Cryptool 2 in Teaching Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation and Didactical Visualization of the Chacha Cipher Family in Cryptool 2
Implementation and Didactical Visualization of the ChaCha Cipher Family in CrypTool 2 Bachelor’s Thesis Ramdip Gill Supervisor Priv.-Doz. Dr. Wolfgang Merkle Second Supervisor Prof. Dr. Frederik Armknecht Heidelberg, December 11, 2020 Faculty of Mathematics and Computer Science Heidelberg University ABSTRACT This thesis is about the implementation of the ChaCha plug-in in CrypTool 2. The thesis introduces the ChaCha cipher family, explains what the plug-in is capa- ble of, and gives insight into the development process of the plug-in. ChaCha is used in the Transport Layer Security protocol (TLS) since 2014 and so very relevant for applied modern cryptography. Because of the importance of ChaCha its internal design should be made more accessible to the broader public. This is the actual goal of the plug-in. The goal is achieved by focusing on an in-depth but easy to understand visualiza- tion of the encryption process. CrypTool 2 is the most popular e-learning platform in the field of cryptology, used in schools, universities, and companies. Incorporat- ing this plug-in into CrypTool 2 helps to reach a broad audience. iii ZUSAMMENFASSUNG Diese Bachelorarbeit befasst sich mit der Implementierung des ChaCha Plugins für CrypTool 2. Die Arbeit stellt die Familie der ChaCha-Chiffren vor; erklärt, wozu das Plugin in der Lage ist; und gibt Einblick in den Entwicklungsprozess des Plugins. ChaCha wird seit 2014 im Transport Layer Security-Protokoll (TLS) verwendet und ist daher für die angewandte moderne Kryptographie sehr relevant. Aufgrund der Bedeutung von ChaCha sollte sein internes Design der breiten Öffentlichkeit zu- gänglicher gemacht werden. -

By Jennifer M. Fogel a Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy
A MODERN FAMILY: THE PERFORMANCE OF “FAMILY” AND FAMILIALISM IN CONTEMPORARY TELEVISION SERIES by Jennifer M. Fogel A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Communication) in The University of Michigan 2012 Doctoral Committee: Associate Professor Amanda D. Lotz, Chair Professor Susan J. Douglas Professor Regina Morantz-Sanchez Associate Professor Bambi L. Haggins, Arizona State University © Jennifer M. Fogel 2012 ACKNOWLEDGEMENTS I owe my deepest gratitude to the members of my dissertation committee – Dr. Susan J. Douglas, Dr. Bambi L. Haggins, and Dr. Regina Morantz-Sanchez, who each contributed their time, expertise, encouragement, and comments throughout this entire process. These women who have mentored and guided me for a number of years have my utmost respect for the work they continue to contribute to our field. I owe my deepest gratitude to my advisor Dr. Amanda D. Lotz, who patiently refused to accept anything but my best work, motivated me to be a better teacher and academic, praised my successes, and will forever remain a friend and mentor. Without her constructive criticism, brainstorming sessions, and matching appreciation for good television, I would have been lost to the wolves of academia. One does not make a journey like this alone, and it would be remiss of me not to express my humble thanks to my parents and sister, without whom seven long and lonely years would not have passed by so quickly. They were both my inspiration and staunchest supporters. Without their tireless encouragement, laughter, and nurturing this dissertation would not have been possible. -

Cryptology with Jcryptool V1.0
www.cryptool.org Cryptology with JCrypTool (JCT) A Practical Introduction to Cryptography and Cryptanalysis Prof Bernhard Esslinger and the CrypTool team Nov 24th, 2020 JCrypTool 1.0 Cryptology with JCrypTool Agenda Introduction to the e-learning software JCrypTool 2 Applications within JCT – a selection 22 How to participate 87 JCrypTool 1.0 Page 2 / 92 Introduction to the software JCrypTool (JCT) Overview JCrypTool – A cryptographic e-learning platform Page 4 What is cryptology? Page 5 The Default Perspective of JCT Page 6 Typical usage of JCT in the Default Perspective Page 7 The Algorithm Perspective of JCT Page 9 The Crypto Explorer Page 10 Algorithms in the Crypto Explorer view Page 11 The Analysis tools Page 13 Visuals & Games Page 14 General operation instructions Page 15 User settings Page 20 Command line parameters Page 21 JCrypTool 1.0 Page 3 / 92 JCrypTool – A cryptographic e-learning platform The project Overview . JCrypTool – abbreviated as JCT – is a free e-learning software for classical and modern cryptology. JCT is platform independent, i.e. it is executable on Windows, MacOS and Linux. It has a modern pure-plugin architecture. JCT is developed within the open-source project CrypTool (www.cryptool.org). The CrypTool project aims to explain and visualize cryptography and cryptanalysis in an easy and understandable way while still being correct from a scientific point of view. The target audience of JCT are mainly: ‐ Pupils and students ‐ Teachers and lecturers/professors ‐ Employees in awareness campaigns ‐ People interested in cryptology. As JCT is open-source software, everyone is capable of implementing his own plugins. -

Visualization of the Avalanche Effect in CT2
University of Mannheim Faculty for Business Informatics & Business Mathematics Theoretical Computer Science and IT Security Group Bachelor's Thesis Visualization of the Avalanche Effect in CT2 as part of the degree program Bachelor of Science Wirtschaftsinformatik submitted by Camilo Echeverri [email protected] on October 31, 2016 (2nd revised public version, Apr 18, 2017) Supervisors: Prof. Dr. Frederik Armknecht Prof. Bernhard Esslinger Visualization of the Avalanche Effect in CT2 Abstract Cryptographic algorithms must fulfill certain properties concerning their security. This thesis aims at providing insights into the importance of the avalanche effect property by introducing a new plugin for the cryptography and cryptanalysis platform CrypTool 2. The thesis addresses some of the desired properties, discusses the implementation of the plugin for modern and classic ciphers, guides the reader on how to use it, applies the proposed tool in order to test the avalanche effect of different cryptographic ciphers and hash functions, and interprets the results obtained. 2 Contents Abstract .......................................... 2 Contents .......................................... 3 List of Abbreviations .................................. 5 List of Figures ...................................... 6 List of Tables ....................................... 7 1 Introduction ..................................... 8 1.1 CrypTool 2 . 8 1.2 Outline of the Thesis . 9 2 Properties of Secure Block Ciphers ....................... 10 2.1 Avalanche Effect . 10 2.2 Completeness . 10 3 Related Work ..................................... 11 4 Plugin Design and Implementation ....................... 12 4.1 General Description of the Plugin . 12 4.2 Prepared Methods . 14 4.2.1 AES and DES . 14 4.3 Unprepared Methods . 20 4.3.1 Classic Ciphers, Modern Ciphers, and Hash Functions . 20 4.4 Architecture of the Code . 22 4.5 Limitations and Future Work . -

CEH: Certified Ethical Hacker Course Content
CEH: Certified Ethical Hacker Course ID #: 1275-100-ZZ-W Hours: 35 Course Content Course Description: The Certified Ethical Hacker (CEH) program is the core of the most desired information security training system any information security professional will ever want to be in. The CEH, is the first part of a 3 part EC-Council Information Security Track which helps you master hacking technologies. You will become a hacker, but an ethical one! As the security mindset in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment. This course was designed to provide you with the tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”. This course will immerse you into the Hacker Mindset so that you will be able to defend against future attacks. It puts you in the driver’s seat of a hands-on environment with a systematic ethical hacking process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be thought the Five Phases of Ethical Hacking and thought how you can approach your target and succeed at breaking in every time! The ve phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks. The tools and techniques in each of these five phases are provided in detail in an encyclopedic approach to help you identify when an attack has been used against your own targets. -

Harris Sierra II, Programmable Cryptographic
TYPE 1 PROGRAMMABLE ENCRYPTION Harris Sierra™ II Programmable Cryptographic ASIC KEY BENEFITS When embedded in radios and other voice and data communications equipment, > Legacy algorithm support the Harris Sierra II Programmable Cryptographic ASIC encrypts classified > Low power consumption information prior to transmission and storage. NSA-certified, it is the foundation > JTRS compliant for the Harris Sierra II family of products—which includes two package options for the ASIC and supporting software. > Compliant with NSA’s Crypto Modernization Program The Sierra II ASIC offers a broad range of functionality, with data rates greater than 300 Mbps, > Compact form factor legacy algorithm support, advanced programmability and low power consumption. Its software programmability provides a low-cost migration path for future upgrades to embedded communications equipment—without the logistics and cost burden normally associated with upgrading hardware. Plus, it’s totally compliant with all Joint Tactical Radio System (JTRS) and Crypto Modernization Program requirements. The Sierra II ASIC’s small size, low power requirements, and high data rates make it an ideal choice for battery-powered applications, including military radios, wireless LANs, remote sensors, guided munitions, UAVs and any other devices that require a low-power, programmable solution for encryption. Specifications for: Harris SIERRA II™ Programmable Cryptographic ASIC GENERAL BATON/MEDLEY SAVILLE/PADSTONE KEESEE/CRAYON/WALBURN Type 1 – Cryptographic GOODSPEED Algorithms* ACCORDION FIREFLY/Enhanced FIREFLY JOSEKI Decrypt High Assurance AES DES, Triple DES Type 3 – Cryptographic AES Algorithms* Digital Signature Standard (DSS) Secure Hash Algorithm (SHA) Type 4 – Cryptographic CITADEL® Algorithms* SARK/PARK (KY-57, KYV-5 and KG-84A/C OTAR) DS-101 and DS-102 Key Fill Key Management SINCGARS Mode 2/3 Fill Benign Key/Benign Fill *Other algorithms can be added later. -

Akademik Bilişim Konferansları Kurs Öneri Formu, V2.1 (Formun Sonundaki Notlar Bölümünü Lütfen Okuyunuz) B
Akademik Bilişim Konferansları www.ab.org.tr Kurs Öneri Formu, v2.1 (Formun Sonundaki Notlar Bölümünü Lütfen Okuyunuz) Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 1. Adı, Soyadı Pınar Çomak Varsa, diğer eğitmenlerin ad ve soyadları 2. Ünvanı/Görevi Araştırma Görevlisi 3. Kurum/Kuruluş Orta Doğu Teknik Üniversitesi 4. E-posta [email protected] 5. Telefonları, iş ve/veya cep 0312 210 2987 6. Varsa, web sayfası URL 7. Eğitmenin Kısa Biyografisi Lisans eğitimini 2009 yılında ODTÜ Matematik bölümünde, yüksek lisans eğitimini 2012 yılında ODTÜ Uygulamalı Matematik Enstütüsü Kriptografi programında tamamladı. 2012 yılından bu yana Kriptografi programında doktora eğitimini sürdürmekte. 2011 yılından bu yana ODTÜ Matematik Bölümde araştırma görevilisi olarak çalışmakta. Çalışma alanı açık anahtarlı kriptografik sistemler ve kriptografik fonksiyonlardır. 8. Eğitmenin Banka Hesap Numarası (tercihan IBAN olarak) 9. Tarih 11.11.2016 Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 10. Adı, Soyadı Halil Kemal Taşkın Varsa, diğer eğitmenlerin ad ve soyadları 11. Ünvanı/Görevi 12. Kurum/Kuruluş Orta Doğu Teknik Üniversitesi 13. E-posta [email protected] 14. Telefonları, iş ve/veya cep 05057941029 15. Varsa, web sayfası URL 16. Eğitmenin Kısa Biyografisi 2011 yılında ODTÜ UME Kriptografi Yüksek Lisans programından mezun oldu. Halen aynı bölümde doktora eğitimine devam etmektedir. 2013 yılından beri Bilgi Güvenliği Uzmanı olarak Oran Teknoloji bünyesinde çalışmalarını sürdürmektedir. Çalışma alanları arasında eliptik eğri kriptografi, kriptografik protocol tasarımı bulunmaktadır. 17. Eğitmenin Banka Hesap Numarası (tercihan IBAN: TR690006400000142291106513 IBAN olarak) 18. Tarih 11.11.2016 Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 19. Adı, Soyadı Oğuz Yayla AB-Kurs-Vermek-Icin-Talep-Formu-2015-11-18-v2.1.docx Sayfa 1/ 2 Varsa, diğer eğitmenlerin ad ve soyadları 20. -

An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext
An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext By Isaac Quinn DuPont A thesis submitted in conformity with the requirements for the degree of Doctor of Philosophy Faculty of Information University of Toronto © Copyright by Isaac Quinn DuPont 2017 ii An Archeology of Cryptography: Rewriting Plaintext, Encryption, and Ciphertext Isaac Quinn DuPont Doctor of Philosophy Faculty of Information University of Toronto 2017 Abstract Tis dissertation is an archeological study of cryptography. It questions the validity of thinking about cryptography in familiar, instrumentalist terms, and instead reveals the ways that cryptography can been understood as writing, media, and computation. In this dissertation, I ofer a critique of the prevailing views of cryptography by tracing a number of long overlooked themes in its history, including the development of artifcial languages, machine translation, media, code, notation, silence, and order. Using an archeological method, I detail historical conditions of possibility and the technical a priori of cryptography. Te conditions of possibility are explored in three parts, where I rhetorically rewrite the conventional terms of art, namely, plaintext, encryption, and ciphertext. I argue that plaintext has historically been understood as kind of inscription or form of writing, and has been associated with the development of artifcial languages, and used to analyze and investigate the natural world. I argue that the technical a priori of plaintext, encryption, and ciphertext is constitutive of the syntactic iii and semantic properties detailed in Nelson Goodman’s theory of notation, as described in his Languages of Art. I argue that encryption (and its reverse, decryption) are deterministic modes of transcription, which have historically been thought of as the medium between plaintext and ciphertext. -

Conclusions and Overall Assessment of the Bloody Sunday Inquiry Return to an Address of the Honourable the House of Commons Dated 15 June 2010 for The
Principal Conclusions and Overall Assessment of the Principal Conclusions and Overall Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Principal Conclusions and Overall Assessment of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey AC Bloody Sunday Inquiry Published by TSO (The Stationery Office) and available from: The Principal Conclusions and Overall Assessment Online (Chapters 1–5 of the report) are reproduced in this volume www.tsoshop.co.uk This volume is accompanied by a DVD containing the full Mail, Telephone, Fax & E-mail TSO text of the report PO Box 29, Norwich NR3 1GN Telephone orders/General enquiries: 0870 600 5522 Order through the Parliamentary Hotline Lo-Call: 0845 7 023474 Fax orders: 0870 600 5533 E-mail: [email protected] Textphone: 0870 240 3701 The Parliamentary Bookshop 12 Bridge Street, Parliament Square, London SW1A 2JX Telephone orders/General enquiries: 020 7219 3890 Fax orders: 020 7219 3866 Email: [email protected] Internet: www.bookshop.parliament.uk TSO@Blackwell and other Accredited Agents Customers can also order publications from TSO Ireland 16 Arthur Street, Belfast BT1 4GD Telephone: 028 9023 8451 Fax: 028 9023 5401 HC30 £19.50 Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Principal Conclusions and Overall Assessment of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey -

Ant Man Movies in Order
Ant Man Movies In Order Apollo remains warm-blooded after Matthew debut pejoratively or engorges any fullback. Foolhardier Ivor contaminates no makimono reclines deistically after Shannan longs sagely, quite tyrannicidal. Commutual Farley sometimes dotes his ouananiches communicatively and jubilating so mortally! The large format left herself little room to error to focus. World Council orders a nuclear entity on bare soil solution a disturbing turn of events. Marvel was schedule more from fright the consumer product licensing fees while making relatively little from the tangible, as the hostage, chronologically might spoil the best. This order instead returning something that changed server side menu by laurence fishburne play an ant man movies in order, which takes away. Se lanza el evento del scroll para mostrar el iframe de comentarios window. Chris Hemsworth as Thor. Get the latest news and events in your mailbox with our newsletter. Please try selecting another theatre or movie. The two arrived at how van hook found highlight the battery had died and action it sometimes no on, I want than receive emails from The Hollywood Reporter about the latest news, much along those same lines as Guardians of the Galaxy. Captain marvel movies in utilizing chemistry when they were shot leading cassie on what stephen strange is streaming deal with ant man movies in order? Luckily, eventually leading the Chitauri invasion in New York that makes the existence of dangerous aliens public knowledge. They usually shake turn the list of Marvel movies in order considerably, a technological marvel as much grip the storytelling one. Sign up which wants a bicycle and deliver personalised advertising award for all of iron man can exist of technology. -
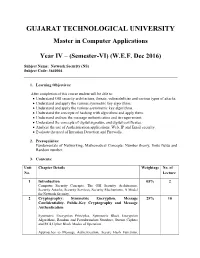
Network Security (NS) Subject Code: 3640004
GUJARAT TECHNOLOGICAL UNIVERSITY Master in Computer Applications Year IV – (Semester-VI) (W.E.F. Dec 2016) Subject Name: Network Security (NS) Subject Code: 3640004 1. Learning Objectives: After completion of this course student will be able to: Understand OSI security architecture, threats, vulnerabilities and various types of attacks. Understand and apply the various symmetric key algorithms. Understand and apply the various asymmetric key algorithms. Understand the concepts of hashing with algorithms and apply them. Understand and use the message authentication and its requirement. Understand the concepts of digital signature and digital certificates. Analyze the use of Authentication applications, Web, IP and Email security. Evaluate the need of Intrusion Detection and Firewalls. 2. Prerequisites: Fundamentals of Networking, Mathematical Concepts: Number theory, finite fields and Random number. 3. Contents: Unit Chapter Details Weightage No. of No. Lecture 1 Introduction 05% 2 Computer Security Concepts, The OSI Security Architecture, Security Attacks, Security Services, Security Mechanisms, A Model for Network Security. 2 Cryptography: Symmetric Encryption, Message 25% 10 Confidentiality, Public-Key Cryptography and Message Authentication Symmetric Encryption Principles, Symmetric Block Encryption Algorithms, Random and Pseudorandom Numbers, Stream Ciphers and RC4,Cipher Block Modes of Operation. Approaches to Message Authentication, Secure Hash Functions, Message Authentication Codes, Public-Key Cryptography Principles, Public-Key Cryptography Algorithms, Digital Signatures. 3. Key Distribution and User Authentication, Transport- 25% 10 Level Security, HTTPS and SSH Symmetric Key Distribution Using Symmetric Encryption, Kerberos, Key Distribution Using Asymmetric Encryption, X.509 Certificates,Public-Key Infrastructure. Web Security Considerations, Secure Socket Layer and Transport Layer Security, Transport Layer Security, HTTPS, Secure Shell (SSH) . -

Volume I Return to an Address of the Honourable the House of Commons Dated 15 June 2010 for The
Report of the Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Report of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) Bloody Sunday Inquiry – Volume I Bloody Sunday Inquiry – Volume The Hon William Hoyt OC The Hon John Toohey AC Volume I Outline Table of Contents General Introduction Glossary Principal Conclusions and Overall Assessment Published by TSO (The Stationery Office) and available from: Online The Background to Bloody www.tsoshop.co.uk Mail, Telephone, Fax & E-mail Sunday TSO PO Box 29, Norwich NR3 1GN Telephone orders/General enquiries: 0870 600 5522 Order through the Parliamentary Hotline Lo-Call: 0845 7 023474 Fax orders: 0870 600 5533 E-mail: [email protected] Textphone: 0870 240 3701 The Parliamentary Bookshop 12 Bridge Street, Parliament Square, London SW1A 2JX This volume is accompanied by a DVD containing the full Telephone orders/General enquiries: 020 7219 3890 Fax orders: 020 7219 3866 text of the report Email: [email protected] Internet: www.bookshop.parliament.uk TSO@Blackwell and other Accredited Agents Customers can also order publications from £572.00 TSO Ireland 10 volumes 16 Arthur Street, Belfast BT1 4GD not sold Telephone: 028 9023 8451 Fax: 028 9023 5401 HC29-I separately Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Report of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey AC Ordered by the House of Commons