Virus Bulletin, November 1990
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

C:\Andrzej\PDF\ABC Nagrywania P³yt CD\1 Strona.Cdr
IDZ DO PRZYK£ADOWY ROZDZIA£ SPIS TREFCI Wielka encyklopedia komputerów KATALOG KSI¥¯EK Autor: Alan Freedman KATALOG ONLINE T³umaczenie: Micha³ Dadan, Pawe³ Gonera, Pawe³ Koronkiewicz, Rados³aw Meryk, Piotr Pilch ZAMÓW DRUKOWANY KATALOG ISBN: 83-7361-136-3 Tytu³ orygina³u: ComputerDesktop Encyclopedia Format: B5, stron: 1118 TWÓJ KOSZYK DODAJ DO KOSZYKA Wspó³czesna informatyka to nie tylko komputery i oprogramowanie. To setki technologii, narzêdzi i urz¹dzeñ umo¿liwiaj¹cych wykorzystywanie komputerów CENNIK I INFORMACJE w ró¿nych dziedzinach ¿ycia, jak: poligrafia, projektowanie, tworzenie aplikacji, sieci komputerowe, gry, kinowe efekty specjalne i wiele innych. Rozwój technologii ZAMÓW INFORMACJE komputerowych, trwaj¹cy stosunkowo krótko, wniós³ do naszego ¿ycia wiele nowych O NOWOFCIACH mo¿liwoYci. „Wielka encyklopedia komputerów” to kompletne kompendium wiedzy na temat ZAMÓW CENNIK wspó³czesnej informatyki. Jest lektur¹ obowi¹zkow¹ dla ka¿dego, kto chce rozumieæ dynamiczny rozwój elektroniki i technologii informatycznych. Opisuje wszystkie zagadnienia zwi¹zane ze wspó³czesn¹ informatyk¹; przedstawia zarówno jej historiê, CZYTELNIA jak i trendy rozwoju. Zawiera informacje o firmach, których produkty zrewolucjonizowa³y FRAGMENTY KSI¥¯EK ONLINE wspó³czesny Ywiat, oraz opisy technologii, sprzêtu i oprogramowania. Ka¿dy, niezale¿nie od stopnia zaawansowania swojej wiedzy, znajdzie w niej wyczerpuj¹ce wyjaYnienia interesuj¹cych go terminów z ró¿nych bran¿ dzisiejszej informatyki. • Komunikacja pomiêdzy systemami informatycznymi i sieci komputerowe • Grafika komputerowa i technologie multimedialne • Internet, WWW, poczta elektroniczna, grupy dyskusyjne • Komputery osobiste — PC i Macintosh • Komputery typu mainframe i stacje robocze • Tworzenie oprogramowania i systemów komputerowych • Poligrafia i reklama • Komputerowe wspomaganie projektowania • Wirusy komputerowe Wydawnictwo Helion JeYli szukasz ]ród³a informacji o technologiach informatycznych, chcesz poznaæ ul. -
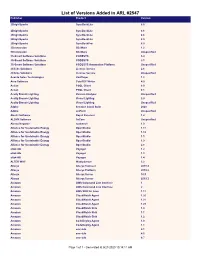
List of Versions Added in ARL #2547 Publisher Product Version
List of Versions Added in ARL #2547 Publisher Product Version 2BrightSparks SyncBackLite 8.5 2BrightSparks SyncBackLite 8.6 2BrightSparks SyncBackLite 8.8 2BrightSparks SyncBackLite 8.9 2BrightSparks SyncBackPro 5.9 3Dconnexion 3DxWare 1.2 3Dconnexion 3DxWare Unspecified 3S-Smart Software Solutions CODESYS 3.4 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions CODESYS Automation Platform Unspecified 4Clicks Solutions License Service 2.6 4Clicks Solutions License Service Unspecified Acarda Sales Technologies VoxPlayer 1.2 Acro Software CutePDF Writer 4.0 Actian PSQL Client 8.0 Actian PSQL Client 8.1 Acuity Brands Lighting Version Analyzer Unspecified Acuity Brands Lighting Visual Lighting 2.0 Acuity Brands Lighting Visual Lighting Unspecified Adobe Creative Cloud Suite 2020 Adobe JetForm Unspecified Alastri Software Rapid Reserver 1.4 ALDYN Software SvCom Unspecified Alexey Kopytov sysbench 1.0 Alliance for Sustainable Energy OpenStudio 1.11 Alliance for Sustainable Energy OpenStudio 1.12 Alliance for Sustainable Energy OpenStudio 1.5 Alliance for Sustainable Energy OpenStudio 1.9 Alliance for Sustainable Energy OpenStudio 2.8 alta4 AG Voyager 1.2 alta4 AG Voyager 1.3 alta4 AG Voyager 1.4 ALTER WAY WampServer 3.2 Alteryx Alteryx Connect 2019.4 Alteryx Alteryx Platform 2019.2 Alteryx Alteryx Server 10.5 Alteryx Alteryx Server 2019.3 Amazon AWS Command Line Interface 1 Amazon AWS Command Line Interface 2 Amazon AWS SDK for Java 1.11 Amazon CloudWatch Agent 1.20 Amazon CloudWatch Agent 1.21 Amazon CloudWatch Agent 1.23 Amazon -

Instant File Delivery Software Version 3.01
Using DropChuteTM Instant file delivery software Version 3.01 Instructions for the DropChute family of software, including: l DropChute Pro l DropChute Enterprise The makers of HyperTerminal®, included l DropChute Lite with Microsoft Windows Information in this manual is subject to change without notice and does not represent a commitment on the part of Hilgraeve Inc. The software described in this manual is furnished under a license agreement. The software may be used or copied only in accordance with the terms of the agreement. It is against the law to copy the software on any medium except as specifically allowed in the agreement. No part of this manual may be reproduced or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without prior written permission of Hilgraeve Inc. RESTRICTED RIGHTS LEGEND Use, duplication, or disclosure by the Government is subject to restrictions set forth in paragraph (b)(3)(B) of the Rights in Technical Data and Computer Software clause of DAR 7-104.9(a). Contractor/Manufacturer is Hilgraeve, Genesis Centre, 111 Conant Avenue, Suite A, Monroe, MI 48161. TRADEMARKS Microsoft, MS-DOS, and Windows are registered trademarks of Microsoft Corporation. DropChute, HyperGuard, and CommSense are trademarks of Hilgraeve Inc. Commercial names of products from other manufacturers or developers that appear in this manual are registered or unregistered trademarks of those respective manufacturers or developers, which have expressed neither approval nor disapproval of Hilgraeve products. DropChute Lite, DropChute Pro, and DropChute Enterprise are protected by US Patents 5,319,776 and 5,553,271. Document version 3.01 Copyright Hilgraeve Inc. -

20. CLI Command Summary
SM8TAT2SA, SM16TAT2SA, SM24TAT2SA and SM8TAT2SA-DC Smart Managed Gigabit Ethernet PoE+ Switches 8-/16-/24-Port Gigabit PoE+, 2-Port 100/1000 SFP CLI Reference 33718 Rev. E 33718 Rev. E https://www.transition.com Page 1 of 270 Transition Networks SMxTAT2SA CLI Reference Trademarks All trademarks and registered trademarks are the property of their respective owners. Copyright Notice/Restrictions Copyright © 2017-2020 Transition Networks. All rights reserved. No part of this work may be reproduced or used in any form or by any means (graphic, electronic or mechanical) without written permission from Transition Networks. Printed in the U.S.A. SMxTAT2SA Smart Managed Switches CLI Reference, 33718 Rev. E Contact Information Transition Networks 10900 Red Circle Drive Minnetonka, MN 55343 USA tel: +1.952.941.7600 | toll free: 1.800.526.9267 | fax: 952.941.2322 [email protected] | [email protected] | [email protected] Revision History Rev Date Description Update for FW v1.01.1227 to support DMS on VLAN other than 1. FW v1.02.1261 updates SSL certificates. FW v1.02.1363: 802.1x supports assign VLAN attribute; C 11/9/18 DHCP server based on incoming port to assign IP address; add DHCP per Port, Link-Local Address binding interface, and NTP Time Sync Interval. Add Interface Config commands. Update for FW v1.02.1368 which adds non-stop PoE power on reboot. Update for FW v1.02.1398 which adds PoE Force mode. Update for FW v1.02.1409 HW v1.03, Mechanical D 8/26/19 v1.01, and PoE FW v 208-211: upgrade security, add Traffic Manager back in DMS, PoE force mode, PoE Auto Power Reset event in Event Notifications, add PoE Soft Reboot feature. -

List of Applications Updated in ARL #2581
List of Applications Updated in ARL #2581 Application Name Publisher .NET Core Runtime 3.0 Preview Microsoft .NET Core Toolset 3.1 Preview Microsoft .NET Framework 4.5 Microsoft .NET Framework 4.6 Microsoft .NET Framework Developer Pack 4.7 Microsoft .NET Framework Multi-Targeting Pack for Windows Store Apps 4.5 RC Microsoft .NET Framework SDK 4.8 Microsoft _connect.BRAIN 4.8 Bizerba 2200 TapeStation Software 3.1 Agilent Technologies 2200 TapeStation Software 3.2 Agilent Technologies 24x7 Automation Suite 3.6 SoftTree Technologies 3500 Rack Configuration Software 6.0 Bently Nevada 365 16.0 Microsoft 3D Sprint 2.10 3D Systems 3D Sprint 2.11 3D Systems 3D Sprint 2.12 3D Systems 3D Viewer Microsoft 3PAR Host Explorer VMware 4.0 HP 4059 Extended Edition Attendant Console 2.1 ALE International 4uKey 1.4 Tenorshare 4uKey 1.6 Tenorshare 4uKey 2.2 Tenorshare 50 Accounts 21.0 Sage Group 50 Accounts 25.1 Sage Group 793 Controller Software 5.8 MTS Systems 793 Controller Software 5.9 MTS Systems 793 Controller Software 6.1 MTS Systems 7-Zip 19.00 Igor Pavlov ABAQUS 2018 Student Dassault Systemes ABAQUS 2019 Student Dassault Systemes Abstract 73.0 Elastic Projects ABU Service 14.10 Teradata Access Client 3.5 Barracuda Networks Access Client 3.7 Barracuda Networks Access Client 4.1 Barracuda Networks Access Module for Azure 15.1 Teradata Access Security Gateway (ASG) Soft Key Avaya AccuNest 10.3 Gerber Technology AccuNest 11.0 Gerber Technology ACDSee 2.3 Free ACD Systems ACDSee 2.4 Free ACD Systems ACDSee Photo Studio 2019 Professional ACD Systems -

Model 428T Operators Manual
MODEL 428T DIRECT THERMAL PRINTER OPERATOR’S MANUAL PART NUMBER: 880037-0155 September 29, 2014 CPC Copyright © 2014 by Microcom Corporation, Lewis Center, Ohio – All rights reserved. Printed in the United States of America Proprietary Statement This manual contains information proprietary to Microcom Corporation. This information is intended solely for the use of parties operating and maintaining such equipment described herein. Product Enhancements Microcom Corporation is committed to the continual improvement of performance and quality in our products. For this reason, specifications are subject to change without notice. Liability Disclaimer Microcom Corporation makes every effort to assure that all information and specifications contained in this manual are accurate; however, mistakes are sometimes made. Microcom Corporation shall not be liable for any damages resulting in the use or misuse of this product. The exclusion or limitation involving consequential or incidental damage does not apply to all states; therefore limitation mentioned above may or may not apply. FCC Compliance Statement This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy, and if not installed and used in accordance with the instructions contained in this manual, may cause harmful interference to radio communications. HyperTerminal® and HyperAccess® are trademarks of Hilgraeve Inc. Centronics® is a registered trademark of Data Computer Corporation. HP® and LaserJet II® are trademarks of Hewlett-Packard Company. -

438M Programming Guide - 880043-0101 I
438M PROGRAMMING GUIDE PART NUMBER 880043-0101 Revised: June 22, 2021 CPC © Copyright 2021 by Microcom Corporation, Lewis Center, Ohio – All rights reserved. Printed in the United States of America This Page Intentionally Left Blank This Page Intentionally Left Blank Proprietary Statement This manual contains information proprietary to Microcom Corporation. This information is intended solely for the use of parties operating and maintaining such equipment described herein. Product Enhancements Microcom Corporation is committed to the continual improvement of performance and quality in our products. For this reason, specifications are subject to change without notice. Liability Disclaimer Microcom Corporation makes every effort to assure that all information and specifications contained in this manual are accurate; however, mistakes are sometimes made. Microcom Corporation shall not be liable for any damages resulting in the use or misuse of this product. The exclusion or limitation involving consequential or incidental damage does not apply to all states; therefore limitation mentioned above may or may not apply. FCC Compliance Statement This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy, and if not installed and used in accordance with the instructions contained in this manual, may cause harmful interference to radio communications. SolarWinds® is a registered trademark of SolarWinds.Net, Inc. Tera Term Pro® is a registered trademark of T. -

Express XR/XRT 128 Kbps ISDN Modem
Table of Contents Express XR/XRT 128 kbps ISDN Modem Quick Start Guide 1200153L1 Express XR, Data Only 1200153L2 Express XRT, Two Phone Ports 3360.9VU01 Express XR Power Supply, 9.0 V DC Output 336048VUR-2 Express XRT Power Supply, 48 V DC Output 61200.153L1-13E September 1996 Table of Contents Trademarks Express XR, Express XRT, and Express Configuration Wizard are trademarks of ADTRAN, Inc. Hayes is a registered trademark of Hayes Microcomputer Products, Inc. HyperACCESS is a registered trademark of Hilgraeve Inc. MicroPhone Pro is a trademark of Software Ventures Corporation. PROCOMM PLUS is a registered trademark of Datastorm Technologies, Inc. ReachOut is a registered trademark of Stac Electronics. Windows is a registered trademark and Windows NT is a trademark of Microsoft Corporation. pcANYWHERE is a trademark of Symantec Corporation. The Express XR and Express XRT incorporate Synchronous Data Compres- sion based on either IBM or Stac Electronics proprietary intellectual property depending on the time of manufacture. The following trademarks and copyrights are applicable: Stacker LZS Compression Copyright (c) 1989 Carnegie Mellon University. All rights reserved. Redistribution and use in source and binary forms are permitted provided that the above copyright notice and this paragraph are duplicated in all such forms and that any documentation, advertising materials, and other materi- als related to such distribution and use acknowledge that the software was developed by Carnegie Mellon University. The name of the University may not be used to endorse or promote products derived from this software without specific prior written permission. This software is provided "as is" and without any express or implied warranties, including, without limita- tion, the implied warranties of merchantability and fitness for a particular 901 Explorer Boulevard P.O. -

Apprentice431 Usermanual V1
© 2001 Autodesk, Inc. All rights reserved. Autodesk, the Autodesk logo, AutoCAD, Buzzsaw, Layered Document Format, LDF and Plans & Specs are either registered trademarks or trademarks of Buzzsaw, Inc. or Autodesk, Inc. in the U.S.A. or other countries. All other trademarks are the property of their respective owners. Ppir ! 8uhr D qpv :KDW,V$SSUHQWLFH" $SSUHQWLFH6HUYHU $SSUHQWLFH5HPRWH&OLHQW 7KH&RQFHSW *HWWLQJ+HOS 2QOLQHKHOS 7RROWLSV :HEVLWH 8uhr ! Dhyyhv ,QVWDOOLQJ$SSUHQWLFH 8uhr " UurTsh rDr shpr 6WDUWLQJ$SSUHQWLFH 7KH8VHU,QWHUIDFH 0HQXEDU 7RROEDUDQGTXLFNPHQXV ,QIRUPDWLRQEDU 3HQRYHUYLHZ :LQGRZ /RJR 9LHZHUWRROEDU 7LWOHEDU 6WDWXVEDU $FFHVVLQJPHQXVDQGRSWLRQV 6HWWLQJSUHIHUHQFHV 4XLWWLQJ$SSUHQWLFH 8uhr # 8svt hv &RQILJXULQJ0DMRU3URGXFWV *HQHUDOWDE &RPPXQLFDWLRQVWDE -RE'HIDXOW6HWWLQJVWDE 'LUHFWRULHVWDE 3RVW6FULSWWDE " $XWR&$'WDE 3DSHU6L]HVWDE ,QWURGXFWLRQWR&RQILJXUDWLRQ0DQDJHU 8VLQJWKH&RQILJXUDWLRQ0DQDJHU 8QGHUVWDQGLQJWKHVHWWLQJV /RFDWLQJVSHFLILFVHWWLQJV 8uhr $ X xP qr 8vr $FFHVVLQJWKH:RUN2UGHU&XVWRPL]HU 2UGHU5HFHLSW+HDGHU :RUN2UGHUILHOGV :RUN2UGHUFRORUVDQGIRQWV 3UHYLHZLQJWKH:RUN2UGHU&KDQJHV 'LVWULEXWLQJWKH&XVWRPL]HG:RUN2UGHU 8uhr % ChqyvtEi ,QWURGXFWLRQ &UHDWLQJQHZMREV $GGLQJILOHVWRMREV $GGLQJGUDZLQJVIURP3URMHFW3RLQWVLWHV ,QVHUWLQJ)LOHVLQWRD-RE $GGLQJILOHVIURPDWH[WILOH 6DYLQJMREV &ORVLQJMREV 2SHQLQJH[LVWLQJMREV 0HUJLQJMREV 5HPRYLQJGUDZLQJVIURPMREV 'HOHWLQJGUDZLQJV 5HQDPLQJMREV 2UJDQL]LQJ'UDZLQJV:LWKLQD-RE 6NLSSLQJGUDZLQJVZLWKLQDMRE 0RYLQJGUDZLQJVZLWKLQDMRE &RS\LQJGUDZLQJVZLWKLQDMRE -

Auto-Configuration of Cisco Routers with Application Software
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2003-09 Auto-configuration of Cisco routers with application software Prado, Alexandre Barcellos Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/6285 MONTEREY, CALIFORNIA THESIS AUTO-CONFIGURATION OF CISCO ROUTERS WITH APPLICATION SOFTWARE by Alexandre Barcellos Prado September 2003 Thesis Advisor: Geoffrey Xie Second Reader: John Gibson Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704- 0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington DC 20503. 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED September 2003 Master’s Thesis 4. TITLE AND SUBTITLE: Auto-Configuration of Cisco 5. FUNDING NUMBERS Routers with Application Software 6. AUTHOR(S) Prado, Alexandre 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING ORGANIZATION Naval Postgraduate School REPORT NUMBER Monterey, CA 93943-5000 9. SPONSORING /MONITORING AGENCY NAME(S) AND ADDRESS(ES) 10. SPONSORING/MONITORING N/A AGENCY REPORT NUMBER 11. SUPPLEMENTARY NOTES The views expressed in this thesis are those of the author and do not reflect the official policy or position of the Department of Defense or the U.S. -

Communications Manual
TABLE OF CONTENTS Understanding GPNet 2 GPNet Submissions 2 Acceptable Asynchronous Communications Communications Packages 2 Technical Support 3 ANSI 837 Completion Information 4 Manual Version 5010 4 Payer ID Information 4 Using GPNet Asynchronous Transmission 5 Log In and User Validation 5 Messages 5 Main Menu 5 Upload a File 5 Download a File 6 List Files In Mailbox 7 Example of INV Message 8 NDM Response Examples 8 Informational Message 8 Invalid File Header 8 Rejected ID 8 System Accessibility 8 GPNet File Transfer Protocol (FTP) 9 FTP Instructions 9 Logging onto GPNet Using FTP 9 Uploading Files Using FTP 12 Downloading Files Using FTP 13 Network Data Mover (NDM) Specifications 14 NDM Node Connection 14 PLEASE NOTE: The GPNet Communications Manual is subject to change as we receive Report Retrieval 14 additional information regarding the transition 837 Claims Submission Dataset Names 15 to HIPAA-ready electronic formats. We will post updated versions of this and other ANSI v5010 Responses 16 HIPAA-related documents on our website. Please visit the CGS J15 Web page at TA1 16 http://www.cignagovernmentservices.com/J15. 999 16 277CA 16 Accepted 17 Rejected 18 835 18 GPNet Communications Manual UNDERSTANDING GPNET GPNet is the EDI gateway to CGS. The GPNet communication platform supports asynchronous telecommunications up to 56K bps. It will support numerous asynchronous telecommunication protocols, including Kermit, Xmodem (Check Sum), Ymodem (Batch), and Zmodem. Most off- the-shelf communication software will support one or all of these protocols. You may select any of the protocols indicated; however, Zmodem is recommended based on its speed and reliability. -

994-0089 D400 Substation Gateway Instruction Manual
GE Grid Solutions Multilin D400TM Substation Gateway Instruction Manual 994-0089 Version 2.40 Revision 4 GE Information GE Grid Solutions Copyright Notice © 2006-2019, General Electric Company. All rights reserved. The information contained in this online publication is the exclusive property of General Electric Company, except as otherwise indicated. You may view, copy and print documents and graphics incorporated in this online publication (the “Documents”) subject to the following: (1) the Documents may be used solely for personal, infor- mational, non-commercial purposes; (2) the Documents may not be modified or altered in any way; and (3) Gen- eral Electric Company withholds permission for making the Documents or any portion thereof accessible via the internet. Except as expressly provided herein, you may not use, copy, print, display, reproduce, publish, license, post, transmit or distribute the Documents in whole or in part without the prior written permission of General Electric Company. The information contained in this online publication is proprietary and subject to change without notice. The software described in this online publication is supplied under license and may be used or copied only in accor- dance with the terms of such license. Trademark Notices GE and are trademarks and service marks of General Electric Company. * Trademarks of General Electric Company. CompactFlash is a registered trademark of SanDisk Corporation. ERNI is a registered trademark of ERNI Elek- troapparate GMBH. Hyperterminal is a registered trademark of Hilgraeve, Incorporated. Tera Term is a registered trademark of T. Teranishi, IEC is a registered trademark of Commission Electrotechnique Internationale. IEEE is a registered trademark of the Institute of Electrical and Electronics Engineers, Inc.