Secure View V3.16.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Yibo Wu Final.Pdf
The Pennsylvania State University The Graduate School RESOURCE-AWARE CROWDSOURCING IN WIRELESS NETWORKS A Dissertation in Computer Science and Engineering by Yibo Wu c 2018 Yibo Wu Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy May 2018 The dissertation of Yibo Wu was reviewed and approved∗ by the following: Guohong Cao Professor of Computer Science and Engineering Dissertation Adviser, Chair of Committee Robert Collins Associate Professor of Computer Science and Engineering Sencun Zhu Associate Professor of Computer Science and Engineering Associate Professor of Information Sciences and Technology Zhenhui Li Associate Professor of Information Sciences and Technology Bhuvan Urgaonkar Associate Professor of Computer Science and Engineering Graduate Program Chair of Computer Science and Engineering ∗Signatures are on file in the Graduate School. Abstract The ubiquity of mobile devices has opened up opportunities for a wide range of applications based on photo/video crowdsourcing, where the server collects a large number of photos/videos from the public to obtain desired information. How- ever, transmitting large numbers of photos/videos in a wireless environment with bandwidth constraints is challenging, and it is hard to run computation-intensive image processing techniques on mobile devices with limited energy and computa- tion power to identify the useful photos/videos and remove redundancy. To address these challenges, we propose a framework to quantify the quality of crowdsourced photos/videos based on the accessible geographical and geometrical information (called metadata) including the orientation, position, and all other related param- eters of the built-in camera. From metadata, we can infer where and how the photo/video is taken, and then only transmit the most useful photos/videos. -

A Survey of Enabling Technologies in Successful Consumer Digital Imaging Products
R06 R06 A Survey of Enabling Technologies in Successful Consumer Digital Imaging Products R. Fontaine, TechInsights1 The early trend for both types of masked PDAF pixels was Abstract—The image quality and customized functionality of to deploy them within a relatively small central region of the small-pixel mobile camera systems continues to bring true active pixel array, or as linear arrays (periodic rows of product differentiation to smartphones. Recently, phase PDAF pixel pairs). Today, masked pixel PDAF arrays in detection autofocus (PDAF) pixels, pixel isolation structures, marquee products occupy more than 90% of the host active chip stacking and other technology elements have contributed to a remarkable increase in mobile camera performance. pixel arrays and display a trend of increasing density Other imaging applications continue to benefit from small- generation-over-generation. pixel development efforts as foundries and IDMs transfer leading edge technology to active pixel arrays for emerging A. Masked PDAF in Front-Illuminated CCDs imaging and sensing applications. Hybrid PDAF systems were introduced to the camera market by a FujiFilm press release in July 2010. The Index Terms—CMOS image sensor, through silicon via, FinePix Z800EXR featured a hybrid AF system with a Cu-Cu hybrid bonding, direct bonding interconnect, stated AF performance of 0.158 s [1]. This front-illuminated homogeneous wafer-to-wafer bonding (oxide bonding), stacked chip, phase detection autofocus, image signal processor charge-coupled device (CCD) imager, fabricated by Toshiba, employed metal half-masks in two of 32 pixels I. INTRODUCTION within a rectangular PDAF subarray occupying the central ~7% of the active pixel array [2]. -

SECOND AMENDED COMPLAINT 3:14-Cv-582-JD
Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 1 of 19 1 EDUARDO G. ROY (Bar No. 146316) DANIEL C. QUINTERO (Bar No. 196492) 2 JOHN R. HURLEY (Bar No. 203641) PROMETHEUS PARTNERS L.L.P. 3 220 Montgomery Street Suite 1094 San Francisco, CA 94104 4 Telephone: 415.527.0255 5 Attorneys for Plaintiff 6 DANIEL NORCIA 7 UNITED STATES DISTIRCT COURT 8 NORTHERN DISTRICT OF CALIFORNIA 9 DANIEL NORCIA, on his own behalf and on Case No.: 3:14-cv-582-JD 10 behalf of all others similarly situated, SECOND AMENDED CLASS ACTION 11 Plaintiffs, COMPLAINT FOR: 12 v. 1. VIOLATION OF CALIFORNIA CONSUMERS LEGAL REMEDIES 13 SAMSUNG TELECOMMUNICATIONS ACT, CIVIL CODE §1750, et seq. AMERICA, LLC, a New York Corporation, and 2. UNLAWFUL AND UNFAIR 14 SAMSUNG ELECTRONICS AMERICA, INC., BUSINESS PRACTICES, a New Jersey Corporation, CALIFORNIA BUS. & PROF. CODE 15 §17200, et seq. Defendants. 3. FALSE ADVERTISING, 16 CALIFORNIA BUS. & PROF. CODE §17500, et seq. 17 4. FRAUD 18 JURY TRIAL DEMANDED 19 20 21 22 23 24 25 26 27 28 1 SECOND AMENDED COMPLAINT 3:14-cv-582-JD Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 2 of 19 1 Plaintiff DANIEL NORCIA, having not previously amended as a matter of course pursuant to 2 Fed.R.Civ.P. 15(a)(1)(B), hereby exercises that right by amending within 21 days of service of 3 Defendants’ Motion to Dismiss filed October 20, 2014 (ECF 45). 4 Individually and on behalf of all others similarly situated, Daniel Norcia complains and alleges, 5 by and through his attorneys, upon personal knowledge and information and belief, as follows: 6 NATURE OF THE ACTION 7 1. -
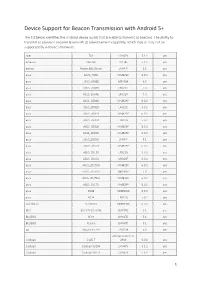
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Network and Device Forensic Analysis of Android Social-Messaging Applications
DIGITAL FORENSIC RESEARCH CONFERENCE Network And Device Forensic Analysis Of Android Social-Messaging Applications By Daniel Walnycky, Ibrahim Baggili, Andrew Marrington, Frank Breitinger and Jason Moore Presented At The Digital Forensic Research Conference DFRWS 2015 USA Philadelphia, PA (Aug 9th - 13th) DFRWS is dedicated to the sharing of knowledge and ideas about digital forensics research. Ever since it organized the first open workshop devoted to digital forensics in 2001, DFRWS continues to bring academics and practitioners together in an informal environment. As a non-profit, volunteer organization, DFRWS sponsors technical working groups, annual conferences and challenges to help drive the direction of research and development. http:/dfrws.org Network'and'device'forensic'analysis'of'' Android'socialOmessaging'applica=ons' Daniel'Walnycky,'Ibrahim'Baggili,'Andrew'Marrington,' Jason'Moore,'Frank'Brei=nger' Graduate'Research'Assistant,'UNHcFREG'Member' Presen=ng'@'DFRWS,'Philadelphia,'PA,'2015' Agenda' • Introduc=on' • Related'work' • Methodology' • Experimental'results' • Discussion'and'conclusion' • Future'work' • Datapp' 2' Introduc=on' Tested'20'Android'messaging'apps'for'“low'hanging'fruit”'a.k.a'unencrypted'data:' • on'the'device,'in'network'traffic,'and'on'server'storage' Found'eviden=ary'traces:'passwords,'screen'shots,'text,'images,'videos,'audio,'GPS' loca=on,'sketches,'profile'pictures,'and'more…' 3' Related'work' • Forensic'value'of'smartphone'messages:' • Smartphones'may'contain'the'same'rich'variety'of'digital'evidence'which'might'be'found'on'a'computer' -

Terraillon Wellness Coach Supported Devices
Terraillon Wellness Coach Supported Devices Warning This document lists the smartphones compatible with the download of the Wellness Coach app from the App Store (Apple) and Play Store (Android). Some models have been tested by Terraillon to check the compatibility and smooth operation of the Wellness Coach app. However, many models have not been tested. Therefore, Terraillon doesn't ensure the proper functioning of the Wellness Coach application on these models. If your smartphone model does not appear in the list, thank you to send an email to [email protected] giving us the model of your smartphone so that we can activate if the application store allows it. BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED ACER Liquid Z530 acer_T02 Android 4.3+ ACER Liquid Jade S acer_S56 Android 4.3+ ACER Liquid E700 acer_e39 Android 4.3+ ACER Liquid Z630 acer_t03 Android 4.3+ ACER Liquid Z320 T012 Android 4.3+ ARCHOS 45 Helium 4G a45he Android 4.3+ ARCHOS 50 Helium 4G a50he Android 4.3+ ARCHOS Archos 45b Helium ac45bhe Android 4.3+ ARCHOS ARCHOS 50c Helium ac50che Android 4.3+ APPLE iPhone 4S iOS8+ APPLE iPhone 5 iOS8+ APPLE iPhone 5C iOS8+ APPLE iPhone 5S iOS8+ APPLE iPhone 6 iOS8+ APPLE iPhone 6 Plus iOS8+ APPLE iPhone 6S iOS8+ APPLE iPhone 6S Plus iOS8+ APPLE iPad Mini 1 iOS8+ APPLE iPad Mini 2 iOS8+ 1 / 48 www.terraillon.com Terraillon Wellness Coach Supported Devices BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED APPLE iPad Mini 3 iOS8+ APPLE iPad Mini 4 iOS8+ APPLE iPad 3 iOS8+ APPLE iPad 4 iOS8+ APPLE iPad Air iOS8+ -

BPOD-I2498 HTC One M7 Lollipop SU-V8.Indd
Android 5.0 operating system update for your HTC ONE®. Software Version: SU6A - Build Number: 5.28.605.12; Baseband: 1.13.41.1209 SU6B - Build Number: 6.21.605.3; Baseband: 1.13.41.1209 Verizon Wireless is pleased to announce an operating system update to Android 5.0 Lollipop. This version brings Android beyond smartphones and tablets, allowing access to apps and Android services on other connected screens like TV’s, cars and wearables. The new material design offers complex animations and 3-D views, 64-bit ABI support and improved runtime. NOTIFICATION PANEL • Lollipop Notification Panel behavior has been adopted • Swipe down once for Notifications • Swipe down a second time for Quick Settings • Toggle Button from KitKat has been replaced by Settings LOCK SCREEN • Lollipop Notification style has been adopted The following Sense settings have been removed • Security > Enable lock screen widgets • Security > Notification Settings • Security > Bypass lock screen on wake HTC One® | For step-by-step instructions on how to perform the download, please visit www.verizonwireless.com/htconeupdate | Data Usage Applies. © 2015 Verizon Wireless. 0315-I2498 1 2 3 HTC ONE LOLLIPOP SETTINGS • “Sound” has been changed to “Sound & notification” in Settings • Notification light settings have been moved to “Sound & notification” • Calendar Picker View offers dropdown capabilities • Search function has been added to settings • Date & Time settings have been reordered • Syncing with new Google Settings and adding in Accessibility • Switch Access • Color Inversion • Color Correction • High Contrast Text • “Sidetone” will be added as a Call Setting, which provides audible feedback to the caller CLOCK • World Clock Globe has been removed for memory considerations | For step-by-step instructions on how to perform the download, please visit www.verizonwireless.com/htconeupdate | Data Usage Applies. -
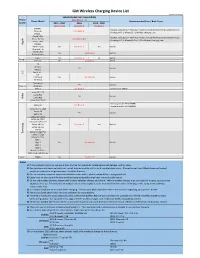
GM Wireless Charging Device List
GM Wireless Charging Device List Revision: Aug 30, 2019 Vehicle Model Year Compatibility Phone ( See Notes 1 - 7) Phone Model Recommended Case / Back Cover Brand 2015 - 2017 2018 2019 - 2020 (See Note 8) (See Note 8) (See Note 9) iPhone 6 ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case iPhone 6s See Note: A ŸAircharge MFi Qi iPhone 6S / 6 Wireless Charging Case iPhone 7 iPhone 6 Plus ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case e iPhone 6s Plus See Note: A & B l ŸAircharge MFi Qi iPhone 6S Plus / 6 Plus Wireless Charging Case p iPhone 7 Plus p A iPhone 8 iPhone X (10) No See Note: C Yes Built-in iPhone Xs / Xr iPhone 8 Plus No See Note: B Built-in iPhone Xs Max Pixel 3 No See Note: C Yes Built-in Google Pixel 3XL No See Note: B Built-in G6 Nexus 4 Yes Built-in Nexus 5 G Spectrum 2 L V30 V40 ThinQ No See Note: B Built-in G7 ThinQ Droid Maxx Yes Built-in Motorola Droid Mini Moto X See Note: A Incipio model: MT231 Lumia 830 / 930 a i Lumia 920 k Yes Built-in o Lumia 928 N Lumia 950 / 950 XL ŸSamsung model: EP-VG900BBU Galaxy S5 See Note: A ŸSamsung model: EP-CG900IBA Galaxy S6 / S6 Edge Galaxy S8 Yes Built-in Galaxy S9 Galaxy S10 / S10e Galaxy S6 Active Galaxy S7 / S7 Active g Galaxy S8 Plus No See Note: C Yes Built-in n u Galaxy S9 Plus s m S10 5G a Galaxy S6 Edge Plus S Galaxy S7 Edge Galaxy S10 Plus Note 5 Note 7 No See Note: B Built-in Note 8 Note 9 Note 10 / 10 Plus Note 10 5G / 10 Plus 5G Xiami MIX2S No See Note: B Built-in Notes: 1) If phone does not charge: remove it from charger for 3 seconds, rotate phone 180 degrees, and try again. -

Brand Old Device
# New Device Old Device - Brand Old Device - Model Name 1 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE500KL 2 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE601KL 3 Galaxy A6+ Asus Asus ZenFone 2 ZE550ML 4 Galaxy A6+ Asus Asus Zenfone 2 ZE551ML 5 Galaxy A6+ Asus Asus Zenfone 3 Laser 6 Galaxy A6+ Asus Asus Zenfone 3 Max ZC520TL 7 Galaxy A6+ Asus Asus Zenfone 3 Max ZC553KL 8 Galaxy A6+ Asus Asus Zenfone 3 ZE520KL 9 Galaxy A6+ Asus Asus Zenfone 3 ZE552KL 10 Galaxy A6+ Asus Asus Zenfone 3s Max 11 Galaxy A6+ Asus Asus Zenfone Max 12 Galaxy A6+ Asus Asus Zenfone Selfie 13 Galaxy A6+ Asus Asus ZenFone Zoom ZX550 14 Galaxy A6+ Gionee Gionee A1 15 Galaxy A6+ Gionee Gionee A1 Lite 16 Galaxy A6+ Gionee Gionee A1 Plus 17 Galaxy A6+ Gionee Gionee Elife E8 18 Galaxy A6+ Gionee Gionee Elife S Plus 19 Galaxy A6+ Gionee Gionee Elife S7 20 Galaxy A6+ Gionee Gionee F103 21 Galaxy A6+ Gionee Gionee F103 Pro 22 Galaxy A6+ Gionee Gionee Marathon M4 23 Galaxy A6+ Gionee Gionee Marathon M5 24 Galaxy A6+ Gionee Gionee marathon M5 Lite 25 Galaxy A6+ Gionee Gionee Marathon M5 Plus 26 Galaxy A6+ Gionee Gionee P5L 27 Galaxy A6+ Gionee Gionee P7 Max 28 Galaxy A6+ Gionee Gionee S6 29 Galaxy A6+ Gionee Gionee S6 Pro 30 Galaxy A6+ Gionee Gionee S6s 31 Galaxy A6+ Gionee Gionee X1s 32 Galaxy A6+ Google Google Pixel 33 Galaxy A6+ Google Google Pixel XL LTE 34 Galaxy A6+ Google Nexus 5X 35 Galaxy A6+ Google Nexus 6 36 Galaxy A6+ Google Nexus 6P 37 Galaxy A6+ HTC Htc 10 38 Galaxy A6+ HTC Htc Desire 10 Pro 39 Galaxy A6+ HTC Htc Desire 628 40 Galaxy A6+ HTC HTC Desire 630 41 Galaxy A6+ -
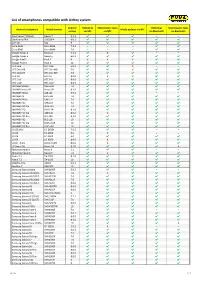
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔ -

Nexus-4 User Manual
NeXus-4 User Manual Version 2.0 0344 Table of contents 1 Service and support 3 1.1 About this manual 3 1.2 Warranty information 3 2 Safety information 4 2.1 Explanation of markings 4 2.2 Limitations of use 5 2.3 Safety measures and warnings 5 2.4 Precautionary measures 7 2.5 Disclosure of residual risk 7 2.6 Information for lay operators 7 3 Product overview 8 3.1 Product components 8 3.2 Intended use 8 3.3 NeXus-4 views 9 3.4 User interface 9 3.5 Patient connections 10 3.6 Device label 10 4 Instructions for use 11 4.1 Software 11 4.2 Powering the NeXus-4 12 4.3 Transfer data to PC 12 4.4 Perform measurement 13 4.5 Mobility 13 5 Operational principles 14 5.1 Bipolar input channels 14 5.2 Auxiliary input channel 14 5.3 Filtering 14 6 Maintenance 15 7 Electromagnetic guidance 16 8 Technical specifications 19 2 1 Service and support 1.1 About this manual This manual is intended for the user of the NeXus-4 system – referred to as ‘product’ throughout this manual. It contains general operating instructions, precautionary measures, maintenance instructions and information for use of the product. Read this manual carefully and familiarize yourself with the various controls and accessories before starting to use the product. This product is exclusively manufactured by Twente Medical Systems International B.V. for Mind Media B.V. Distribution and service is exclusively performed by or through Mind Media B.V. -
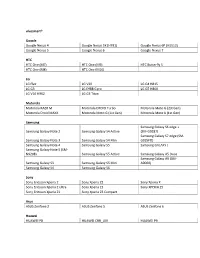
Vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus
vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (M9) HTC Butterfly S HTC One (M8) HTC One (M10) LG LG Flex LG V20 LG G4 H815 LG G3 LG E988 Gpro LG G5 H860 LG V10 H962 LG G3 Titan Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto X (1st Gen) Samsung Samsung Galaxy S6 edge + Samsung Galaxy Note 2 Samsung Galaxy S4 Active (SM-G9287) Samsung Galaxy S7 edge (SM- Samsung Galaxy Note 3 Samsung Galaxy S4 Mini G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Samsung GALAXY J Samsung Galaxy Note 5 (SM- N9208) Samsung Galaxy S5 Active Samsung Galaxy A5 Duos Samsung Galaxy A9 (SM- Samsung Galaxy S3 Samsung Galaxy S5 Mini A9000) Samsung Galaxy S4 Samsung Galaxy S6 Sony Sony Ericsson Xperia Z Sony Xperia Z2 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Sony XPERIA Z5 Sony Ericsson Xperia Z1 Sony Xperia Z3 Compact Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI CRR_L09 HUAWEI P9 Oppo OPPO X9076 OPPO X9009 Xiaomi XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note One Plus OnePlus 3 (A3000) vívosmart® 3 Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Pixel HTC HTC One (M9) HTC One (M10) HTC U11 HTC One (A9) HTC U Ultra LG LG V10 H962 LG G4 H815 LG G6 H870 LG V20 LG G5 H860 Motorola Motorola Moto Z Samsung Samsung Galaxy Note 3 Samsung Galaxy S6 Samsung Galaxy J5 Samsung Galaxy S6 edge + Samsung Galaxy Note 4 (SM-G9287) Samsung Galaxy