IBM CICS TS for Z/VSE V2R1: Enhancements Guide EXEC Interface Block
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SATELLITES at WORK Space in the Seventies
SaLf ILMITRATBONS REPROMhdONkp N BLACK ANd WHiT? SATELLITES AT WORK Space in the Seventies 4 (SPACE IN N72-13 8 6 6 (NASA-EP-8 ) SATELLITES AT WORK THE SEVENTIES) W.R. Corliss (NASA) Jun. 1971 29 p CSCL 22B Unclas Reproduced by G3/31 11470 NATIONAL TECHNICAL u. INFORMATION SERVICE U S Department of Commerce Springfield VA 22151 J National Aeronautics and Space Administration SPACE IN THE SEVENTIES Man has walked on the Moon, made scientific observations there, and brought back to Earth samples of the lunar surface. Unmanned scientific spacecraft have probed for facts about matter, radiation and magnetism in space, and have collected data relating to the Moon, Venus, Mars, the Sun and some of the stars, and reported their findings to ground stations on Earth. Spacecraft have been put into orbit around the Earth as weather observation stations, as communications relay stations for a world-wide telephone and television network, and as aids to navigation. In addition, the space program has accelerated the advance of technology for science and industry, contributing many new ideas, processes and materials. All this took place in the decade of the Sixties. What next? What may be expected of space exploration in the Seventies? NASA has prepared a series of publications and motion pictures to provide a look forward to SPACE IN THE SEVENTIES. The topics covered in this series include: Earth orbital science; planetary exploration; practical applications of satellites; technology utilization; man in space; and aeronautics. SPACE IN THE SEVENTIES presents the planned programs of NASA for the coming decade. -
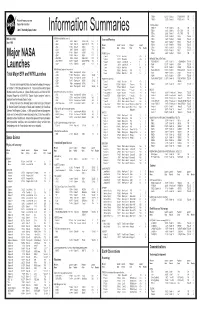
Information Summaries
TIROS 8 12/21/63 Delta-22 TIROS-H (A-53) 17B S National Aeronautics and TIROS 9 1/22/65 Delta-28 TIROS-I (A-54) 17A S Space Administration TIROS Operational 2TIROS 10 7/1/65 Delta-32 OT-1 17B S John F. Kennedy Space Center 2ESSA 1 2/3/66 Delta-36 OT-3 (TOS) 17A S Information Summaries 2 2 ESSA 2 2/28/66 Delta-37 OT-2 (TOS) 17B S 2ESSA 3 10/2/66 2Delta-41 TOS-A 1SLC-2E S PMS 031 (KSC) OSO (Orbiting Solar Observatories) Lunar and Planetary 2ESSA 4 1/26/67 2Delta-45 TOS-B 1SLC-2E S June 1999 OSO 1 3/7/62 Delta-8 OSO-A (S-16) 17A S 2ESSA 5 4/20/67 2Delta-48 TOS-C 1SLC-2E S OSO 2 2/3/65 Delta-29 OSO-B2 (S-17) 17B S Mission Launch Launch Payload Launch 2ESSA 6 11/10/67 2Delta-54 TOS-D 1SLC-2E S OSO 8/25/65 Delta-33 OSO-C 17B U Name Date Vehicle Code Pad Results 2ESSA 7 8/16/68 2Delta-58 TOS-E 1SLC-2E S OSO 3 3/8/67 Delta-46 OSO-E1 17A S 2ESSA 8 12/15/68 2Delta-62 TOS-F 1SLC-2E S OSO 4 10/18/67 Delta-53 OSO-D 17B S PIONEER (Lunar) 2ESSA 9 2/26/69 2Delta-67 TOS-G 17B S OSO 5 1/22/69 Delta-64 OSO-F 17B S Pioneer 1 10/11/58 Thor-Able-1 –– 17A U Major NASA 2 1 OSO 6/PAC 8/9/69 Delta-72 OSO-G/PAC 17A S Pioneer 2 11/8/58 Thor-Able-2 –– 17A U IMPROVED TIROS OPERATIONAL 2 1 OSO 7/TETR 3 9/29/71 Delta-85 OSO-H/TETR-D 17A S Pioneer 3 12/6/58 Juno II AM-11 –– 5 U 3ITOS 1/OSCAR 5 1/23/70 2Delta-76 1TIROS-M/OSCAR 1SLC-2W S 2 OSO 8 6/21/75 Delta-112 OSO-1 17B S Pioneer 4 3/3/59 Juno II AM-14 –– 5 S 3NOAA 1 12/11/70 2Delta-81 ITOS-A 1SLC-2W S Launches Pioneer 11/26/59 Atlas-Able-1 –– 14 U 3ITOS 10/21/71 2Delta-86 ITOS-B 1SLC-2E U OGO (Orbiting Geophysical -

Photographs Written Historical and Descriptive
CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY HAER FL-8-B BUILDING AE HAER FL-8-B (John F. Kennedy Space Center, Hanger AE) Cape Canaveral Brevard County Florida PHOTOGRAPHS WRITTEN HISTORICAL AND DESCRIPTIVE DATA HISTORIC AMERICAN ENGINEERING RECORD SOUTHEAST REGIONAL OFFICE National Park Service U.S. Department of the Interior 100 Alabama St. NW Atlanta, GA 30303 HISTORIC AMERICAN ENGINEERING RECORD CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY BUILDING AE (Hangar AE) HAER NO. FL-8-B Location: Hangar Road, Cape Canaveral Air Force Station (CCAFS), Industrial Area, Brevard County, Florida. USGS Cape Canaveral, Florida, Quadrangle. Universal Transverse Mercator Coordinates: E 540610 N 3151547, Zone 17, NAD 1983. Date of Construction: 1959 Present Owner: National Aeronautics and Space Administration (NASA) Present Use: Home to NASA’s Launch Services Program (LSP) and the Launch Vehicle Data Center (LVDC). The LVDC allows engineers to monitor telemetry data during unmanned rocket launches. Significance: Missile Assembly Building AE, commonly called Hangar AE, is nationally significant as the telemetry station for NASA KSC’s unmanned Expendable Launch Vehicle (ELV) program. Since 1961, the building has been the principal facility for monitoring telemetry communications data during ELV launches and until 1995 it processed scientifically significant ELV satellite payloads. Still in operation, Hangar AE is essential to the continuing mission and success of NASA’s unmanned rocket launch program at KSC. It is eligible for listing on the National Register of Historic Places (NRHP) under Criterion A in the area of Space Exploration as Kennedy Space Center’s (KSC) original Mission Control Center for its program of unmanned launch missions and under Criterion C as a contributing resource in the CCAFS Industrial Area Historic District. -

<> CRONOLOGIA DE LOS SATÉLITES ARTIFICIALES DE LA
1 SATELITES ARTIFICIALES. Capítulo 5º Subcap. 10 <> CRONOLOGIA DE LOS SATÉLITES ARTIFICIALES DE LA TIERRA. Esta es una relación cronológica de todos los lanzamientos de satélites artificiales de nuestro planeta, con independencia de su éxito o fracaso, tanto en el disparo como en órbita. Significa pues que muchos de ellos no han alcanzado el espacio y fueron destruidos. Se señala en primer lugar (a la izquierda) su nombre, seguido de la fecha del lanzamiento, el país al que pertenece el satélite (que puede ser otro distinto al que lo lanza) y el tipo de satélite; este último aspecto podría no corresponderse en exactitud dado que algunos son de finalidad múltiple. En los lanzamientos múltiples, cada satélite figura separado (salvo en los casos de fracaso, en que no llegan a separarse) pero naturalmente en la misma fecha y juntos. NO ESTÁN incluidos los llevados en vuelos tripulados, si bien se citan en el programa de satélites correspondiente y en el capítulo de “Cronología general de lanzamientos”. .SATÉLITE Fecha País Tipo SPUTNIK F1 15.05.1957 URSS Experimental o tecnológico SPUTNIK F2 21.08.1957 URSS Experimental o tecnológico SPUTNIK 01 04.10.1957 URSS Experimental o tecnológico SPUTNIK 02 03.11.1957 URSS Científico VANGUARD-1A 06.12.1957 USA Experimental o tecnológico EXPLORER 01 31.01.1958 USA Científico VANGUARD-1B 05.02.1958 USA Experimental o tecnológico EXPLORER 02 05.03.1958 USA Científico VANGUARD-1 17.03.1958 USA Experimental o tecnológico EXPLORER 03 26.03.1958 USA Científico SPUTNIK D1 27.04.1958 URSS Geodésico VANGUARD-2A -

Index of Astronomia Nova
Index of Astronomia Nova Index of Astronomia Nova. M. Capderou, Handbook of Satellite Orbits: From Kepler to GPS, 883 DOI 10.1007/978-3-319-03416-4, © Springer International Publishing Switzerland 2014 Bibliography Books are classified in sections according to the main themes covered in this work, and arranged chronologically within each section. General Mechanics and Geodesy 1. H. Goldstein. Classical Mechanics, Addison-Wesley, Cambridge, Mass., 1956 2. L. Landau & E. Lifchitz. Mechanics (Course of Theoretical Physics),Vol.1, Mir, Moscow, 1966, Butterworth–Heinemann 3rd edn., 1976 3. W.M. Kaula. Theory of Satellite Geodesy, Blaisdell Publ., Waltham, Mass., 1966 4. J.-J. Levallois. G´eod´esie g´en´erale, Vols. 1, 2, 3, Eyrolles, Paris, 1969, 1970 5. J.-J. Levallois & J. Kovalevsky. G´eod´esie g´en´erale,Vol.4:G´eod´esie spatiale, Eyrolles, Paris, 1970 6. G. Bomford. Geodesy, 4th edn., Clarendon Press, Oxford, 1980 7. J.-C. Husson, A. Cazenave, J.-F. Minster (Eds.). Internal Geophysics and Space, CNES/Cepadues-Editions, Toulouse, 1985 8. V.I. Arnold. Mathematical Methods of Classical Mechanics, Graduate Texts in Mathematics (60), Springer-Verlag, Berlin, 1989 9. W. Torge. Geodesy, Walter de Gruyter, Berlin, 1991 10. G. Seeber. Satellite Geodesy, Walter de Gruyter, Berlin, 1993 11. E.W. Grafarend, F.W. Krumm, V.S. Schwarze (Eds.). Geodesy: The Challenge of the 3rd Millennium, Springer, Berlin, 2003 12. H. Stephani. Relativity: An Introduction to Special and General Relativity,Cam- bridge University Press, Cambridge, 2004 13. G. Schubert (Ed.). Treatise on Geodephysics,Vol.3:Geodesy, Elsevier, Oxford, 2007 14. D.D. McCarthy, P.K. -

Legacy Image
NASA SP17069 NASA Thesaurus Astronomy Vocabulary Scientific and Technical Information Division 1988 National Aeronautics and Space Administration Washington, M= . ' NASA SP-7069 NASA Thesaurus Astronomy Vocabulary A subset of the NASA Thesaurus prepared for the international Astronomical Union Conference July 27-31,1988 This publication was prepared by the NASA Scientific and Technical Information Facility operated for the National Aeronautics and Space Administration by RMS Associates. INTRODUCTION The NASA Thesaurus Astronomy Vocabulary consists of terms used by NASA indexers as descriptors for astronomy-related documents. The terms are presented in a hierarchical format derived from the 1988 edition of the NASA Thesaurus Volume 1 -Hierarchical Listing. Main (postable) terms and non- postable cross references are listed in alphabetical order. READING THE HIERARCHY Each main term is followed by a display of its context within a hierarchy. USE references, UF (used for) references, and SN (scope notes) appear immediately below the main term, followed by GS (generic structure), the hierarchical display of term relationships. The hierarchy is headed by the broadest term within that hierarchy. Terms that are broader in meaning than the main term are listed . above the main term; terms narrower in meaning are listed below the main term. The term itself is in boldface for easy identification. Finally, a list of related terms (RT) from other hierarchies is provided. Within a hierarchy, the number of dots to the left of a term indicates its hierarchical level - the more dots, the lower the level (i.e., the narrower the meaning of the term). For example, the term "ELLIPTICAL GALAXIES" which is preceded by two dots is narrower in meaning than "GALAXIES"; this in turn is narrower than "CELESTIAL BODIES". -

United States Space Program Firsts
KSC Historical Report 18 KHR-18 Rev. December 2003 UNITED STATES SPACE PROGRAM FIRSTS Robotic & Human Mission Firsts Kennedy Space Center Library Archives Kennedy Space Center, Florida Foreword This summary of the United States space program firsts was compiled from various reference publications available in the Kennedy Space Center Library Archives. The list is divided into four sections. Robotic mission firsts, Human mission firsts, Space Shuttle mission firsts and Space Station mission firsts. Researched and prepared by: Barbara E. Green Kennedy Space Center Library Archives Kennedy Space Center, Florida 32899 phone: [321] 867-2407 i Contents Robotic Mission Firsts ……………………..........................……………...........……………1-4 Satellites, missiles and rockets 1950 - 1986 Early Human Spaceflight Firsts …………………………............................……........…..……5-8 Projects Mercury, Gemini, Apollo, Skylab and Apollo Soyuz Test Project 1961 - 1975 Space Shuttle Firsts …………………………….........................…………........……………..9-12 Space Transportation System 1977 - 2003 Space Station Firsts …………………………….........................…………........………………..13 International Space Station 1998-2___ Bibliography …………………………………..............................…………........…………….....…14 ii KHR-18 Rev. December 2003 DATE ROBOTIC EVENTS MISSION 07/24/1950 First missile launched at Cape Canaveral. Bumper V-2 08/20/1953 First Redstone missile was fired. Redstone 1 12/17/1957 First long range weapon launched. Atlas ICBM 01/31/1958 First satellite launched by U.S. Explorer 1 10/11/1958 First observations of Earth’s and interplanetary magnetic field. Pioneer 1 12/13/1958 First capsule containing living cargo, squirrel monkey, Gordo. Although not Bioflight 1 a NASA mission, data was utilized in Project Mercury planning. 12/18/1958 First communications satellite placed in space. Once in place, Brigadier Project Score General Goodpaster passed a message to President Eisenhower 02/17/1959 First fully instrumented Vanguard payload. -

Diagnostics – Explorers
EXPLORERS For diagnosing calculus and caries and exploring of pockets, restorations and furcations. DIAGNOSTICS – EXPLORERS Explorer 5-9 Explorer 17-23 Explorer 3-6 LMErgoSense LM 5-9 ES LMErgoSense LM 17-23 ES LMErgoSense LM 3-6 ES LMErgoMax LM 5-9 XSI LMErgoMax LM 17-23 XSI LMErgoMax LM 3-6 XSI LMErgoNorm LM 5-9 SI LMErgoNorm LM 17-23 SI LMErgoNorm LM 3-6 SI - For distal surfaces (17) - Standard explorer for diagnostic and - Standard explorer for diagnostic - Elongated lower shank and “back-action” blade (17) operative procedures and operative procedures - For areas in the vicinity of proximal contact surfaces (17) - Also for probing occlusal surface grooves (23) - For detecting subgingival calculus (23) Especially for Especially for For subgingival probing distal probing distal root surfaces of surfaces. examination. posterior teeth. Explorer 5-8 Explorer, centered 9-17C Explorer 17C-23 Explorer 11-12 LMErgoSense LM 5-8 ES LMErgoSense LM 9-17C ES LMErgoSense LM 17C-23 ES LMErgoSense LM 11-12 ES LMErgoMax LM 5-8 XSI LMErgoMax LM 9-17C XSI LMErgoMax LM 17C-23 XSI LMErgoMax LM 11-12 XSI LMErgoNorm LM 5-8 SI LMErgoNorm LM 9-17C SI LMErgoNorm LM 17C-23 SI LMErgoNorm LM 11-12 SI - Centered tip (17C) - For distal surfaces (17C) - Angles similar to Gracey 11/12 - Standard explorer for diagnostic - Elongated lower shank - Centered tip (17C) - For probing proximal and cervical and operative procedures and “back-action” blade - For areas in the vicinity of proximal contact surfaces (17C) caries - Also for probing occlusal surface grooves (23) - For detecting subgingival calculus (23) 11 DIAGNOSTICS – EXPLORERS TOP FAVORITE Handle options: High sensitivity Flexplorer 11F-12F Explorer 18-19 Explorer 29 at seams. -

NASA Is Not Archiving All Potentially Valuable Data
‘“L, United States General Acchunting Office \ Report to the Chairman, Committee on Science, Space and Technology, House of Representatives November 1990 SPACE OPERATIONS NASA Is Not Archiving All Potentially Valuable Data GAO/IMTEC-91-3 Information Management and Technology Division B-240427 November 2,199O The Honorable Robert A. Roe Chairman, Committee on Science, Space, and Technology House of Representatives Dear Mr. Chairman: On March 2, 1990, we reported on how well the National Aeronautics and Space Administration (NASA) managed, stored, and archived space science data from past missions. This present report, as agreed with your office, discusses other data management issues, including (1) whether NASA is archiving its most valuable data, and (2) the extent to which a mechanism exists for obtaining input from the scientific community on what types of space science data should be archived. As arranged with your office, unless you publicly announce the contents of this report earlier, we plan no further distribution until 30 days from the date of this letter. We will then give copies to appropriate congressional committees, the Administrator of NASA, and other interested parties upon request. This work was performed under the direction of Samuel W. Howlin, Director for Defense and Security Information Systems, who can be reached at (202) 275-4649. Other major contributors are listed in appendix IX. Sincerely yours, Ralph V. Carlone Assistant Comptroller General Executive Summary The National Aeronautics and Space Administration (NASA) is respon- Purpose sible for space exploration and for managing, archiving, and dissemi- nating space science data. Since 1958, NASA has spent billions on its space science programs and successfully launched over 260 scientific missions. -
NASA Major Launch Record
NASA Major Launch Record 1958 MISSION/ LAUNCH LAUNCH PERIOD CURRENT ORBITAL PARAMETERS WEIGHT REMARKS Intl Design VEHICLE DATE (Mins.) Apogee (km) Perigee (km) Incl (deg) (kg) (All Launches from ESMC, unless otherwise noted) 1958 1958 Pioneer I (U) Thor-Able I Oct 11 DOWN OCT 12, 1958 34.2 Measure magnetic fields around Earth or Moon. Error in burnout Eta I 130 (U) velocity and angle; did not reach Moon. Returned 43 hours of data on extent of radiation band, hydromagnetic oscillations of magnetic field, density of micrometeors in interplanetary space, and interplanetary magnetic field. Beacon I (U) Jupiter C Oct 23 DID NOT ACHIEVE ORBIT 4.2 Thin plastic sphere (12-feet in diameter after inflation) to study (U) atmosphere density at various levels. Upper stages and payload separated prior to first-stage burnout. Pioneer II (U) Thor-Able I Nov 8 DID NOT ACHIEVE ORBIT 39.1 Measurement of magnetic fields around Earth or Moon. Third stage 129 (U) failed to ignite. Its brief data provided evidence that equatorial region about Earth has higher flux and higher energy radiation than previously considered. Pioneer III (U) Juno II (U) Dec 6 DOWN DEC 7, 1958 5.9 Measurement of radiation in space. Error in burnout velocity and angle; did not reach Moon. During its flight, discovered second radiation belt around Earth. 1959 1959 Vanguard II (U) Vanguard Feb 17 122.8 3054 557 32.9 9.4 Sphere (20 inches in diameter) to measure cloud cover. First Earth Alpha 1 (SLV-4) (U) photo from satellite. Interpretation of data difficult because satellite developed precessing motion. -
Silk Truelog Explorer 19.0
Silk TrueLog Explorer 19.0 Help Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright © Micro Focus 1992-2018. All rights reserved. MICRO FOCUS, the Micro Focus logo and Silk Performer are trademarks or registered trademarks of Micro Focus IP Development Limited or its subsidiaries or affiliated companies in the United States, United Kingdom and other countries. All other marks are the property of their respective owners. 2018-06-06 ii Contents TrueLog Explorer 19.0 .......................................................................................5 Getting Started ....................................................................................................................5 TrueLog Explorer Overview ...................................................................................... 5 What You Can Do with TrueLog Explorer ................................................................ 5 Tour of the UI ............................................................................................................6 Best Practice Use of TrueLog Explorer ................................................................. 10 Understanding TrueLog ..........................................................................................11 Analyzing Tests ...................................................................................................... 14 Working With Silk Performer ................................................................................. 20 TrueLog Explorer -

Contactstore System Administration Guide
IP Office ContactStore System Administration Guide 15-601039 Issue 2 (24 May 2006) © 2006 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and accurate at the time of printing, Avaya Inc. can assume no liability for any errors. Changes and corrections to the information in this document may be incorporated in future releases. Documentation Disclaimer Avaya Inc. is not responsible for any modifications, additions, or deletions to the original published version of this documentation unless such modifications, additions, or deletions were performed by Avaya. Link Disclaimer Avaya Inc. is not responsible for the contents or reliability of any linked Web sites referenced elsewhere within this Documentation, and Avaya does not necessarily endorse the products, services, or information described or offered within them. We cannot guarantee that these links will work all of the time and we have no control over the availability of the linked pages. License USE OR INSTALLATION OF THE PRODUCT INDICATES THE END USER’S ACCEPTANCE OF THE TERMS SET FORTH HEREIN AND THE GENERAL LICENSE TERMS AVAILABLE ON THE AVAYA WEBSITE AT http://support.avaya.com/LicenseInfo/ (“GENERAL LICENSE TERMS”). IF YOU DO NOT WISH TO BE BOUND BY THESE TERMS, YOU MUST RETURN THE PRODUCT(S) TO THE POINT OF PURCHASE WITHIN TEN (10) DAYS OF DELIVERY FOR A REFUND OR CREDIT. Avaya grants End User a license within the scope of the license types described below. The applicable number of licenses and units of capacity for which the license is granted will be one (1), unless a different number of licenses or units of capacity is specified in the Documentation or other materials available to End User.