Windows-Command-Line-Administration-Instant-Reference.Pdf
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Network Printing Guide
Network Printing Guide Windows 95/98/Me Configuration Windows 2000 Configuration Windows XP Configuration Windows NT 4.0 Configuration NetWare Configuration Macintosh Configuration Appendix For safe and correct use of this machine, please be sure to read the Safety Information in the Operating Instructions that comes with the machine before you use it. Introduction To get maximum versatility from this machine all operators should carefully read and follow the instruc- tions in this manual. Please keep this manual in a handy place near the machine. Important Contents of this manual are subject to change without prior notice. In no event will the company be li- able for direct, indirect, special, incidental, or consequential damages as a result of handling or oper- ating the machine. Software Version Conventions Used in this Manual • NetWare 3.x means NetWare 3.12 and 3.2. • NetWare 4.x means NetWare 4.1, 4.11 and IntranetWare. Trademarks Apple, AppleTalk, EtherTalk, LaserWriter, Macintosh and Mac are registered trademarks of Apple Computer, Inc. Ethernet is a registered trademark of Xerox Corporation. Microsoft, Windows and Windows NT are registered trademarks of Microsoft Corporation in the United States and/or other countries. Netscape and Netscape Navigator are registered trademarks of Netscape Communications Corpora- tion. Novell, NetWare and NDS are registered trademarks of Novell, Inc. PostScript is a registered trademark of Adobe Systems, Incorporated. Sun is a registered trademark of Sun Microsystems, Inc. SunOS is a trademark of Sun Microsystems, Inc. Other product names used herein are for identification purposes only and might be trademarks of their respective companies. -

Operating System Boot from Fully Encrypted Device
Masaryk University Faculty of Informatics Operating system boot from fully encrypted device Bachelor’s Thesis Daniel Chromik Brno, Fall 2016 Replace this page with a copy of the official signed thesis assignment and the copy of the Statement of an Author. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Daniel Chromik Advisor: ing. Milan Brož i Acknowledgement I would like to thank my advisor, Ing. Milan Brož, for his guidance and his patience of a saint. Another round of thanks I would like to send towards my family and friends for their support. ii Abstract The goal of this work is description of existing solutions for boot- ing Linux and Windows from fully encrypted devices with Secure Boot. Before that, though, early boot process and bootloaders are de- scribed. A simple Linux distribution is then set up to boot from a fully encrypted device. And lastly, existing Windows encryption solutions are described. iii Keywords boot process, Linux, Windows, disk encryption, GRUB 2, LUKS iv Contents 1 Introduction ............................1 1.1 Thesis goals ..........................1 1.2 Thesis structure ........................2 2 Boot Process Description ....................3 2.1 Early Boot Process ......................3 2.2 Firmware interfaces ......................4 2.2.1 BIOS – Basic Input/Output System . .4 2.2.2 UEFI – Unified Extended Firmware Interface .5 2.3 Partitioning tables ......................5 2.3.1 MBR – Master Boot Record . -

Užitečné Postupy Pro Windows a Office Nepublikované V Oficiální Literatuře Artur Cimbálník
UNIVERZITA PARDUBICE Fakulta elektrotechniky a informatiky Užitečné postupy pro Windows a Office nepublikované v oficiální literatuře Artur Cimbálník Bakalářská práce 2011 Prohlášení autora Prohlašuji, ţe jsem tuto práci vypracoval samostatně. Veškeré literární prameny a informace, které jsem v práci vyuţil, jsou uvedeny v seznamu pouţité literatury. Byl jsem seznámen s tím, ţe se na moji práci vztahují práva a povinnosti vyplývající ze zákona č. 121/2000 Sb., autorský zákon, zejména se skutečností, ţe Univerzita Pardubice má právo na uzavření licenční smlouvy o uţití této práce jako školního díla podle § 60 odst. 1 autorského zákona, a s tím, ţe pokud dojde k uţití této práce mnou nebo bude poskytnuta licence o uţití jinému subjektu, je Univerzita Pardubice oprávněna ode mne poţadovat přiměřený příspěvek na úhradu nákladů, které na vytvoření díla vynaloţila, a to podle okolností aţ do jejich skutečné výše. Souhlasím s prezenčním zpřístupněním své práce v Univerzitní knihovně. V Pardubicích dne 29. 04. 2011 Artur Cimbálník Poděkování Tímto bych chtěl poděkovat doc. Ing Milanu Javůrkovi, CSc., vedoucímu mé bakalářské práce za pomoc při shánění materiálu a jeho rady při psaní tohoto textu. Anotace Práce se zabývá testováním postupů racionalizujících práci ve Windows a programech Microsoft Office. Jsou zde popsány jednotlivé pracovní postupy doplněné grafickými obrazovkami a popisem dané problematiky. Dále hodnotí jednotlivé verze kancelářských balíků Microsoft Office. Klíčová slova Office, Word, Excel, Windows, tipy, postupy, rady Title Useful procedures for Windows and Office unpublished in the official literature. Annotation Bachelor thesis deals with the testing of procedures rationalizing work in Windows and Microsoft Office. There are describing individual work procedures with graphic screens. -

Arc Hydro Geoprocessing Tools - Tutorial
Arc Hydro Geoprocessing Tools - Tutorial Version 2.0 – October 2011 ESRI 380 New York St., Redlands, CA 92373-8100, USA TEL 909-793-2853 FAX 909-793-5953 E-MAIL [email protected] WEB www.esri.com Arc Hydro GP Tools v 2.0 – Tutorial Copyright © 2011 Esri All rights reserved. Printed in the United States of America. The information contained in this document is the exclusive property of Esri. This work is protected under United States copyright law and other international copyright treaties and conventions. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or by any information storage or retrieval system, except as expressly permitted in writing by Esri. All requests should be sent to Attention: Contracts Manager, Esri, 380 New York Street, Redlands, CA 92373-8100, USA. The information contained in this document is subject to change without notice. October 2011 i Arc Hydro GP Tools v 2.0 – Tutorial Table of Contents Introduction 5 Objective 5 Loading Arc Hydro Tools Toolbox 5 Accessing the Arc Hydro Geoprocessing Tools Help 7 Arc Hydro Tools Configuration 9 Arc Hydro Setup 10 1. Set Target Locations 10 2. Set Batch Target Locations 13 3. Standard Geoprocessing Configuration 15 Terrain Preprocessing 16 1. Level DEM 17 2. DEM Reconditioning 22 3. Assign Stream Slope 25 4. Burn Stream Slope 27 5. Build Walls 28 6. Sink Prescreening 29 7. Sink Evaluation 29 8. Sink Selection 31 9. Fill Sinks 32 10. Flow Direction 33 11. -

Transaction Insight Reference Manual Contents I Admin - Filters - Partner Filter
TIBCO Foresight® Transaction Insight® Reference Manual Software Release 5.2 September 2017 Two-second advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN LICENSE.PDF) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO and Two-Second Advantage, TIBCO Foresight EDISIM, TIBCO Foresight Instream, TIBCO Foresight Studio, and TIBCO Foresight Transaction Insight are either registered trademarks or trademarks of TIBCO Software Inc. in the United States and/or other countries. -
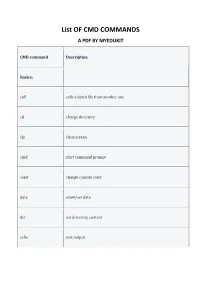
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Vmware ESX Host Utilities 5.2.1 Installation and Setup Guide
IBM System Storage N series VMWare ESX Host Utilities 5.2.1 Installation and Setup Guide GC53-1173-03 NA 210-05158_A0 Table of Contents | 3 Contents Supported features ....................................................................................... 7 Getting information, help, and services ...................................................... 9 Before you call ............................................................................................................ 9 Using the documentation ............................................................................................. 9 Web sites ................................................................................................................... 10 Accessing online technical support ........................................................................... 10 Hardware service and support ................................................................................... 10 Supported servers and operating systems .................................................................. 10 Firmware updates ...................................................................................................... 10 How to send your comments ...................................................................... 13 Changes to this document: March 2011 ................................................... 15 Introduction to Host Utilities ..................................................................... 17 What the Host Utilities are ....................................................................................... -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

View the Slides (Smith)
Network Shells Michael Smith Image: https://commons.wikimedia.org/wiki/File:Network-connections.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png Management at a distance (netsh) Netsh: Configure DHCP servers with netsh -r RemoteMachine -u domain\username [RemoteMachine] netsh>interface [RemoteMachine] netsh interface>ipv6 [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (netsh) Netsh: Configure DHCP servers with netsh Location-r RemoteMachine -u domain\username Hierarchical [RemoteMachine] netsh>interfacecontext Simpler [RemoteMachine] netsh interface>ipv6 commands [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (WSMan) WSMan (in Powershell): Manage Windows remotely with Set-Location -Path WSMan:\SERVER01 Get-ChildItem -Path . Set-Item Client\TrustedHosts *.domain2.com -Concatenate Reference: https://docs.microsoft.com/en-us/powershell/module/microsoft.wsman.management/about/about_wsman_provider -

Server Support Interview Questions and Answers Guide
Server Support Interview Questions And Answers Guide. Global Guideline. https://www.globalguideline.com/ Server Support Interview Questions And Answers Global Guideline . COM Server Support Job Interview Preparation Guide. Question # 1 Tell me where are cluster logs stored? Answer:- Please share your answers. Read More Answers. Question # 2 What are the Logical / Physical Structures of the AD Environment? Answer:- Active Directory Logical components are Forests, Trees, Domains, OUs and Objects. Active Directory Physical components are Domain Controllers, Sites and subnets. Read More Answers. Question # 3 What applications or services use AD application partitions? Name a couple? Answer:- Application partition contains the information of application data and other data related to application as well. But it does not contain any data related AD object such as USER, COMPUTER and GROUP. The saved data will be replicated to some of the particular DC not to all the DCs. Read More Answers. Question # 4 What are the types of hard disks used in servers? Answer:- Mostly we use scsi hardrive in server due few reason to it, high scalability & flexibility in raid array, faster from other type of hdd interface like-sata,ata,ide also it reliable & compatible with older scsi devices Read More Answers. Question # 5 What are some of the command-line tools available for managing a Windows 2003 Server/Active Directory environment? Answer:- Command Line Tools 1) GPupdate 2) Where 3) SystemInfo 4) CSVDE 5) LDIFDE 6) CMDCONS 7) Ipconfig 8) RoboCopy 9) CMDHere 10) PathPing Read More Answers. Question # 6 What if a FSMO server role fails? Answer:- FSMO roles are important role in server . -

Netsh Commands William John Holden 20140411 (Version 2) Interface Configuration Configure an Ipv4 Address with Subnet Mask and Default Gateway
Netsh Commands William John Holden 20140411 (version 2) Interface Configuration Configure an IPv4 address with subnet mask and default gateway. Omitted netmask implies classful addressing. netsh int ipv4 set address "Local Area Connection" static 192.168.1.3 255.255.255.0 192.168.1.1 Remove an IPv4 address and default gateway from an interface. netsh int ipv4 del address "Local Area Connection" 192.168.1.3 192.168.1.1 You can add more than one IP address to an interface. Additional addresses don't show up in ipconfig without /all. netsh int ipv4 add address "Local Area Connection" 192.168.1.4 Add a global unicast IP with prefix. Prefix is optional and defaults to /64. netsh int ipv6 set address "Local Area Connection" 2001:beef::1/64 Add a linklocal IP to an interface. See the similarity to above? netsh int ipv6 add address "Local Area Connection" fe80::6 Delete the IP. Remove a linklocal IP the same way. netsh int ipv6 del address "Local Area Connection" 2001:beef::1 Set an IPv6 default route. netsh int ipv6 add route ::/0 "Local Area Connection" fe80::3 Delete the default route. netsh int ipv6 delete route ::/0 "Local Area Connection" fe80::3 Reset Configuration Reset interface configuration completely (requires restart): netsh int ipv6 reset all netsh int ipv4 reset all shutdown r t 0 Verification (“show commands”) netsh has several commands that are very similar to ipconfig, route print (netstat r), netstat a, and getmac. Poke around netsh int ipv4 show ? and you’ll find lots of interesting stuff. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies.