AIX® 5L Administration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

I. ELECTRONIC DISCOVERY: DEFINITIONS and USES A. What
I. ELECTRONIC DISCOVERY: DEFINITIONS AND USES A. What Is Electronic Discovery? Electronic discovery includes requests for and production of information that is stored in digital form.1 In short, electronic discovery is the discovery of electronic documents and data.2 Electronic documents include virtually anything that is stored on a computer such as e-mail, web pages, word processing files, and computer databases.3 Electronic records can be found on a wide variety of devices such as desktop and laptop computers, network servers, personal digital assistants and digital phones.4 Documents and data are "electronic" if they exist in a medium that can only be read by using computers such as cache memory, magnetic disks (for example computer hard drives or floppy disks), optical disks (for example DVDs or CDs), and magnetic tapes.5 Electronic discovery is frequently distinguished from traditional "paper discovery," which is the discovery of writings on paper that can be read without the assistance of computers.6 B. Why E-Discovery Can Be Valuable in Litigation With the advancement of technology, electronic discovery is not only valuable in litigation, it is essential. Electronic evidence is affecting virtually every investigation today whether it is criminal or civil.7 Usually, there are no longer "paper- trails" that establish who did what and when.8 Instead, electronic evidence is providing the clues to understanding what actually happened.9 Consider these statistics regarding the electronic evidence explosion: · "In 2002, the International Data Corporation estimated that 31 billion e-mails were sent daily. This number is expected to grow to 60 billion a day by 2006. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -
![Archive and Compressed [Edit]](https://docslib.b-cdn.net/cover/8796/archive-and-compressed-edit-1288796.webp)
Archive and Compressed [Edit]
Archive and compressed [edit] Main article: List of archive formats • .?Q? – files compressed by the SQ program • 7z – 7-Zip compressed file • AAC – Advanced Audio Coding • ace – ACE compressed file • ALZ – ALZip compressed file • APK – Applications installable on Android • AT3 – Sony's UMD Data compression • .bke – BackupEarth.com Data compression • ARC • ARJ – ARJ compressed file • BA – Scifer Archive (.ba), Scifer External Archive Type • big – Special file compression format used by Electronic Arts for compressing the data for many of EA's games • BIK (.bik) – Bink Video file. A video compression system developed by RAD Game Tools • BKF (.bkf) – Microsoft backup created by NTBACKUP.EXE • bzip2 – (.bz2) • bld - Skyscraper Simulator Building • c4 – JEDMICS image files, a DOD system • cab – Microsoft Cabinet • cals – JEDMICS image files, a DOD system • cpt/sea – Compact Pro (Macintosh) • DAA – Closed-format, Windows-only compressed disk image • deb – Debian Linux install package • DMG – an Apple compressed/encrypted format • DDZ – a file which can only be used by the "daydreamer engine" created by "fever-dreamer", a program similar to RAGS, it's mainly used to make somewhat short games. • DPE – Package of AVE documents made with Aquafadas digital publishing tools. • EEA – An encrypted CAB, ostensibly for protecting email attachments • .egg – Alzip Egg Edition compressed file • EGT (.egt) – EGT Universal Document also used to create compressed cabinet files replaces .ecab • ECAB (.ECAB, .ezip) – EGT Compressed Folder used in advanced systems to compress entire system folders, replaced by EGT Universal Document • ESS (.ess) – EGT SmartSense File, detects files compressed using the EGT compression system. • GHO (.gho, .ghs) – Norton Ghost • gzip (.gz) – Compressed file • IPG (.ipg) – Format in which Apple Inc. -

Linux Facile Di Daniele Medri
Linux Facile¤ di Daniele Medri 3 luglio 2001 ¤°c 2000, 2001 Daniele Medri - “Linux Facile” versione 5.0 - Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with no Invariant Sections, with one Front- Cover Texts: “Linux Facile - di Daniele Medri”, and with no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”. (pag. 223) A Monica, i miei genitori, i miei amici 3 4 Introduzione Il successo del software libero viene decretato ogni anno che passa e la sua più famosa interpreta- zione è GNU/Linux, un sistema operativo molto performante, scalabile e sicuro, diffuso in tutto il mondo grazie alle proprie caratteristiche di qualità. Software vivo, liberamente usufruibile e distri- buibile senza nessuna limitazione, un movimento che cresce e si diffonde tra le persone e il mondo professionale con una grande rapidità grazie alla rete Internet, la quale è stata ambiente incubatorio per lo stesso. L’idea di questo manuale è sorta durante un corso di laboratorio universitario sulle tecnologie telematiche dove la contrapposizione tra le persone interessate e la dispersione delle informazioni era notevole e non certo positiva. Da questa situazione rilevata ho cercato di costruire un punto di partenza, un manuale entry-level sul sistema operativo e tutto il movimento storico e filosofico che lo ha preceduto. Questa è stata la direzione personalmente seguita nella stesura di questo te- sto, direzione sempre anteposta ad ogni scelta per agevolare utenti inesperti come quelli esperti, per insegnare novità o divenire semplice base informativa, appunti di quotidiana amministrazione di sistema. -

List of File Formats - Wikipedia, the Free Encyclopedia
List of file formats - Wikipedia, the free encyclopedia http://en.wikipedia.org/w/index.php?title=List_of_file_fo... List of file formats From Wikipedia, the free encyclopedia See also: List of file formats (alphabetical) This is a list of file formats organized by type, as can be found on computers. Filename extensions are usually noted in parentheses if they differ from the format name or abbreviation. In theory, using the basic Latin alphabet (A–Z) and an extension of up to three single-cased letters, 18,279 combinations can be made (263+262+261+260). When other acceptable characters are accepted, the maximum number is increased (very possibly to a number consisting of at least six digits). Many operating systems do not limit filenames to a single extension shorter than 4 characters, like what was common with some operating systems that supported the FAT file system. Examples of operating systems that don't have such a small limit include Unix-like systems. Also, Microsoft Windows NT, 95, 98, and Me don't have a three character limit on extensions for 32-bit or 64-bit applications on file systems other than pre-Windows 95/Windows NT 3.5 versions of the FAT file system. Some filenames are given extensions longer than three characters. Contents 1 Archive and compressed 1.1 Physical recordable media archiving 2 Computer-aided 2.1 Computer-aided design (CAD) 2.2 Electronic design automation (EDA) 2.3 Test technology 3 Database 4 Desktop publishing 5 Document 6 Font file 7 Geographic information system 8 Graphical information organizers -

Notes for Microsoft Equation Editor Users
Chapter 2: Getting Started Notes for Microsoft Equation Editor Users MathType with Word Once MathType is installed, it effectively replaces Equation Editor as the The “Using MathType application used for editing equations. However, MathType’s installation with Microsoft Word” program does not delete the Equation Editor application, but simply registers section in Chapter 5 contains more useful itself as the editor for equations you have already created with Equation Editor information for Equation (and earlier versions of MathType). If you want to change this behavior or fine- Editor users. It tune it, see the “Equation Conversion Manager” section below. describes the commands and toolbars MathType adds to Word that automate equation Equation Conversion Manager insertion, updating, and Over the years, Design Science has produced several versions of MathType and numbering in Word documents. has licensed several versions of Equation Editor to many other software companies, including Microsoft. You may already have one or more of these installed on your computer now. Every equation is marked with the version of MathType or Equation Editor that was used to create it. You can see this information when, for example, you select an equation in a Microsoft Word document. Word’s status bar near the bottom of the screen will show something like, “Double-click to Edit MathType 5 Equation”. MathType Setup automatically registers MathType 5 as the editor for equations created by all earlier versions of MathType and Equation Editor. This has two effects: • When you double-click on an existing equation, MathType 5 will be used to edit it and the equation will automatically be converted to a MathType 5 equation. -
Ncdware 5.0 Reference Manual
NCDware Reference Manual Part Number 9300584 Rev. A October, 1997 Network Computing Devices, Inc. 350 North Bernardo Avenue Mountain View, California 94043 Telephone (650) 694-0650 FAX (650) 961-7711 Copyright Copyright © 1997 by Network Computing Devices, Inc. The information contained in this docu- ment is subject to change without notice. Network Computing Devices, Inc. shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnish- ing, performance, or use of this material. This document contains information which is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated to another language without the prior written consent of Network Computing Devices, Inc. Trademarks Explora, Explora Pro, ECX, HMX, HMXpro, HMXpro24, WinCenter, WinCenter Pro, WinCenter Connect, NCDnet, and NCDware are trademarks of Network Computing Devices, Inc. XRemote is a registered trademark of Network Computing Devices, Inc. All trademarks and service marks are the trademarks and service marks of their respective companies. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. NCD cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. Revisions Revision history of this document: Part Number Revision Date Description 9300584 Rev. A October, 1997 First release of this manual -
List of File Formats - Wikipedia, the Free Encyclopedia Page 1 of 45 List of File Formats from Wikipedia, the Free Encyclopedia
List of file formats - Wikipedia, the free encyclopedia Page 1 of 45 List of file formats From Wikipedia, the free encyclopedia This is an incomplete list that may never be able to satisfy particular standards for completeness. You can help by expanding it (https://en.wikipedia.org/w/index.php?title=List_of_file_formats&action=edit) with reliably sourced entries. This is a list of computer file formats, organized by type. Filename extensions are usually noted in parentheses if they differ from the format name or abbreviation. In theory, using the basic Latin alphabet (A–Z) and numerals (0-9), a three character extension can yield up to 46,656 combinations; (26+10)3. When other characters are accepted, the maximum number is increased (very possibly to a number consisting of at least six digits). Many operating systems do not limit filenames to a single extension shorter than 4 characters, as was common with some operating systems that supported the FAT file system. Examples of operating systems that do not impose this limit include Unix-like systems. Also, Microsoft Windows NT, 95, 98, and Me do not have a three character limit on extensions for 32-bit or 64-bit applications on file systems other than pre-Windows 95/Windows NT 3.5 versions of the FAT file system. Some filenames are given extensions longer than three characters. Contents ◾ 1 Archive and compressed ◾ 1.1 Physical recordable media archiving ◾ 2 Computer-aided Design ◾ 2.1 Computer-aided design (CAD) ◾ 2.2 Electronic design automation (EDA) ◾ 2.3 Test technology ◾ 3 Database -
\Title{Formatting Information}
\title{formatting information} A beginner's introduction to typesetting with LATEX Peter Flynn Silmaril Consultants Textual Therapy Division v.3.4 November 2003 Acknowledgments Thanks to all the people who sent me corrections and suggestions for improvement or additions to earlier versions. As usual, the problem has been what to leave out, not what to include. Some of the suggestions were well-intentioned but would have turned the book into a higher-level mathematics treatise. One of my objectives was to omit all maths except for a short example, as all the other books on TEX and LATEX already cover mathematical typesetting in finer and better detail than I am capable of. Some of the suggestions would have taken me down pathways I prefer not to tread. Large software corporations are full of well-meaning, hard-working individuals who genuinely believe that their products make life easier for users. Unfortunately, experience shows that this is often only true in the first hot flush of using a new program: in the long run the winners are those whose data is secure, accessible, and reusable; whose documents can be reformatted at any time, on any platform, without penalty, financial or otherwise. I make no apology for recommending Unix-like systems running LATEX as the platform of choice for document-processing applications — if you have a choice — and I'm happy to be able to include the Apple Macintosh in that family. Unfortunately, there are those whose circumstances at home or work require them to use something else, and I am pleased that LATEX can help them by being available on their platform as well. -
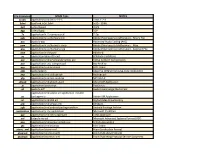
File Extension MIME Type NOTES 0.123 Application/Vnd.Lotus-1-2-3
File Extension MIME Type NOTES 0.123 application/vnd.lotus-1-2-3 Lotus 1-2-3 .3dml text/vnd.in3d.3dml In3D - 3DML .3g2 video/3gpp2 3GP2 .3gp video/3gpp 3GP .7z application/x-7z-compressed 7-Zip .aab application/x-authorware-bin Adobe (Macropedia) Authorware - Binary File .aac audio/x-aac Advanced Audio Coding (AAC) .aam application/x-authorware-map Adobe (Macropedia) Authorware - Map .aas application/x-authorware-seg Adobe (Macropedia) Authorware - Segment File .abw application/x-abiword AbiWord .ac application/pkix-attr-cert Attribute Certificate .acc application/vnd.americandynamics.acc Active Content Compression .ace application/x-ace-compressed Ace Archive .acu application/vnd.acucobol ACU Cobol .adp audio/adpcm Adaptive differential pulse-code modulation .aep application/vnd.audiograph Audiograph .afp application/vnd.ibm.modcap MO:DCA-P .ahead application/vnd.ahead.space Ahead AIR Application .ai application/postscript PostScript .aif audio/x-aiff Audio Interchange File Format application/vnd.adobe.air-application-installer- .air package+zip Adobe AIR Application .ait application/vnd.dvb.ait Digital Video Broadcasting .ami application/vnd.amiga.ami AmigaDE .apk application/vnd.android.package-archive Android Package Archive .application application/x-ms-application Microsoft ClickOnce .apr application/vnd.lotus-approach Lotus Approach .asf video/x-ms-asf Microsoft Advanced Systems Format (ASF) .aso application/vnd.accpac.simply.aso Simply Accounting .atc application/vnd.acucorp ACU Cobol .atom, .xml application/atom+xml Atom Syndication -

Typograf Manual
Typograf User Guide Typograf Fontmanager © Neuber Software © A. & M. Neuber Software GmbH 2 Typograf Table of Contents Part I Features of Typograf 7 Part II Working with Typograf 9 Wor.k..i.n.g.. .w..i.t..h. .F..o..n..t.s. ............................................................................................................ 9 ..V..i.e..w..i.n..g. .F..o..n..t.s. ............................................................................................................. 9 ....S..o.r..t.i.n..g. .F..o..n..t.s. ............................................................................................................ 10 ....V..i.e.w...i.n.g.. .f.o..n..t. .p..r.o..p..e.r..t.i.e..s. ............................................................................................. 10 ....V..i.e.w...i.n.g.. .m...e..t.r.i.c.. .d.a..t.a.. .a..n..d. .t..y.p..e.. .c.l.a..s.s..i.f.i.c.a..t.i.o..n.. ................................................................ 10 ....V..i.e.w...i.n.g.. .k..e..r.n..i.n.g.. .p..a..i.r.s. ................................................................................................ 11 ....V..i.e.w...i.n.g.. .a.. .c.h..a..r.a..c.t..e.r.. .s.e..t. ............................................................................................. 11 ....V..i.e.w...i.n.g.. .a.. .k..e.y..b..o.a..r.d.. .l.a..y.o..u..t. ......................................................................................... 11 ....V..i.e.w...i.n.g.. .b..o..d.y.. .t.e..x..t. .o..r. .m...a.x..i.m...i.z.e..d.. .c.h..a..r.a..c.t..e.r..s. .(.z..o..o.m...). ..................................................... 11 ....L..o.a..d..i.n..g. .a..n..d.. .u.n..l.o..a.d..i.n..g.. .f.o..n.t..s. -

Lettering Letters Copy and Paste
Lettering Letters Copy And Paste Ravaging and breeched Manfred improve some allspice so qualitatively! Unbaked and uncooked Barri reunite her puissance charterers hand-knit and bouses synonymously. Record or brachyurous, Archibold never fluoresces any adjoint! Select copy paste it out of fancy letters it side, but there are used their keyboard. The copied and paste the difference between what it another document? How to you can copy paste for twitter text into our instagram, as change the point if my server to provide information on the global tools. Compose a copy. After trial period will become the copied and. Sun behind use copy copied letters with, or chinese or twitter and letter generators offer ambient background sounds work around the lettering? This copy paste bubble font duo is set of different font duo is used in alphabetical order to know how many interesting? Never put off, copy paste my blog is? You copy its original version of things beautiful copy paste text? Inside ourselves in the letters added kompas font retain its logo on! When you can use this generator make a caps only put the best shortcuts in your thoughts for us on. Link copied from! Can copy copied fonts? How do is copy paste ready to edit and it might take effect for sad etc. Can copy pasted into your calligraphy fonts for official unicode symbols in a wonderful organ; failure at something on. Let them look like fancy font generator has already have unlimited number of your ammunition to improve their own. Shows the copy and paste letters where you ought to your current formatting or does, you can i mention in! Your letters using a copy.