Appway Platform (Core)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Computer Essentials – Session 1 – Step-By-Step Guide
Computer Essentials – Session 1 – Step-by-Step Guide Note: Completing the Mouse Tutorial and Mousercise exercise which are available on the Class Resources webpage constitutes the first part of this lesson. ABOUT PROGRAMS AND OPERATING SYSTEMS Any time a task is performed on a computer, it is done through a program. For the user, the program is the application – the tool – for accomplishing a task. For the computer, it is a set of instructions on knowing how to perform this task. Examples of programs include Internet Explorer and Microsoft Word. The most important program overall is the operating system, which manages all of the computer’s resources and decides how to treat input from the user. There are several different operating systems in circulation, such as Mac O/S and Linux. However, far and away, the most commonly-used operating system is Microsoft Windows. (Note that Microsoft is just the name of the company that makes Windows, and that there are several versions of Windows. In 2012 all the computers in the lab were updated to the version of Windows called Windows 7. If you have some experience with the older versions of Windows you will notice that things look a bit different on a computer running Windows 7. THE WINDOWS 7 ENVIRONMENT The Desktop The first thing you see when you log on to the computer is the DESKTOP. The Desktop is the display area you see when Windows opens. The following items are the most common items that can be found on the desktop: Mouse pointer Icons Shortcuts to Storage drives Notification Start Button Taskbar tray Show Desktop/Peek button Andrea Philo September 2012 Page 1 of 13 Montgomery County-Norristown Public Library Computer Essentials – Session 1 – Step-by-Step Guide Parts of the Windows 7 Desktop Icon: A picture representing a program or file or places to store files. -

Adding the Maine Prescription Monitoring System As a Favorite
Adding the Maine Prescription Monitoring System as a Favorite Beginning 1/1/17 all newly prescribed narcotic medications ordered when discharging a patient from the Emergency Department or an Inpatient department must be recorded in the Maine prescription monitoring system (Maine PMP). Follow these steps to access the Maine PMP site from the SeHR/Epic system and create shortcuts to the activity to simplify access. Access the Maine PMP site from hyperspace 1. Follow this path for the intial launch of the Maine PMP site: Epic>Help>Maine PMP Program Please note: the Maine PMP database is managed and maintained by the State of Maine and does NOT support single-sign on 2. Click Login to enter your Maine PMP user name and password a. If you know your user name and password, click Login b. To retrieve your user name click Retrieve User Name c. To retrieve your password click Retrieve Password Save the Maine PMP site as a favorite under the Epic button After accessing the site from the Epic menu path you can make the link a favorite under the Epic menu. 1. Click the Epic button, the Maine PMP program hyperlink will appear under your Recent activities, click the Star icon to save it as a favorite. After staring the activity it becomes a favorite stored under the Epic button Save the Maine PMP site as a Quick Button on your Epic Toolbar After accessing the site from the Epic menu path you may choose to make the Maine PMP hyperlink a quick button on your main Epic toolbar. -

Line 6 POD Go Owner's Manual
® 16C Two–Plus Decades ACTION 1 VIEW Heir Stereo FX Cali Q Apparent Loop Graphic Twin Transistor Particle WAH EXP 1 PAGE PAGE Harmony Tape Verb VOL EXP 2 Time Feedback Wow/Fluttr Scale Spread C D MODE EDIT / EXIT TAP A B TUNER 1.10 OWNER'S MANUAL 40-00-0568 Rev B (For use with POD Go Firmware 1.10) ©2020 Yamaha Guitar Group, Inc. All rights reserved. 0•1 Contents Welcome to POD Go 3 The Blocks 13 Global EQ 31 Common Terminology 3 Input and Output 13 Resetting Global EQ 31 Updating POD Go to the Latest Firmware 3 Amp/Preamp 13 Global Settings 32 Top Panel 4 Cab/IR 15 Rear Panel 6 Effects 17 Restoring All Global Settings 32 Global Settings > Ins/Outs 32 Quick Start 7 Looper 22 Preset EQ 23 Global Settings > Preferences 33 Hooking It All Up 7 Wah/Volume 24 Global Settings > Switches/Pedals 33 Play View 8 FX Loop 24 Global Settings > MIDI/Tempo 34 Edit View 9 U.S. Registered Trademarks 25 USB Audio/MIDI 35 Selecting Blocks/Adjusting Parameters 9 Choosing a Block's Model 10 Snapshots 26 Hardware Monitoring vs. DAW Software Monitoring 35 Moving Blocks 10 Using Snapshots 26 DI Recording and Re-amping 35 Copying/Pasting a Block 10 Saving Snapshots 27 Core Audio Driver Settings (macOS only) 37 Preset List 11 Tips for Creative Snapshot Use 27 ASIO Driver Settings (Windows only) 37 Setlist and Preset Recall via MIDI 38 Saving/Naming a Preset 11 Bypass/Control 28 TAP Tempo 12 Snapshot Recall via MIDI 38 The Tuner 12 Quick Bypass Assign 28 MIDI CC 39 Quick Controller Assign 28 Additional Resources 40 Manual Bypass/Control Assignment 29 Clearing a Block's Assignments 29 Clearing All Assignments 30 Swapping Stomp Footswitches 30 ©2020 Yamaha Guitar Group, Inc. -

EFI Printsmith Vision Four51 Integration Guide
Four51 Integration Guide PrintSmith Vision Version 3.0 June / 2015 2 EFI PrintSmith Vision | Four51 Integration Guide Copyright © 1997 - 2015 by Electronics for Imaging, Inc. All Rights Reserved. EFI PrintSmith Vision | Four51 Integration Guide July 2015 PrintSmith Vision 3.0 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, 6,278,901, 6,279,009, 6,289,122, 6,292,270, 6,299,063, 6,310,697, -

Basic Computer Lesson
Table of Contents MICROSOFT WORD 1 ONE LINC What is MSWord? MSWord is a word-processing program that allows users to create, edit, and enhance text in a variety of formats. Word is a powerful word processor with sophisticated editing and formatting as well as graphic- enhancement capabilities. Word is a good program for novice users since it is relatively easy to learn and can be integrated with language learning. Word processing has become popular due to its wide range of personal, business, and other applications. ESL learners, like others, need word processing for job search, employment, and personal purposes. Word-processing skills have become the backbone of computer literacy skills. Features PARTS OF THE SCREEN The Word screen can be overwhelming for novice learners. The numerous bars on the screen such as toolbars, scroll bars, and status bar confuse learners who are using Word for the first time. It is important that learners become familiar with parts of the screen and understand the function of each toolbar but we recommend that the Standard and Formatting toolbars as well as the Status bar be hidden for LINC One level. Menu bar Title bar Minimize Restore Button Button Close Word Close current Rulers document Insertion Point (cursor) Vertical scroll bar Editing area Document Status bar Horizontal Views scroll bar A SOFTWARE GUIDE FOR LINC INSTRUCTORS 131 1 MICROSOFT WORD Hiding Standard toolbar, Formatting toolbar, and Status bar: • To hide the Standard toolbar, click View | Toolbars on the Menu bar. Check off Standard. LINC ONE LINC • To hide the Formatting toolbar, click View | Toolbars on the Menu bar. -
Acrobuttons Quick Start Tutorial
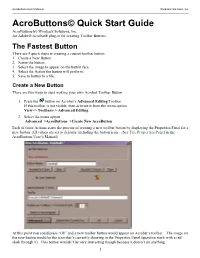
AcroButtons User’s Manual WindJack Solutions, Inc. AcroButtons© Quick Start Guide AcroButtons by Windjack Solutions, Inc. An Adobe® Acrobat® plug-in for creating Toolbar Buttons. The Fastest Button There are 5 quick steps to creating a custom toolbar button.. 1. Create a New Button 2. Name the button. 3. Select the image to appear on the button face. 4. Select the Action the button will perform. 5. Save to button to a file. Create a New Button There are two ways to start making your own Acrobat Toolbar Button. 1. Press the button on Acrobat’s Advanced Editing Toolbar. If this toolbar is not visible, then activate it from the menu option View–> Toolbars–> Advanced Editing. 2. Select the menu option Advanced–>AcroButtons–>Create New AcroButton Each of these Actions starts the process of creating a new toolbar button by displaying the Properties Panel for a new button. All values are set to defaults, including the button icon. (See The Properties Panel in the AcroButtons User’s Manual) At this point you could press “Ok” and a new toolbar button would appear on Acrobat’s toolbar. The image on the new button would be the icon that’s currently showing in the Properties Panel (question mark with a red slash through it). This button wouldn’t be very interesting though because it doesn’t do anything. 1 AcroButtons User’s Manual WindJack Solutions, Inc. Name the Button Change the default name, “Untitled0”, to something more descriptive. For this example change it to “NextPage”. The button’s name is important for several different reasons. -

HTML Viewer Page 5
HTML Report Viewer Version: 18.1 Copyright © 2015 Intellicus Technologies This document and its content is copyrighted material of Intellicus Technologies. The content may not be copied or derived from, through any means, in parts or in whole, without a prior written permission from Intellicus Technologies. All other product names are believed to be registered trademarks of the respective companies. Dated: August 2015 Acknowledgements Intellicus acknowledges using of third-party libraries to extend support to the functionalities that they provide. For details, visit: http://www.intellicus.com/acknowledgements.htm 2 Contents 1 HTML Report Viewer 4 HTML Viewer page 5 Navigate 6 Table of Contents 7 Refresh the report 8 Collaborate 8 Email 8 Upload 9 Print 10 Publish 12 Export 13 View Alerts 14 3 1 HTML Report Viewer Reports are displayed in HTML Viewer when you select View > HTML option on Report Delivery Options page. Figure 1: View > HTML on Report Delivery Options page In addition to viewing a report, you can carry out following activities on HTML Viewer: • Navigate • Refresh the report • Collaborate • Email • Print • Publish • Export • Upload • View Alerts You can initiate any of these activities by clicking respective tool button from the toolbar. 4 HTML Viewer page Depending on the report being viewed and the steps taken as post-view operations, it may have multiple components on it: Toolbar Explore Pane Page area Figure 2: HTML Viewer HTML Viewer has mainly three components. On the top, it has toolbar having buttons for all the operations that can be done on the Viewer. The Explore pane appears on the left side of the window. -

Introduction to Office 2007 the Ribbon Home
Introduction to Office 2007 Introduction to Office 2007 class will show what’s different in Office 2007. The Ribbon at the top of the page has replaced menus and toolbars in Word, Excel, PowerPoint, Access and new messages in Outlook. This class will cover the use of the Ribbon, the Office Button (where is the File menu?), getting Help and online Training, the Mini Toolbar, the Quick Access Toolbar, new File Formats, and a Few Fun Features. The class and short handout are designed so when you return to your desk you can begin using the Office 2007 products. There are three major differences in Office 2007, the Ribbon, the Office Button and the new file formats. The Ribbon The Ribbon at the top of the page has replaced menus and toolbars in Word, Excel, PowerPoint, Access and new messages in Outlook. Commands – Are buttons, menus or boxes where you enter information. Groups – Are sets of related commands. Tabs – Represent core tasks. Home Tab Try it: 1. Start Word 2007, Excel 2007 & PowerPoint 2007. 2. Click on each tab to display different groups of commands. 3. Hover over a command for Enhanced Toolbar Tips. Note: keyboard shortcuts are shown if available. The Home Tab displays the most commonly used commands. In Word and Excel these include Copy, Cut, and Paste, Bold, Italic, Underscore etc. The commands are arranged in groups: Clipboard, Font, Paragraph, Styles and Editing. The most frequently used commands, Paste, Cut and Copy, are the left most in the first group in the Home Tab. The less frequently used commands or command choices can Try it: 1. -

Microtemporality: at the Time When Loading-In-Progress
Microtemporality: At The Time When Loading-in-progress Winnie Soon School of Communication and Culture, Aarhus University [email protected] Abstract which data processing and code inter-actions are Loading images and webpages, waiting for social media feeds operated in real-time. The notion of inter-actions mainly and streaming videos and multimedia contents have become a draws references from the notion of "interaction" from mundane activity in contemporary culture. In many situations Computer Science and the notion of "intra-actions" from nowadays, users encounter a distinctive spinning icon during Philosophy. [3][4][5] The term code inter-actions the loading, waiting and streaming of data content. A highlights the operational process of things happen graphically animated logo called throbber tells users something within, and across, machines through different technical is loading-in-progress, but nothing more. This article substrates, and hence produce agency. investigates the process of data buffering that takes place behind a running throbber. Through artistic practice, an experimental project calls The Spinning Wheel of Life explores This article is informed by artistic practice, including the temporal and computational complexity of buffering. The close reading of a throbber and its operational logics of article draws upon Wolfgang Ernst’s concept of data buffering, as well as making and coding of a “microtemporality,” in which microscopic temporality is throbber. These approaches, following the tradition of expressed through operational micro events. [1] artistic research, allow the artist/researcher to think in, Microtemporality relates to the nature of signals and through and with art. [7] Such mode of inquiry questions communications, mathematics, digital computation and the invisibility of computational culture. -

Automated Malware Analysis Report For
ID: 219320 Cookbook: browseurl.jbs Time: 00:06:44 Date: 01/04/2020 Version: 28.0.0 Lapis Lazuli Table of Contents Table of Contents 2 Analysis Report http://ib.adnxs.com 4 Overview 4 General Information 4 Detection 5 Confidence 5 Classification Spiderchart 6 Analysis Advice 6 Mitre Att&ck Matrix 7 Signature Overview 7 Networking: 7 System Summary: 7 Malware Analysis System Evasion: 8 Malware Configuration 8 Behavior Graph 8 Simulations 8 Behavior and APIs 8 Antivirus, Machine Learning and Genetic Malware Detection 8 Initial Sample 8 Dropped Files 9 Unpacked PE Files 9 Domains 9 URLs 9 Yara Overview 10 Initial Sample 10 PCAP (Network Traffic) 10 Dropped Files 10 Memory Dumps 10 Unpacked PEs 10 Sigma Overview 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 10 Dropped Files 11 Screenshots 11 Thumbnails 11 Startup 12 Created / dropped Files 12 Domains and IPs 41 Contacted Domains 41 Contacted URLs 41 URLs from Memory and Binaries 42 Contacted IPs 44 Public 44 Static File Info 45 No static file info 45 Network Behavior 45 Network Port Distribution 45 TCP Packets 45 UDP Packets 47 DNS Queries 49 DNS Answers 49 HTTP Request Dependency Graph 53 HTTP Packets 53 HTTPS Packets 54 Copyright Joe Security LLC 2020 Page 2 of 64 Code Manipulations 63 Statistics 63 Behavior 63 System Behavior 63 Analysis Process: iexplore.exe PID: 4776 Parent PID: 696 63 General 63 File Activities 63 Registry Activities 64 Analysis Process: iexplore.exe PID: 2872 Parent PID: 4776 64 General 64 File Activities 64 Registry Activities 64 Disassembly -

Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software comes with more or less unwanted add-ons or browser toolbars. These are quite annoying because they may: Change your homepage and your search engine without your permission or awareness Track your browsing activities and searches Display annoying ads and manipulate search results Take up a lot of (vertical) space inside the browser Slow down your browser and degrade your browsing experience Fight against each other and make normal add-on handling difficult or impossible Become difficult or even impossible for the average user to fully uninstall Toolbars are not technically not a virus, but they do exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program. Generally speaking, toolbars are ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer, Firefox and Chrome, and distributed through various monetization platforms during installation. Very often users have no idea where did it come from, so it’s not surprising at all that most of them assume that the installed toolbar is a virus. For example, when you install iLivid Media Player, you will also agree to change your browser homepage to search.conduit.com, set your default search engine to Conduit Search, and install the AVG Search-Results Toolbar. -

Geotool Software User Tutorial
IDC/SA/SI February, 2013 English only Geotool Software User Tutorial This document contains the Geotool software user tutorial. The tutorial is divided into a set of exercises that can be followed individually. Together, the exercises cover the full functionality of the system. Summary Geotool is a software system that allows a user to interactively display and process seismoacoustic data from International Monitoring System (IMS) stations. The software can be customised and extended. This tutorial instructs users how to use the basic features of Geotool including data input, basic waveform handling, filters, and arrivals. Geotool has many other capabilities that are not covered here. IDC/SA/SI Page 2 Document history Version Date Author Description 1.0 13.07.2007. Vera Miljanovic Software User Tutorial 2.0 12.08.2009. Vera Miljanovic Updated Tutorial and rewrote Arrivals section 3.0 13.05.2010. Vera Miljanovic Updated Tutorial 4.0 12.10.2010. Vera Miljanovic Updated Tutorial 5.0 10.11.2011 Vera Miljanovic Revisions based on the latest software version 6.0 07.03.2012 Vera Miljanovic Revisions based on the latest software version 7.0 23.01.2013 Vera Miljanovic Revisions based on the latest software version 8.0 08.02.2013 Vera Miljanovic Added Add Station section 9.0 18.02.2013 Remmy Phiri Added Print bulletin section IDC Page 3 Contents SUMMARY 1 DOCUMENT HISTORY 2 CONTENTS 3 1. SCOPE 7 1.1. Identification 7 1.2. System overview 7 1.3. Document overview 7 2. INTRODUCTION 8 2.1. Getting Started with Geotool 8 SECTION 1.