The Reality of Virtual Computing Chris Hare, CISSP, CISA
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Applications Log Viewer
4/1/2017 Sophos Applications Log Viewer MONITOR & ANALYZE Control Center Application List Application Filter Traffic Shaping Default Current Activities Reports Diagnostics Name * Mike App Filter PROTECT Description Based on Block filter avoidance apps Firewall Intrusion Prevention Web Enable Micro App Discovery Applications Wireless Email Web Server Advanced Threat CONFIGURE Application Application Filter Criteria Schedule Action VPN Network Category = Infrastructure, Netw... Routing Risk = 1-Very Low, 2- FTPS-Data, FTP-DataTransfer, FTP-Control, FTP Delete Request, FTP Upload Request, FTP Base, Low, 4... All the Allow Authentication FTPS, FTP Download Request Characteristics = Prone Time to misuse, Tra... System Services Technology = Client Server, Netwo... SYSTEM Profiles Category = File Transfer, Hosts and Services Confe... Risk = 3-Medium Administration All the TeamViewer Conferencing, TeamViewer FileTransfer Characteristics = Time Allow Excessive Bandwidth,... Backup & Firmware Technology = Client Server Certificates Save Cancel https://192.168.110.3:4444/webconsole/webpages/index.jsp#71826 1/4 4/1/2017 Sophos Application Application Filter Criteria Schedule Action Applications Log Viewer Facebook Applications, Docstoc Website, Facebook Plugin, MySpace Website, MySpace.cn Website, Twitter Website, Facebook Website, Bebo Website, Classmates Website, LinkedIN Compose Webmail, Digg Web Login, Flickr Website, Flickr Web Upload, Friendfeed Web Login, MONITOR & ANALYZE Hootsuite Web Login, Friendster Web Login, Hi5 Website, Facebook Video -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Remote Process Control Over the Internet
Session 1520 Remote Process Control over the Internet Mark Smith Purdue University North Central Abstract This paper presents remote process control over the Internet using remote-control computing software. Remote-control computing software allows you to connect to remote computers from your computer and control those systems. You can monitor and control attached system processes, provide problem solving assistance, upload and download files, and even change system parameters. This paper describes what remote-control computing is, who the major players in the industry are, and how it can be used to monitor and control remote processes. A case study of remote-control computing software in operation is also presented, describing how one off-the-shelf package was setup to monitor and control a plant floor production system. Introduction Networking technologies, and especially the Internet, have become a major component of application systems. As we teach the design and implementation of process control systems in the Engineering curriculum, we must recognize that these systems will require capabilities for control and support from remote locations. For example, the need for remote control may be driven by the high cost of a particular process. The Oak Ridge National Laboratory uses remote process control at its High Temperature Materials Laboratory to allow researches from across the country to use a million-dollar electron microscope1. Even when control of the process is not required across the country, there are times when it is helpful (or even critical) to monitor another node on a LAN. For example, Conquergood describes in his research the ability to monitor and control potentially high voltages from one location by gathering voltage information from PCs doing data acquisition from various plant processes2. -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

Teaching General Chemistry with Instructor's
TEachiNG GENEral CHEMISTry WITH INSTRUCTOR’S SCREEN SHARING: STUDENTS’ OPINIONS ABOUT THE IDEA AND ITS IMPLEMENTATION Uladzimir Slabin Abstract. Knowing students’ opinions about instructor’s screen sharing via various media is important for developing online science courses including chemistry. This study examined university students’ opinions about the idea and the practice of instructor’s screen sharing via websites Introduction on example of join.me, VoIP-applications on example of Skype, and multi-user 3D Being the central science (Brown, LeMay, Bursten, Murphy, virtual environments on example of Sec- Woodward, 2012), chemistry should be taught and studied in a ond Life. It was conducted during summer special and effective way. Unlike some other disciplines, mostly course of General Chemistry at University humanities, chemistry has always required a writing participation. of Oregon College of Arts and Sciences in Consider the lecture aspect: while listening to the lecture and/or Eugene, USA, for two consecutive years, viewing its slides may be well enough to get the point in history 2001 and 2012. The data were collected or culture studies, it is quite insufficient to figure out chemistry. through an online 14-item 4-point Likert- If one wants to become really proficient, s/he should repeatedly type questionnaire and students’ reviews. write chemical symbols, formulas, equations, etc. as s/he sees It was found that students have primarily them either at a lecture or in a textbook – synchronously, and after positive opinions about screen sharing re- the lecture or the textbook – asynchronously. Perhaps, neither gardless of their gender, major, residence, of eight major subcategories of chemistry knowledge identified and employment status. -

Hacking for Dummies.Pdf
01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page v 01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page ii Hacking For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 Copyright © 2004 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permis- sion of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4447, e-mail: permcoordinator@ wiley.com. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. -
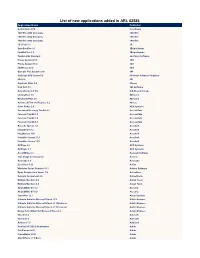
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

What Did You Do in School Today Junior? an Analysis of Application Usage on K-12 School Networks
What Did You Do In School Today Junior? An Analysis of Application Usage on K-12 School Networks March 2012 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com Table of Contents Key Findings ....................................................................................................................................................... 3 Introduction ....................................................................................................................................................... 4 Tools That Enable Circumvention ....................................................................................................................... 5 Encrypted Tunnels: Protection or Evasion? ................................................................................................................ 5 Remote Desktop Applications: What is the Use Case? .............................................................................................. 6 External Proxies: K‐12 Usage is Double Enteprise Usage ........................................................................................... 7 P2P FileSharing: Solution Of Choice For Moving Large Files ................................................................................. 8 Browser‐based Filesharing: Education or Entertainment? ................................................................................... 9 Browser‐based Filesharing use Case: Productivity .................................................................................................. -

Specifičnosti Softvera Teamviewer Za Podršku Timskom Radu Na Daljinu
Međunarodna naučna konferencija International Scientific Conference MENADŽMENT 2010 MANAGEMENT 2010 Kruševac, Srbija, 17-18. mart 2010 Krusevac, Serbia, 17-18 March, 2010 SPECIFIČNOSTI SOFTVERA TEAMVIEWER ZA PODRŠKU TIMSKOM RADU NA DALJINU THE CHARACTERISTICS OF TEAMVIEWER SOFTWARE SUPPORT FOR TEAM WORK AT DISTANCE Marija Marković1 Zoran Nikolić2 Radovan Milovankić3 Rezime: Zbog kontinuiranog razvoja i globalizacije savremene radne snage, sve više firmi i ustanova razmišlja o prihvatanju strategije rada na daljinu s ciljem uštede troškova i zadržavanja najkvalitetnijih radnika. Softversko rešenje TeamViewer, koje je predstavljeno u radu, doseže nove nivoe efikasnosti i delotvornosti jer omogućava korisnicima rad i međusobnu saradnju bez obzira na to gde se fizički nalaze. Njegovom primenom omogućava se povezanost korisnika na daljinu i njihova virtualna saradnja, što doprinosi porastu merljivih prednosti rada i učenja na daljinu, kako za radnike i poslodavce, tako za studente i predavače. Istaknuto je da je TeamViewer jednostavan, brz i siguran program koji ima ulogu daljinskog upravljača. Posebna pažnja posvećena je scenarijima u kojima se on može koristiti. Pored mogućnosti primene ukazano je i na njegove nedostatke. Ključne reči: Rad na daljinu, učenje na daljinu, softver TeamViewer Abstract: Due to continuous development and globalization of the modern workforce, more and more companies and institutions think about the acceptance strategy of distance in order to save costs and retain quality workers. TeamViewer software solution, which is represented in the work, reaching new levels of efficiency and effectiveness because it lets users work and cooperation, regardless of where they are physically located. This application allows the connection to the remote user and their virtual cooperation, which contributes to increasing measurable benefits of work and distance learning, both for workers and employers, so for students and lecturers. -

Symantec Pcanywhere™ Administrator's Guide
Symantec pcAnywhere™ Administrator’s Guide Symantec pcAnywhere™ Administrator’s Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 10.0 PN: 07-30-00453 Copyright Notice Copyright 1995-2001 Symantec Corporation. All Rights Reserved. This document may not, in whole or in part, be copied, photocopied, reproduced, translated, or reduced to any electronic medium or machine-readable form without prior consent in writing from Symantec Corporation, 20330 Stevens Creek Boulevard, Cupertino, CA 95014. ALL EXAMPLES WITH NAMES, COMPANY NAMES, OR COMPANIES THAT APPEAR IN THIS GUIDE ARE FICTICIOUS AND DO NOT REFER TO, OR PORTRAY, IN NAME OR SUBSTANCE, ANY ACTUAL NAMES, ORGANIZATIONS, ENTITIES, OR INSTITUTIONS. ANY RESEMBLANCE TO ANY REAL PERSON, ORGANIZATION, ENTITY, OR INSTITUTION IS PURELY COINCIDENTAL. Every effort has been made to ensure the accuracy of this guide. However, Symantec makes no warranties with respect to this documentation and disclaims any implied warranties of merchantability and fitness for a particular purpose. Symantec shall not be liable for any errors or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual or the examples herein. The information in this document is subject to change without notice. Trademarks Symantec pcAnywhere, Symantec, the Symantec logo, ColorScale, and SpeedSend, are U.S. registered trademarks of Symantec Corporation. Microsoft, MS, Windows, Windows NT, Word, and the Office logo are either registered trademarks or trademarks of Microsoft Corporation in the U.S. and/or other countries. Other product names mentioned in this guide may be trademarks or registered trademarks of their respective companies and are the sole property of their respective manufacturers. -

Mac OS X Server Network Services Administration for Version 10.4 Or Later
Mac OS X Server Network Services Administration For Version 10.4 or Later Apple Computer, Inc. © 2005 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid-for support services. Every effort has been made to ensure that the information in this manual is accurate. Apple computer, Inc., is not responsible for printing or clerical errors. Apple 1Infinite Loop Cupertino, CA 95014-2084 408-996-1010 www.apple.com Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AirPort, AppleScript, AppleShare, AppleTalk, Mac, Mac OS, Macintosh, Power Mac, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. -

Comparison of Remote Desktop Software - Wikipedia
9/29/2020 Comparison of remote desktop software - Wikipedia Comparison of remote desktop software This page is a comparison of remote desktop software available for various platforms. Contents Remote desktop software Operating system support Features Terminology See also Notes References Remote desktop software https://en.wikipedia.org/wiki/Comparison_of_remote_desktop_software 1/9 9/29/2020 Comparison of remote desktop software - Wikipedia First Latest Free for Free for public Software Protocols Creator stable year, License personal commercial release version use use date AetherPal Proprietary AetherPal Inc. 2011 2016, Valet Proprietary No No Ammyy Admin Proprietary Ammyy Inc. 2007 2015, 3.5[1] Proprietary Yes No AnyDesk Software 2020-07-28, AnyDesk Proprietary 2015 Proprietary Yes No GmbH 6.0.7 Anyplace Control Anyplace Control Proprietary 2002 2012, 5.4.0.0 Proprietary No No Software AnywhereTS RDP, ICA Qzone ? 2009, 3.4 Proprietary Yes Yes Apple Remote Desktop RFB (VNC) Apple 2002 2017, 3.9[2] Proprietary No No Apple Screen Sharing (iChat) Proprietary, RFB (VNC) Apple 2007 2014, 1.6 Proprietary Yes Yes AppliDis RDP Systancia ? 2013, 4 SP3 Proprietary No No BeAnywhere Support Proprietary BeAnywhere 1996 2015, 6.00 Proprietary No No Express 2020-07-29, Cendio ThinLinc RFB (VNC) Cendio AB 2003 Proprietary Yes[a] Yes[a] 4.12.0 Chicken of the VNC RFB (VNC) ? 2002 2011-02, 2.1.1 GPL Yes Yes BSD Client, 2018, Chrome Remote Desktop Chromoting Google 2011 Proprietary Yes Yes 70.0.3538.21 Server CloudBerry Lab (CloudBerry May 25, Proprietary