An Analysis of End User Application Trends in the Enterprise, 7The Edition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

South Korea Section 3
DEFENSE WHITE PAPER Message from the Minister of National Defense The year 2010 marked the 60th anniversary of the outbreak of the Korean War. Since the end of the war, the Republic of Korea has made such great strides and its economy now ranks among the 10-plus largest economies in the world. Out of the ashes of the war, it has risen from an aid recipient to a donor nation. Korea’s economic miracle rests on the strength and commitment of the ROK military. However, the threat of war and persistent security concerns remain undiminished on the Korean Peninsula. North Korea is threatening peace with its recent surprise attack against the ROK Ship CheonanDQGLWV¿ULQJRIDUWLOOHU\DW<HRQS\HRQJ Island. The series of illegitimate armed provocations by the North have left a fragile peace on the Korean Peninsula. Transnational and non-military threats coupled with potential conflicts among Northeast Asian countries add another element that further jeopardizes the Korean Peninsula’s security. To handle security threats, the ROK military has instituted its Defense Vision to foster an ‘Advanced Elite Military,’ which will realize the said Vision. As part of the efforts, the ROK military complemented the Defense Reform Basic Plan and has UHYDPSHGLWVZHDSRQSURFXUHPHQWDQGDFTXLVLWLRQV\VWHP,QDGGLWLRQLWKDVUHYDPSHGWKHHGXFDWLRQDOV\VWHPIRURI¿FHUVZKLOH strengthening the current training system by extending the basic training period and by taking other measures. The military has also endeavored to invigorate the defense industry as an exporter so the defense economy may develop as a new growth engine for the entire Korean economy. To reduce any possible inconveniences that Koreans may experience, the military has reformed its defense rules and regulations to ease the standards necessary to designate a Military Installation Protection Zone. -

The New England College of Optometry Peer to Peer (P2P) Policy
The New England College of Optometry Peer To Peer (P2P) Policy Created in Compliance with the Higher Education Opportunity Act (HEOA) Peer-to-Peer File Sharing Requirements Overview: Peer-to-peer (P2P) file sharing applications are used to connect a computer directly to other computers in order to transfer files between the systems. Sometimes these applications are used to transfer copyrighted materials such as music and movies. Examples of P2P applications are BitTorrent, Gnutella, eMule, Ares Galaxy, Megaupload, Azureus, PPStream, Pando, Ares, Fileguri, Kugoo. Of these applications, BitTorrent has value in the scientific community. For purposes of this policy, The New England College of Optometry (College) refers to the College and its affiliate New England Eye Institute, Inc. Compliance: In order to comply with both the intent of the College’s Copyright Policy, the Digital Millennium Copyright Act (DMCA) and with the Higher Education Opportunity Act’s (HEOA) file sharing requirements, all P2P file sharing applications are to be blocked at the firewall to prevent illegal downloading as well as to preserve the network bandwidth so that the College internet access is neither compromised nor diminished. Starting in September 2010, the College IT Department will block all well-known P2P ports on the firewall at the application level. If your work requires the use of BitTorrent or another program, an exception may be made as outlined below. The College will audit network usage/activity reports to determine if there is unauthorized P2P activity; the IT Department does random spot checks for new P2P programs every 72 hours and immediately blocks new and emerging P2P networks at the firewall. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -

The Versatility of Microblogging
www.spireresearch.com Side Click: The versatility of microblogging Microblogging is well-established globally as a way of keeping in touch with others about events occurring in their lives in real-time. Popular microblogging sites include Twitter in the U.S., Tencent QQ in China and Me2day in South Korea. Twitter has 140 million active users1, while China’s Tencent QQ has a staggering 721 million active user accounts2, ranking only behind Facebook in terms of being the most used social networking service worldwide. Microblogging allows users to combine blogging and instant messaging to post short messages on their profiles3; including small and conversational talk, self-promotion, spam and news 4 . On a deeper level, microblogging has altered the way people consume and generate information – not only democratizing the broadcasting of information but also enabling it to be done in real-time. Connecting to stakeholders There are several benefits to integrating microblogging into a business’s regular stakeholder communication regime. Consumers who “follow” a company’s products or services would be the first to know of any promotions. The company also benefits through obtaining prompt feedback and suggestions for improvement. A concerned investor 1 Twitter turns six, Twitter Blog, 21 March 21 2012 2 QQ Continues to Dominate Instant Messaging in China, eMarketer Inc., 27 April 2012 3 An Insight Into Microblogging Trends And Toolbars, ArticlesXpert,21 January 2012 4 Twitter Study – August 2009, PearAnalytics.com, August 2009 © 2012 Spire Research and Consulting Pte Ltd would want to be the first to know of any important news which might impact her returns. -

Congratulations Susan & Joost Ueffing!
CONGRATULATIONS SUSAN & JOOST UEFFING! The Staff of the CQ would like to congratulate Jaguar CO Susan and STARFLEET Chief of Operations Joost Ueffi ng on their September wedding! 1 2 5 The beautiful ceremony was performed OCT/NOV in Kingsport, Tennessee on September 2004 18th, with many of the couple’s “extended Fleet family” in attendance! Left: The smiling faces of all the STARFLEET members celebrating the Fugate-Ueffi ng wedding. Photo submitted by Wade Olsen. Additional photos on back cover. R4 SUMMIT LIVES IT UP IN LAS VEGAS! Right: Saturday evening banquet highlight — commissioning the USS Gallant NCC 4890. (l-r): Jerry Tien (Chief, STARFLEET Shuttle Ops), Ed Nowlin (R4 RC), Chrissy Killian (Vice Chief, Fleet Ops), Larry Barnes (Gallant CO) and Joe Martin (Gallant XO). Photo submitted by Wendy Fillmore. - Story on p. 3 WHAT IS THE “RODDENBERRY EFFECT”? “Gene Roddenberry’s dream affects different people in different ways, and inspires different thoughts... that’s the Roddenberry Effect, and Eugene Roddenberry, Jr., Gene’s son and co-founder of Roddenberry Productions, wants to capture his father’s spirit — and how it has touched fans around the world — in a book of photographs.” - For more info, read Mark H. Anbinder’s VCS report on p. 7 USPS 017-671 125 125 Table Of Contents............................2 STARFLEET Communiqué After Action Report: R4 Conference..3 Volume I, No. 125 Spies By Night: a SF Novel.............4 A Letter to the Fleet........................4 Published by: Borg Assimilator Media Day..............5 STARFLEET, The International Mystic Realms Fantasy Festival.......6 Star Trek Fan Association, Inc. -

Test-Beds and Guidelines for Securing Iot Products and for Secure Set-Up Production Environments
IoT4CPS – Trustworthy IoT for CPS FFG - ICT of the Future Project No. 863129 Deliverable D7.4 Test-beds and guidelines for securing IoT products and for secure set-up production environments The IoT4CPS Consortium: AIT – Austrian Institute of Technology GmbH AVL – AVL List GmbH DUK – Donau-Universit t Krems I!AT – In"neon Technologies Austria AG #KU – JK Universit t Lin$ / Institute for &ervasive 'om(uting #) – Joanneum )esearch !orschungsgesellschaft mbH *+KIA – No,ia -olutions an. Net/or,s 0sterreich GmbH *1& – *1& -emicon.uctors Austria GmbH -2A – -2A )esearch GmbH -)!G – -al$burg )esearch !orschungsgesellschaft -''H – -oft/are 'om(etence 'enter Hagenberg GmbH -AG0 – -iemens AG 0sterreich TTTech – TTTech 'om(utertechni, AG IAIK – TU Gra$ / Institute for A((lie. Information &rocessing an. 'ommunications ITI – TU Gra$ / Institute for Technical Informatics TU3 – TU 3ien / Institute of 'om(uter 4ngineering 1*4T – 1-Net -ervices GmbH © Copyright 2020, the Members of the IoT4CPS Consortium !or more information on this .ocument or the IoT5'&- (ro6ect, (lease contact8 9ario Drobics7 AIT Austrian Institute of Technology7 mario:.robics@ait:ac:at IoT4C&- – <=>?@A Test-be.s an. guidelines for securing IoT (ro.ucts an. for secure set-up (ro.uction environments Dissemination level8 &U2LI' Document Control Title8 Test-be.s an. gui.elines for securing IoT (ro.ucts an. for secure set-u( (ro.uction environments Ty(e8 &ublic 4.itorBsC8 Katharina Kloiber 4-mail8 ,,;D-net:at AuthorBsC8 Katharina Kloiber, Ni,olaus DEr,, -ilvio -tern )evie/erBsC8 -te(hanie von )E.en, Violeta Dam6anovic, Leo Ha((-2otler Doc ID8 DF:5 Amendment History Version Date Author Description/Comments VG:? ?>:G?:@G@G -ilvio -tern Technology Analysis VG:@ ?G:G>:@G@G -ilvio -tern &ossible )esearch !iel.s for the -2I--ystem VG:> >?:G<:@G@G Katharina Kloiber Initial version (re(are. -

Table of Contents 500 GREAT PROGRAM IDEAS
Table of Contents 500 GREAT PROGRAM IDEAS Compiled by Recreation and Leisure Studies Students Gordon College Presented at Massachusetts Recreation and Park Association State Conference October 23, 2007 Workshop Presenters: Dr. Peggy Hothem Professor of Recreation and Leisure Studies Students: Christine Arruda, Christine Scanlon and Kendra Spotts Adult: Let's Talk An open forum for parents to exchange ideas, learn how to cope with ups and downs of parenthood, and acquire useful information from local guest speakers. Childcare and refreshments provided for participants. Where are Your Teenagers ----- on the Internet? Facebook, MySpace, IM, Textmessaging, and what is coming next? Learn to communicate in their language. (Best Buy and other technology retail stores can be a resource for providing an instructor – usually free of charge) Understanding Japanese Culture A course designed as an introduction to Japanese cuisine. Participants will learn Japanese cooking techniques, ingredients, quality brands, shopping tips, and how to locate Japanese grocers. Also you will prepare entrees. Fit Fitness in your Schedule Various fitness classes to choose from; Coed Body Sculpting, Exercise for the Early Bird, and Ultimate Step and Tone are only a few offered. Shorter sessions allow for greater flexibility for those with tight schedules Digital Camera Club Learn the newest techniques. Meetings consist of presentations by professional photographers, field trips, photo contests and photo demonstrations. A Mile In My Shoes A walking club offering the guidance and direction to start walking into shape! Tally sheets to keep track of walking distance, instructional handouts and fitness instructors will be provided. Each participant will record his/her mileage and receive prizes upon reaching goals. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Weekly Wireless Report WEEK ENDING September 4, 2015
Weekly Wireless Report WEEK ENDING September 4, 2015 INSIDE THIS ISSUE: THIS WEEK’S STORIES This Week’s Stories Ad Blocking In Apple’s iOS 9 Highlights Rift Over Ads With Ad Blocking In Apple’s iOS 9 Highlights Rift Over Ads With App Publishers App Publishers September 4, 2015 More Than 225,000 Apple Apple has warned developers that, in the name of privacy and user preference, it is adding ad-blocking iPhone Accounts Hacked capability in its upcoming release of iOS 9 software, which is expected to arrive with new iPhones as early as Sept. 9. And that’s creating some tension with Google, mobile marketing companies, and PRODUCTS & SERVICES publishers alike. A New App That Lets Users’ If iOS 9 and the ad blockers are widely adopted, it could mean significant disruption to the $70 billion Friends ‘Virtually Walk Them mobile marketing business. More ad blocking means that many users simply won’t see as many ads in Home At Night’ Is Exploding In their games or apps. Publishers, ad networks, and marketing tech companies will get less revenue. Popularity Mobile game companies don’t need to panic now, but they’d better pay attention. Sprint Revises Free Service The battle over the legality of ad-blocking software is still playing out on the Web, where online ads are Deal For DirecTV Customers, a $141 billion business. In May, a German court ruled that ad blocking is not illegal. In mobile, Apple Adds Data Options has added the ability to block ads via a change in its platform that allows third-party companies to create ad-blocking apps. -
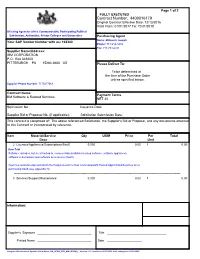
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00