Module 1: Getting Started with Windows Powershell
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Attacker Antics Illustrations of Ingenuity
ATTACKER ANTICS ILLUSTRATIONS OF INGENUITY Bart Inglot and Vincent Wong FIRST CONFERENCE 2018 2 Bart Inglot ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Rock Climber ◆ Globetrotter ▶ From Poland but live in Singapore ▶ Spent 1 year in Brazil and 8 years in the UK ▶ Learning French… poor effort! ◆ Twitter: @bartinglot ©2018 FireEye | Private & Confidential 3 Vincent Wong ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Baby Sitter ◆ 3 years in Singapore ◆ Grew up in Australia ©2018 FireEye | Private & Confidential 4 Disclosure Statement “ Case studies and examples are drawn from our experiences and activities working for a variety of customers, and do not represent our work for any one customer or set of customers. In many cases, facts have been changed to obscure the identity of our customers and individuals associated with our customers. ” ©2018 FireEye | Private & Confidential 5 Today’s Tales 1. AV Server Gone Bad 2. Stealing Secrets From An Air-Gapped Network 3. A Backdoor That Uses DNS for C2 4. Hidden Comment That Can Haunt You 5. A Little Known Persistence Technique 6. Securing Corporate Email is Tricky 7. Hiding in Plain Sight 8. Rewriting Import Table 9. Dastardly Diabolical Evil (aka DDE) ©2018 FireEye | Private & Confidential 6 AV SERVER GONE BAD Cobalt Strike, PowerShell & McAfee ePO (1/9) 7 AV Server Gone Bad – Background ◆ Attackers used Cobalt Strike (along with other malware) ◆ Easily recognisable IOCs when recorded by Windows Event Logs ▶ Random service name – also seen with Metasploit ▶ Base64-encoded script, “%COMSPEC%” and “powershell.exe” ▶ Decoding the script yields additional PowerShell script with a base64-encoded GZIP stream that in turn contained a base64-encoded Cobalt Strike “Beacon” payload. -

Powershell Integration with Vmware View 5.0
PowerShell Integration with VMware® View™ 5.0 TECHNICAL WHITE PAPER PowerShell Integration with VMware View 5.0 Table of Contents Introduction . 3 VMware View. 3 Windows PowerShell . 3 Architecture . 4 Cmdlet dll. 4 Communication with Broker . 4 VMware View PowerCLI Integration . 5 VMware View PowerCLI Prerequisites . 5 Using VMware View PowerCLI . 5 VMware View PowerCLI cmdlets . 6 vSphere PowerCLI Integration . 7 Examples of VMware View PowerCLI and VMware vSphere PowerCLI Integration . 7 Passing VMs from Get-VM to VMware View PowerCLI cmdlets . 7 Registering a vCenter Server . .. 7 Using Other VMware vSphere Objects . 7 Advanced Usage . 7 Integrating VMware View PowerCLI into Your Own Scripts . 8 Scheduling PowerShell Scripts . 8 Workflow with VMware View PowerCLI and VMware vSphere PowerCLI . 9 Sample Scripts . 10 Add or Remove Datastores in Automatic Pools . 10 Add or Remove Virtual Machines . 11 Inventory Path Manipulation . 15 Poll Pool Usage . 16 Basic Troubleshooting . 18 About the Authors . 18 TECHNICAL WHITE PAPER / 2 PowerShell Integration with VMware View 5.0 Introduction VMware View VMware® View™ is a best-in-class enterprise desktop virtualization platform. VMware View separates the personal desktop environment from the physical system by moving desktops to a datacenter, where users can access them using a client-server computing model. VMware View delivers a rich set of features required for any enterprise deployment by providing a robust platform for hosting virtual desktops from VMware vSphere™. Windows PowerShell Windows PowerShell is Microsoft’s command line shell and scripting language. PowerShell is built on the Microsoft .NET Framework and helps in system administration. By providing full access to COM (Component Object Model) and WMI (Windows Management Instrumentation), PowerShell enables administrators to perform administrative tasks on both local and remote Windows systems. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -
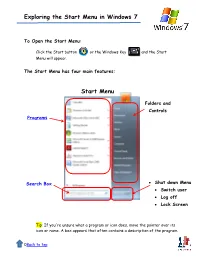
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

View the Slides (Smith)
Network Shells Michael Smith Image: https://commons.wikimedia.org/wiki/File:Network-connections.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png Management at a distance (netsh) Netsh: Configure DHCP servers with netsh -r RemoteMachine -u domain\username [RemoteMachine] netsh>interface [RemoteMachine] netsh interface>ipv6 [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (netsh) Netsh: Configure DHCP servers with netsh Location-r RemoteMachine -u domain\username Hierarchical [RemoteMachine] netsh>interfacecontext Simpler [RemoteMachine] netsh interface>ipv6 commands [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (WSMan) WSMan (in Powershell): Manage Windows remotely with Set-Location -Path WSMan:\SERVER01 Get-ChildItem -Path . Set-Item Client\TrustedHosts *.domain2.com -Concatenate Reference: https://docs.microsoft.com/en-us/powershell/module/microsoft.wsman.management/about/about_wsman_provider -

Windows NT® 4 for Dummies® File:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM
Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM Table of Contents Windows NT® 4 For Dummies® Introduction About This Book How to Use This Book And What about You? How This Book Is Organized Part I: Introducing Windows NT (Bare-Bones Stuff) Part II: Making Windows NT Do Something Part III: Using Windows NT Applications Part IV: Been There, Done That: Quick References for Moving to Windows NT Part V: Getting Help Part VI: The Part of Tens Icons Used in This Book Where to Go from Here Part I: Intro to Windows NT (Bare Bones Stuff) Chapter 1: What Is Windows NT? What Is This "Windows" Stuff, Anyway? What Does Windows NT 4 Do? Why Should I Bother Using Windows NT? Will I Like Windows NT 4 Better than Windows NT 3.51? What's the Difference between Windows NT Workstation and Windows NT Server? Bracing Yourself for Windows NT 4 Chapter 2: Boring Information, Bothersome Computer Parts The Computer Microprocessor Floppy Disks, Compact Discs (CDs), and Disk Drives Floppy disk flipping What disk drives does Windows NT like? What does "write-protected" mean? Driving with compact discs The Mouse and That Double-Click Stuff Cards and Monitors Keyboards Groups of keys More key principles Print Screen: the one fun, weird code key Modems Printers Networks Sound Cards (Disgusting Bioactive Noises) Parts Required by Windows NT Chapter 3: Windows NT Stuff Everybody Thinks You Already Know Backing Up Your Work Clicking 1 of 9 07/14/99 08:29:14 Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

How to Open Control Panel in Windows 10 Way 1: Open It in the Start Menu
Course Name : O Level(B4-Ist sem.) Subject : ITT&NB Topic : Control Panel Date : 27-03-20 Control Panel The Control Panel is a component of Microsoft Windows that provides the ability to view and change system settings. It consists of a set of applets that include adding or removing hardware and software, controlling user accounts, changing accessibility options, and accessing networking settings. How to open Control Panel in Windows 10 Way 1: Open it in the Start Menu. Click the bottom-left Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results. Way 2: Access Control Panel from the Quick Access Menu. Press Windows+X or right-tap the lower-left corner to open the Quick Access Menu, and then choose Control Panel in it. Way 3: Go to Control Panel through the Settings Panel. Open the Settings Panel by Windows+I, and tap Control Panel on it. Way 4: Open Control Panel in the File Explorer. Click the File Explorer icon on the taskbar, select Desktop and double-tap Control Panel. Way 5: Open the program via Run. Press Windows+R to open the Run dialog, enter control panel in the empty box and click OK. Changing System Date and Time Step 1: Click the bottom-right clock icon on the taskbar, and select Date and time settings. Or we can right click the clock icon, click Adjust data /time. Step 2: As the Date and time Windows opens, we can turn off Set time automatically. Step 3: In the Date and Time Settings window, respectively change date and time, and then tap OK to confirm the changes. -

Revoke Obfuscation Report
Revoke-Obfuscation: PowerShell Obfuscation Detection Using Science Daniel Bohannon @danielhbohannon | Lee Holmes @Lee_Holmes Revoke-Obfuscation is the result of industry research collaboration between Daniel Bohannon - Senior Applied Security Researcher at Mandiant/FireEye, and Lee Holmes – Lead Security Architect of Azure ManaGement at Microsoft. Background By far the most prevalent delivery and execution vehicle for malware in the industry today is basic malicious executables and malicious documents. While not represented accurately by its popularity in the news, a small portion of the current malware ecosystem leverages PowerShell as part of its attack chain. Of malware that uses PowerShell, the most prevalent use is the garden-variety stager: an executable or document macro that launches PowerShell to download another executable and run it. Despite its relative statistical rarity, development of malicious and offense-focused PowerShell techniques has been a rich field of innovation. Commercial products have started to react to these techniques in several ways. Because they are often delivered as script files, Antivirus vendors have long had the ability to write signatures that block malicious PowerShell scripts. With the release of Windows 10, some vendors have additionally begun to implement support for Windows’ Antimalware Scan Interface. This interface gives Antivirus vendors the ability to implement deep content scanning, providing visibility as each stage of malware fetches and dynamically executes new instructions from a remote network location. In addition to antivirus signatures, many SIEM vendors have started to implement alerting based on command-line parameters that are frequently used in malicious contexts. Palo Alto provides an excellent survey of commonly-used malicious PowerShell command-line arguments in their post, Pulling Back the Curtains on EncodedCommand PowerShell Attacks.