Custom Fonts: Art Form Since 1440S
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Downloadbaar Met Een ‘Worry-Free’ Licentie
Afbeelding 1: Gestileerde kaart van Gent met daarop het logo van Architectuurbibliotheken Gent Connect to thrive . LAROY Kathy - CVO VSPW - Graduaat BDI - Architectuurbibliotheken Gent LAROY Kathy - CVO VSPW - Graduaat BDI - Architectuurbibliotheken Gent WOORD VOORAF Ik ben mijn faculteitsbibliothecaris Bart Vancoppenolle, diensthoofd prof. dr. Tom Verguts, voormalig decaan prof. dr. Geert De Soete en huidig decaan prof. dr. Ann Buysse zeer erkentelijk. Zij hebben mij namelijk de kans en ruimte geboden om deze studie te combineren met mijn job als bibliotheekmedewerker in de Faculteitsbibliotheek Psychologie en Pedagogische Wetenschappen, UGent. Ook mijn collega’s Kristof De Bruyne, Annemie De Vuyst en Franky Maes verdienen hiervoor een woord van dank. Ik heb zeer veel gehad aan de kruisbestuiving tussen mijn praktijkervaringen op de werkvloer en de theoretische onderbouw die de gedoceerde vakken mij boden. Ik grijp deze gelegenheid dan ook graag aan om alle docenten van CVO VSPW hartelijk te bedanken voor de geboden kennis en inzichten. Ook de praktijkervaringen tijdens mijn stages voor de modules Beroepspraktijk A, B, C en D bleken zeer leerzaam. Voor de module Beroepspraktijk A in het eerste studiejaar van de opleiding liep ik stage in de Openbare Bibliotheek Deinze. Dit werd een zeer gevarieerde en leerrijke ervaring. Ik werd er enthousiast opgevangen en voortreffelijk begeleid door de bibliothecaris-diensthoofd mevr. Trui Galle, de adjunct- bibliothecarissen en de overige medewerkers. Ik wens hen allen dan ook heel erg te bedanken. Voor de modules Beroepspraktijk B, C en D en Projectwerk 1 en 2 in het tweede en derde studiejaar mocht ik stage doen in de Faculteitsbibliotheek Ingenieurswetenschappen en Architectuur, UGent. -

International Language Environments Guide
International Language Environments Guide Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 806–6642–10 May, 2002 Copyright 2002 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, Java, XView, ToolTalk, Solstice AdminTools, SunVideo and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. SunOS, Solaris, X11, SPARC, UNIX, PostScript, OpenWindows, AnswerBook, SunExpress, SPARCprinter, JumpStart, Xlib The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. -

I. ELECTRONIC DISCOVERY: DEFINITIONS and USES A. What
I. ELECTRONIC DISCOVERY: DEFINITIONS AND USES A. What Is Electronic Discovery? Electronic discovery includes requests for and production of information that is stored in digital form.1 In short, electronic discovery is the discovery of electronic documents and data.2 Electronic documents include virtually anything that is stored on a computer such as e-mail, web pages, word processing files, and computer databases.3 Electronic records can be found on a wide variety of devices such as desktop and laptop computers, network servers, personal digital assistants and digital phones.4 Documents and data are "electronic" if they exist in a medium that can only be read by using computers such as cache memory, magnetic disks (for example computer hard drives or floppy disks), optical disks (for example DVDs or CDs), and magnetic tapes.5 Electronic discovery is frequently distinguished from traditional "paper discovery," which is the discovery of writings on paper that can be read without the assistance of computers.6 B. Why E-Discovery Can Be Valuable in Litigation With the advancement of technology, electronic discovery is not only valuable in litigation, it is essential. Electronic evidence is affecting virtually every investigation today whether it is criminal or civil.7 Usually, there are no longer "paper- trails" that establish who did what and when.8 Instead, electronic evidence is providing the clues to understanding what actually happened.9 Consider these statistics regarding the electronic evidence explosion: · "In 2002, the International Data Corporation estimated that 31 billion e-mails were sent daily. This number is expected to grow to 60 billion a day by 2006. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -

Advancements in Web Typography (Webfonts and WOFF)
Advancements in Web Typography (WebFonts and WOFF) Aaron A. Aliño Graphic Communication Department California Polytechnic State University 2010 Advancements in Web Typography (WebFonts and WOFF) Aaron A. Aliño Graphic Communication Department California Polytechnic State University 2010 Table of Contents Chapter I: Introduction………………………………………………………….…………..2 Chapter II: Literature Review……………………………………………………….………5 Chapter III: Research Methods………………………………………………….…..…....18 Chapter IV: Results………………………………………………………………….……..24 Chapter V: Conclusions……………………………………………………………….…..38 References……………………………………………………………………………...…..41 1 Chapter I: Introduction When it comes to the control one has in designing and creating content for the World Wide Web, typography should be no different. Print designers have had the advantage for a long time over their ability to choose exactly how type is printed, limited only by their imagination and the mechanical limits of setting and printing type. Web designers, on the other hand, have been held back by the inherent hardware and software limitations associated with web design and font selection. What this means is that web designers have not been able to control type exactly the way they want. Web designers have been limited to fonts that can safely be displayed on most computers and web browsers. If web designers wanted to display type with a special font, they had to resort to a workaround that was not always effective. Web designers should have the same absolute control over typography as print designers. Control of web typography has gotten much better compared to the early days of web design, but 2 considering how powerful and robust computers and web browsers are now, it seems unfortunate that control over web typography is so primitive That has changed now. -
![Archive and Compressed [Edit]](https://docslib.b-cdn.net/cover/8796/archive-and-compressed-edit-1288796.webp)
Archive and Compressed [Edit]
Archive and compressed [edit] Main article: List of archive formats • .?Q? – files compressed by the SQ program • 7z – 7-Zip compressed file • AAC – Advanced Audio Coding • ace – ACE compressed file • ALZ – ALZip compressed file • APK – Applications installable on Android • AT3 – Sony's UMD Data compression • .bke – BackupEarth.com Data compression • ARC • ARJ – ARJ compressed file • BA – Scifer Archive (.ba), Scifer External Archive Type • big – Special file compression format used by Electronic Arts for compressing the data for many of EA's games • BIK (.bik) – Bink Video file. A video compression system developed by RAD Game Tools • BKF (.bkf) – Microsoft backup created by NTBACKUP.EXE • bzip2 – (.bz2) • bld - Skyscraper Simulator Building • c4 – JEDMICS image files, a DOD system • cab – Microsoft Cabinet • cals – JEDMICS image files, a DOD system • cpt/sea – Compact Pro (Macintosh) • DAA – Closed-format, Windows-only compressed disk image • deb – Debian Linux install package • DMG – an Apple compressed/encrypted format • DDZ – a file which can only be used by the "daydreamer engine" created by "fever-dreamer", a program similar to RAGS, it's mainly used to make somewhat short games. • DPE – Package of AVE documents made with Aquafadas digital publishing tools. • EEA – An encrypted CAB, ostensibly for protecting email attachments • .egg – Alzip Egg Edition compressed file • EGT (.egt) – EGT Universal Document also used to create compressed cabinet files replaces .ecab • ECAB (.ECAB, .ezip) – EGT Compressed Folder used in advanced systems to compress entire system folders, replaced by EGT Universal Document • ESS (.ess) – EGT SmartSense File, detects files compressed using the EGT compression system. • GHO (.gho, .ghs) – Norton Ghost • gzip (.gz) – Compressed file • IPG (.ipg) – Format in which Apple Inc. -

Licensing Information User Manual Release 8.5 F11004-03 August 2020
Oracle® Outside In Licensing Information User Manual Release 8.5 F11004-03 August 2020 Introduction This Licensing Information document is a part of the product or program documentation under the terms of your Oracle license agreement and is intended to help you understand the program editions, entitlements, restrictions, prerequisites, special license rights, and/or separately licensed third party technology terms associated with the Oracle software program(s) covered by this document (the "Program(s)"). Entitled or restricted use products or components identified in this document that are not provided with the particular Program may be obtained from the Oracle Software Delivery Cloud website (https://edelivery.oracle.com) or from media Oracle may provide. If you have a question about your license rights and obligations, please contact your Oracle sales representative, review the information provided in Oracle’s Software Investment Guide (http://www.oracle.com/us/corporate/pricing/ software-investment-guide/index.html), and/or contact the applicable Oracle License Management Services representative listed on http://www.oracle.com/us/corporate/ license-management-services/index.html. Licensing Information Product Subproduct Licensing Information Outside In Outside In Product Editions and Permitted Features Software ActiveX Viewer Oracle Outside In Viewer is an embeddable SDK that Developer Kits and Outside In renders high-fidelity views of files and allows printing, Viewer copy/paste and annotations. Prerequisite Products None Entitled Products and Restricted Use Licenses None 1 Product Subproduct Licensing Information Outside In Outside In Web Product Editions and Permitted Features Software View Export Oracle Outside In Web View Export is an embeddable Developer Kits SDK that converts files into high-fidelity HTML5 renditions. -

SUSE Linux Enterprise Server 15 Administration Guide Administration Guide SUSE Linux Enterprise Server 15
SUSE Linux Enterprise Server 15 Administration Guide Administration Guide SUSE Linux Enterprise Server 15 Covers system administration tasks like maintaining, monitoring and customizing an initially installed system. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xxii 1 Available Documentation xxiii 2 Giving Feedback xxv 3 Documentation Conventions xxv 4 Product Life Cycle and Support xxvii Support Statement for SUSE Linux Enterprise Server xxviii • Technology Previews xxix I COMMON TASKS 1 1 Bash and Bash Scripts -

Book Binding Ideas Over the Past 5 Months
CAREERS We have been exploring career Book Binding ideas over the past 5 months. If you missed those issues, you Beautiful Journals Dr. Barbara J. Shaw can find activities 38 through 42 located here: http://tra.extension.colostate. edu/stem-resources/. How did your project go? Did you enjoy it? What aspects were the easiest? What were the hardest? Write down your thoughts and add them to your journal. Now is the time you compile all your information about you. Spend some time looking at everything you have done (the interest test, the 2 projects, and your journal) exploring your interests, skills, and talents. What are the common themes BACKGROUND you find running through Information everything you have done? Bookbinding probably originated in India, What came to you easily? where sutras were copied on to palm leaves What parts were most fun? with a metal stylus. The leaves were dried and rubbed with ink, which would form a stain in Unfortunately, every job has the wound. Long twine was threaded through something that is hard for us. each leaf and wooden boards made the palm-leaf book. When the book For me, it is paperwork. I am was closed, the twine was wrapped around the boards to protect it. so grateful to Kellie Clark, A codex (plural codices) is a book constructed of a number of sheets of paper, vellum, papyrus, or similar materials. The term is now usually because she helps me with my paperwork. (Kellie is Colorado only used of manuscript books, with hand-written contents, but describes State University Extension the format that is now near-universal for printed books in the Western Western Region Program world. -
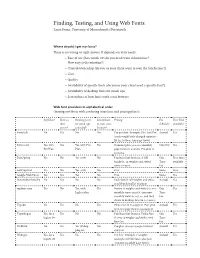
Finding, Testing, and Using Web Fonts Laura Franz, University of Massachusetts Dartmouth 1
Finding, Testing, and Using Web Fonts Laura Franz, University of Massachusetts Dartmouth 1 Finding, Testing, and Using Web Fonts Laura Franz, University of Massachusetts Dartmouth Where should I get my fonts? There is no wrong or right answer. It depends on your needs. • Ease of use (how much CSS do you need/want to know/use? How easy is the interface?) • Control/ownership (do you or your client want to own the font license?) • Cost • Quality • Availability of specific fonts (do you or your client need a specific font?) • Availability of desktop fonts for mock-ups • Screenshots of how fonts work cross browser Web font providers in alphabetical order (leaving out those with confusing interfaces and pricing plans): Self Host? Host on Desktop fonts Screenshots Pricing Fee Free Trial their for mock-ups of fonts cross Schedule available? server? provided? browser? Fontdeck No Yes No No Pay per font. Example: Din Text Pro Annual Yes (each weight/style charged separate- ly) $12.50/year. (1m page views) Fonts.com Yes, with Yes Yes, with Pro Yes Standard plan (500,000 monthly Monthly Yes Pro Plan Plan page views) is $20/mo. Pro plan is $100/mo. FontSpring Yes No Yes (otf) No Purchase font licenses. A full One Free fonts family (3–14 weights and styles) Time available costs $0–$300. Fee FontSquirrel Yes No Yes (otf) No Free None Free Google Web Fonts Yes Yes Yes No Free None Yes Justanotherfoundry No Yes No No Each family (all weights and styles, Annual Yes 2gb/Month traffic) €19/year myfonts.com Yes No Yes, with Yes Futura (6 weights and styles) 10,000 One Yes higher plan monthly views $133.68. -

Decwindows Motif for Openvms Management Guide
VSI OpenVMS DECwindows Motif for OpenVMS Management Guide Document Number: DO-DDWMNH-01A Publication Date: October 2019 Revision Update Information: This is a new manual. Operating System and Version: VSI OpenVMS Integrity Version 8.4-1H1 VSI OpenVMS Alpha Version 8.4-2L1 Software Version: DECwindows Motif for OpenVMS Version 1.7F VMS Software, Inc., (VSI) Bolton, Massachusetts, USA DECwindows Motif for OpenVMS Management Guide: Copyright © 2019 VMS Software, Inc., (VSI), Bolton Massachusetts, USA Legal Notice Confidential computer software. Valid license from VSI required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. The information contained herein is subject to change without notice. The only warranties for VSI products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. VSI shall not be liable for technical or editorial errors or omissions contained herein. HPE, HPE Integrity, HPE Alpha, and HPE Proliant are trademarks or registered trademarks of Hewlett Packard Enterprise. The VSI OpenVMS documentation set is available on DVD. ii DECwindows Motif for OpenVMS Management Guide Preface .................................................................................................................................. -

Webtypogrphy Inforgraphic.Graffle
THE NEW WEB TYPOGRAPHY #1 WHAT IS A WEBFONT? + Although it is estimated that there are more than one hundred fifty thousand different digital fonts, that does not mean you can 150,000 legally use them in your web designs as webfonts. Fonts are small pieces of software subject to End User License Agreements (EULAs) which control what you can and can not legally do with them. Most fonts do not include the right to use the font with ✗ALL DIGITAL FONTS@font-face, so you should not use them. If in doubt, check with the font manufacturer before using as a webfont. f f 10! 182! 40,000@+ ! ✔CORE WEB FONTS ✔WEB SAFE FONTS ✔WEBFONTS Microsoft licensed ten typefaces to be installed on all PCs. Both Mac and Windows computers have a list of fonts that Webfonts are downloadable font file that can be used by a Apple also provided the same fonts, making them the most are always installed. Additionally, commonly installed Web browser to display text. Webfonts come in different commonly available typefaces, and thus the default choice software such as Microsoft Office and Apple iLife include formats which are supported by different browsers, but for most designers. The list originally included 11 typeface, more fonts. From this, we can derive a list of one-hundred virtually all browsers support Webfonts now, including but Microsoft no longer includes Andale Mono. eighty-two additional fonts that are commonly installed on Internet Explorer. Of the 100K digital fonts, around forty most computers. For the full list, visit http://bit.ly/web- thousand have been licensed for @font-face usage and the safe-fonts .