Machine Learning for Reliable Communication and Improved Tracking of Dynamical Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tm Synchronization and Channel Coding—Summary of Concept and Rationale
Report Concerning Space Data System Standards TM SYNCHRONIZATION AND CHANNEL CODING— SUMMARY OF CONCEPT AND RATIONALE INFORMATIONAL REPORT CCSDS 130.1-G-3 GREEN BOOK June 2020 Report Concerning Space Data System Standards TM SYNCHRONIZATION AND CHANNEL CODING— SUMMARY OF CONCEPT AND RATIONALE INFORMATIONAL REPORT CCSDS 130.1-G-3 GREEN BOOK June 2020 TM SYNCHRONIZATION AND CHANNEL CODING—SUMMARY OF CONCEPT AND RATIONALE AUTHORITY Issue: Informational Report, Issue 3 Date: June 2020 Location: Washington, DC, USA This document has been approved for publication by the Management Council of the Consultative Committee for Space Data Systems (CCSDS) and reflects the consensus of technical panel experts from CCSDS Member Agencies. The procedure for review and authorization of CCSDS Reports is detailed in Organization and Processes for the Consultative Committee for Space Data Systems (CCSDS A02.1-Y-4). This document is published and maintained by: CCSDS Secretariat National Aeronautics and Space Administration Washington, DC, USA Email: [email protected] CCSDS 130.1-G-3 Page i June 2020 TM SYNCHRONIZATION AND CHANNEL CODING—SUMMARY OF CONCEPT AND RATIONALE FOREWORD This document is a CCSDS Report that contains background and explanatory material to support the CCSDS Recommended Standard, TM Synchronization and Channel Coding (reference [3]). Through the process of normal evolution, it is expected that expansion, deletion, or modification of this document may occur. This Report is therefore subject to CCSDS document management and change control procedures, which are defined in Organization and Processes for the Consultative Committee for Space Data Systems (CCSDS A02.1-Y-4). Current versions of CCSDS documents are maintained at the CCSDS Web site: http://www.ccsds.org/ Questions relating to the contents or status of this document should be sent to the CCSDS Secretariat at the email address indicated on page i. -
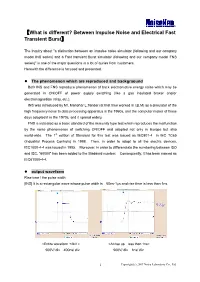
What Is Different? Between Impulse Noise and Electrical Fast Transient Burst】
【What is different? Between Impulse Noise and Electrical Fast Transient Burst】 The Inquiry about "a distinction between an impulse noise simulator (following and our company model INS series) and a Fast transient Burst simulator (following and our company model FNS series)" is one of the major questions in a lot of quries from customers. Herewith the difference is focused and presented. The phenomenon which are reproduced and backgraound Both INS and FNS reproduce phenomenon of back electromotive energy noise which may be generated in ON/OFF of power supply switching (like a gas insulated braker and/or electromagnetism relay, etc.). INS was introduced by Mr. Manohar L.Tandor (at that time worked in I.B.M) as a simulator of the high frequency noise to data processing apparatus in the 1960s, and the computer maker of those days adopted it in the 1970s, and it spread widely. FNS is indicated as a basic standard of the immunity type test which reproduces the malfunction by the noise phenomenon of switching ON/OFF and adopted not only in Europe but also world-wide. The 1st edition of Standard for this test was issued as IEC801-4 in IEC TC65 (Industrial Process Controls) in 1988. Then, in order to adopt to all the electric devices, IEC1000-4-4 was issued in 1995. Moreover, in order to differenciate the numbering between ISO and IEC, “60000” has been added to the Stadanrd number. Consequently, it has been named as IEC61000-4-4. output waveform Rise time / the pulse width [INS] It is a rectangular wave whose pulse width is 50ns-1μs and rise time is less than 1ns. -

Improved 1/F Noise Measurements for Microwave Transistors Clemente Toro Jr
University of South Florida Scholar Commons Graduate Theses and Dissertations Graduate School 6-25-2004 Improved 1/f Noise Measurements for Microwave Transistors Clemente Toro Jr. University of South Florida Follow this and additional works at: https://scholarcommons.usf.edu/etd Part of the American Studies Commons Scholar Commons Citation Toro, Clemente Jr., "Improved 1/f Noise Measurements for Microwave Transistors" (2004). Graduate Theses and Dissertations. https://scholarcommons.usf.edu/etd/1271 This Thesis is brought to you for free and open access by the Graduate School at Scholar Commons. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Scholar Commons. For more information, please contact [email protected]. Improved 1/f Noise Measurements for Microwave Transistors by Clemente Toro, Jr. A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering Department of Electrical Engineering College of Engineering University of South Florida Major Professor: Lawrence P. Dunleavy, Ph.D. Thomas Weller, Ph.D. Horace Gordon, Jr., M.S.E., P.E. Date of Approval: June 25, 2004 Keywords: low, frequency, flicker, model, correlation © Copyright 2004, Clemente Toro, Jr. DEDICATION This thesis is dedicated to my father, Clemente, and my mother, Miriam. Thank you for helping me and supporting me throughout my college career! ACKNOWLEDGMENT I would like to acknowledge Dr. Lawrence P. Dunleavy for proving the opportunity to perform 1/f noise research under his supervision. For providing software solutions for the purposes of data gathering, I give credit to Alberto Rodriguez. In addition, his experience in the area of noise and measurements was useful to me as he generously brought me up to speed with understanding the fundamentals of noise and proper data representation. -

Enhanced-SNR Impulse Radio Transceiver Based on Phasers Babak Nikfal,Studentmember,IEEE, Qingfeng Zhang, Member, IEEE,Andchristophe Caloz, Fellow, IEEE
778 IEEE MICROWAVE AND WIRELESS COMPONENTS LETTERS, VOL. 24, NO. 11, NOVEMBER 2014 Enhanced-SNR Impulse Radio Transceiver Based on Phasers Babak Nikfal,StudentMember,IEEE, Qingfeng Zhang, Member, IEEE,andChristophe Caloz, Fellow, IEEE Abstract—The concept of signal-to-noise ratio (SNR) enhance- transmitter. The message data, which are reduced in the figure ment in impulse radio transceivers based on phasers of opposite to a single baseband rectangular pulse representing a bit of in- chirping slopes is introduced. It is shown that SNR enhancements formation, is injected into the pulse shaper to be transformed by factors and are achieved for burst noise and Gaussian into a smooth Gaussian-type pulse, , of duration .This noise, respectively, where is the stretching factor of the phasers. An experimental demonstration is presented, using stripline cas- pulse is mixed with an LO signal of frequency , which yields caded C-section phasers, where SNR enhancements in agreement the modulated pulse , of peak power . with theory are obtained. The proposed radio analog signal pro- This modulated pulse is injected into a linear up-chirp phaser, cessing transceiver system is simple, low-cost and frequency scal- and subsequently transforms into an up-chirped pulse, . able, and may therefore be suitable for broadband impulse radio Assuming energy conservation (lossless system), the duration ranging and communication applications. of this pulse has increased to while its peak power has de- Index Terms—Dispersion engineering, impulse radio, phaser, creased to ,where is the stretching factor of the phaser, radio analog signal processing, signal-to-noise ratio. given by ,where and are the duration of the input and output pulses, respectively, is the slope of the group delay response of the phaser (in I. -

AN-1496 Noise, TDMA Noise, and Suppression Techniques (Rev. D)
Application Report SNAA033D–May 2006–Revised May 2013 AN-1496 Noise, TDMA Noise, and Suppression Techniques ..................................................................................................................................................... ABSTRACT The term “noise” is often and loosely used to describe unwanted electrical signals that distort the purity of the desired signal. Some forms of noise are unavoidable (e.g., real fluctuations in the quantity being measured), and they can be overcome only with the techniques of signal averaging and bandwidth narrowing. Other forms of noise (for example, radio frequency interference and “ground loops”) can be reduced or eliminated by a variety of techniques, including filtering and careful attention to wiring configuration and parts location. Finally, there is noise that arises in signal amplification and it can be reduced through the techniques of low-noise amplifier design. Although noise reduction techniques can be effective, it is prudent to begin with a system that is free of preventable interference and that possesses the lowest amplifier noise possible1. This application note will specifically address the problem of TDMA Noise customers have encountered while driving mono speakers in their GSM phone designs. Contents 1 Noise and TDMA Noise .................................................................................................... 2 2 Conclusion ................................................................................................................... 6 -

22Nd International Congress on Acoustics ICA 2016
Page intentionaly left blank 22nd International Congress on Acoustics ICA 2016 PROCEEDINGS Editors: Federico Miyara Ernesto Accolti Vivian Pasch Nilda Vechiatti X Congreso Iberoamericano de Acústica XIV Congreso Argentino de Acústica XXVI Encontro da Sociedade Brasileira de Acústica 22nd International Congress on Acoustics ICA 2016 : Proceedings / Federico Miyara ... [et al.] ; compilado por Federico Miyara ; Ernesto Accolti. - 1a ed . - Gonnet : Asociación de Acústicos Argentinos, 2016. Libro digital, PDF Archivo Digital: descarga y online ISBN 978-987-24713-6-1 1. Acústica. 2. Acústica Arquitectónica. 3. Electroacústica. I. Miyara, Federico II. Miyara, Federico, comp. III. Accolti, Ernesto, comp. CDD 690.22 ISBN 978-987-24713-6-1 © Asociación de Acústicos Argentinos Hecho el depósito que marca la ley 11.723 Disclaimer: The material, information, results, opinions, and/or views in this publication, as well as the claim for authorship and originality, are the sole responsibility of the respective author(s) of each paper, not the International Commission for Acoustics, the Federación Iberoamaricana de Acústica, the Asociación de Acústicos Argentinos or any of their employees, members, authorities, or editors. Except for the cases in which it is expressly stated, the papers have not been subject to peer review. The editors have attempted to accomplish a uniform presentation for all papers and the authors have been given the opportunity to correct detected formatting non-compliances Hecho en Argentina Made in Argentina Asociación de Acústicos Argentinos, AdAA Camino Centenario y 5006, Gonnet, Buenos Aires, Argentina http://www.adaa.org.ar Proceedings of the 22th International Congress on Acoustics ICA 2016 5-9 September 2016 Catholic University of Argentina, Buenos Aires, Argentina ICA 2016 has been organised by the Ibero-american Federation of Acoustics (FIA) and the Argentinian Acousticians Association (AdAA) on behalf of the International Commission for Acoustics. -

Understanding Noise Figure
Understanding Noise Figure Iulian Rosu, YO3DAC / VA3IUL, http://www.qsl.net/va3iul One of the most frequently discussed forms of noise is known as Thermal Noise. Thermal noise is a random fluctuation in voltage caused by the random motion of charge carriers in any conducting medium at a temperature above absolute zero (K=273 + °Celsius). This cannot exist at absolute zero because charge carriers cannot move at absolute zero. As the name implies, the amount of the thermal noise is to imagine a simple resistor at a temperature above absolute zero. If we use a very sensitive oscilloscope probe across the resistor, we can see a very small AC noise being generated by the resistor. • The RMS voltage is proportional to the temperature of the resistor and how resistive it is. Larger resistances and higher temperatures generate more noise. The formula to find the RMS thermal noise voltage Vn of a resistor in a specified bandwidth is given by Nyquist equation: Vn = 4kTRB where: k = Boltzmann constant (1.38 x 10-23 Joules/Kelvin) T = Temperature in Kelvin (K= 273+°Celsius) (Kelvin is not referred to or typeset as a degree) R = Resistance in Ohms B = Bandwidth in Hz in which the noise is observed (RMS voltage measured across the resistor is also function of the bandwidth in which the measurement is made). As an example, a 100 kΩ resistor in 1MHz bandwidth will add noise to the circuit as follows: -23 3 6 ½ Vn = (4*1.38*10 *300*100*10 *1*10 ) = 40.7 μV RMS • Low impedances are desirable in low noise circuits. -
2008 Registration Document
2008 REGISTRATION DOCUMENT CONTENTS RENAULT AND THE GROUP 3 RENAULT AND ITS SHAREHOLDERS 165 0 1 1.1 Presentation of Renault and the Group 4 05 5.1 General information 166 1.2 Risk factors 24 5.2 General information about Renault’s share 1.3 The Renault-Nissan Alliance 26 capital 168 5.3 Market for Renault shares 172 5.4 Investor relations policy 176 MANAGEMENT REPORT 43 02 2.1 Earnings report 44 2.2 Research and Development 63 MIXED GENERAL MEETING OF 2.3 Risk management 69 06 MAY 6, 2009 PRESENTATION OF THE RESOLUTIONS 179 The Board first of all proposes the adoption of SUSTAINABLE DEVELOPMENT 83 eleven resolutions by the Ordinary General Meeting 180 Next, nine resolutions are within the powers of 3.1 Employee-relations performance 84 03 the Extraordinary General Meeting 182 3.2 Environmental performance 101 3.3 Social performance 116 3.4 Renault, a responsible company 127 FINANCIAL STATEMENTS 187 3.5 Table of objectives 129 07 7.1 Statutory auditors’ report on the consolidated financial statements 188 7.2 Consolidated f inancial s tatements 190 CORPORATE GOVERNANCE 135 7.3 Statutory Auditors’ reports on the parent 04 4.1 The Board of Directors 136 company only 252 4.2 Management bodies at March 1, 2009 146 7.4 Renault SA parent company 4.3 Audits 149 financial statements 255 4.4 Interests of senior executives 150 4.5 Report of the Chairman of the Board, pursuant to Article L. 225-37 of French ADDITIONAL INFORMATION 273 Company Law (Code de commerce) 156 08 8.1 Person responsible 4.6 Statutory auditors’ report on the report of for the Registration document 274 the Chairman 163 8.2 Information concerning FY 2007 and 2006 275 8.3 Internal regulations of the Board of Directors 276 8.4 Appendices relating to the environment 282 8.5 Cross reference tables 288 REGISTRATION DOCUMENT REGISTRATION 2008 INCLUDING THE MANAGEMENT REPORT APPROVED BY THE BOARD OF DIRECTORS ON FEBRUARY 11, 2009 This Registration document is on line on the Web-site www.renault.com (French and English versions) and on the AMF Web-site www.amf-france.org (F rench version only). -

PROCEEDINGS of the ICA CONGRESS (Onl the ICA PROCEEDINGS OF
ine) - ISSN 2415-1599 ISSN ine) - PROCEEDINGS OF THE ICA CONGRESS (onl THE ICA PROCEEDINGS OF Page intentionaly left blank 22nd International Congress on Acoustics ICA 2016 PROCEEDINGS Editors: Federico Miyara Ernesto Accolti Vivian Pasch Nilda Vechiatti X Congreso Iberoamericano de Acústica XIV Congreso Argentino de Acústica XXVI Encontro da Sociedade Brasileira de Acústica 22nd International Congress on Acoustics ICA 2016 : Proceedings / Federico Miyara ... [et al.] ; compilado por Federico Miyara ; Ernesto Accolti. - 1a ed . - Gonnet : Asociación de Acústicos Argentinos, 2016. Libro digital, PDF Archivo Digital: descarga y online ISBN 978-987-24713-6-1 1. Acústica. 2. Acústica Arquitectónica. 3. Electroacústica. I. Miyara, Federico II. Miyara, Federico, comp. III. Accolti, Ernesto, comp. CDD 690.22 ISSN 2415-1599 ISBN 978-987-24713-6-1 © Asociación de Acústicos Argentinos Hecho el depósito que marca la ley 11.723 Disclaimer: The material, information, results, opinions, and/or views in this publication, as well as the claim for authorship and originality, are the sole responsibility of the respective author(s) of each paper, not the International Commission for Acoustics, the Federación Iberoamaricana de Acústica, the Asociación de Acústicos Argentinos or any of their employees, members, authorities, or editors. Except for the cases in which it is expressly stated, the papers have not been subject to peer review. The editors have attempted to accomplish a uniform presentation for all papers and the authors have been given the opportunity -

Performance of Image Similarity Measures Under Burst Noise with Incomplete Reference
International Journal of Applied Engineering Research ISSN 0973-4562 Volume 12, Number 23 (2017) pp. 13524-13533 © Research India Publications. http://www.ripublication.com Performance of Image Similarity Measures under Burst Noise with Incomplete Reference Nisreen R. Hamza1, Hind R. M. Shaaban1, Zahir M. Hussain1,* and Katrina L. Neville2 1 Faculty of Computer Science & Mathematics, University of Kufa, Najaf, Iraq. 2 School of Engineering, RMIT, Melbourne, Australia. E-mail: [email protected] * Corresponding Author, Orcid: 0000-0002-1707-5485 Abstract by Wang and Bovik [3, 7] and the Feature Similarity Index (FSIM) which was proposed in [8]. In information theory A comprehensive study on the performance of image similarity approaches the similarity can be defined as the variance techniques for face recognition is presented in this work. between information-theoretic characteristics in the two images Adverse conditions on the reference image are considered in [9]. The Sjhcorr2 method is a hybrid measure based on both this work for the practical importance of face recognition under information-theory based features as well as statistical features non-ideal conditions of noise and / or incomplete image used for assessing the similarity among images [10]. information. |This study presents results from experiments on the effect of burst noise has on images and their structural Several factors affect the security and accuracy of data similarity when transmitted through communication channels. transmitted through communications systems over physical Also addressed in this work is the effect incomplete images channels, one major issue which will be specifically examine have on structural similarity including the effect of intensive in this work is burst noise which affects the reliability and rate burst noise on the missing parts of the image. -

Notes on Noise Reduction
PHYS 331: Junior Physics Laboratory I Notes on Noise Reduction When setting out to make a measurement one often finds that the signal, the quantity we want to see, is masked by noise, which is anything that interferes with seeing the signal. Maximizing the signal and minimizing the effects of noise then become the goals of the experimenter. To reach these goals we must understand the nature of the signal, the possible sources of noise and the possible strategies for extracting the desired quantity from a noisy environment.. Figure 1 shows a very generalized experimental situation. The system could be electrical, mechanical or biological, and includes all important environmental variables such as temperature, pressure or magnetic field. The excitation is what evokes the response we wish to measure. It might be an applied voltage, a light beam or a mechanical vibration, depending on the situation. The system response to the excitation, along with some noise, is converted to a measurable form by a transducer, which may add further noise. The transducer could be something as simple as a mechanical pointer to register deflection, but in modern practice it almost always converts the system response to an electrical signal for recording and analysis. In some experiments it is essential to recover the full time variation of the response, for example the time-dependent fluorescence due to excitation of a chemical reaction with a short laser pulse. It is then necessary to record the transducer output as a function of time, perhaps repetitively, and process the output to extract the signal of interest while minimizing noise contributions. -

Communication Channel Models
Communication channel model Goal The goal of this experiment is to become familiar with the definition of channel model and the effect of the channel model on the transmitted signal both in the time and the frequency domain. Theory Communicating data from one location to another requires some form of pathway or medium. These pathways, called communication channels, use two types of media: cable (twisted-pair wire, cable, and fiber-optic cable) and broadcast (microwave, satellite, radio, and infrared). Cable or wire line media use physical wires of cables to transmit data and information. Twisted-pair wire and coaxial cables are made of copper, and fiber-optic cable is made of glass. The simplified block diagram of any communication system can be presented by Figure 1: Transmitter Channel Receiver Noise Figure 1. Block diagram of communication systems As it is seen in Figure 1, in order to model the whole transmission environment, the transmitted signal first passes through the channel and then, noise is added to the signal. In communication systems, noise is an error or undesired random disturbance of a useful information signal in a communication channel. The noise is a summation of unwanted or disturbing energy from natural and sometimes man-made sources. Noise is, however, typically distinguished from interference, for example in the signal-to-noise ratio (SNR), signal-to-interference ratio (SIR) and signal-to- noise plus interference ratio (SNIR) measures. Noise is also typically distinguished from distortion, which is an unwanted systematic alteration of the signal waveform by the communication equipment, for example in the signal-to-noise and distortion ratio (SINAD).