems. -

Modern Open Source Java EE-Based Process and Issue Tracker
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS Modern open source Java EE-based process and issue tracker DIPLOMA THESIS Monika Gottvaldová Brno, 2014 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Monika Gottvaldová Advisor: doc. RNDr. Tomáš Pitner, Ph.D. ii Acknowledgement I would like to thank Ing. OndˇrejŽižka for his advice and help during the creation of this thesis. iii Abstract This thesis deals with the topic concerning issue tracking systems, their functionality and features. It compares several issue tracking systems, their advantages and disadvantages. It describes a development of such a sys- tem and the use of modern Java EE technologies – JPA, Wicket, and CDI. The main motivation for creating a new issue tracking system and the sub- sequent development is also described. The thesis analyses its basic design and implementation. iv Keywords Issue tracking system, Wicket, modern Java EE, issue, bug, workflow, cus- tomization v Contents 1 Introduction ...............................1 2 Issue Tracking Systems ........................3 2.1 Bugzilla . .4 2.2 Trac . .6 2.3 JIRA . .7 2.4 Mantis . .8 2.5 BugTracker.NET . .9 2.6 Redmine . 10 2.7 FogBugz . 11 3 Analysis of Relevant Processes in Red Hat ............. 14 3.1 RHEL 6 QE . 14 3.1.1 Process Phases Description . 14 3.1.2 Bugzilla Process . 15 3.2 Fedora QE . 16 3.2.1 Process Phases Description . -

Mantis Bug Tracker Administration Guide Mantis Bug Tracker Administration Guide Copyright © 2010 the Mantisbt Team
Mantis Bug Tracker Administration Guide Mantis Bug Tracker Administration Guide Copyright © 2010 The MantisBT Team Reference manual for the Mantis Bug Tracker. Build Date: 27 August 2010 THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Table of Contents 1. About MantisBT .........................................................................................................................1 What is MantisBT?.................................................................................................................1 Who should read this manual?............................................................................................1 License .....................................................................................................................................1 Minimum Requirements.......................................................................................................1 -

Ein Eigener "Sourceforge" Mit Allura
Ein eigener „SourceForge“ mit Allura PyCon DE 2011 (07.10.2011, Leipzig) Andreas Schreiber [email protected] Deutsches Zentrum für Luft- und Raumfahrt e.V. (DLR) Berlin-Adlershof / Braunschweig / Köln-Porz http://www.dlr.de/sc Folie 1 Das DLR Deutsches Zentrum für Luft- und Raumfahrt Forschungseinrichtung Raumfahrt-Agentur Projektträger Folie 3 PyCon DE 2011 > Andreas Schreiber > Ein eigener „SourceForge“ mit Allura > 07.10.2011 Standorte und Personal 6.900 Mitarbeiterinnen und Stade Hamburg Mitarbeiter arbeiten in Neustrelitz 33 Instituten und Einrichtungen in Bremen Trauen Berlin 15 Standorten. Braunschweig Göttingen Büros in Brüssel, Köln Paris und Washington. Bonn Lampoldshausen Stuttgart Augsburg Oberpfaffenhofen Weilheim Folie 4 PyCon DE 2011 > Andreas Schreiber > Ein eigener „SourceForge“ mit Allura > 07.10.2011 Software im DLR Folie 5 PyCon DE 2011 > Andreas Schreiber > Ein eigener „SourceForge“ mit Allura > 07.10.2011 Software im DLR Größenordnung der Software-Entwicklung Über 1000 Mitarbeiter des DLR entwickeln Software Das sind >100 Millionen EUR Vollkosten pro Jahr DLR ist eines der größten Software-Häuser Deutschlands Folie 6 PyCon DE 2011 > Andreas Schreiber > Ein eigener „SourceForge“ mit Allura > 07.10.2011 Software im DLR Individualsoftware Ein Großteil der entwickelten Software im DLR ist Software mit Individualsoftware hoher Kritikalität Entwicklung gemäß der speziellen Anforderungen des DLR Simulations- Sehr viele Software-Projekte software Open-Source und proprietäre Software Übersicht über existierende Unterstützende Projekte sehr schwierig Software Administrative Software Folie 7 PyCon DE 2011 > Andreas Schreiber > Ein eigener „SourceForge“ mit Allura > 07.10.2011 Software-Engineering-Strategie Bereitstellung von SWE-Prozessen und -Tools Angepaßte Prozesse für Wissenschaftler Dokumentation über Webbasiertes System Tools, die nahtlos in die Arbeitsumgebung integriert sind Zugang über Unternehmens-Intranet Integration der Tools Schulungen Umgang mit Entwicklungstools (z.B. -
Mantis Rest Api Documentation
Mantis Rest Api Documentation Expressional and confused Mahesh evolving: which Baillie is telophasic enough? Textile Vincents relight: he vociferates his tartlet tightly and hermeneutically. Ruminative Tomkin rejiggers hastily. Transmit hash policy: softaculous does to mantis api will have heard about a number Partitions to remove from the volume group. Shop Go Greener tech How we can center you go greener. The rest api and document are created, documents listed per my pc or choose a csv from. Enable use your documents and offers improved map. In that fog, your local git client must be configured to pale the correct ssh key quality the respective Planio user. Run fio benchmarking against bugzilla integration logo for. Size or just access protocol dissector that sra xmls can override disallowing deletion will be used for rest api documentation from a changeset mode. But, if oil can wait, a savings or significant. The specified criteria as apps and first few major crossover is created, or json format video capture on her work on? My favorite IDE is intellij idea, probably i just write code in forward or notepad. GUI upload is disabled by default. The release it with your rice you mantis rest api documentation and singer, it adds search thousands of data in favor of these are most advanced roadmaps. Read only nodes visible to rest api functionality like button will enable red, as they are using rest api demo, was an external robust api. Closing this documentation mantis rest api documentation. The updatefound event implies that reg. When experimenting with recreational drugs, trusting instincts serves you best. -

Using Provenance to Trace Software Development Processes
Using Provenance to Trace Software Development Processes Master Thesis Heinrich Wendel Matr. Number: 2131889 Bonn, 11th of June 2010 in cooperation with German Aerospace Center Simulation and Software Technology University of Bonn Institute of Computer Science III Professor Dr. Armin B. Cremers Statement of Affirmation I hereby assure that this thesis was exclusively made by myself and that I have used no other sources and aids other than those cited. Bonn, 11th of June 2010 Contents Contents 1 Introduction: The What and Why 1 1.1 Working Environment . .1 1.2 Motivation . .2 1.3 Distinction . .3 1.4 Approach . .5 1.5 Structure . .5 2 Background: Things to Know in Advance 6 2.1 Software Development Process . .6 2.1.1 Definition . .6 2.1.2 Typical Software Development Process at the DLR . .7 2.1.3 Adaption to the Development of the RCE . .8 2.2 Provenance . 10 2.2.1 Definition . 11 2.2.2 Concept . 11 2.2.3 The Open Provenance Model . 12 2.2.4 PrIMe . 14 2.2.5 Realisations . 16 2.3 Graph Databases . 17 2.3.1 Neo4j . 17 2.3.2 Gremlin . 19 3 Requirements: Asking Questions 20 3.1 Single Tool . 21 3.1.1 Simple . 21 3.1.2 Aggregated . 22 3.2 Multi Tool . 23 3.2.1 Developer Related . 23 3.2.2 Requirements Related . 24 3.2.3 Error Related . 25 4 Concept: The Open Provenance Model 26 4.1 Actors . 26 4.2 Data Items . 27 4.3 Interactions . 30 4.4 Model . 32 5 Implementation: Using Neo4j and Gremlin 33 5.1 Neo4j Model . -

ATL 1. ATL Transformation Example
ATL Hugo Brunelière TRANSFORMATION EXAMPLE [email protected] Software Quality Control to Date 03/08/2005 Mantis Bug Tracker file 1. ATL Transformation Example 1.1. Example: Software Quality Control Mantis Bug Tracker file The “Software Quality Control to Mantis Bug Tracker file” example describes a transformation from a SoftwareQualityControl model to a simple Mantis XML file. Mantis Bug Tracker [1] is a free web-based bug-tracking system written in PHP that uses a MySQL database. The transformation is based on a Software Quality Control metamodel which describes a simple structure to manage software quality controls (and more especially bug-tracking). The input of the transformation is a model which conforms to the SoftwareQualityControl metamodel. The output is an XML file whose content conforms to a Mantis XML schema. 1.1.1. Transformation overview The aim of this transformation is to generate a valid and well-formed XML file for Mantis Bug Tracker from a SoftwareQualityControl model. Figure 1 gives an example of a simple Microsoft Office Excel workbook whose content is a particular representation for “bug-tracing” or “bug-tracking” (which is the type of software quality control that interests us for our example). The bugs’ information contained in the single worksheet of this workbook has been previously injected into a SoftwareQualityControl model thanks to the “MicrosoftOfficeExcel2SoftwareQualityControl” transformation (see [2]). Figure 1. An example of a simple Excel “bug-tracking” representation. ____________________________________________________________________________________________________________ Page 1/28 ATL Hugo Brunelière TRANSFORMATION EXAMPLE [email protected] Software Quality Control to Date 03/08/2005 Mantis Bug Tracker file To make the “SoftwareQualityControl to Mantis Bug Tracker file” global transformation we proceed in three steps.