CEH: Certified Ethical Hacker Course Content
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation and Didactical Visualization of the Chacha Cipher Family in Cryptool 2
Implementation and Didactical Visualization of the ChaCha Cipher Family in CrypTool 2 Bachelor’s Thesis Ramdip Gill Supervisor Priv.-Doz. Dr. Wolfgang Merkle Second Supervisor Prof. Dr. Frederik Armknecht Heidelberg, December 11, 2020 Faculty of Mathematics and Computer Science Heidelberg University ABSTRACT This thesis is about the implementation of the ChaCha plug-in in CrypTool 2. The thesis introduces the ChaCha cipher family, explains what the plug-in is capa- ble of, and gives insight into the development process of the plug-in. ChaCha is used in the Transport Layer Security protocol (TLS) since 2014 and so very relevant for applied modern cryptography. Because of the importance of ChaCha its internal design should be made more accessible to the broader public. This is the actual goal of the plug-in. The goal is achieved by focusing on an in-depth but easy to understand visualiza- tion of the encryption process. CrypTool 2 is the most popular e-learning platform in the field of cryptology, used in schools, universities, and companies. Incorporat- ing this plug-in into CrypTool 2 helps to reach a broad audience. iii ZUSAMMENFASSUNG Diese Bachelorarbeit befasst sich mit der Implementierung des ChaCha Plugins für CrypTool 2. Die Arbeit stellt die Familie der ChaCha-Chiffren vor; erklärt, wozu das Plugin in der Lage ist; und gibt Einblick in den Entwicklungsprozess des Plugins. ChaCha wird seit 2014 im Transport Layer Security-Protokoll (TLS) verwendet und ist daher für die angewandte moderne Kryptographie sehr relevant. Aufgrund der Bedeutung von ChaCha sollte sein internes Design der breiten Öffentlichkeit zu- gänglicher gemacht werden. -

Cryptology with Jcryptool V1.0
www.cryptool.org Cryptology with JCrypTool (JCT) A Practical Introduction to Cryptography and Cryptanalysis Prof Bernhard Esslinger and the CrypTool team Nov 24th, 2020 JCrypTool 1.0 Cryptology with JCrypTool Agenda Introduction to the e-learning software JCrypTool 2 Applications within JCT – a selection 22 How to participate 87 JCrypTool 1.0 Page 2 / 92 Introduction to the software JCrypTool (JCT) Overview JCrypTool – A cryptographic e-learning platform Page 4 What is cryptology? Page 5 The Default Perspective of JCT Page 6 Typical usage of JCT in the Default Perspective Page 7 The Algorithm Perspective of JCT Page 9 The Crypto Explorer Page 10 Algorithms in the Crypto Explorer view Page 11 The Analysis tools Page 13 Visuals & Games Page 14 General operation instructions Page 15 User settings Page 20 Command line parameters Page 21 JCrypTool 1.0 Page 3 / 92 JCrypTool – A cryptographic e-learning platform The project Overview . JCrypTool – abbreviated as JCT – is a free e-learning software for classical and modern cryptology. JCT is platform independent, i.e. it is executable on Windows, MacOS and Linux. It has a modern pure-plugin architecture. JCT is developed within the open-source project CrypTool (www.cryptool.org). The CrypTool project aims to explain and visualize cryptography and cryptanalysis in an easy and understandable way while still being correct from a scientific point of view. The target audience of JCT are mainly: ‐ Pupils and students ‐ Teachers and lecturers/professors ‐ Employees in awareness campaigns ‐ People interested in cryptology. As JCT is open-source software, everyone is capable of implementing his own plugins. -

Visualization of the Avalanche Effect in CT2
University of Mannheim Faculty for Business Informatics & Business Mathematics Theoretical Computer Science and IT Security Group Bachelor's Thesis Visualization of the Avalanche Effect in CT2 as part of the degree program Bachelor of Science Wirtschaftsinformatik submitted by Camilo Echeverri [email protected] on October 31, 2016 (2nd revised public version, Apr 18, 2017) Supervisors: Prof. Dr. Frederik Armknecht Prof. Bernhard Esslinger Visualization of the Avalanche Effect in CT2 Abstract Cryptographic algorithms must fulfill certain properties concerning their security. This thesis aims at providing insights into the importance of the avalanche effect property by introducing a new plugin for the cryptography and cryptanalysis platform CrypTool 2. The thesis addresses some of the desired properties, discusses the implementation of the plugin for modern and classic ciphers, guides the reader on how to use it, applies the proposed tool in order to test the avalanche effect of different cryptographic ciphers and hash functions, and interprets the results obtained. 2 Contents Abstract .......................................... 2 Contents .......................................... 3 List of Abbreviations .................................. 5 List of Figures ...................................... 6 List of Tables ....................................... 7 1 Introduction ..................................... 8 1.1 CrypTool 2 . 8 1.2 Outline of the Thesis . 9 2 Properties of Secure Block Ciphers ....................... 10 2.1 Avalanche Effect . 10 2.2 Completeness . 10 3 Related Work ..................................... 11 4 Plugin Design and Implementation ....................... 12 4.1 General Description of the Plugin . 12 4.2 Prepared Methods . 14 4.2.1 AES and DES . 14 4.3 Unprepared Methods . 20 4.3.1 Classic Ciphers, Modern Ciphers, and Hash Functions . 20 4.4 Architecture of the Code . 22 4.5 Limitations and Future Work . -

Akademik Bilişim Konferansları Kurs Öneri Formu, V2.1 (Formun Sonundaki Notlar Bölümünü Lütfen Okuyunuz) B
Akademik Bilişim Konferansları www.ab.org.tr Kurs Öneri Formu, v2.1 (Formun Sonundaki Notlar Bölümünü Lütfen Okuyunuz) Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 1. Adı, Soyadı Pınar Çomak Varsa, diğer eğitmenlerin ad ve soyadları 2. Ünvanı/Görevi Araştırma Görevlisi 3. Kurum/Kuruluş Orta Doğu Teknik Üniversitesi 4. E-posta [email protected] 5. Telefonları, iş ve/veya cep 0312 210 2987 6. Varsa, web sayfası URL 7. Eğitmenin Kısa Biyografisi Lisans eğitimini 2009 yılında ODTÜ Matematik bölümünde, yüksek lisans eğitimini 2012 yılında ODTÜ Uygulamalı Matematik Enstütüsü Kriptografi programında tamamladı. 2012 yılından bu yana Kriptografi programında doktora eğitimini sürdürmekte. 2011 yılından bu yana ODTÜ Matematik Bölümde araştırma görevilisi olarak çalışmakta. Çalışma alanı açık anahtarlı kriptografik sistemler ve kriptografik fonksiyonlardır. 8. Eğitmenin Banka Hesap Numarası (tercihan IBAN olarak) 9. Tarih 11.11.2016 Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 10. Adı, Soyadı Halil Kemal Taşkın Varsa, diğer eğitmenlerin ad ve soyadları 11. Ünvanı/Görevi 12. Kurum/Kuruluş Orta Doğu Teknik Üniversitesi 13. E-posta [email protected] 14. Telefonları, iş ve/veya cep 05057941029 15. Varsa, web sayfası URL 16. Eğitmenin Kısa Biyografisi 2011 yılında ODTÜ UME Kriptografi Yüksek Lisans programından mezun oldu. Halen aynı bölümde doktora eğitimine devam etmektedir. 2013 yılından beri Bilgi Güvenliği Uzmanı olarak Oran Teknoloji bünyesinde çalışmalarını sürdürmektedir. Çalışma alanları arasında eliptik eğri kriptografi, kriptografik protocol tasarımı bulunmaktadır. 17. Eğitmenin Banka Hesap Numarası (tercihan IBAN: TR690006400000142291106513 IBAN olarak) 18. Tarih 11.11.2016 Bölüm 1: Öneri Sahibi Eğitmene Ait Bilgiler 19. Adı, Soyadı Oğuz Yayla AB-Kurs-Vermek-Icin-Talep-Formu-2015-11-18-v2.1.docx Sayfa 1/ 2 Varsa, diğer eğitmenlerin ad ve soyadları 20. -

Cryptool 2 in Teaching Cryptography
Journal of Computations & Modelling, vol.4, no.1, 2014, 349-358 ISSN: 1792-7625 (print), 1792-8850 (online) Scienpress Ltd, 2014 Cryptool 2 in Teaching Cryptography Major Konstantinos Loussios1 Abstract. Considering the value it had in the past, has continued to the present and will continue to have, perhaps to an even greater extent in the future concealing information during transmission or transport, leads automatically to attempt to discover the importance and the value of the means, methods and techniques used to implement the concealment. Cryptography is a branch of computer science attracts the attention with its great utility that has nowadays. Given therefore deemed necessary to standardize, analyze and present the encryption algorithms to learning and training on the operation with as efficiently and easily as possible. Having in mind that the theory must be accompanied by practice and examples that help to consolidate the syllabi material, we felt that the analytical presentation of an educational tool on learning algorithms of cryptography is a way of learning while embedding. The learning tool cryptool 2 is an implementation of all the above, and through this we will try to show, those essential functions, which help the user with visual and practical way, to see in detail all the properties and functional details of the algorithms contained, will present representative examples of functioning algorithms, we proceed to create digital signatures and will implement the cryptanalysis algorithms. The above is an object of study and teaching in the professional area of land, in the field of communications and transmissions-service systems. Knowing, however, that historically since the antiquity, first we Greeks, we use encryption in a simple form, for military purposes, but later down through the years and fighting wars around the world, the art encryption and decryption evolved and became object of all armies and weapons. -
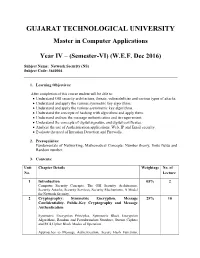
Network Security (NS) Subject Code: 3640004
GUJARAT TECHNOLOGICAL UNIVERSITY Master in Computer Applications Year IV – (Semester-VI) (W.E.F. Dec 2016) Subject Name: Network Security (NS) Subject Code: 3640004 1. Learning Objectives: After completion of this course student will be able to: Understand OSI security architecture, threats, vulnerabilities and various types of attacks. Understand and apply the various symmetric key algorithms. Understand and apply the various asymmetric key algorithms. Understand the concepts of hashing with algorithms and apply them. Understand and use the message authentication and its requirement. Understand the concepts of digital signature and digital certificates. Analyze the use of Authentication applications, Web, IP and Email security. Evaluate the need of Intrusion Detection and Firewalls. 2. Prerequisites: Fundamentals of Networking, Mathematical Concepts: Number theory, finite fields and Random number. 3. Contents: Unit Chapter Details Weightage No. of No. Lecture 1 Introduction 05% 2 Computer Security Concepts, The OSI Security Architecture, Security Attacks, Security Services, Security Mechanisms, A Model for Network Security. 2 Cryptography: Symmetric Encryption, Message 25% 10 Confidentiality, Public-Key Cryptography and Message Authentication Symmetric Encryption Principles, Symmetric Block Encryption Algorithms, Random and Pseudorandom Numbers, Stream Ciphers and RC4,Cipher Block Modes of Operation. Approaches to Message Authentication, Secure Hash Functions, Message Authentication Codes, Public-Key Cryptography Principles, Public-Key Cryptography Algorithms, Digital Signatures. 3. Key Distribution and User Authentication, Transport- 25% 10 Level Security, HTTPS and SSH Symmetric Key Distribution Using Symmetric Encryption, Kerberos, Key Distribution Using Asymmetric Encryption, X.509 Certificates,Public-Key Infrastructure. Web Security Considerations, Secure Socket Layer and Transport Layer Security, Transport Layer Security, HTTPS, Secure Shell (SSH) . -

Multicast Routing Over Computer Networks: Secure Performance Designs
Digital Forensics in the Cloud: Encrypted Data Evidence Tracking ZHUANG TIAN, BSc (Hons) a thesis submitted to the graduate faculty of design and creative technologies Auckland University of Technology in partial fulfilment of the requirements for the degree of Master of Forensic Information Technology School of Computer and Mathematical Sciences Auckland, New Zealand 2014 ii Declaration I hereby declare that this submission is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which to a substantial extent has been accepted for the qualification of any other degree or diploma of a University or other institution of higher learning, except where due acknowledgement is made in the acknowledgements. ........................... Zhuang Tian iii Acknowledgements This thesis was completed at the Faculty of Design and Creative Technologies in the school of Computing and Mathematical Sciences at Auckland University of Technology, New Zealand. While conducting the research project I received support from many people in one way or another, without whose support, this thesis would not have been completed in its present form. It is my pleasure to take this opportunity to thank all of you, without the intention or possibility to be complete. I would like to apologize to those who I did not mention by name here; however, I highly value your kind support. Firstly, I would like to deeply thank my thesis supervisor Prof. Brian Cusack for the exceptional support given during the thesis project. He provided me with the freedom to explore research directions and to choose the routes that I wanted to investigate. -

Fbi Fbi Flash
TLP: GREEN FBI FLASH FBI FBI Liaison Alert System #M-000045-TT The following information was obtained through FBI investigation and is provided in conjunction with the FBI’s statutory requirement to conduct victim notification as outlined in 42 USC § 10607. In furtherance of public-private partnerships, the FBI routinely advises private industry of various cyber threat indicators observed during the course of our investigations. This data is provided in order to help cyber security professionals and systems administrators to guard against the persistent malicious actions of cyber criminals. This product is released at TLP: GREEN. The information in this product is useful for the awareness of all participating organizations as well as with peers within the broader community or sector. Recipients may share this information with peers and partner organizations within their sector or community, but not via publicly accessible channels. SUMMARY The FBI is providing the following information with HIGH confidence: A group of cyber actors utilizing infrastructure located in Iran have been conducting computer network exploitation activity against public and private U.S. organizations, including Cleared Defense Contractors (CDCs), academic institutions, and energy sector companies. The actors typically utilize common computer intrusion techniques such as the use of TOR, open source reconnaissance, exploitation via SQL injection and web shells, and open source tools for further network penetration and persistence. Internet-facing infrastructures, such as web servers, are typical targets for this group. Once the actors penetrate a victim network, the actors exfiltrate network design information and legitimate user credentials for the victim network. Often times, the actors are able to harvest administrative user credentials and use the credentials to move laterally through a network. -

Enhancing the Security of AES Algorithm Using Quantum Three-Pass Protocol
International Journal of Security and Its Application Vol.11, No.1 (2017), pp.219-232 http://dx.doi.org/10.14257/ijsia.2017.11.1.18 Enhancing the Security of AES Algorithm using Quantum Three-Pass Protocol Rajeev Kumar Gupta*, R. K. Pateriya and Ankita Patil MANIT Bhopal, 462003, India [email protected], [email protected], [email protected] Abstract In this paper, a hybrid cryptosystem is presented combining classical cryptography with quantum cryptography, in which the secure key distribution between the parties utilizing AES cipher is performed using quantum three-pass protocol. This protocol guarantees the absolutely secure key transmission whose security relies on the no-cloning theorem of quantum mechanics. The key is transmitted in the form of polarized photons, which is further encrypted by rotating each photon by a certain angle. This key is utilized by AES (Advance encryption Standard) cryptosystem which is a symmetric block cipher whose strength relies on the substitution box (S-box) that introduces non linearity into the cryptosystem. The S-box used in the existing AES is fixed which may pose security threats if scrutinized by an attacker. Hence, in this paper, a key-dependent S-box is also proposed which is tested to satisfy the properties such as avalanche effect, strict avalanche criteria and confusion property. The results show that the proposed algorithm is effective for generating a key-dependent S-box and since the S-box is not pre-calculated, it can strengthen the AES cryptosystem against attacks launched by the fixed S-box analysis. Keywords: AES, Avalanche effect, Quantum key distribution, Quantum three-pass protocol, S-box. -

Lecture 15: Encryption and Anonymity
1 CS-340 Introduction to Computer Networking Lecture 15: Encryption and Anonymity Steve Tarzia Last Lecture: Ethernet Link Layer 2 • Link layer handles error detection and correction: Parity, Checksum, and Cyclic Redandancy Check (CRC). • Ethernet adds MAC addresses to identify src/dst on a shared link. • ARP uses Ethernet broadcast to find IP address → MAC address mapping • DHCP requests are sent by Ethernet broadcast (to FF:FF:FF:FF:FF:FF) • Old Ethernet hubs broadcasted data to all ports. • Ethernet switches learn/remember which MAC addresses are reachable on each port and relay traffic only to the appropriate ports. • Reduce broadcast traffic and eliminate collisions. • VLANs create multiple isolated LANs/subnets on one switch. • Data Centers & Supercomputers demand fast local networks. Network Security Overview 3 STOP Why is the STOP How would you and and define "network THINK Internet difficult THINK Goals security?" Challenges to secure? • Confidentiality: • Internet messages travel through Keep message private/secret. untrusted, 3rd-party links and routers. • Routers must see all bits of the packet to • Reliability: copy it to the next hop. Deliver message to the intended recipient. Don't drop it! • Local networks use shared media. • Nearby Ethernet or WiFi hosts can often • Integrity: see your packets. Deliver message without alteration. • DNS may be poisoned, sending you to the • Authentication: wrong IP address. Verify the identity of the endpoint I’m communicating with. • Individual attackers, corporations, and governments all wish to violate your • Anonymity: network security. Conceal relationship between two Internet hosts. Conceal who I am talking to. • IP packets must be addressed to reach destination. -

Analysis and Processing of Cryptographic Protocols
Analysis and Processing of Cryptographic Protocols Submitted in partial fulfilment of the requirements of the degree of Bachelor of Science (Honours) of Rhodes University Bradley Cowie Grahamstown, South Africa November 2009 Abstract The field of Information Security and the sub-field of Cryptographic Protocols are both vast and continually evolving fields. The use of cryptographic protocols as a means to provide security to web servers and services at the transport layer, by providing both en- cryption and authentication to data transfer, has become increasingly popular. However, it is noted that it is rather difficult to perform legitimate analysis, intrusion detection and debugging on data that has passed through a cryptographic protocol as it is encrypted. The aim of this thesis is to design a framework, named Project Bellerophon, that is capa- ble of decrypting traffic that has been encrypted by an arbitrary cryptographic protocol. Once the plain-text has been retrieved further analysis may take place. To aid in this an in depth investigation of the TLS protocol was undertaken. This pro- duced a detailed document considering the message structures and the related fields con- tained within these messages which are involved in the TLS handshake process. Detailed examples explaining the processes that are involved in obtaining and generating the var- ious cryptographic components were explored. A systems design was proposed, considering the role of each of the components required in order to produce an accurate decryption of traffic encrypted by a cryptographic protocol. Investigations into the accuracy and the efficiency of Project Bellerophon to decrypt specific test data were conducted. -

Download CVS 1.11.1P1-3 From: Ftp://Ftp.Software.Ibm.Com/Aix/Freesoftware/Aixtoolbox/RPMS/Ppc/Cvs/ Cvs-1.11.1P1-3.Aix4.3.Ppc.Rpm
2003 CERT Advisories CERT Division [DISTRIBUTION STATEMENT A] Approved for public release and unlimited distribution. http://www.sei.cmu.edu REV-03.18.2016.0 Copyright 2017 Carnegie Mellon University. All Rights Reserved. This material is based upon work funded and supported by the Department of Defense under Contract No. FA8702-15-D-0002 with Carnegie Mellon University for the operation of the Software Engineering Institute, a federally funded research and development center. The view, opinions, and/or findings contained in this material are those of the author(s) and should not be con- strued as an official Government position, policy, or decision, unless designated by other documentation. References herein to any specific commercial product, process, or service by trade name, trade mark, manu- facturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by Carnegie Mellon University or its Software Engineering Institute. This report was prepared for the SEI Administrative Agent AFLCMC/AZS 5 Eglin Street Hanscom AFB, MA 01731-2100 NO WARRANTY. THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN "AS-IS" BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. [DISTRIBUTION STATEMENT A] This material has been approved for public release and unlimited distribu- tion. Please see Copyright notice for non-US Government use and distribution.