The Misuse of Android Unix Domain Sockets and Security Implications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards a Toolchain for Exploiting Smart Contracts on the Ethereum Blockchain
Towards a Toolchain for Exploiting Smart Contracts on the Ethereum Blockchain by Sebastian Kindler M.A., University of Bayreuth, 2011 Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Bachelor of Science in the Computer Science Program Faculty of Computer Science Supervisor: Prof. Dr. Stefan Traub Second Assessor: Prof. Dr. Markus Schäffter External Assessor: Dr. Henning Kopp Ulm University of Applied Sciences March 22, 2019 Abstract The present work introduces the reader to the Ethereum blockchain. First, on a con- ceptual level, explaining general blockchain concepts, and viewing the Ethereum blockchain in particular from different perspectives. Second, on a practical level, the main components that make up the Ethereum blockchain are explained in detail. In preparation for the objective of the present work, which is the analysis of EVM bytecode from an attacker’s perspective, smart contracts are introduced. Both, on the level of EVM bytecode and Solidity source code. In addition, critical assem- bly instructions relevant to the exploitation of smart contracts are explained in detail. Equipped with a definition of what constitutes a vulnerable contract, further practical and theoretical aspects are discussed: The present work introduces re- quirements for a possible smart contract analysis toolchain. The requirements are viewed individually, and theoretical focus is put on automated bytecode analysis and symbolic execution as this is the underlying technique of automated smart contract analysis tools. The importance of semantics is highlighted with respect to designing automated tools for smart contract exploitation. At the end, a min- imal toolchain is presented, which allows beginners to efficiently analyze smart contracts and develop exploits. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

LG G3 User Guide
Available applications and services are subject to change at any time. Table of Contents Get Started 1 Your Phone at a Glance 1 Set Up Your Phone 1 Activate Your Phone 4 Complete the Setup Screens 5 Make Your First Call 6 Set Up Your Voicemail 6 Sprint Account Information and Help 7 Sprint Account Passwords 7 Manage Your Account 7 Sprint Support Services 8 Phone Basics 9 Your Phone's Layout 9 Turn Your Phone On and Off 11 Screen On/Off 11 Lock and Unlock Your Phone 12 Unlock Your Screen Using the Knock Code Feature 13 Guest Mode 14 Set Up Guest Mode 14 Use Guest Mode 15 Hardware Key Control Mode 15 Battery and Charger 15 Extend Your Battery Life 17 Phone Function Keys 17 Recent Apps Key 18 Work with Menus 18 Notifications Panel 19 Home Key 20 Back Key 21 Touchscreen Navigation 21 Your Home Screen 22 Home Screen 22 Extended Home Screen 23 i Use the Applications Key 23 Applications: How to View, Open and Switch 23 Applications 25 Customize Your Home Screen 27 Add and Remove Widgets on the Home Screen 28 Change the Phone's Wallpaper 29 Customize Applications Icons on the Home Screen 30 Access Recently-Used Applications 31 Home Screen Clean View 31 Quick Access 32 Change the Screen Orientation 32 Status Bar 32 Enter Text With the On-screen Keyboard 35 Tips for Editing Text 37 Search Your Phone and the Web 42 Phone and Web Search Using Text Entry 42 Phone and Web Search Using Voice Command 44 Using Clip Tray 44 Text Link 44 Phone Calls 46 HD™ Voice 46 Make Phone Calls 46 Call Using the Phone Dialer 46 Dialing Options 47 Missed Call Notification -

A Practical UNIX Capability System
A Practical UNIX Capability System Adam Langley <[email protected]> 22nd June 2005 ii Abstract This report seeks to document the development of a capability security system based on a Linux kernel and to follow through the implications of such a system. After defining terms, several other capability systems are discussed and found to be excellent, but to have too high a barrier to entry. This motivates the development of the above system. The capability system decomposes traditionally monolithic applications into a number of communicating actors, each of which is a separate process. Actors may only communicate using the capabilities given to them and so the impact of a vulnerability in a given actor can be reasoned about. This design pattern is demonstrated to be advantageous in terms of security, comprehensibility and mod- ularity and with an acceptable performance penality. From this, following through a few of the further avenues which present themselves is the two hours traffic of our stage. Acknowledgments I would like to thank my supervisor, Dr Kelly, for all the time he has put into cajoling and persuading me that the rest of the world might have a trick or two worth learning. Also, I’d like to thank Bryce Wilcox-O’Hearn for introducing me to capabilities many years ago. Contents 1 Introduction 1 2 Terms 3 2.1 POSIX ‘Capabilities’ . 3 2.2 Password Capabilities . 4 3 Motivations 7 3.1 Ambient Authority . 7 3.2 Confused Deputy . 8 3.3 Pervasive Testing . 8 3.4 Clear Auditing of Vulnerabilities . 9 3.5 Easy Configurability . -

Open Yibo Wu Final.Pdf
The Pennsylvania State University The Graduate School RESOURCE-AWARE CROWDSOURCING IN WIRELESS NETWORKS A Dissertation in Computer Science and Engineering by Yibo Wu c 2018 Yibo Wu Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy May 2018 The dissertation of Yibo Wu was reviewed and approved∗ by the following: Guohong Cao Professor of Computer Science and Engineering Dissertation Adviser, Chair of Committee Robert Collins Associate Professor of Computer Science and Engineering Sencun Zhu Associate Professor of Computer Science and Engineering Associate Professor of Information Sciences and Technology Zhenhui Li Associate Professor of Information Sciences and Technology Bhuvan Urgaonkar Associate Professor of Computer Science and Engineering Graduate Program Chair of Computer Science and Engineering ∗Signatures are on file in the Graduate School. Abstract The ubiquity of mobile devices has opened up opportunities for a wide range of applications based on photo/video crowdsourcing, where the server collects a large number of photos/videos from the public to obtain desired information. How- ever, transmitting large numbers of photos/videos in a wireless environment with bandwidth constraints is challenging, and it is hard to run computation-intensive image processing techniques on mobile devices with limited energy and computa- tion power to identify the useful photos/videos and remove redundancy. To address these challenges, we propose a framework to quantify the quality of crowdsourced photos/videos based on the accessible geographical and geometrical information (called metadata) including the orientation, position, and all other related param- eters of the built-in camera. From metadata, we can infer where and how the photo/video is taken, and then only transmit the most useful photos/videos. -

Beej's Guide to Unix IPC
Beej's Guide to Unix IPC Brian “Beej Jorgensen” Hall [email protected] Version 1.1.3 December 1, 2015 Copyright © 2015 Brian “Beej Jorgensen” Hall This guide is written in XML using the vim editor on a Slackware Linux box loaded with GNU tools. The cover “art” and diagrams are produced with Inkscape. The XML is converted into HTML and XSL-FO by custom Python scripts. The XSL-FO output is then munged by Apache FOP to produce PDF documents, using Liberation fonts. The toolchain is composed of 100% Free and Open Source Software. Unless otherwise mutually agreed by the parties in writing, the author offers the work as-is and makes no representations or warranties of any kind concerning the work, express, implied, statutory or otherwise, including, without limitation, warranties of title, merchantibility, fitness for a particular purpose, noninfringement, or the absence of latent or other defects, accuracy, or the presence of absence of errors, whether or not discoverable. Except to the extent required by applicable law, in no event will the author be liable to you on any legal theory for any special, incidental, consequential, punitive or exemplary damages arising out of the use of the work, even if the author has been advised of the possibility of such damages. This document is freely distributable under the terms of the Creative Commons Attribution-Noncommercial-No Derivative Works 3.0 License. See the Copyright and Distribution section for details. Copyright © 2015 Brian “Beej Jorgensen” Hall Contents 1. Intro................................................................................................................................................................1 1.1. Audience 1 1.2. Platform and Compiler 1 1.3. -

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

Improving Mobile-Malware Investigations with Static and Dynamic Code Analysis Techniques
IMPROVING MOBILE-MALWARE INVESTIGATIONS WITH STATIC AND DYNAMIC CODE ANALYSIS TECHNIQUES Vom Fachbereich Informatik (FB 20) der Technischen Universität Darmstadt zur Erlangung des akademischen Grades eines Doktor-Ingenieurs (Dr.-Ing.) genehmigte Dissertation von Siegfried Rasthofer, M.Sc. geboren in Landshut, Deutschland. Referenten: Prof. Dr. Eric Bodden (Referent) Prof. Dr. Andreas Zeller (Korreferent) Prof. Dr. Mira Mezini (Korreferentin) Tag der Einreichung: 7. November 2016 Tag der Disputation: 22. Dezember 2016 Darmstadt 2017 Hochschulkennziffer: D17 Siegfried Rasthofer: Improving Mobile-Malware Investigations with Static and Dynamic Code Analysis Techniques © January 2017 phd referees: Prof. Dr. Eric Bodden Prof. Dr. Andreas Zeller Prof. Dr. Mira Mezini further phd committee members: Prof. Dr. Reiner Hähnle Prof. Dr. Christian Bischof Prof. Dr. Patrick Eugster Darmstadt, Germany January 2017 ABSTRACT Similar to the PC world, the abundance of mobile malware has become a serious threat to smartphone users. Thousands of new apps or app versions are uploaded to popular app stores every day. All of them need to be analyzed against violations of the app store’s content policy. In particular, one wishes to detect whether an application contains malicious behavior. Similarly, antivirus companies check thousands of apps every day to determine whether or not they are malicious. Both app store operators and antivirus vendors face the same problem: it is generally challenging to tell apart malware from benign applications. This is because malware developers aim to hide their applications’ malicious behavior as long as possible from being detected by applying different obfuscation techniques. The raising sophistication with which such measures are implemented pose a serious problem not just to automated malware detection approaches but also to the manual analysis of potential malware by human experts. -
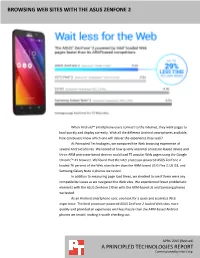
Browsing Web Sites with the Asus Zenfone 2
BROWSING WEB SITES WITH THE ASUS ZENFONE 2 When Android™ smartphone users connect to the Internet, they want pages to load quickly and display correctly. With all the different Android smartphones available, how can buyers know which one will deliver the experience they seek? At Principled Technologies, we compared the Web browsing experience of several Android phones. We looked at how quickly one Intel processor-based device and three ARM processor-based devices could load 75 popular Web pages using the Google Chrome™ 41 browser. We found that the Intel processor-powered ASUS ZenFone 2 loaded 76 percent of the Web sites faster than the ARM-based LG G Flex 2, LG G3, and Samsung Galaxy Note 4 phones we tested. In addition to measuring page load times, we checked to see if there were any compatibility issues as we navigated the Web sites. We experienced fewer problematic elements with the ASUS ZenFone 2 than with the ARM-based LG and Samsung phones we tested. As an Android smartphone user, you look for a quick and seamless Web experience. The Intel processor-powered ASUS ZenFone 2 loaded Web sites more quickly and provided an experience with less hassle than the ARM-based Android phones we tested, making it worth checking out. APRIL 2015 (Revised) A PRINCIPLED TECHNOLOGIES REPORT Commissioned by Intel Corp. A BETTER ANDROID WEB EXPERIENCE WITH ASUS & INTEL Android smartphones are a great way to view Web sites, though they don’t all behave the same way. A mobile device that does a speedy job of loading pages while displaying elements correctly can really improve the user experience. -
![[Linux] - Unix/Linix Commands](https://docslib.b-cdn.net/cover/5564/linux-unix-linix-commands-595564.webp)
[Linux] - Unix/Linix Commands
[Linux] - Unix/Linix Commands 1. $ ssh username@servername command used to login to server 2$ pwd it prints present working directory 3$ ls -l listing the files in present directory 4$ cd..takes you to previous Dir 5$ mkdir <directory>will create directory 6$ mkdir -p /home/user1/d1/d2/d3will create all the non-existing Dir’s 7$ vi <file_name>opens file for reading/editing 8$ cat <file_name>display contents of file 9$ more <file_name>displays page by page contents of file 10$ grep <pattern> file_namechecks pattern/word in file name specified 11$ head <file_name>shows first 10 lines of file_name 12$ touch <file_name>creates a zero/dummy file 13$ ln file1 file2 creates link of file1 to file2 14$ cp <file1> <file2>Copy a file 15$ mv <file1> <file2>Move/rename a file or folder 16$ clearclears the scree 17$ whoDisplays logged in user to the system. 18$ file <file_name>shows what type of file it is like 19$wwill display more info abt the users logged in 20$ ps -efshows process 21$ which <file_name>shows if the file_name/command exists and if exists display the path 22$ rm <file_name>will delete file specified$ rm * Delete all the files in the present directory (BE CAREFUL WHILE GIVING THIS COMMAND) 23$ find . -type f -print -exec grep -i <type_ur_text_here> {} \;this is recursive grep$ find / - name <file_name> -print 24$ tail <file_name>shows last 10 lines of fileuse tail -f for continous update of file_name 25$ chmod 777 <file_name>changes file_name/directory permissions use –R switch for recursive 26$ chown owner:group <file_name>changes -

CICS and IPCS
CICS and IPCS Andre Clark Staff CICS L2 Support Agenda § Dump types § Some basic IPCS commands § CICS Verbexit DFHPDxxx § Common System Area (CSA) § Storage Manager (SM) § Transaction Manager (XM) § Dispatcher (DS) § Kernel (KE) § Loader domain (LD) § Program domain (PG) § Lock Manager (LM) § Enqueue domain (NQ) § Application domain (AP) § Task Summary (TK) § Trace (TR) 3 IPCS Primary Menu ------------------- IPCS PRIMARY OPTION MENU --------------------------------- OPTION ===> ******************** 0 DEFAULTS - Specify default dump and options * USERID - USASSC1 1 BROWSE - Browse dump data set * 2 ANALYSIS - Analyze dump contents * 3 UTILITY - Perform utility functions * TIME - 16:46 4 INVENTORY - Inventory of problem data * PREFIX - USASSC1 5 SUBMIT - Submit problem analysis job to batch * TERMINAL- 3278 6 COMMAND - Enter subcommand, CLIST or REXX exec * PF KEYS - 24 T TUTORIAL - Learn how to use the IPCS dialog ******************** X EXIT - Terminate using log and list defaults Enter END command to terminate IPCS dialog F1=HELP F2=SPLIT F3=END F4=RETURN F5=RFIND F6=MORE F7=UP F8=DOWN F9=SWAP F10=LEFT F11=RIGHT F12=CURSOR 4 IPCS Default Menu ------------------------- IPCS Default Values --------------------------------- Command ===> You may change any of the defaults listed below. The defaults shown before any changes are LOCAL. Change scope to GLOBAL to display global defaults. Scope ==> BOTH (LOCAL, GLOBAL, or BOTH) If you change the Source default, IPCS will display the current default Address Space for the new source and will ignore any data entered in the Address Space field. Source ==> DSNAME('USASSC1.SHAREFC.DUMP') Address Space ==> ASID(X'0044') Message Routing ==> NOPRINT TERMINAL Message Control ==> FLAG(WARNING) NOCONFIRM VERIFY Display Content ==> MACHINE REMARK REQUEST NOSTORAGE SYMBOL Press ENTER to update defaults.