Cisco VXI Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Good for Enterprise – Android V1.9.1 Release Notes (Service Release)
Good for Enterprise – Android v1.9.1 Release Notes (Service Release) Updated: April 27, 2012 Good for Enterprise – Android v1.9.1 (Service Release) .............................................................................................. 1 Issues Resolved ........................................................................................................................................................ 1 Good for Enterprise – Android v1.9.0 ........................................................................................................................... 1 New Features ............................................................................................................................................................ 1 Issues Resolved ........................................................................................................................................................ 2 Good for Enterprise – Android v1.8.1 (Service Release) .............................................................................................. 2 Good for Enterprise – Android v1.8.0 ........................................................................................................................... 3 New Features ............................................................................................................................................................ 3 Good for Enterprise – Android v1.7.5 Service Release ................................................................................................ 3 -

Next Generation UC Clients and Endpoints
Next Generation UC Clients and Endpoints Agenda • Next Generation Endpoints and Clients • Call Control Enhancements • Next Gen Design Considerations – Quality and Experience Control (Medianet, QoS & CAC) – Seamless Secure Access (Secure Connect) – Wireless LAN and Bluetooth – VXI Design Next Generation Endpoints and Clients Cisco UC Client Integration Cisco Unified Client Services Framework (2nd Generation) Cisco Cisco UC Cisco UC Cisco Jabber Cisco Jabber for Integration Integration Developer & Quad Phone for Mac Windows for Microsoft for RTX Integrator SDK Cisco Unified Infrastructure Services Cisco Jabber – CSF2G Capabilities Instant Messaging Rich / Group Chat Presence Contact Search Enterprise User Management Call Control & Authentication Business Video Web/Desktop Collaboration Conferencing Visual Voicemail Cisco Jabber App Integration Remote Access (MS Office) 2nd Generation CSF (CSF2G) Jabber Phones Products CUCI Integrations Virtual Communicator User Interface, App Specific logic CUVA Mode Call Control (SIP, CTI, DVO) Portable Libraries Media (A/V) Control IM & Presence APIs (C, C++) CSF2G Person Mngt (LDAP, AD, UDS) Visual Voicemail (IMAP, REST) Implementations Configuration (TFTP, CUP) Remote Access (SSA) Media A/V Engines Media Device Interface Platform-Specific System Implementation Implementation OS Abstraction Windows Operating System OS X, iOS Android Extending CSF to New Next Gen Platforms • Web Integrated - Quad • Smartphones – Cius Cisco Unified Client Services Framework Cisco Cius 802.11a/b/g/n, 3G/4G and Bluetooth Wired to Wireless Transition H.264 video standard High-definition 720p video Built-in Cameras Dual Independent Displays VDI Support – Vmware, Citrix, Wyse Front Cisco AppHQ Android Mkt Cisco Partner Market Place Applications Applications Applications Customer Applications BoA Administrat Home Depot or Administrator BoA “Admin User Controlled Home Depot Access “ User USF #CiscoPlusCA USF User Administrator 11 Cisco VXC Clients Brings together VDI And Collaboration (VXI) New Desktop Virtualization Endpoints . -

Towards a Mobile, Assistive and Intuitive Videoconferencing
eTELEMED 2012 : The Fourth International Conference on eHealth, Telemedicine, and Social Medicine Towards a Mobile, Assistive and Intuitive Videoconferencing Víctor Torres-Padrosa, Eusebi Calle, Jose L. Marzo, Mercè Rovira Universitat de Girona, Spain {victor.torres, eusebi.calle, joseluis.marzo, merce.rovira}@udg.edu Abstract—In this paper we present TAM-TAM (Tele Assistance for improving the usage of Internet technologies, price and and Monitoring), a tool devised to provide assistive and intuitive simple interfaces are considered to be prominent. videoconferencing. It can be used to provide social support, In this paper we present TAM-TAM (Tele Assistance remote consultation, remote monitoring and training or Monitoring), a tool that offers an intuitive interface for the rehabilitation group sessions through multi-user elderly, impaired and long-term care people as well as for videoconferencing. TAM-TAM relies on a simple and minimalist health professionals to provide social support, remote interface based on accessible standard web technologies and open consultation, remote monitoring and training and rehabilitation video streaming solutions. We also describe our progress for group sessions through multi-user videoconferencing. bringing TAM-TAM mobile, targeting Android and iOS tablet PCs and mobile market. II. RELATED WORK Keywords–videoconferencing; teleconsultation; social care; Although there are several initiatives and projects dealing nursing home; group home; elderly. with devices and applications devised for the aforementioned collectives, whenever a hardware device is needed but not produced in mass, it results in a relevant increase of the cost of I. INTRODUCTION the system, which is not affordable by public health systems. The accelerating pace of the world’s population aging is That’s why TAM-TAM focuses on standard hardware such as remarkably changing the demographic distribution of PCs and tablet PCs, as discussed in subsequent sections. -
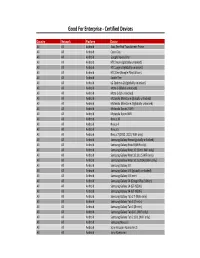
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

UC API (Cius, Jabber SDK)
UC API (Cius, Jabber SDK) Jaroslav Martan, CSE, CCIE #5871 e-mail/im:[email protected], video:[email protected] Jiří Šolc, Collaboration Team Leader, ICZ © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 • UC API Overview • Cius • Jabber SDK © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 2 APIs Fall Into Specific Categories • Provisioning Make changes to the Application’s actual configuration • Serviceability Allow you to collect information about the current state of the system Provide access to historical information such as logs and CDR • Device Monitoring and Call Control Allow you to monitor the real-time state of a device Provide a way to instruct the system on how to route a call • Other Allow you to extend the functionality of the system Allow you to integrate UC into other business applications © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 http://developer.cisco.com/web/ipps http://developer.cisco.com/web/jmapi • Other XML Services (XSI) MIDlets © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 • Provisioning AXL • Serviceability SNMP PerfMon • Device Monitoring and Call Control JTAPI TAPI (TSP) Webdialer • Other Extension Mobility © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 5 http://developer.cisco.com/web/vgapi • Provisioning • Serviceability • Device Monitoring and Call Control TCL IVR Voice XML • Other © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Public 6 http://developer.cisco.com/web/cuc • Provisioning • Serviceability • Device Monitoring and Call Control • Other © 2010 Cisco and/or its affiliates. -

Nasazení VDI/VXI Z Pohledu Bezpečnosti a Nástrojů Pro Spolupráci
Cisco Expo 2012 Nasazení VDI/VXI z pohledu bezpečnosti a nástrojů pro spolupráci ARCH2/L2 Tomáš Horák, [email protected] Systems Engineer, Data Center & Collaboration Petr Wünsch, [email protected] Systems Engineer Cisco Expo © 2012 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 • Twitter www.twitter.com/CiscoCZ • Talk2cisco www.talk2cisco.cz/dotazy • SMS 721 994 600 CiscoCisco Expo Expo © 2011© 2011 Cisco Cisco and/or and/or its affiliates. its affiliates. All rights All rights reserved. reserved. Cisco Public 2 • Why Desktop Virtualization? • Cisco VXI Vision • VXI & Collaboration • NetApp Storage for VDI • VXI Security • DC Security • Conslusion CiscoCisco Expo Expo © 2011© 2011 Cisco Cisco and/or and/or its affiliates. its affiliates. All rights All rights reserved. reserved. Cisco Public 3 © 2010 Cisco and/or its affiliates. All rights reserved. 4 Broker Keyboard, Video, Mouse Client • Large OS • Many local applicationsCompute Storage • Vulnerable Network • Constant patching • Data backup • Complex management • Software distribution delivery challenges • Skilled local support staff required • Personal Computer is disaggregated • Keyboard, Video, and Mouse stay with user • Compute and storage move to the data center • Network availability is required for all application access • Network performance is critical to user experience CiscoCisco Expo Expo © 2011© 2011 Cisco Cisco and/or and/or its affiliates. its affiliates. All rights All rights reserved. reserved. Cisco Public 5 Challenges of Traditional PC Environment Purchase Drivers Microsoft Windows 7 Migration . Reduce migration costs Data Security . Reduce application incompatibility Compliance . Extend life of existing desktop software Lost Agility & Productivity Contractors and Employee-Owned IT . Manage desktop image on employee-owned assets . -

Unified Communications 8.6(2A) Japan System Release テスト結果サマリ
Unified Communications 8.6(2a) Japan System Release テスト結果サマリ Jun 2012 © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 1 Category Component Version Remark Call Control Cisco Unified Communications 8.6.2.20000-2 Manager 8.6.2.1000-1 Locale 3-1-9.JP Dial Plan Cisco Unified Survivable Remote Site Telephony (SRST) 15.2.2T IOS 9 15.2.2T IOS Cisco Unified Communications Manager Express 8.8.2.4 LI Cisco TelePresence Video Communication Server (VCS) X7.0.3 Cisco TelePresence Video Communication Server Expressway X6.1 Applications Cisco Unified Presence 8.6.3.10000-20 Cisco Unified Contact Center Express 8.5.1 SU2 Cisco Unity Connection 8.6.2.21900-5 uc-locale-ja_JP- 8.6.2.1-25.cop Locale © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2 Category Component Version Remark E20 TE4.1.1 EX60 TC5.1 EX90 TC5.1 Cisco TelePresence Quick Set C20 TC 5.1 CIUS 9.2(2) 6911 SCCP69xx.9-2-2-5/SIP69xx.9-2-2-2 6921 SCCP69xx.9-2-2-6/SIP69xx.9-2-2-7 Endpoints and Clients 6941 SCCP69xx.9-2-2-6/SIP69xx.9-2-2-7 6945 SCCP69xx.9-2-2-4/SIP69xx.9-2-2-6 6961 SCCP69xx.9-2-2-6/SIP69xx.9-2-2-7 7961G SCCP79xx.9-2-3/SIP79xx.9-2-3 7962 SCCP79xx.9-2-3/SIP79xx.9-2-3 7965 SCCP79xx.9-2-3/SIP79xx.9-2-3 7975 SCCP79xx.9-2-3/SIP79xx.9-2-3 7985 cmterm_7985.4-1-7-0 © 2010 Cisco and/or its affiliates. -

Session 1: the World According to Cisco Cius
Session 1: The World According to Cisco Cius #CiscoPlus Technology and Business Needs Converging . Always available . Video communications . On / off campus . 1+1 =3… Video + Voice . Voice, video, unified . Virtual Desktop delivers messaging, virtual teams business apps . Employee productivity . Driving TCO reduction #CiscoPlus Workspace Technology is Evolving Convergence Driven by: . Portability . Versatility . User Experience . High resolution display © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 3 Cisco Delivers Next Wave of Innovation . 802.11 Wi-Fi . High-definition video . 3G/4G data . Cisco TelePresence Interop . Bluetooth . Adobe Flash . Voice, video, . Virtual Desktop unified messaging . Thin client . Conferencing applications . Presence & IM . Cloud computing #CiscoPlus Bringing Together Cisco’s Collaboration Suite Designed For Business Seamless Integration and Interoperability UC Manager Cisco Unified Instant (Manageability) Cisco Jabber IM Communications Unity Connection Messaging Cisco TelePresence and Lifelike Virtual Endpoint Interoperability Video Cisco Quad Teaming VDI Meeting Collaborative Desktop + Cisco WebEx (Integrated) Center Virtualization Rich Media © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 5 Enterprise Grade Security – End-to-End Policy Media and Mobility Manageme Data Enterprise Security nt Access Hardware Network Security Certificate Security Security Manageme Foundation Password nt Remote Complexity Wipe Secure Disable Credential Cisco ActiveSync -

Monthly Technology Briefs
the way we see it Changing the Game: Monthly Technology Briefs July 2011 Internet, to Web, to Clouds: The Critical role of Standardization Read the Capgemini Chief Technology Officers’ Blog at www.capgemini.com/ctoblog Public the way we see it Internet, to Web, to Clouds – the Critical Role of Standardization The evolutionary path of the new generation of technology based on services delivered from clouds began with the Internet as did the use of standards to ensure universal connectivity. The World Wide Web followed by extending this principle to provide universal content capabilities, and these two building blocks transformed the understanding of what technology could do. For the first time, a genuinely open external environment in which people could find and exchange content emerged around a relatively simple set of standards using a very different approach to the application-centric proprietary internal use of IT to automate business process. The new Internet/Web model became the basis for further development leading to Web 2.0. This again promoted simple standards for accessibility that could support a growing range of services through which people could gain the new capability for human-centric universal interaction. The important point with both the Web and Web 2.0 was the manner in which standards allowed ‘any’ to ‘any’, or ‘any’ to ‘many’, and even ‘many’ to ‘many’ activities to be supported on-demand, with no pre-planned integration being required. This is a radical departure from the client-server application generation of internal IT, where the number of users of an application, and, its relationship to every other system must be established. -

The New Collaboration Experience
The New Collaboration Experience Joao Justo Goncalves Collaboration Sales, Cisco Portugal © 20112010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 1 Globalization (I) © 20112010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2 Globalization (II) © 20112010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 3 Globalization (III) © 2011 4Cisco and/or its16 affiliates. May All rights reserved. Cisco Confidential 4 2012 © 20112010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 5 98% Made in USA 35% Made in USA 1970 2008 © 2011 6Cisco and/or its16 affiliates. May All rights reserved. ”Jumbo” 747 ”787” Cisco Confidential 6 2012 © 2011 Cisco and/or its affiliates. All rights reserved. mobile Cisco Confidential 7 © 2011 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 8 PC World Post PC World z Applications Client OS Server Architecture Devices © 2011 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 9 Cisco Jabber All-in-one UC Application Collaborate from Any Workspace • Presence & IM • PC, Mac, tablet, smart phone • Voice, Video, voice messaging • On-premises and Cloud • Desktop sharing, conferencing • Integration with Microsoft Office © 2011 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 10 Best Experience Across PC, Tablet and Phone Addressing Needs of Post-PC Workspace Phone PC Tablet iPhone Android Blackberry Win OS Mac OS iPad Cius Samsung Nokia • Changes in device ownership • More choice - When, where, how & what device © 2011 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 11 Jabber Video for iPad © 2011 Cisco and/or its affiliates. -

Cisco Cius Quick Start, Release 9.2(3)
Battery Quick Tips Applications When using Cisco Cius for the first time, charge the battery for a minimum of 5 hours. You can use Quick Launch Bar Some Cius applications require an active network your Cius while it charges. connection and registration to a Cisco Unified The quick launch bar at the bottom of the home Communications Manager server. CISCO CIUS QUICK START screen provides the following links: For 4G Models: Insert a SIM Card • Launch the Applications menu Phone Application • Launch the Phone application The Phone application is integrated with the • Launch the Add to Cius Home Screen menu Contacts, Chat, and other Cisco collaboration • Launch the Google Search application applications. Cius Home Screen Incoming Calls To add widgets or shortcuts to the home screen or To insert a SIM card: to change the wallpaper: From a locked screen, slide Answer to the left, 1. Completely remove the SIM card tray. • Tap Add to Cius Home Screen , or or slide Ignore to the right. 2. Place the SIM card into the tray. First Steps • Tap and hold an open space on the home 3. Reinsert the tray. screen Welcome to Cisco Cius, the world’s first To remove a widget or shortcut, tap and hold the Unlock Your Screen mobile collaboration endpoint. widget or shortcut and drag it to the trash. To get started, you must charge the battery, To unlock the screen, drag the arrow at the bottom unlock the screen, and run the Setup Assistant. right corner across to the left side. Notification Bar The notification bar at the top of the screen shows From an active Cius, choose to Answer, Divert, or To turn on your Cisco Cius, application notifications on the left and status Ignore a call. -

LISP Architecture, Protocols, and Product Update Bruce Pinsky, [email protected] CCIE #1045/CCDE 2007::0003/Ccar Session 1.1 Agenda
LISP Architecture, Protocols, and Product Update Bruce Pinsky, [email protected] CCIE #1045/CCDE 2007::0003/CCAr Session 1.1 Agenda • LISP Problem Statement • LISP Overview • LISP Product Happenings in 2011 • LISP IETF Happenings in 2011 • What’s Next Session 1.1 Slide 2 Today – No ID/Locator Separation (1) Is this John at the location ‘cisco’? (2) Is this John at location ‘home’? (3) Is this John at ‘Starbucks’? If I have a connection to John does it break because he changed locations? chambers.cisco.com 198.133.219.25 Application ID Network ID Network Location Session 1.1 Slide 3 Future – With ID/Locator Separation (1) The service binds to an Application Name (DNS) (2) The Application Name binds to a Endpoint ID (EID) (3) The EID binds dynamically to a Routing Locator (RLOC) (1) Users use DNS names (the human “who”) (2) Applications use EIDs (the network “who”) (3) Routing uses RLOCs (the network “where”) DNS Name EID RLOC chambers.cisco.com 198.133.219.25 64.100.100.1 static binding dynamic binding Provided by the DNS system Provided by the LISP routing system Session 1.1 Slide 4 LISP Overview What’s the problem with an “overloaded” semantic? . The IP address is overloaded on location and identity Why do current IP semantics cause scaling issues? − Overloaded IP address semantic makes efficient routing impossible − Today, “addressing follows topology,” which limits route aggregation compactness − IPv6 does not fix this Why are route scaling issues bad? − Routers require expensive memory to hold the Internet Routing Table in forwarding plane − Your router may have enough memory today; network gear lifetime can be 7 years or more.