Network and Device Forensic Analysis of Android Social-Messaging Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Is Our Privacy Being Compromised As We Speak? Eavesdropper's Heaven
IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.10, October 2017 119 Is our privacy being compromised as we speak? Eavesdropper’s heaven or a nightmare? A study of Mobile Voice over Internet Protocol (mVoIP) and Instant Messaging (IM) Applications. Farhan Ahmed Muhammad Ahsan Muhammad Saeed Nasir Touheed Siddiqui Najam Department of Computer Department of Computer Department of Computer Department of Computer Science, University of Science, IBA Karachi Science, University of Science, University of Karachi Pakistan Karachi Karachi Karachi, Pakistan Karachi, Pakistan Karachi, Pakistan Abstract around these applications, these two key areas are not at all In the recent times, mobile voice over internet protocol (mVoIP) explored and there are only a handful of studies if at all applications have been greatly adopted by the masses and have which examine aspect of these so called “perfect really captured much of the attention in the application market applications”. Majority of the people who use these place. These applications not only provide voice communication applications aren’t even aware of the fact that anyone can with little to no cost but also offer instant messaging service. basically intercept their communication and if the People across the world use applications like this and some even communicate daily with others just by using these applications communication is not encrypted, can easily read and misuse rather than the conventional way of text messages and GSM calls. their information. Other than this, is the communication With applications consolidating millions and millions of users, encrypted at the servers or is the privacy of the user in the security and privacy is a topic which many prefer not to discuss. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

A Survey of Enabling Technologies in Successful Consumer Digital Imaging Products
R06 R06 A Survey of Enabling Technologies in Successful Consumer Digital Imaging Products R. Fontaine, TechInsights1 The early trend for both types of masked PDAF pixels was Abstract—The image quality and customized functionality of to deploy them within a relatively small central region of the small-pixel mobile camera systems continues to bring true active pixel array, or as linear arrays (periodic rows of product differentiation to smartphones. Recently, phase PDAF pixel pairs). Today, masked pixel PDAF arrays in detection autofocus (PDAF) pixels, pixel isolation structures, marquee products occupy more than 90% of the host active chip stacking and other technology elements have contributed to a remarkable increase in mobile camera performance. pixel arrays and display a trend of increasing density Other imaging applications continue to benefit from small- generation-over-generation. pixel development efforts as foundries and IDMs transfer leading edge technology to active pixel arrays for emerging A. Masked PDAF in Front-Illuminated CCDs imaging and sensing applications. Hybrid PDAF systems were introduced to the camera market by a FujiFilm press release in July 2010. The Index Terms—CMOS image sensor, through silicon via, FinePix Z800EXR featured a hybrid AF system with a Cu-Cu hybrid bonding, direct bonding interconnect, stated AF performance of 0.158 s [1]. This front-illuminated homogeneous wafer-to-wafer bonding (oxide bonding), stacked chip, phase detection autofocus, image signal processor charge-coupled device (CCD) imager, fabricated by Toshiba, employed metal half-masks in two of 32 pixels I. INTRODUCTION within a rectangular PDAF subarray occupying the central ~7% of the active pixel array [2]. -

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

Technology Requirements for Using Video Conferencing with Victims
Technology Requirements for Using Video Conferencing with Victims Videoconferencing can offer survivors an alternative way to meet with a provider or counselor. For survivors who lack transportation or live too far from a program or counselor, videoconferencing may be the only way they can obtain medical, legal, or trauma-informed therapy. There are several free or low cost (if upgraded) web-based conference services, each with different advantages and technical requirements. (For more information on safety and privacy considerations when using video conferencing, read “Tips for Using Video Conferencing for Victim Services.”) Types of Web-Based Services and Technical Requirements There are many factors to consider when choosing a web-based video conferencing system, including cost, operating systems, whether calls can be recorded, and how many people can be on a call at the same time. All web-conferencing systems require a connection to the Internet and can be used with either Windows or Mac. The systems reviewed here include Skype, Google Hangouts, Oovoo, Gruveo, and Zoom. Note that the systems reviewed here are available for free or for minimal costs. Some paid-for services may offer more features, security, and privacy. An important consideration in choosing a web-based conferencing system is the degree to which data is encrypted. This means whether data is encrypted indicating no one but the users can access the data or whether the data can be viewed and accessed by the service provider. This may be critical should the service provider receive a subpoena for your data. All of the systems below offer instant messaging, in-call chat, an unlimited number of meetings, and a telephone call-in option while video conferencing. -

VISUAL Message Center Smartconsole User Guide
SmartConsole User Guide 8.0 VMC-Mxx VISUAL Message Center SmartConsole - User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice Copyright © 2014 Tango/04 All rights reserved. Document date: May 2014 Document version: 1.8 Product version: 8.0 No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic mechani- cal, magnetic, optical, chemical, manual, or otherwise, without the prior written permission of Tango/04. Trademarks Any references to trademarked product names are owned by their respective companies. Technical Support For technical support visit our web site at www.tango04.com. Tango/04 Computing Group S.L. Avda. Meridiana 358, 5 A-B Barcelona, 08027 Spain Tel: +34 93 274 0051 Table of Contents Table of Contents Table of Contents.............................................................................. iii How to Use this Guide......................................................................xiii Chapter 1 Introduction ......................................................................................1 1.1. What is VISUAL Message Center?.................................................................2 1.2. How Does VISUAL Message Center Work?...................................................2 1.2.1. Collection Layer ........................................................................................3 -

SECOND AMENDED COMPLAINT 3:14-Cv-582-JD
Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 1 of 19 1 EDUARDO G. ROY (Bar No. 146316) DANIEL C. QUINTERO (Bar No. 196492) 2 JOHN R. HURLEY (Bar No. 203641) PROMETHEUS PARTNERS L.L.P. 3 220 Montgomery Street Suite 1094 San Francisco, CA 94104 4 Telephone: 415.527.0255 5 Attorneys for Plaintiff 6 DANIEL NORCIA 7 UNITED STATES DISTIRCT COURT 8 NORTHERN DISTRICT OF CALIFORNIA 9 DANIEL NORCIA, on his own behalf and on Case No.: 3:14-cv-582-JD 10 behalf of all others similarly situated, SECOND AMENDED CLASS ACTION 11 Plaintiffs, COMPLAINT FOR: 12 v. 1. VIOLATION OF CALIFORNIA CONSUMERS LEGAL REMEDIES 13 SAMSUNG TELECOMMUNICATIONS ACT, CIVIL CODE §1750, et seq. AMERICA, LLC, a New York Corporation, and 2. UNLAWFUL AND UNFAIR 14 SAMSUNG ELECTRONICS AMERICA, INC., BUSINESS PRACTICES, a New Jersey Corporation, CALIFORNIA BUS. & PROF. CODE 15 §17200, et seq. Defendants. 3. FALSE ADVERTISING, 16 CALIFORNIA BUS. & PROF. CODE §17500, et seq. 17 4. FRAUD 18 JURY TRIAL DEMANDED 19 20 21 22 23 24 25 26 27 28 1 SECOND AMENDED COMPLAINT 3:14-cv-582-JD Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 2 of 19 1 Plaintiff DANIEL NORCIA, having not previously amended as a matter of course pursuant to 2 Fed.R.Civ.P. 15(a)(1)(B), hereby exercises that right by amending within 21 days of service of 3 Defendants’ Motion to Dismiss filed October 20, 2014 (ECF 45). 4 Individually and on behalf of all others similarly situated, Daniel Norcia complains and alleges, 5 by and through his attorneys, upon personal knowledge and information and belief, as follows: 6 NATURE OF THE ACTION 7 1. -
REGUS Infographic Rev 1
The changing world of work New technologies are making it easier than ever to create intercontinental workforces and put our businesses on the global map. Employees are looking to use this new connectivity to create a better work-life balance and to make their daily output more efficient. Our latest survey shows how this change has already started, and reveals many of the ideas and motivations behind the flexible working revolution. Remote working on the rise 54% 83% 54% of global respondents 83% of executives plan to already work remotely 2.5 increase their use of flexible days per week or more. employment in the coming years, meaning these numbers are set to rise. The global context Working mothers, ageing populations and young workers seeking flexibility are changing the nature of the global workforce. 6% Returning mothers 13% Older workers remaining beyond their pensionable age 19% Outsourced suppliers 22% Part-time workers 29% Freelance workers 30% Consultants 33% Other The role of technology New Cloud technology, better Wi-Fi and modern communication tools mean we’re on call 24/7. Messaging tools used in the previous month: Whatsapp Skype Facebook Messenger WeChat Viber Snapchat LINE QQ MessageMe Tango ChatOn Hike Kakaotalk Nibuzz 0% 10% 20% 30% 40% 50% 60% 70% Online flexible working tools used in the last month: Dropbox Google Drive Video conferencing Team Viewer WeTransfer Server cloud access Google Hangouts MS Remote Desktop Chrome remote desktop Virtual workgroups Apple remote desktop GoToMyPC LogMeIn Ignition Splashtop Wyse PocketCloud 0% 10% 20% 30% 40% 50% 60% 70% Relishing remote work As these tech advances help employees take their work with them, they’re increasingly seeing the advantages of flexible workspaces. -

Digital Filtering in Saudi Arabia
Opening Digital Borders Cautiously yet Decisively: Digital Filtering in Saudi Arabia Fatemah Alharbi Michalis Faloutsos Taibah University, Yanbu University of California, Riverside Nael Abu-Ghazaleh University of California, Riverside Abstract (a) traditional Internet filtering on websites; and (b) access to mobile applications. The study spans the period from March Our study makes a rare positive observation: Saudi Arabia 2018 to April 2020, with three separate measurements, one in has been opening its digital borders since 2017 in a delib- each calendar year. Our goal is to answer the three questions: erate new era towards openness. In this paper, we present a (a) “what content is filtered?", (b) “how is filtering imple- comprehensive longitudinal study of digital filtering, which mented?", and (c) “how does filtering evolve over time in we define to include both mobile apps and website access, response to geopolitical conditions?" in Saudi Arabia over a period of three years. Our results show that Saudi Arabia has indeed made significant progress We pursue a mutli-pronged strategy as follows. towards opening its digital borders: (a) the use of mobile 1. Quantification: What is filtered? We provide a fairly ex- applications has been significantly permitted; and (2) web ac- tensive study on the accessibility of both mobile apps and cess is becoming more open. We use: (a) 18 social media and websites from within Saudi Arabia and its evolution over communications mobile apps such as WhatsApp, Facetime, time. Our results show significant progress towards the open- and Skype; and (b) Alexa’s top 500 websites in 18 different ing of the country’s digital borders. -
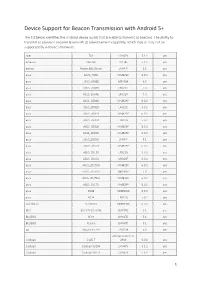
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Table of Contents
2016-2017 PARENT-STUDENT HANDBOOK De Smet Jesuit High School 233 North New Ballas Road Creve Coeur, MO 63141 (314) 567-3500 www.desmet.org DE SMET JESUIT HIGH SCHOOL Parent and Student Handbook Dear Parents: Your knowledge of the information in the Student and Parent Handbook is essential for the efficient operation of the school. Please review this handbook and discuss the guidelines with your son. Each student and his parents must sign a copy of the signature form (that your son will receive the first day of school) and return it to his homeroom teacher. Signing this form indicates that both the student and his parents have read the handbook, including policies regarding acceptable use of computers, and agree to abide by these policies. Additionally, signing this signature page acknowledges your legal and financial responsibility to De Smet Jesuit High School. Also, in an effort to communicate more efficiently, De Smet Jesuit requires at least one current parent/guardian e-mail address. Your son is to return this signed form to his homeroom teacher during the first full week of school. Friday, August 26, 2016 is the deadline. Students will be removed from the De Smet Jesuit network if they have not returned this form by August 26, 2016. There may be a 24-48 hour delay in receiving network privileges if a signed agreement is returned after that date. Additionally, an electronic version of this handbook is available at www.desmet.org. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - HANDBOOK AND COMPUTER POLICY SIGNATURE FORM __________________________________ ________________________________ NAME OF STUDENT (PLEASE PRINT) SR / JR / SO / FR ___________________________________ ______________ ______________ STUDENT SIGNATURE HOMEROOM STUDENT NO.